An identity theft service that sells Social Security numbers, birth records, credit and background reports on millions of Americans has infiltrated computers at some of America’s largest consumer and business data aggregators, according to a seven-month investigation by KrebsOnSecurity.
 The Web site ssndob[dot]ms (hereafter referred to simply as SSNDOB) has for the past two years marketed itself on underground cybercrime forums as a reliable and affordable service that customers can use to look up SSNs, birthdays and other personal data on any U.S. resident. Prices range from 50 cents to $2.50 per record, and from $5 to $15 for credit and background checks. Customers pay for their subscriptions using largely unregulated and anonymous virtual currencies, such as Bitcoin and WebMoney.
The Web site ssndob[dot]ms (hereafter referred to simply as SSNDOB) has for the past two years marketed itself on underground cybercrime forums as a reliable and affordable service that customers can use to look up SSNs, birthdays and other personal data on any U.S. resident. Prices range from 50 cents to $2.50 per record, and from $5 to $15 for credit and background checks. Customers pay for their subscriptions using largely unregulated and anonymous virtual currencies, such as Bitcoin and WebMoney.
Until very recently, the source of the data sold by SSNDOB has remained a mystery. That mystery began to unravel in March 2013, when teenage hackers allegedly associated with the hacktivist group UGNazi showed just how deeply the service’s access went. The young hackers used SSNDOB to collect data for exposed.su, a Web site that listed the SSNs, birthdays, phone numbers, current and previous addresses for dozens of top celebrities — such as performers Beyonce, Kanye West and Jay Z — as well as prominent public figures, including First Lady Michelle Obama, CIA Director John Brennan, and then-FBI Director Robert Mueller.
Earlier this summer, SSNDOB was compromised by multiple attackers, its own database plundered. A copy of the SSNDOB database was exhaustively reviewed by KrebsOnSecurity.com. The database shows that the site’s 1,300 customers have spent hundreds of thousands of dollars looking up SSNs, birthdays, drivers license records, and obtaining unauthorized credit and background reports on more than four million Americans.
Frustratingly, the SSNDOB database did not list the sources of that stolen information; it merely indicated that the data was being drawn from a number of different places designated only as “DB1,” “DB2,” and so on.
But late last month, an analysis of the networks, network activity and credentials used by SSNDOB administrators indicate that these individuals also were responsible for operating a small but very potent botnet — a collection of hacked computers that are controlled remotely by attackers. This botnet appears to have been in direct communications with internal systems at several large data brokers in the United States. The botnet’s Web-based interface (portions of which are shown below) indicated that the miscreants behind this ID theft service controlled at least five infected systems at different U.S.-based consumer and business data aggregators.
![The botnet interface used by the miscreants who own and operate ssndob[dot]ms](http://krebsonsecurity.com/wp-content/uploads/2013/09/SSNdobBotC2-600x118.png)
The botnet interface used by the miscreants who own and operate ssndob[dot]ms
DATA-BROKER BOTNET
Two of the hacked servers were inside the networks of Atlanta, Ga.-based LexisNexis Inc., a company that according to Wikipedia maintains the world’s largest electronic database for legal and public-records related information. Contacted about the findings, LexisNexis confirmed that the two systems listed in the botnet interface were public-facing LexisNexis Web servers that had been compromised.
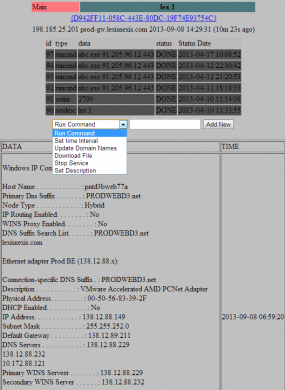
One of two bots connected to SSNDOB that was inside of LexisNexis.
The botnet’s online dashboard for the LexisNexis systems shows that a tiny unauthorized program called “nbc.exe” was placed on the servers as far back as April 10, 2013, suggesting the intruders have had access to the company’s internal networks for at least the past five months. The program was designed to open an encrypted channel of communications from within LexisNexis’s internal systems to the botnet controller on the public Internet.
Two other compromised systems were located inside the networks of Dun & Bradstreet, a Short Hills, New Jersey data aggregator that licenses information on businesses and corporations for use in credit decisions, business-to-business marketing and supply chain management. According to the date on the files listed in the botnet administration panel, those machines were compromised at least as far back as March 27, 2013.
