Submitted by: (via Neatorama)
Shared posts
Cough and sneeze into elbows, not hands

NSW Health authorities should withdraw advertisements urging people to cover their coughs and sneezes with their hands and instead tell people to use their inner elbow, according to a letter to the editor published in the Medical Journal of Australia today.
In his letter, University of Sydney Associate Professor of Surgery and Cancer Guy Eslick said covering a cough or a sneeze with the hands was more likely to spread cold and flu germs around than prevent infection of others. He used the example of a 2012 New South Wales Health poster (pictured above) that depicts a person sneezing into their hands.
Dr Guy Eslick said he was prompted to write the letter by warnings that this flu season will be particularly bad and by the need for public education.
“When living in Boston at the height of the H1N1 pandemic, at her childcare centre, my daughter was being taught to sneeze into her sleeve, not into her hands, and coming home showing me how it was done,” he said.
“When I got back to Sydney, I was on a bus and saw these posters showing a person coughing into their hands.
“I hope New South Wales Health will change the image on their posters to be more in line with CDC [US Center for Disease Control] recommendations.”

The Minnesota Department of Health poster (left) is a good example, he said.
“I’m also hoping it might get discussion going within the community about optimal ways to stop flu spreading.”
A NSW Department of Health spokesperson said its annual flu campaign was aimed at reducing the spread and severity of the illness, and the posters were only designed to provide a reminder to people about the main messages.
“The cartoon icon of the person coughing was not meant to be an instruction of how to cough safely,” the spokesperson said.
The campaign is revised annually to include the most current flu advice from Australia and around the world, the spokesperson said. The 2013 campaign will recommend people cover coughs and sneezes with a tissue and then dispose of it, or if that’s not possible, to cough into their elbow.
Professor Lindsay Grayson, Director of Hand Hygiene Australia and Director of Infectious Diseases at Austin Health, said the letter raised a reasonable point.
“We know hands are a major transmitter of influenza,” Professor Grayson said
Posters should depict a number of key messages, he said, including coughing into your elbow; ensuring hands are washed often, with soap and water or alcohol hand rub; avoiding handkerchiefs and using tissues, where possible; and staying home from work if you’re sick.
“Don’t be a martyr; you’ll just spread it,” he said.
hockey as she is played
| archive - contact - sexy exciting merchandise - cute - search - about | |||
 |
|||
| ← previous | May 14th, 2013 | next | |
|
May 14th, 2013: STILL BIG INTO TCAF OVER HERE. I just wanted to say thanks to everyone who came out and said hi - I met so many awesome people and it was terrific! In conclusion: YAY TCAF. One year ago today: medusa fan comix – Ryan 
| |||
#937; The Tramp Stamp of Advertising
Familiar Simpsons’ Names Found in Matt Groening’s Mother’s Obituary
Last month when the mother of Simpsons’ creator Matt Groening, Margaret (aka “Marge”), died, Portland newspaper The Oregonian published her obituary which was filled with names familiar to fans of the animated series. Last year, Matt revealed the namesake of the show’s fictional town of Springfield.
image via Yarrr_piratejackoff
Depression Part Two
I didn't understand why it was fun for me, it just was.
But as I grew older, it became harder and harder to access that expansive imaginary space that made my toys fun. I remember looking at them and feeling sort of frustrated and confused that things weren't the same.
I played out all the same story lines that had been fun before, but the meaning had disappeared. Horse's Big Space Adventure transformed into holding a plastic horse in the air, hoping it would somehow be enjoyable for me. Prehistoric Crazy-Bus Death Ride was just smashing a toy bus full of dinosaurs into the wall while feeling sort of bored and unfulfilled. I could no longer connect to my toys in a way that allowed me to participate in the experience.
Depression feels almost exactly like that, except about everything.
At first, though, the invulnerability that accompanied the detachment was exhilarating. At least as exhilarating as something can be without involving real emotions.
The beginning of my depression had been nothing but feelings, so the emotional deadening that followed was a welcome relief. I had always wanted to not give a fuck about anything. I viewed feelings as a weakness — annoying obstacles on my quest for total power over myself. And I finally didn't have to feel them anymore.
But my experiences slowly flattened and blended together until it became obvious that there's a huge difference between not giving a fuck and not being able to give a fuck. Cognitively, you might know that different things are happening to you, but they don't feel very different.
Which leads to horrible, soul-decaying boredom.
I tried to get out more, but most fun activities just left me existentially confused or frustrated with my inability to enjoy them.
Months oozed by, and I gradually came to accept that maybe enjoyment was not a thing I got to feel anymore. I didn't want anyone to know, though. I was still sort of uncomfortable about how bored and detached I felt around other people, and I was still holding out hope that the whole thing would spontaneously work itself out. As long as I could manage to not alienate anyone, everything might be okay!
