Read more of this story at Slashdot.
Shared posts
Is Clean Energy Buried at the Bottom of Abandoned Oil Wells?
We're looking for people to cover Microsoft tech news at Neowin

Hackers can infect >100 Lenovo models with unremovable malware. Are you patched?
Maxim BangeNo ThinkPads ;-)

Enlarge / This is the 14-inch variant of the Yoga Slim 9i, with leather finish. (credit: Lenovo)
Lenovo has released security updates for more than 100 laptop models to fix critical vulnerabilities that make it possible for advanced hackers to surreptitiously install malicious firmware that can be next to impossible to remove or, in some cases, to detect.
Three vulnerabilities affecting more than 1 million laptops can give hackers the ability to modify a computer’s UEFI. Short for Unified Extensible Firmware Interface, the UEFI is the software that bridges a computer’s device firmware with its operating system. As the first piece of software to run when virtually any modern machine is turned on, it’s the initial link in the security chain. Because the UEFI resides in a flash chip on the motherboard, infections are difficult to detect and even harder to remove.
Oh, no
Two of the vulnerabilities—tracked as CVE-2021-3971 and CVE-2021-3972—reside in UEFI firmware drivers intended for use only during the manufacturing process of Lenovo consumer notebooks. Lenovo engineers inadvertently included the drivers in the production BIOS images without being properly deactivated. Hackers can exploit these buggy drivers to disable protections, including UEFI secure boot, BIOS control register bits, and protected range register, which are baked into the serial peripheral interface (SPI) and designed to prevent unauthorized changes to the firmware it runs.
Undetectable Backdoors in Machine-Learning Models
New paper: “Planting Undetectable Backdoors in Machine Learning Models“:
Abstract: Given the computational cost and technical expertise required to train machine learning models, users may delegate the task of learning to a service provider. We show how a malicious learner can plant an undetectable backdoor into a classifier. On the surface, such a backdoored classifier behaves normally, but in reality, the learner maintains a mechanism for changing the classification of any input, with only a slight perturbation. Importantly, without the appropriate “backdoor key”, the mechanism is hidden and cannot be detected by any computationally-bounded observer. We demonstrate two frameworks for planting undetectable backdoors, with incomparable guarantees.
First, we show how to plant a backdoor in any model, using digital signature schemes. The construction guarantees that given black-box access to the original model and the backdoored version, it is computationally infeasible to find even a single input where they differ. This property implies that the backdoored model has generalization error comparable with the original model. Second, we demonstrate how to insert undetectable backdoors in models trained using the Random Fourier Features (RFF) learning paradigm or in Random ReLU networks. In this construction, undetectability holds against powerful white-box distinguishers: given a complete description of the network and the training data, no efficient distinguisher can guess whether the model is “clean” or contains a backdoor.
Our construction of undetectable backdoors also sheds light on the related issue of robustness to adversarial examples. In particular, our construction can produce a classifier that is indistinguishable from an “adversarially robust” classifier, but where every input has an adversarial example! In summary, the existence of undetectable backdoors represent a significant theoretical roadblock to certifying adversarial robustness.
EDITED TO ADD (4/20): Cory Doctorow wrote about this as well.
Apple Starts Manufacturing iPhone 13 In India
Read more of this story at Slashdot.
De-anonymizing Bitcoin
Andy Greenberg wrote a long article — an excerpt from his new book — on how law enforcement de-anonymized bitcoin transactions to take down a global child porn ring.
Within a few years of Bitcoin’s arrival, academic security researchers — and then companies like Chainalysis — began to tear gaping holes in the masks separating Bitcoin users’ addresses and their real-world identities. They could follow bitcoins on the blockchain as they moved from address to address until they reached one that could be tied to a known identity. In some cases, an investigator could learn someone’s Bitcoin addresses by transacting with them, the way an undercover narcotics agent might conduct a buy-and-bust. In other cases, they could trace a target’s coins to an account at a cryptocurrency exchange where financial regulations required users to prove their identity. A quick subpoena to the exchange from one of Chainalysis’ customers in law enforcement was then enough to strip away any illusion of Bitcoin’s anonymity.
Chainalysis had combined these techniques for de-anonymizing Bitcoin users with methods that allowed it to “cluster” addresses, showing that anywhere from dozens to millions of addresses sometimes belonged to a single person or organization. When coins from two or more addresses were spent in a single transaction, for instance, it revealed that whoever created that “multi-input” transaction must have control of both spender addresses, allowing Chainalysis to lump them into a single identity. In other cases, Chainalysis and its users could follow a “peel chain” — a process analogous to tracking a single wad of cash as a user repeatedly pulled it out, peeled off a few bills, and put it back in a different pocket. In those peel chains, bitcoins would be moved out of one address as a fraction was paid to a recipient and then the remainder returned to the spender at a “change” address. Distinguishing those change addresses could allow an investigator to follow a sum of money as it hopped from one address to the next, charting its path through the noise of Bitcoin’s blockchain.
Thanks to tricks like these, Bitcoin had turned out to be practically the opposite of untraceable: a kind of honeypot for crypto criminals that had, for years, dutifully and unerasably recorded evidence of their dirty deals. By 2017, agencies like the FBI, the Drug Enforcement Agency, and the IRS’s Criminal Investigation division (or IRS-CI) had traced Bitcoin transactions to carry out one investigative coup after another, very often with the help of Chainalysis.
Bookmarked (Re)Introducing Readlists by Jim Nie...
Bookmarked (Re)Introducing Readlists by Jim Nielsen
This is another good example to put on my list of ‘discontinued services that deserve to be re-created’, although not necessarily as a central tool and more like a personal tool that can network. Delicious, Dopplr are others that come to mind. Also relevant because, in terms of reading, pulling together a collection of web articles on the same topic and then reading and annotating them in one go, this might be more effective in terms of learning. Might give this a try with some already saved articles on one topic or other. (found via Frank Meeuwsen)
I found myself every few weeks thinking, “gosh, I wish that service was still up. I really need to make a readlist out these handful of articles.” … I finally asked myself: “well then why don’t you recreate it?”