The fifth server compromised as part of this botnet was located at Internet addresses assigned to Kroll Background America, Inc., a company that provides employment background, drug and health screening. Kroll Background America is now part of HireRight, a background-checking firm managed by the Falls Church, Va.-based holding company Altegrity, which owns both the Kroll and HireRight properties. Files left behind by intruders into the company’s internal network suggest the HireRight breach extends back to at least June 2013.
An initial analysis of the malicious bot program installed on the hacked servers reveals that it was carefully engineered to avoid detection by antivirus tools. A review of the bot malware in early September using Virustotal.com – which scrutinizes submitted files for signs of malicious behavior by scanning them with antivirus software from nearly four dozen security firms simultaneously — gave it a clean bill of health: none of the 46 top anti-malware tools on the market today detected it as malicious (as of publication, the malware is currently detected by 6 out of 46 anti-malware tools at Virustotal).
ASSESSING THE DAMAGE
All three victim companies said they are working with federal authorities and third-party forensics firms in the early stages of determining how far the breaches extend, and whether indeed any sensitive information was accessed and exfiltrated from their networks.
For its part, LexisNexis confirmed that the compromises appear to have begun in April of this year, but said it found “no evidence that customer or consumer data were reached or retrieved,” via the hacked systems. The company indicated that it was still in the process of investigating whether other systems on its network may have been compromised by the intrusion.
“Immediately upon becoming aware of this matter, we contacted the FBI and initiated a comprehensive investigation working with a leading third party forensic investigation firm,” said Aurobindo Sundaram, vice president of information assurance and data protection at Reed Elsevier, the parent company of LexisNexis. ”In that investigation, we have identified an intrusion targeting our data but to date have found no evidence that customer or consumer data were reached or retrieved. Because this matter is actively being investigated by law enforcement, I can’t provide further information at this time.”
Dun & Bradstreet and Altegrity were less forthcoming about what they’d found so far. Elliot Glazer, chief technology officer at Dun & Bradstreet, said the information provided about the botnet’s interaction with the company’s internal systems had been “very helpful.”
“We are aggressively investigating the matter, take it very seriously and are in touch with the appropriate authorities,” Glazer said. “Data security is a company priority, and I can assure you that we are devoting all resources necessary to ensure that security.”
Altegrity declined to confirm or deny the apparent compromises, but through spokesman Ray Howell offered the following statement: “We consider the protection and safeguarding of our various systems of the utmost importance. We have dedicated significant information security resources to managing security and protecting the data and privacy of our customers. We have a range of incident response specialists and teams from both inside and outside the company investigating your allegations vigorously.”
Referring to the SSNDOB compromises, FBI Spokesperson Lindsay Godwin confirmed that the FBI is “aware of and investigating this case,” but declined to comment further except to say that the investigation is ongoing.
KNOWLEDGE IS POWER
The intrusions raise major questions about how these compromises may have aided identity thieves. The prevailing wisdom suggests that the attackers were going after these firms for the massive amounts of consumer and business data that they hold. While those data stores are certainly substantial, fraud experts say the really valuable stuff is in the data that these firms hold about consumer and business habits and practices.
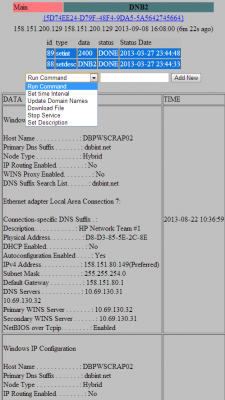
The botnet control panel entry for a hacked Dun & Bradstreet server
Avivah Litan, a fraud analyst with Gartner Inc., said most credit-granting organizations assess the likelihood that a given application for credit is valid or fraudulent largely based on how accurately an applicant answers a set of questions about their financial and consumer history.
These questions, known in industry parlance as “knowledge-based authentication” or KBA for short, have become the gold standard of authentication among nearly all credit-granting institutions, from loan providers to credit card companies, Litan said. She estimates that the KBA market is worth at least $2 billion a year.
“Let’s say you’re trying to move money via online bank transfer, or apply for a new line of credit,” Litan proposed. “There are about 100 questions and answers that companies like LexisNexis store on all of us, such as, ‘What was your previous address?’ or ‘Which company services your mortgage?’ They also have a bunch of bogus questions that they can serve up to see if you really are who you say you are.”
