Read more of this story at Slashdot.
Fred Souza
Shared posts
Older Workers Are Better At Adapting To New Technology, Study Finds
Microsoft, Google, Apple Could Be Requested To Actively Block Pirated Downloads, Says Report
Read more of this story at Slashdot.
Police Asked Facebook To Deactivate Woman's Account During Deadly Standoff
Read more of this story at Slashdot.
Project Hosting Service Fosshub Compromised, Embedding Malware Inside Hosted Files
Read more of this story at Slashdot.
Frequent password changes are the enemy of security, FTC technologist says

Enlarge / FTC Chief Technologist Lorrie Cranor speaking at PasswordsCon 2016, part of the Bsides security conference in Las Vegas.
Shortly after Carnegie Mellon University professor Lorrie Cranor became chief technologist at the Federal Trade Commission in January, she was surprised by an official agency tweet that echoed some oft-repeated security advice. It read: "Encourage your loved ones to change passwords often, making them long, strong, and unique." Cranor wasted no time challenging it.
The reasoning behind the advice is that an organization's network may have attackers inside who have yet to be discovered. Frequent password changes lock them out. But to a university professor who focuses on security, Cranor found the advice problematic for a couple of reasons. For one, a growing body of research suggests that frequent password changes make security worse. As if repeating advice that's based more on superstition than hard data wasn't bad enough, the tweet was even more annoying because all six of the government passwords she used had to be changed every 60 days.
"I saw this tweet and I said, 'Why is it that the FTC is going around telling everyone to change their passwords?'" she said during a keynote speech at the BSides security conference in Las Vegas. "I went to the social media people and asked them that and they said, 'Well, it must be good advice because at the FTC we change our passwords every 60 days."
Massachusetts Bans Employers from Asking Applicants About Previous Pay
America Uses Stealthy Submarines To Hack Other Countries' Systems
Read more of this story at Slashdot.
Ask Slashdot: Best Browser Extensions -- 2016 Edition
Read more of this story at Slashdot.
Microsoft To Disable Policies In Windows 10 Pro With Anniversary Update
Read more of this story at Slashdot.
C Top Programming Language For 2016, Finds IEEE's Study
Read more of this story at Slashdot.
'The Wolf of Wall Street' Movie Was Financed With Stolen Money, Says DOJ
Read more of this story at Slashdot.
20-year-old Windows bug lets printers install malware—patch now
Enlarge (credit: Vectra Networks)
For more than two decades, Microsoft Windows has provided the means for clever attackers to surreptitiously install malware of their choice on computers that connect to booby-trapped printers, or other devices masquerading as printers, on a local area network. Microsoft finally addressed the bug on Tuesday during its monthly patch cycle.
The vulnerability resides in the Windows Print Spooler, which manages the process of connecting to available printers and printing documents. A protocol known as Point-and-Print allows people who are connecting to a network-hosted printer for the first time to automatically download the necessary driver immediately before using it. It works by storing a shared driver on the printer or print server and eliminates the hassle of the user having to manually download and install it.
Researchers with security firm Vectra Networks discovered that the Windows Print Spooler doesn't properly authenticate print drivers when installing them from remote locations. The failure makes it possible for attackers to use several different techniques that deliver maliciously modified drivers instead of the legitimate one provided by the printer maker. The exploit effectively turns printers, printer servers, or potentially any network-connected device masquerading as a printer into an internal drive-by exploit kit that infects machines whenever they connect.
How Technology Disrupted the Truth
Read more of this story at Slashdot.
TOS agreements require giving up first born—and users gladly consent
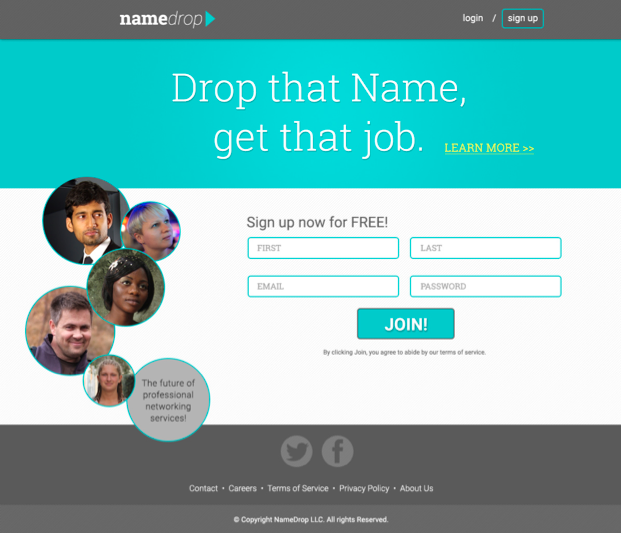
Here is the front door of a fictitious social networking site that study participants thought was real. All participants, US university students, agreed to terms that included demanding their first born as payment. The privacy policy they all checked off said their data would be shared with the NSA and employers. (credit: Biggest Lie on the Internet)
A recent study concludes what everybody already knows: nobody reads the lengthy terms of service and privacy policies that bombard Internet users every day. Nobody understands them. They're too long, and they often don't make sense.
A study out this month made the point all too clear. Most of the 543 university students involved in the analysis didn't bother to read the terms of service before signing up for a fake social networking site called "NameDrop" that the students believed was real. Those who did glossed over important clauses. The terms of service required them to give up their first born, and if they don't yet have one, they get until 2050 to do so. The privacy policy said that their data would be given to the NSA and employers. Of the few participants who read those clauses, they signed up for the service anyway.
"This brings us to the biggest lie on the Internet, which anecdotally, is known as 'I agree to these terms and conditions,'" the study found.
Assembly Code That Took America to the Moon Now Published On GitHub
Read more of this story at Slashdot.