Jim Nielsen
The handshake in space that brought hope to the world
Mystery solved in destructive attack that knocked out >10k Viasat modems

Enlarge / A Viasat Internet satellite dish in the yard of a house in Madison, Virginia. (credit: Getty Images)
Viasat—the high-speed-satellite-broadband provider whose modems were knocked out in Ukraine and other parts of Europe earlier in March—confirmed a theory by third-party researchers that new wiper malware with possible ties to the Russian government was responsible for the attack.
In a report published Thursday, researchers at SentinelOne said they uncovered the new modem wiper and named it AcidRain. The researchers said AcidRain shared multiple technical similarities to parts of VPNFilter, a piece of malware that infected more than 500,000 home and small-office modems in the US. Multiple US government agencies—first the FBI and later organizations including the National Security Agency—all attributed the modem malware to Russian state threat actors.
Enter ukrop
SentinelOne researchers Juan Andres Guerrero-Saade and Max van Amerongen posited that AcidRain was used in a cyberattack that sabotaged thousands of modems used by Viasat customers. Among the clues they found was the name "ukrop" for one of AcidRain's source binaries.
I’m done with Wyze

I just threw my Wyze home security cameras in the trash. I’m done with this company.
I just learned that for the past three years, Wyze has been fully aware of a vulnerability in its home security cameras that could have let hackers look into your home over the internet — but chose to sweep it under the rug. And the security firm that found the vulnerability largely let them do it.
Three years
Instead of patching it, instead of recalling it, instead of just, you know, saying something so I could stop pointing these cameras at my kids, Wyze simply decided to discontinue the WyzeCam v1 this January without a full explanation. But on Tuesday, security research firm Bitdefender finally shed light on why Wyze stopped selling it: because...
Is Burnout Just a Sign of a Broken Labor System?
Read more of this story at Slashdot.
Developer Sabotages Open-Source Software Package
This is a big deal:
A developer has been caught adding malicious code to a popular open-source package that wiped files on computers located in Russia and Belarus as part of a protest that has enraged many users and raised concerns about the safety of free and open source software.
The application, node-ipc, adds remote interprocess communication and neural networking capabilities to other open source code libraries. As a dependency, node-ipc is automatically downloaded and incorporated into other libraries, including ones like Vue.js CLI, which has more than 1 million weekly downloads.
[…]
The node-ipc update is just one example of what some researchers are calling protestware. Experts have begun tracking other open source projects that are also releasing updates calling out the brutality of Russia’s war. This spreadsheet lists 21 separate packages that are affected.
One such package is es5-ext, which provides code for the ECMAScript 6 scripting language specification. A new dependency named postinstall.js, which the developer added on March 7, checks to see if the user’s computer has a Russian IP address, in which case the code broadcasts a “call for peace.”
It constantly surprises non-computer people how much critical software is dependent on the whims of random programmers who inconsistently maintain software libraries. Between log4j and this new protestware, it’s becoming a serious vulnerability. The White House tried to start addressing this problem last year, requiring a “software bill of materials” for government software:
…the term “Software Bill of Materials” or “SBOM” means a formal record containing the details and supply chain relationships of various components used in building software. Software developers and vendors often create products by assembling existing open source and commercial software components. The SBOM enumerates these components in a product. It is analogous to a list of ingredients on food packaging. An SBOM is useful to those who develop or manufacture software, those who select or purchase software, and those who operate software. Developers often use available open source and third-party software components to create a product; an SBOM allows the builder to make sure those components are up to date and to respond quickly to new vulnerabilities. Buyers can use an SBOM to perform vulnerability or license analysis, both of which can be used to evaluate risk in a product. Those who operate software can use SBOMs to quickly and easily determine whether they are at potential risk of a newly discovered vulnerability. A widely used, machine-readable SBOM format allows for greater benefits through automation and tool integration. The SBOMs gain greater value when collectively stored in a repository that can be easily queried by other applications and systems. Understanding the supply chain of software, obtaining an SBOM, and using it to analyze known vulnerabilities are crucial in managing risk.
It’s not a solution, but it’s a start.
EDITED TO ADD (3/22): Brian Krebs on protestware.
Russian Cyber Attacks Are Struggling To Impact Ukraine's Networks
Maxim BangeI find the second half to be the most interesting
Read more of this story at Slashdot.
Why Vaccine Cards Are So Easily Forged
My proof of COVID-19 vaccination is recorded on an easy-to-forge paper card. With little trouble, I could print a blank form, fill it out, and snap a photo. Small imperfections wouldn’t pose any problem; you can’t see whether the paper’s weight is right in a digital image. When I fly internationally, I have to show a negative COVID-19 test result. That, too, would be easy to fake. I could change the date on an old test, or put my name on someone else’s test, or even just make something up on my computer. After all, there’s no standard format for test results; airlines accept anything that looks plausible.
After a career spent in cybersecurity, this is just how my mind works: I find vulnerabilities in everything I see. When it comes to the measures intended to keep us safe from COVID-19, I don’t even have to look very hard. But I’m not alarmed. The fact that these measures are flawed is precisely why they’re going to be so helpful in getting us past the pandemic.
Back in 2003, at the height of our collective terrorism panic, I coined the term security theater to describe measures that look like they’re doing something but aren’t. We did a lot of security theater back then: ID checks to get into buildings, even though terrorists have IDs; random bag searches in subway stations, forcing terrorists to walk to the next station; airport bans on containers with more than 3.4 ounces of liquid, which can be recombined into larger bottles on the other side of security. At first glance, asking people for photos of easily forged pieces of paper or printouts of readily faked test results might look like the same sort of security theater. There’s an important difference, though, between the most effective strategies for preventing terrorism and those for preventing COVID-19 transmission.
