A 3D model of a complex anaplastology case, created in collaboration with the anaplastologist Jan De Cubber, is seen at the Belgian company Materialise. 3D printing has already changed the game for manufacturing specialized products such as medical devices. REUTERS/Yves Herman
When Star Trek debuted in the mid-60s, everybody geeked out about the food synthesizers. Even my mom, a reluctant but compulsory Trek viewer, recognized the utility of this amazing gadget, particularly with two ravenous boys around the house. (My brother and I knew, of course, that the real magic food box was the refrigerator.)
Years later, I wasn’t the only one craving the replicators of Star Trek:The Next Generation for my home workshop. TNG’s follow-on concept of a ‘universal build-box’ upped the ante way beyond a hot cup of Earl Gray. The list of things we would have made, then and there at home, was endless: for the kids, replacement baseball bats, balls and window panes, game controllers and handheld electronic devices. I would have gone in for replacement car parts, repairs for broken appliances and furniture, and an endless supply of consumables like gasoline, toilet paper, kitty litter, and inevitably, a couple of cold—strictly non-syntheholic—beers for afterwards. (I note in passing that Starfleet protocol prohibits civilians from replicating weapons.)
With the recent rise of the Maker movement and the advent of cheaper, easier-to-use 3D-printing technology, the sci-fi concept of a household device that can manufacture functional objects seems to be gaining reality, but for those who witnessed the technology’s birth and growth, it has been a surprisingly long and winding road, one that has, however, recently reached a significant but mostly unnoticed milestone. As for me, it all began with Star Trek and the Silver Surfer.

A 3D object called the Quin.MGX is seen at the Belgian company Materialise, a pioneer in the process. REUTERS/Yves Herman
Exactly how replicators—presumably some sort of universal matter assemblers—might actually work has always remained unclear. The first time that I saw a version of the concept that offered some inkling of how a fabrication machine might operate was in 1969. It was in the classic Marvel comic book, Silver Surfer #1, when our superhero-to-be, Norrin Radd, rushes to build a spaceship so he can fly out to confront Galactus, the super-being that will otherwise consume his homeworld. Radd gets a top scientist to deploy a "mental constructor", a helmet-mounted beam-like device that does all the work for him: "within seconds the image of your ship which in have in my mind...shall take solid form before our eyes!"
The notion of wielding an energy beam to build a working rocket in one’s own lab was like catnip to somebody who ran a side business at the elementary school dealing (to trusted friends only) three-stage, explosive rocket munitions that I’d fabricated in secret at home from notebook paper, Scotch tape, matchbooks and soda straws (but that’s another story…).
A decade and half later, when I was first working as a science and technology writer/editor, it was therefore very natural for me to become captivated by the new manufacturing marvel of the day, 3D-printing technology. Watching 3D Systems’ groundbreaking SLA stereolithography system was particularly impressive. The moving laser beam built parts right there in the chamber out of photo-curable liquid polymer: “Holy shit, it’s the Silver Surfer’s fabricator!”

Thos 3D vase, called The Hidden, was designed by Dan Yeffetlamp. REUTERS/Yves Herman
Adding and subtracting
One of the publications for which I worked covered the machine-tool industry, which built big, powerful milling machines, drills and so forth, devices that carve away material from blanks in a subtractive fashion to leave the desired object, like a sculptor does. In contrast, the new additive 3D machines built the target objects from the bottom up in layers, like a bricklayer. Both technologies rely on the same precision x,y,z machine stages to exactly position the tool or workpiece within the three-dimensional build volume—so it was little wonder we followed the technology closely.
The first step in nearly all those and most of today’s processes for “turning bits into atoms” involves using CAD/CAM software to create a 3D digital design that is then cut into two-dimensional “slices”—as if the virtual object were run through a kitchen egg-slicer. The resulting stack of cross-sections are next fed one-by-one as data into a printer unit, which directs a laser or dispenser head to follow a tool path that produces that layer of the physical object. Generally, nearly all 3D-printers first deposit a thin layer of material—metal or polymer powders, or a plastic goop that’s extruded like toothpaste—and then solidify the patterns layer-by-layer with laser light or other means, a procedure that in time yields a nearly completely finished object.