However, I could no longer rely on genuine emotion to generate facial expressions, and when you have to spend every social interaction consciously manipulating your face into shapes that are only approximately the right ones, alienating people is inevitable.
Everyone noticed.
It's weird for people who still have feelings to be around depressed people. They try to help you have feelings again so things can go back to normal, and it's frustrating for them when that doesn't happen. From their perspective, it seems like there has got to be some untapped source of happiness within you that you've simply lost track of, and if you could just see how beautiful things are...
At first, I'd try to explain that it's not really negativity or sadness anymore, it's more just this detached, meaningless fog where you can't feel anything about anything — even the things you love, even fun things — and you're horribly bored and lonely, but since you've lost your ability to connect with any of the things that would normally make you feel less bored and lonely, you're stuck in the boring, lonely, meaningless void without anything to distract you from how boring, lonely, and meaningless it is.
But people want to help. So they try harder to make you feel hopeful and positive about the situation. You explain it again, hoping they'll try a less hope-centric approach, but re-explaining your total inability to experience joy inevitably sounds kind of negative; like maybe you WANT to be depressed. The positivity starts coming out in a spray — a giant, desperate happiness sprinkler pointed directly at your face. And it keeps going like that until you're having this weird argument where you're trying to convince the person that you are far too hopeless for hope just so they'll give up on their optimism crusade and let you go back to feeling bored and lonely by yourself.
And that's the most frustrating thing about depression. It isn't always something you can fight back against with hope. It isn't even something — it's nothing. And you can't combat nothing. You can't fill it up. You can't cover it. It's just there, pulling the meaning out of everything. That being the case, all the hopeful, proactive solutions start to sound completely insane in contrast to the scope of the problem.
It would be like having a bunch of dead fish, but no one around you will acknowledge that the fish are dead. Instead, they offer to help you look for the fish or try to help you figure out why they disappeared.
The problem might not even have a solution. But you aren't necessarily looking for solutions. You're maybe just looking for someone to say "sorry about how dead your fish are" or "wow, those are super dead. I still like you, though."
I started spending more time alone.
Perhaps it was because I lacked the emotional depth necessary to panic, or maybe my predicament didn't feel dramatic enough to make me suspicious, but I somehow managed to convince myself that everything was still under my control right up until I noticed myself wishing that nothing loved me so I wouldn't feel obligated to keep existing.
It's a strange moment when you realize that you don't want to be alive anymore. If I had feelings, I'm sure I would have felt surprised. I have spent the vast majority of my life actively attempting to survive. Ever since my most distant single-celled ancestor squiggled into existence, there has been an unbroken chain of things that wanted to stick around.
Yet there I was, casually wishing that I could stop existing in the same way you'd want to leave an empty room or mute an unbearably repetitive noise.
That wasn't the worst part, though. The worst part was deciding to keep going.
When I say that deciding to not kill myself was the worst part, I should clarify that I don't mean it in a retrospective sense. From where I am now, it seems like a solid enough decision. But at the time, it felt like I had been dragging myself through the most miserable, endless wasteland, and — far in the distance — I had seen the promising glimmer of a slightly less miserable wasteland. And for just a moment, I thought maybe I'd be able to stop and rest. But as soon as I arrived at the border of the less miserable wasteland, I found out that I'd have to turn around and walk back the other way.
Soon afterward, I discovered that there's no tactful or comfortable way to inform other people that you might be suicidal. And there's definitely no way to ask for help casually.
I didn't want it to be a big deal. However, it's an alarming subject. Trying to be nonchalant about it just makes it weird for everyone.
I was also extremely ill-prepared for the position of comforting people. The things that seemed reassuring at the time weren't necessarily comforting for others.
The next few weeks were a haze of talking to relentlessly hopeful people about my feelings that didn't exist so I could be prescribed medication that might help me have them again.
And every direction was bullshit for a really long time, especially up. The absurdity of working so hard to continue doing something you don't like can be overwhelming. And the longer it takes to feel different, the more it starts to seem like everything might actually be hopeless bullshit.
My feelings did start to return eventually. But not all of them came back, and they didn't arrive symmetrically.
I had not been able to care for a very long time, and when I finally started being able to care about things again, I HATED them. But hatred is technically a feeling, and my brain latched onto it like a child learning a new word.
Hating everything made all the positivity and hope feel even more unpalatable. The syrupy, over-simplified optimism started to feel almost offensive.