Security measures fail in one of two ways: Either they can’t stop a bad actor from doing a bad thing, or they block an innocent person from doing an innocuous thing. Sometimes one is more important than the other. When it comes to attacks that have catastrophic effects—say, launching nuclear missiles—we want the security to stop all bad actors, even at the expense of usability. But when we’re talking about milder attacks, the balance is less obvious. Sure, banks want credit cards to be impervious to fraud, but if the security measures also regularly prevent us from using our own credit cards, we would rebel and banks would lose money. So banks often put ease of use ahead of security.
That’s how we should think about COVID-19 vaccine cards and test documentation. We’re not looking for perfection. If most everyone follows the rules and doesn’t cheat, we win. Making these systems easy to use is the priority. The alternative just isn’t worth it.
I design computer security systems for a living. Given the challenge, I could design a system of vaccine and test verification that makes cheating very hard. I could issue cards that are as unforgeable as passports, or create phone apps that are linked to highly secure centralized databases. I could build a massive surveillance apparatus and enforce the sorts of strict containment measures used in China’s zero-COVID-19 policy. But the costs—in money, in liberty, in privacy—are too high. We can get most of the benefits with some pieces of paper and broad, but not universal, compliance with the rules.
It also helps that many of the people who break the rules are so very bad at it. Every story of someone getting arrested for faking a vaccine card, or selling a fake, makes it less likely that the next person will cheat. Every traveler arrested for faking a COVID-19 test does the same thing. When a famous athlete such as Novak Djokovic gets caught lying about his past COVID-19 diagnosis when trying to enter Australia, others conclude that they shouldn’t try lying themselves.
Our goal should be to impose the best policies that we can, given the trade-offs. The small number of cheaters isn’t going to be a public-health problem. I don’t even care if they feel smug about cheating the system. The system is resilient; it can withstand some cheating.
Last month, I visited New York City, where restrictions that are now being lifted were then still in effect. Every restaurant and cocktail bar I went to verified the photo of my vaccine card that I keep on my phone, and at least pretended to compare the name on that card with the one on my photo ID. I felt a lot safer in those restaurants because of that security theater, even if a few of my fellow patrons cheated.
This essay previously appeared in the Atlantic.
Update 18 – IAEA Director General Statement on Situation in Ukraine
Using Radar to Read Body Language
Yet another method of surveillance:
Radar can detect you moving closer to a computer and entering its personal space. This might mean the computer can then choose to perform certain actions, like booting up the screen without requiring you to press a button. This kind of interaction already exists in current Google Nest smart displays, though instead of radar, Google employs ultrasonic sound waves to measure a person’s distance from the device. When a Nest Hub notices you’re moving closer, it highlights current reminders, calendar events, or other important notifications.
Proximity alone isn’t enough. What if you just ended up walking past the machine and looking in a different direction? To solve this, Soli can capture greater subtleties in movements and gestures, such as body orientation, the pathway you might be taking, and the direction your head is facing — aided by machine learning algorithms that further refine the data. All this rich radar information helps it better guess if you are indeed about to start an interaction with the device, and what the type of engagement might be.
[…]
The ATAP team chose to use radar because it’s one of the more privacy-friendly methods of gathering rich spatial data. (It also has really low latency, works in the dark, and external factors like sound or temperature don’t affect it.) Unlike a camera, radar doesn’t capture and store distinguishable images of your body, your face, or other means of identification. “It’s more like an advanced motion sensor,” Giusti says. Soli has a detectable range of around 9 feet — less than most cameras — but multiple gadgets in your home with the Soli sensor could effectively blanket your space and create an effective mesh network for tracking your whereabouts in a home.
“Privacy-friendly” is a relative term.
These technologies are coming. They’re going to be an essential part of the Internet of Things.
Elk dorp Noordoostpolder krijgt luiercontainer
Elk dorp in de Noordoostpolder krijgt een inzamelpunt voor gebruikte luiers. In Emmeloord komen in totaal vijf inzamelpunten.
De gemeente hoopt zo te voorkomen dat inwoners van de verschillende dorpen soms meer dan tien kilometer moeten reizen met hun vieze luiers, meldt Omroep Flevoland. Bij veel mensen leidt dat tot 'luierschaamte', zij vinden het vervelend om met luiers over straat te moeten.
Het probleem in de Noordoostpolder ontstond 1 januari. Tot die tijd mochten gebruikte luiers in de bak voor gft-afval. Maar omdat er plastic in zit moeten ze met ingang van dit jaar bij het restafval. Dat leidde tot gemor onder de inwoners: in de Noordoostpolder moet per containerleging worden betaald en containers zijn een stuk sneller vol met al die luiers.
Gratis luiers dumpen
Aanvankelijk dacht de gemeente goed te doen door een luiercontainer bij de gemeentewerf te plaatsen, waar je gratis je gebruikte luiers kunt dumpen. Maar voor de inwoners van Bant (zeven kilometer van Emmeloord) Marknesse (acht kilometer), Ens en Nagele (allebei op elf kilometer), alsmede voor een aantal wijken van Emmeloord zelf, bleek dat geen oplossing.
Vandaar dat er nu vijftien luiercontainers bij komen op, wat de gemeente noemt "voor de hand liggende locaties die zo veel mogelijk aansluiten bij bestaande inzamelpunten". De eerste vijf containers worden nog deze maand in de dorpen geplaatst. De overige tien staan er in juli van dit jaar.
Tijdelijke oplossing
De gemeente benadrukt dat het om een tijdelijke oplossing gaat. Er zijn al goede technieken om luiers te recyclen, het ontbreekt alleen aan de capaciteit om dat overal in Nederland al te doen. De verwachting is dat dat over twee jaar wel kan.
Wartime Is a Bad Time To Mess With the Internet
Maxim BangeHear, hear
Like most people, we at EFF are horrified by Russia’s invasion of Ukraine. Also like most people, we are not experts on military strategy or international diplomacy. But we do have some expertise with the internet and civil liberties, which is why we are deeply concerned that governments around the world are pressuring internet companies to interfere with fundamental internet infrastructure. Tinkering with the internet as part of a political or military response is likely to backfire in multiple ways.