Posted to Creative Tools' flickr page, this model of Star Wars' Yoda was made with Fabbster, a 3D printer that can be bought on Amazon.com for $1800 in kit form, or $3000 pre-assembled.
Just a matter of time
The initial users of the technology, mostly product designers and engineers, could revise, tweak and iterate their unfinished designs easily and cheaply using “rapid prototyping” models, a process that in time greatly enhanced design capabilities and engineering productivity. And right from the get-go, the new fab technology hinted that it might bring about potentially revolutionary changes in global manufacturing practices by offering a possible paradigm shift for basic production, one that just might turn traditional supply trains on their heads. From our perspective, it seemed a given that at some point pretty much everybody would have ready access to functional metal and plastic objects—replacement parts, “one-offs,” you name it—made precisely to their specifications quickly and affordably locally.
Sure, the early fab units could only make rather flimsy epoxy and polymer models for design and engineering purposes, but we knew that it was only a matter of time before they would be able to manufacture practical parts out of many different engineering materials. We were certain as well that system and operating costs would drop as the process took greater hold in industry and production volumes rose. Not too long thereafter tougher ABS plastic 3D-printed components arrived, and researchers at places like Sandia Labs, MIT and the University of Texas at Austin were hard at work developing build processes that could manufacture working metal parts like those in your clothes washer, lawn mower or car by welding or fusing together metal powders.

A colorful geometric shape casts a shadow. Photo: fdecomite
Slow progress
As things developed, however, making functional 3D-printed objects a reality took much longer come to fruition than any of us had expected. Researchers have had to toil away for decades to perfect these basic innovations, and time had to pass for some of the crucial patents to expire and for computer, laser and materials technologies to advance sufficiently.
Year after year, the 3D-printer industry booths at manufacturing trade shows like the big International Machine Tool Show in Chicago would feature mostly design models, toys and puzzles and all manner of customized tchotchkes, knick-knacks, and one-off novelty items—yes, increasingly sophisticated stuff with ever-tightening dimensional precision—but for many years real-world commercial products were embarrassingly scarce. Those there that did eventually emerge were typically “high value-added” products, whose market niche typically arose from an acute need for the customization enabled by additive manufacturing processes. 3D-printed medical implants, using CAT scans as blueprints, eventually hit the market, for instance.
In the last decade, the steady progress in digital technology and the 3D-printing industry’s continuing R&D efforts has now brought into being multiple fabrication methods that employ new, better performing materials to achieve significantly better precision and build-quality. Today’s higher-end printers can produce truly amazing objects with highly complex, even ‘impossible,’ geometries as well as integral—built-in—moving parts.
But it was only the emergence of more affordable ‘home’ 3D-printer units, at a couple of thousand dollars a pop, has the technology caused any real excitement among the public. The burgeoning Maker movement—enthusiasts inspired by the DIY/home-grown ethic, the desire to personalize possessions and often a primal desire to democratize production—has captured the imagination of many technologists who once again dream of a replicator in every home. That iconic vision and the ready ability for designs to be downloaded from the Web, or easily scanned using a real object, has fanned the trend to the point that I will soon be able to buy a printer at Staples and download CAD/CAM designs to a ‘neighborhood’ fab shop that runs industrial printing systems. In the meantime, access to user information about the process and demos have become increasingly available at Maker Faires and similar events nationwide.
Until very recently the output of home systems has been mostly restricted to often very cool but mostly non-functional or non-structural aesthetic or decorative objects such as jewelry, highly customized items like cell phone covers, or relatively low-function replacement mechanical parts. That is starting to change.
But even though home 3D-printing has received substantial publicity of late, it is in the industrial sector where the technology will probably make its most significant near-term impact on the world both by manufacturing improved commercial products and by stimulating industry to develop next-generation fab methods and machines that could one day truly bring 3D-printing home to users in a real way.