According to Litan, Dun and Bradstreet does roughly the same thing, except for businesses.
“Dun & Bradstreet doesn’t do KBA per se, but if you’re filling out a business loan and you want to pose as that business, having access to a company like that can help,” Litan said. “Dun & Bradstreet is like the credit bureau for businesses.”
Overall, Litan says, credit applicants fail to answer one or more of the KBA questions correctly about 10-15 percent of the time. Ironically, however, those that get the questions wrong are more often legitimate credit applicants — not the identity thieves.
“These days, the people who fail these questions are mainly those who don’t remember the answers,” Litan said. “But the criminals seem to be having no problems.”
Litan related a story she heard from one fellow fraud analyst who had an opportunity to listen in on the KBA questions that a mortgage lender was asking of a credit applicant who was later determined to have been a fraudster.
“The woman on the phone was asking the applicant, ‘Hey, what is the amount of your last mortgage payment?’, and you could hear the guy on the other line saying hold on a minute….and you could hear him clicking through page after page for the right questions,” Litan said.
The Gartner fraud analyst said she has long suspected that the major KBA providers have been compromised, and has been saying so for years.
“We could well be witnessing the death of knowledge-based authentication, and it’s as it should be,” Litan said. “The problem is that right now there are no good alternatives that are as easy to implement. There isn’t a good software-based alternative. Everybody in the industry knows that KBA is nearing its end of usefulness, but it’s not like you can instantly roll out biometric identifiers to the entire US population. We’re just not there yet. It’s years away. If ever.”
CUSTOMER SERVICE
![Breakdown of ssn[dot]dob users by IP address](http://krebsonsecurity.com/wp-content/uploads/2013/09/ssndobusers-285x171.png)
Breakdown of ssn[dot]dob users by IP address
A closer examination of the database for the identity theft service shows it has served more than 1.02 million unique SSNs to customers and nearly 3.1 million date of birth records since its inception in early 2012.
Thousands of background reports also have been ordered through SSNDOB. Records at the ID theft service indicate that the service was still able to order background reports via LexisNexis more than 10 days after the data aggregator disabled the infected Web servers listed in the botnet’s control panel, suggesting that the intruders still had a store of accounts that could be used to pull information from the company’s databanks.
In a written statement provided to KrebsOnSecurity, LexisNexis officials said that report was generated from a law student ID that was being misused.
“Unrelated to the intrusion you have asked about, you provided to us a LexisNexis report. We determined that that report was generated from a law student ID that was being misused. That ID accesses only unregulated public records information and was identified by our fraud detection tools and shut down by us before you brought it to our attention.”
The registration records for SSNDOB show that most users registered with the ID theft service using Internet addresses in the United States, the Russian Federation, and the United Kingdom, although it is likely that a large portion of these users were using hacked PCs or other proxy systems to mask their true location.
SSNDOB also appears to have licensed its system for use by at least a dozen high-volume users. There is some evidence which indicates that these users are operating third-party identity theft services. A review of the leaked site records show that several bulk buyers were given application programming interfaces (APIs) — customized communications channels that allow disparate systems to exchange data — that could permit third-party or competing online ID theft sites to conduct lookups directly and transparently through the SSNDOB Web site.
Indeed, the records from SSNDOB show that the re-sellers of its service reliably brought in more money than manual look-ups conducted by all of the site’s 1,300 individual customers combined.
I would like to thank Alex Holden of Hold Security LLC for his assistance in making sense of much of this data.
Stay tuned for Part II and Part III of this rapidly unfolding story. Update: See Part II of this series: Data Broker Hackers Also Compromised NW3C.
Update, 2:05 p.m. ET: SSNDOB appears to be down. Also, one likely reseller of the ID theft service’s data — a fraud site called bstab[dot]su, has been having trouble all morning looking up SSN data. Lookups at that service are sending paying customers into an endless loop today. See image below.













![The botnet interface used by the miscreants who own and operate ssndob[dot]ms](http://krebsonsecurity.com/wp-content/uploads/2013/09/SSNdobBotC2-600x118.png)


![Breakdown of ssn[dot]dob users by IP address](http://krebsonsecurity.com/wp-content/uploads/2013/09/ssndobusers-285x171.png)