There is already heavy pressure on social media platforms. Russia is demanding that various companies from Facebook to Google and Netflix carry its state-sponsored content. The European Union, in an unprecedented move, has decided to prohibit the broadcasting and distribution of content by these outlets throughout the European Union, and Ukraine is asking the European Commission to do far more.
But now the government of Ukraine has called on ICANN to disconnect Russia from the internet by revoking its Top Level domain names, “.ru”, “.рф” and “.su” from the root zone, in an attempt to make access to Russian websites and email difficult for people outside as well as inside of Russia. Ukraine also reached out to RIPE, one of the five Regional Registries for Europe, the Middle East and parts of Central Asia, asking the organization to revoke IP address delegation to Russia.
As a practical matter, some of these calls are essentially impossible; ICANN can’t just press a button and boot a country offline; RIPE can’t just revoke IP addresses. But those are not the only problems: remaking fundamental internet infrastructure protocols is likely to lead to a host of dangerous and long-lasting consequences.
Here are a few:
-
It deprives people of the most powerful tool for sharing information just when they need it most
While the internet can be used to spread misinformation, it also enables everyone, including activists, human right defenders, journalists and ordinary people, to document and share the real-time facts and resist propaganda. Indeed, Russia has reportedly been trying for years to “unplug” from the internet so it can completely control communications in the country. Internet providers shouldn’t help the Russian government, or any government, keep people within an information bubble.
-
It sets a dangerous precedent
Intervention pathways, once established, will provide state and state-sponsored actors with additional tools for controlling public dialogue. Once processes and tools to take down expression are developed or expanded, companies can expect a flood of demands to apply them, inevitably to speech those tools were not originally designed, and the companies did not originally intend, to target. At the platform level, state and state-sponsored actors have long since weaponized flagging tools to silence dissent.
-
It compromises security and privacy for everyone
Any attempt to compromise the internet’s infrastructure will affect the security of the internet and its users. For example, revocation of IP addresses means that things like the Routing Policy Specification Language (RPSL), used by ISPs to describe their routing policies, and Resource Public Key Infrastructure (RPKI), which is used to improve the security for the internet’s BGP routing infrastructure, would be severely compromised. This would expose users to man-in-the-middle attacks, compromise daily activities like bank transactions, and undermine the privacy because users would have nowhere to hide.
-
It undermines trust in the network and the policies upon which it is built
Trust is paramount to the way networks self-organize and interoperate with other networks. It is what ensures a resilient global communications infrastructure that can withstand pandemics and wars. That trust depends, in turn, on imperfect but painstaking multi-stakeholder processes to develop neutral policies, rules, and institutional mechanisms. Bypassing those mechanisms irretrievably undermines the trust upon which the internet is founded.
We were relieved to see that ICANN and RIPE have declined to comply with the Ukrainian government’s requests, and we hope other infrastructure organizations follow suit. In moments of crisis, we are often tempted to take previously unthinkable steps. We should resist that temptation here, and take proposals like these off the table altogether. In dark times, people must be able to reach the light, reassure their loved ones, inform themselves and others, and escape the walls of propaganda and censorship. The internet is a crucial tool for all of that – don’t mess with it.
Henny Youngman
‘NO TO WAR’: Russian fury bursts open as Putin bombards Ukraine
MOSCOW — On Tuesday, communist parliamentarian Mikhail Matveyev voted in favor of a proposal paving the way for a Russian “peacekeeping” mission in eastern Ukraine.
Only four days later he made a U-turn аnd said “No” — no to Russia’s war against Ukraine.
“The war should be stopped immediately. When I voted to recognize the Donetsk and Luhansk People’s Republics I voted for peace, not war,” he wrote Saturday on social media, a reference to the ever-so-thin pretext Russian President Vladimir Putin used to launch an all-out war on his neighbor.
Matveyev had voted to recognize the breakaway regions’ independence, he claimed, just to protect the eastern Ukraine Donbass region. “For Russia to act as a shield so that they wouldn’t bomb Donbass,” he said, “not so that Kyiv would be bombed.”
Yet, that’s exactly what has happened.
In today’s Russia, the State Duma exists less to hold the Kremlin to account and more to act as a conduit for decisions taken from above while keeping up a semblance of democracy for the outside world.
For a Duma member to publicly backtrack and criticize a weighty decision in this way is highly unusual — especially when that decision has come straight from Vladimir Putin’s office.
But Matveyev’s post hasn’t been the only surprise in recent days.
Even as the Kremlin has made a show of the supposed political consensus around its “special military operation” to “demilitarize” and “denazify” Ukraine, Russian civil society is exposing the cracks. Since last week there have been spontaneous protests in dozens of cities throughout Russia — from the north, to the Urals, to Siberia — attended by thousands of outraged Russians.
Though that constitutes only a fraction of Russia’s 140-million strong population, the turnout is nonetheless significant considering the context — “after a year in which the protests against the jailing of Alexei Navalny were crushed with violence, and the opposition was either jailed or forced out of the country, completely demoralizing any opposition,” said political analyst and former Kremlin speechwriter Abbas Gallyamov.
The crackdown had pushed Russia’s psychological threshold to protest ever higher, to an almost impossible height.
That is, until Russia went to war with Ukraine.
“The repulsion I feel is so strong, it feels as if a war has been declared against me personally,” said Alexander, a 34-year-old Muscovite who, like many Russians, has Ukrainian roots and signed an anti-war petition.
“That which is happening now is like my worst childhood nightmare,” added a 35-year-old female academic who asked to remain anonymous so as to speak freely and who attended an anti-war protest in St. Petersburg on February 24, the day Putin announced in an early-morning address that he saw “no option” but to enter Ukraine.
She recalled the lyrics of a song from her youth about the German bombardment of Kyiv in 1941: “Kyiv was bombed, we were told it was the beginning of war.”