This winged skull, uploaded to flickr by Jeremy Keith, demonstrates 3D printing tech's ability to produce extremely complex designs.
3D-printing nears mass production
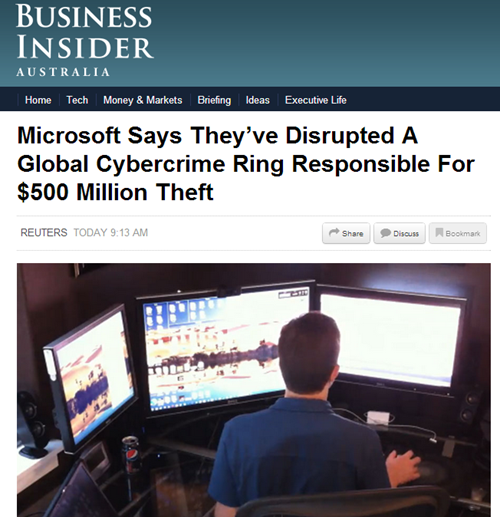
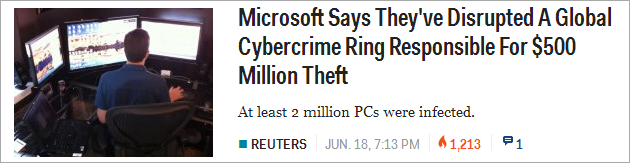
So a couple of months ago when I heard that GE Aviation had decided to put into mass-production a 3D-printed jet engine component within the next few years, I knew that the real revolution had finally begun.
Rows of industrial 3D-printing units in plants will soon be fabricating turbine engine parts—fuel nozzles—from cobalt-chromium alloy powders. Each one of GE’s new LEAP jet engine will contain nineteen of the fuel nozzles, which are up to 25 percent lighter and five-times more durable than traditionally manufactured fuel nozzles. In airplanes cutting weight saves fuel. The LEAP engine has already amassed more than 4,500 orders, so between it and the new GE9X engine, the corporation could end up making as many as 100,000 additive manufactured components by 2020.
GE Aviation and Santa Fe-based Sigma Labs are working together to develop in-process inspection technology that is to verify the quality and geometry of the additive components during the build process, boosting production speeds by as much as a quarter and enabling faster FAA qualification of the parts. Recent news reports indicate that initial assembly of the first pre-production LEAP engines began just last week.
GE researchers also say that clinical testing has begun of a low-cost medical ultrasound sensor prototype made by 3D-printing ceramic powders. The new, cheaper device could potentially bring prenatal imaging to many more expectant mothers in third-world nations.

A Nestle logo was printed by a 3D printer during a display for the inauguration of the system technology centre for the design, development and deployment of their products in Orbe. REUTERS/Denis Balibouse
Make it so
So here’s my point. Such progress in the industrialization of 3D-printing technology is probably the best thing that could happen to the Maker movement. It’s only a matter of time before spin-off technologies start trickling down into the hands of hobbyist and neighborhood makers at affordable prices. Greater R&D investment will in time surely yield a steady flow of more capable and presumably cheaper home printing technology, including new machines, enhanced design software, more and better fab materials and deeper processing knowledge. These innovations should help bring 3D-printing and additive manufacturing firmly into the mainstream and maybe into your own home.
Real-world replicators have taken a lot longer to materialize than I’d thought; it’s been nearly half a century since Star Trek first appeared. (Yeah, they also promised me jet-packs…) But the replicator revolution seems to be happening at last. Now where are those beers?

A handout electron microscope photograph shows a nano-scale model of London's Tower-Bridge created by a recently-developed 3D printing technique for nanostructures. Researchers from the Vienna University created their grain of sand-size structures in just four minutes, a fraction of the time that other tiny items were previously printed. Photo: Vienna University of Technology 











 On a day when I immediately started hitting the usual "waves" of stopped traffic, I decided to drive slow. Rather than repeatedly rushing ahead with everyone else, only to come to a halt, I decided to try to drive at the average speed of the traffic. I let a huge gap open up ahead of me, and timed things so I was arriving at the next "stop-wave" just as the last red brake lights were turning off ahead of me. It certainly felt weird to have that huge empty space ahead of me, but I knew I was driving no slower than anyone else. Sometimes I hit it just right and never had to touch the brakes at all, but sometimes I was too fast or slow. There were many "waves" that evening, and this gave me many opportunities to improve my skill as I drove along.
On a day when I immediately started hitting the usual "waves" of stopped traffic, I decided to drive slow. Rather than repeatedly rushing ahead with everyone else, only to come to a halt, I decided to try to drive at the average speed of the traffic. I let a huge gap open up ahead of me, and timed things so I was arriving at the next "stop-wave" just as the last red brake lights were turning off ahead of me. It certainly felt weird to have that huge empty space ahead of me, but I knew I was driving no slower than anyone else. Sometimes I hit it just right and never had to touch the brakes at all, but sometimes I was too fast or slow. There were many "waves" that evening, and this gave me many opportunities to improve my skill as I drove along. 
















 For $75,
For $75, 


 [Advertisement] Make your team a DevOps team with
[Advertisement] Make your team a DevOps team with 




 A classic experiment into drug addiction science. Would rats choose to take drugs if given a stimulating environment and social company?
A classic experiment into drug addiction science. Would rats choose to take drugs if given a stimulating environment and social company?