“We always thought something like that could never happen again,” she said. “But now when I look up at the blue sky, all I can think about is that the impossible has happened.”
A similar feeling of anger, shame and disbelief seems to have lit a fuse under Russia’s usually passive society.
Scores of celebrities from all spheres of life have spoken out. Russian tennis player Andrei Rublyоv wrote, “No war please,” on a camera lens after winning a match in Dubai. Rapper Oxxxymiron canceled several sold-out shows, calling the war “a catastrophe and a crime” in a video and claiming now was not the time for entertainment.
And comedian Ivan Urgant, Russia’s Stephen Colbert, on Thursday posted a black square on Instagram, captioned “Fear and pain. NO TO WAR,” sparking a flurry of speculation his show had been canceled by state television’s Channel One since it has not been on air since.
They are among dozens of other influential or well-respected public figures who have made their anti-war position clear, including people who until now were considered apolitical, or even in the pro-Kremlin camp.
On Sunday, one of Russia’s richest billionaires Mikhail Fridman called for the “bloodshed to end,” the Financial Times reported, citing a letter he wrote to his staff.
“My country is committing a horrible crime in Ukraine that can have no justification,” Sergei Utkin, the respected head of the state-linked International Relations Institute of the Russian Academy of Sciences, wrote on Twitter.
“We all bear part of the responsibility,” he added. “There is no good way out of that.”
Even Liza Peskova, the daughter of Putin’s spokesman Dmitry Peskov — who, like many of the offspring of Russia’s elite, lives in Europe — on Friday shared an image of the “No to war” hashtag on her Instagram stories. (The message was quickly deleted.)
There have also been dozens of anti-war petitions and open letters, often organized by professionals — teachers, scientists, architects, cultural figures, IT workers, just to name a few.
Another general anti-war petition was heading toward 1 million signatures on Sunday.
“Russia’s official rhetoric claims that this is being done in self-defense,” the letter said. “But history cannot be fooled.”
The letter even nodded to the Nazis’ rise, referencing a fire Adolf Hitler used as false justification to lock up his political opponents: “The burning of the Reichstag arson was exposed, and today no exposures are needed — everything is obvious from the beginning.”
The political sphere has been a notable exception. While some local parliamentarians have denounced the war, at the national level, most lawmakers still parrot the Kremlin line or stay silent.
The only Duma member out of 400 to have voted against the initial proposal to recognize the separatist regions, Communist Oleg Smolin, was reported to have done so by mistake because of his impaired vision. He ended up voting in favor in a second voting round. Smolin did, however, later write a mea culpa, saying he had made a “wrong forecast” in failing to predict Russia would wage war in Ukraine and called for peace.
Cracking down
As Russia’s campaign in Ukraine drags on, and the initial shock increasingly turns to anger, the authorities are trying to prevent a snowball effect.
Some 2,000 people have been detained during anti-war protests, according to the police monitoring website OVD-Info.
The 35-year-old academic who told POLITICO about the war song was among them. On Monday, she joined hundreds of others at a protest in St. Petersburg, where the turnout has been the largest. She was soon detained and taken to a police station.
“There were 15 of us,” she said. “They took away our phones and held us in an enclosed space for 13 hours. It was too small for all of us to be able to sit at the same time, so many had to stand.” She was questioned by police who also took her fingerprints and mugshots.
When she eventually returned home almost 24 hours later, a judge had handed her a fine of 10,000 rubles — just over €100 — for participating in a large gathering that authorities claimed had violated COVID restrictions.
In Russia, where about 120,000 new coronavirus cases are recorded every day, there are hardly any restrictions in public life. Nonetheless, the pandemic has been used as a useful pretext to ban anti-Kremlin protests and prosecute those speaking out.
On Sunday, Russian prosecutors warned that “every instance of financial or other aid to a foreign state and activity aimed against Russia’s national security,” could be considered treason and punishable with a sentence of up to 20 years in prison.
Aside from arrest, there are other ways of cajoling Russians into silence, echoing a Soviet-era system of formal and informal pressures.
On Saturday, Yekaterina Dolinina, the director of the film organization Moskino, said she had been told to resign after she put her name under an anti-war petition signed by more than 4,000 cultural figures.
And a prominent journalist for the business paper Kommersant, Elena Chernenko, was expelled from the diplomatic press pool after she gathered more than 300 signatures under a short statement on Telegram reading: “War has never been and will never be a method of conflict resolution and there are no excuses for it.”
Russia’s independent media outlets feature heavily on the list, but many of the names also belong to local journalists and even some state media employees.
Chernenko said she had been banned “for unprofessionalism.”
Propaganda machine in full flow
Her expulsion shows how sensitive the Russian authorities are about the information sphere. Russia’s propaganda machine has been working overtime to present a view of events that stipulates Russia’s incursion on Ukraine is limited to the east of the country and does not affect civilians. Any questioning of, or alternatives to, that narrative are quashed.
On Saturday, Russia’s media watchdog Roskomnadzor threatened 10 independent media outlets with closure for not sticking to a new rule that bans the use of the word “war” to describe Russia’s war in Ukraine. Twitter and Facebook also have been partly blocked.
“Without a doubt, there is a level of insecurity [among the authorities] that without such measures they will not succeed,” said Gallyamov, the analyst. “Simply deceiving people has not worked, so they have to be prohibited from thinking for themselves with the help of the administrative apparatus.”
Different polls suggest that more than half of the Russian population blames the West for the escalation, and a similar share supports the use of force to keep Ukraine from joining NATO, even though Ukraine’s membership is merely a distant prospect. In a CNN poll, 36 percent of respondents said they supported the use of military force to “reunite Russia and Ukraine.”
“Russian society is divided on this question,” Gallyamov said. He said the coming days would play a defining role.
“The thinking will be: If we win, then we must be right,” he said. “But if we fail to win, every day of the war is costing Putin a few percent of his rating. Another week of this slaughter, and you can say that the conditions for a serious questioning of his legitimacy will be in place.”
Meanwhile, unable to deny the anti-war sentiment altogether, the Kremlin has done its best to dismiss it as marginal.
“The president hears the opinion of everyone, and is aware of the proportion of those who have an alternative point of view, and those who view this necessary operation with understanding,” Peskov, Putin’s spokesman, said on Friday.
And for those who don’t understand it?
“We must do better at explaining it to them,” Peskov said, ”that is absolutely clear.”
“Friends” Leaving Netflix Caused a Piracy Spike in The Netherlands
 For online media consumers, things have improved significantly over the years. More content is made available globally than ever before.
For online media consumers, things have improved significantly over the years. More content is made available globally than ever before.
In today’s on-demand society this is particularly important for new content. A geographical delay of a few days can be sufficient to drive some people to pirate sites.
“Friends” Pirates
Availability is not only important for new releases though as iconic movies and TV shows always stay in high demand. This also applies to the iconic sitcom “Friends,” which originally appeared on NBC between 1994 and 2004.
The series became a hit around the world and with the help of streaming services such as Netflix, it continues to entertain generations both old and new. That is, as long as they still have access.
Due to rights issues, streaming platforms occasionally have to pull content. In the Netherlands, this was also the case for “Friends” which left the streaming platform on December 30th of last year.
No Alternative
Adding to the trouble is the fact that there are no legal streaming alternatives to watch the series on-demand. At least not legally. The only option people have is to use pirate sites. And according to data gathered by TorrentFreak, many people do so.
Today most pirates use unauthorized streaming sites to watch content illegally. This traffic can’t be measured publicly, so we decided to focus on BitTorrent downloads instead, assuming that this is a good proxy for the overall interest on pirate sites.
Our data sample includes torrent piracy activity in the Netherlands for “Friends” starting on December 1, 2021 and ending on January 31, 2022.
In addition to the estimated downloads, we also added the numbers from the neighboring country Belgium as a control group. In Belgium, “Friends” remained available on Netflix for the entire period.
Dutch Piracy Spike
The graph below shows the daily download numbers over time. The absolute numbers in our sample are relatively modest, a few hundred downloads per day, but you can clearly see that the piracy numbers more than quadrupled when “Friends” left Netflix in the Netherlands.
Friends downloads (torrents)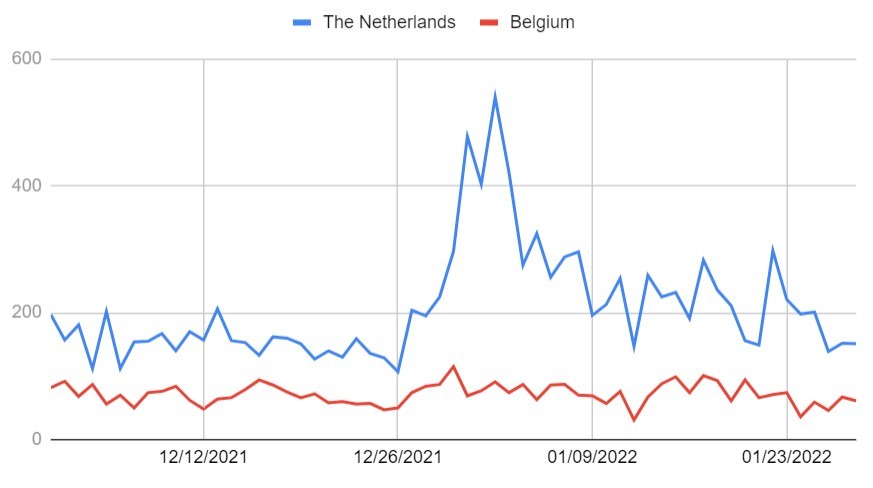
Full-season releases are counted as one download so the number of downloaded episodes is much higher. Also, BitTorrent traffic is only a small fraction of the total piracy ecosystem, and we expect that thousands of others turned to pirate streaming sites to watch Friends.
This basic research confirms the impact that availability has on people’s motivation to pirate. That’s not just limited to new releases, but it equally applies to evergreen content.
While Hollywood might not immediately panic over a few thousand Friends downloads, this problem should not be disregarded. After all, some of these people may have used pirate sites for the first time. And once they know how it works…
From: TF, for the latest news on copyright battles, piracy and more.
New JAMA paper show Ivermectin blows the COVID vaccines out of the water
Maxim Bange@Remlaps: Do you Trust this? I do not.
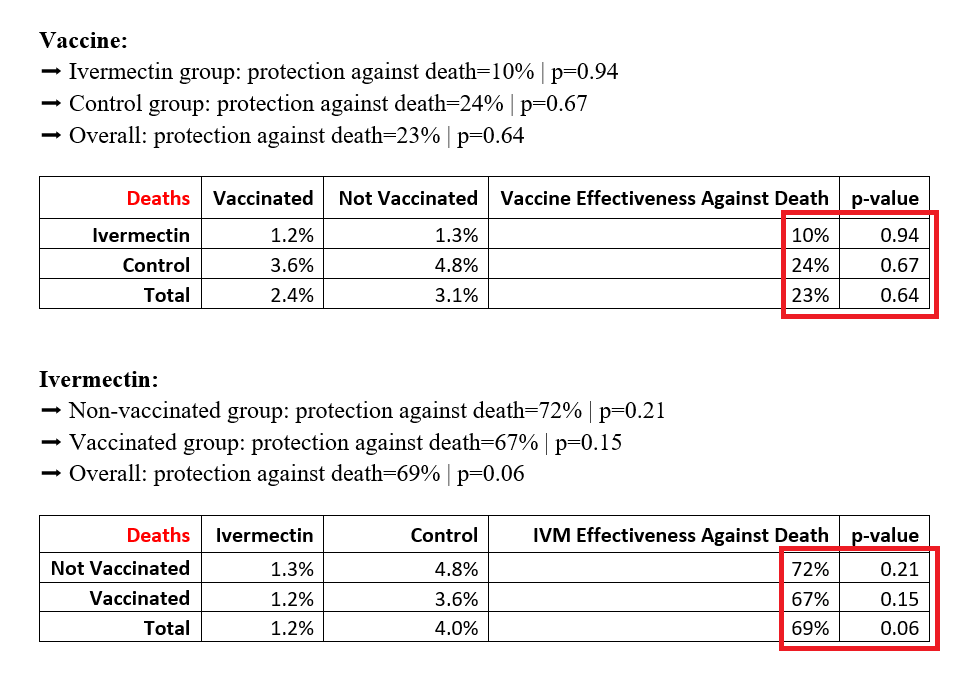
Remember that “horse dewormer” that the FDA, CDC, NIH, CNN, and Sanjay Gupta all told you not to use? A new paper recently published in the Journal of the AMA (JAMA) shows that Ivermectin works way better than the COVID vaccine in keeping you from dying from COVID.
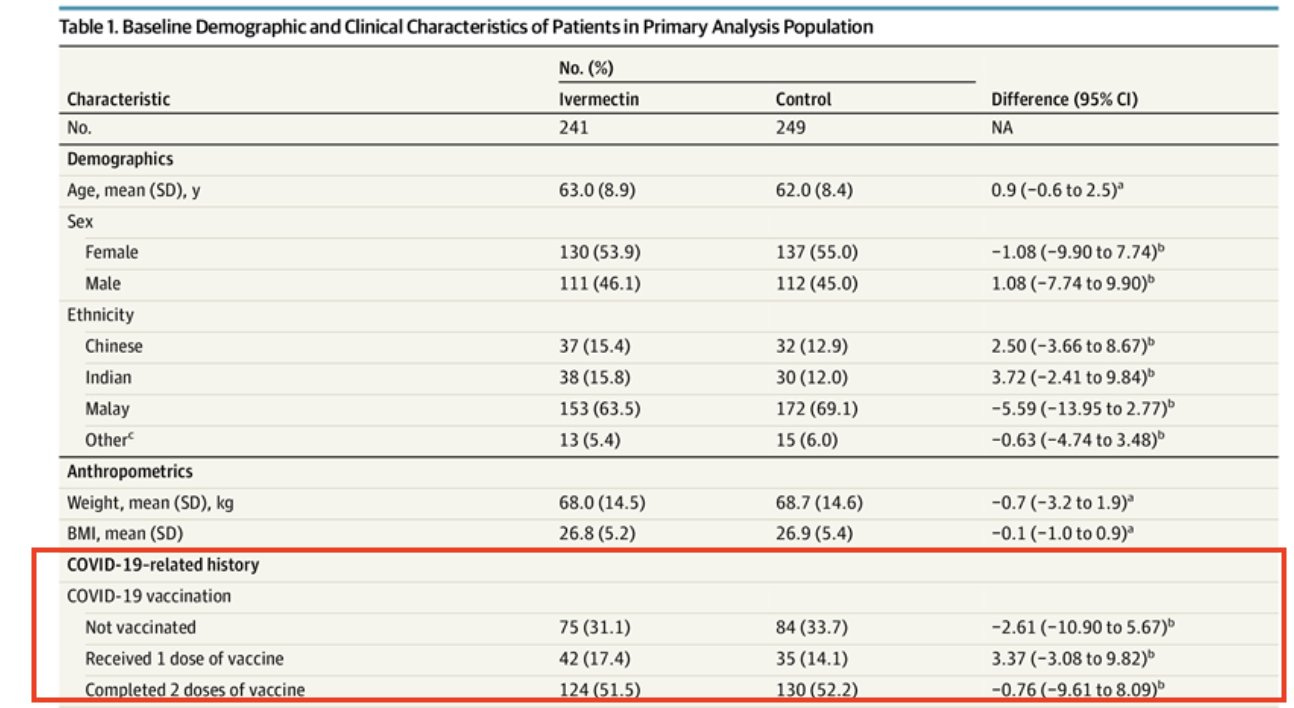
This was an open-label randomized trial done in Malaysia with around 250 patients in each arm. One arm got IVM + standard of care, the other arm got the standard of care.
Of course, JAMA never would have published this if they thought that people would actually look at the data. The abstract says: “The study findings do not support the use of ivermectin for patients with COVID-19.” You are supposed to read the abstract and believe that ivermectin has no effect.
In fact, that’s exactly what people do even when you tell them expressly to ignore that:
Do not fall for it. Read the paper if you want the truth. If you want to be misled, just read the abstract.
Pierre Kory did a brilliant takedown of the paper on his substack. I won’t repeat that here. Instead, I’ll just summarize the data for you; the hidden gems in the paper that you are never supposed to notice.
The data
The lower the p-value, the more significant the result is. A Chi-squared test was used. Data came from the JAMA paper appendix.
Interpretation of the data
So there are five takeaways from the study:
Vaccine efficacy in the real world is quite small. If you got vaccinated, it reduced your chance of death by just 24%. However, the study did NOT look at the all-cause mortality of the vaccine (it only enrolled people who survived the vaccine), so the tiny absolute risk reduction you get from a 24% relative risk reduction (roughly 24% of .25% =.06% benefit) is less than the absolute risk of dying from the vaccine (around .2%). See Incriminating Evidence for details on this.
If you were not vaccinated (which you shouldn’t be), ivermectin reduced your chance of death by 72%. So it was 3 times more effective than the vaccine. But the risk of ivermectin is negligible so the risk-benefit ratio is extremely favorable. Ivermectin has a 3X effect size (benefit) and is more than 100,000X less risky with respect to death risk, killing nobody (compared to over 200,000 people from the vaccine). So it’s the clear choice. It’s the only rational choice.
The vaccine did provide a SMALL incremental benefit if you took both (10% lower risk), but it’s a non-starter since the risk-benefit analysis doesn’t support ever using the vaccine.
If we want to reduce deaths, ivermectin is the way to go. Avoid the vaccine entirely.
There is no way you have a paper like this with 431,000 views and just two comments. This implies that virtually all the comments were counter-narrative and were censored from public view. That in itself is stunning.
Note that multidrug protocols that use ivermectin are much better than ivermectin alone. For example, the Fareed Tyson protocol has treated 10,000 people with no deaths, whereas in this study, 1 of the 75 unvaccinated people who got ivermectin died (1.3%). Multidrug protocols are clearly the way to go.
Acknowledgment
I want to thank Massimaux for highlighting what the study said in his tweet.
 Massimaux @masimaux
Massimaux @masimaux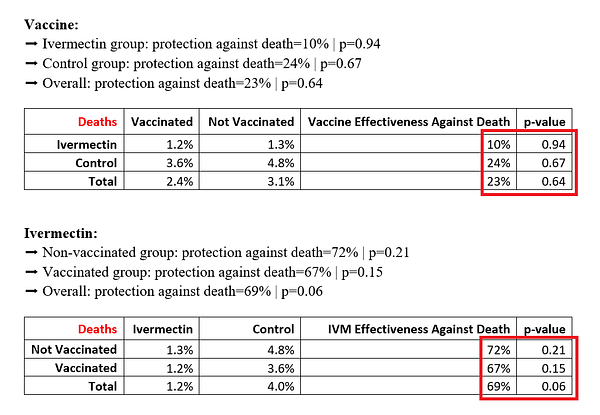
February 20th 2022
11 Retweets17 LikesSummary
It doesn’t get much better than this. A paper published in JAMA showing ivermectin is three times better than the vaccines in preventing death. Combined with the risk data of the vaccines, it’s clear that if you are given a choice, you’d always choose ivermectin and never choose the vaccine.
Will this paper make a difference? I don’t think so.
Ruby On Rails Creator Backpedals About Bitcoin: 'We Need Crypto'
Read more of this story at Slashdot.
Victor Borge
Satellite images show just how ridiculously high the Tonga volcanic plume rose

The volcanic eruption that rocked the Pacific island nation of Tonga in January was so powerful it blasted ash all the way up to the mesosphere, the third and coldest layer of Earth’s atmosphere. Rising 58 kilometers (36 miles) above Earth, the volcanic plume was likely the tallest ever measured by satellite, according to NASA.
NASA was able to measure the plume because two weather satellites happened to be in the right place at the right time. Those satellites took still images and infrared observations that give a play-by-play of the eruption from above.
In just 30 minutes or so following the eruption, ash, steam, and gas from the underwater volcano rose from the surface of the ocean all the way up to the mesosphere. A second blast...
Wordle Is Watching You
Read more of this story at Slashdot.
'A Hacker Group Has Been Framing People for Crimes They Didn't Commit'
Read more of this story at Slashdot.
Study Finds Link Between Alzheimer's and Circadian Clock
Read more of this story at Slashdot.
Posting Directly From My Feed Reader To My Blog
Maxim BangeHi Ton, Unclear if you'll be reading this but I love your posts. Your current project reminds my of an old love I had, Google Reader :-)
Cheers
Today I posted a bookmark directly to this blog, straight from a feed reader I created myself. A few days ago I already posted about how I am building a Microsub client, which basically is the front-end of a feed reader: it’s the part where you actually read the content from the RSS feeds you subscribe to. It does not in itself subscribe to any feeds, or store what it gets from those feeds. That’s the Microsub server, and I use an existing WordPress plugin called Yarns for it. By splitting the server (subscribing, fetching and storing) from the client (presenting), making the feed reader becomes building a website that can show me whatever is stored in the server. It makes it possible to shape my feed reader the way I want it. I had the basic fetching and presenting part done earlier this week. The next step was interacting with the things I read from within the reader, having a reply button underneath each posting, with which I can post to this blog. I’ve got that part working now too. To build it I re-used things I previously already created. For instance I already had a form, to formulate a response (originally stuck on the back-end of another feedreader), and a way of posting directly to this site. So adding this was more a remix than coding something new. The only new additions were the ‘glue’ needed to join the existing parts together, and a bit of Javascript to be able to process the form in the browser, while staying on the same page as where I’m reading feeds. And it works!
Here’s a posting by Peter, as presented in my feed reader:
Note the button underneath which says in Dutch ‘respond to the post above’. Each posting has a button like that.
Clicking such a button reveals a form (which is at first hidden, and revealed by a line of Javascript).
In the form I specify what type of response it is (reply, bookmark, or favourite), and I write my reaction, and can add a quote from the article above which is useful if I’m responding to something specific, and provides context for readers on my own site who aren’t aware of the posting I’m responding to. It also allows me to change the title, author name and URL of the original post. This sometimes is useful when the title is very long, the name in the feed is a user name (e.g. ‘siteadmin’), or when the URL contains appended tracking elements that I want to remove.
Underneath is another button saying ‘Process’ in Dutch.
Hitting that button activates a little bit of Javascript to call the PHP script that processes the form, without leaving the page. It means that once I’ve clicked the button I can go on reading in the same page. The script that silently processes the form, turns what I’ve submitted into proper HTML for a posting, and then sends it on to my blog. Where it ends up as:
On my blog you get to see what the processing script has created, including e.g. the icon for a bookmark (or reply or favourite).
I’m pleased with how this works now, and I can start adding a few things. Like adding optional titles to a reaction (as I’ve done in this posting), or to add multiple tags or categories. For these too I have existing code sections I can re-use. Another element is being able to subcribe, unsubscribe and mark things as read from within the Microsub client.
After that it will become more difficult, if I want to work down my list of things an ideal feed reader should be capable of.
Part of that may require storing feed items client side, or maybe even also building my own Microsub server. So it’s a potential rabbithole I want to approach with caution. For now I will try this as my new workflow for a week or two.