Thankfully, I rediscovered crying just before I got sick of hating things. I call this emotion "crying" and not "sadness" because that's all it really was. Just crying for the sake of crying. My brain had partially learned how to be sad again, but it took the feeling out for a joy ride before it had learned how to use the brakes or steer.
At some point during this phase, I was crying on the kitchen floor for no reason. As was common practice during bouts of floor-crying, I was staring straight ahead at nothing in particular and feeling sort of weird about myself. Then, through the film of tears and nothingness, I spotted a tiny, shriveled piece of corn under the refrigerator.
I don't claim to know why this happened, but when I saw the piece of corn, something snapped. And then that thing twisted through a few permutations of logic that I don't understand, and produced the most confusing bout of uncontrollable, debilitating laughter that I have ever experienced.
I had absolutely no idea what was going on.
My brain had apparently been storing every unfelt scrap of happiness from the last nineteen months, and it had impulsively decided to unleash all of it at once in what would appear to be an act of vengeance.
That piece of corn is the funniest thing I have ever seen, and I cannot explain to anyone why it's funny. I don't even know why. If someone ever asks me "what was the exact moment where things started to feel slightly less shitty?" instead of telling a nice, heartwarming story about the support of the people who loved and believed in me, I'm going to have to tell them about the piece of corn. And then I'm going to have to try to explain that no, really, it was funny. Because, see, the way the corn was sitting on the floor... it was so alone... and it was just sitting there! And no matter how I explain it, I'll get the same, confused look. So maybe I'll try to show them the piece of corn - to see if they get it. They won't. Things will get even weirder.
Anyway, I wanted to end this on a hopeful, positive note, but, seeing as how my sense of hope and positivity is still shrouded in a thick layer of feeling like hope and positivity are bullshit, I'll just say this: Nobody can guarantee that it's going to be okay, but — and I don't know if this will be comforting to anyone else — the possibility exists that there's a piece of corn on a floor somewhere that will make you just as confused about why you are laughing as you have ever been about why you are depressed. And even if everything still seems like hopeless bullshit, maybe it's just pointless bullshit or weird bullshit or possibly not even bullshit.
now, back to our endless watching of romantic comedies
| archive - contact - sexy exciting merchandise - cute - search - about | |||
| dinosaur comics returns monday!
|
|||
| ← previous | April 25th, 2013 | next | |
|
April 25th, 2013: I wrote this comic in 2009, finalized it, and then got distracted and COMPLETELY FORGOT ABOUT IT. I happened across it now entirely by accident (I was searching for the phrase "little hearts" which appears in some cut lines to this comic!) So here is a KLASSIC KOMIC that you should've read over four years ago but you get to read it now. Thanks, past me! You were good at writing comics but bad at actually putting them where anyone else could ever see them. In other news, Squishable Utahraptor wants to live in your house! One year ago today: if you learn one thing from dinosaur comics, let it be that the cloaca is their shared digestive, urinary, and reproductive tract. – Ryan 
| |||
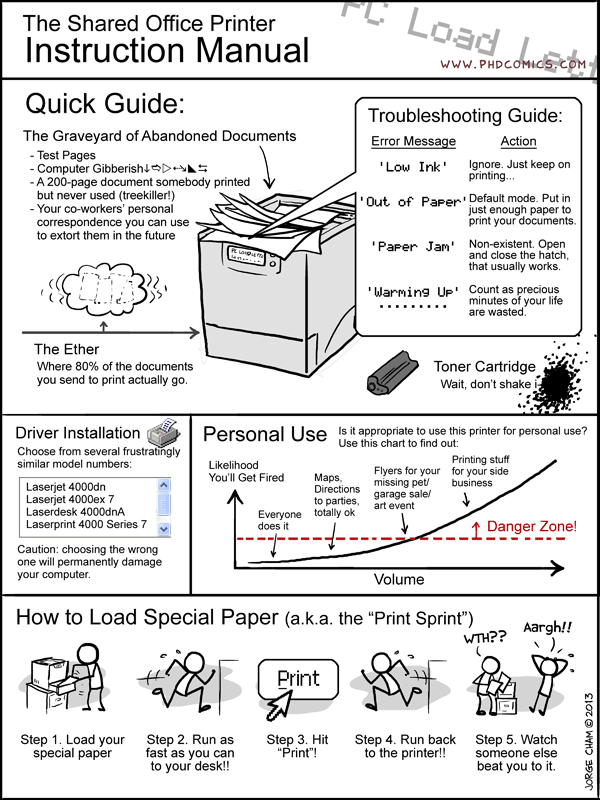
04/24/13 PHD comic: 'The Shared Office Printer'
| Piled Higher & Deeper by Jorge Cham |
www.phdcomics.com
|
|
 |
||
|
title:
"The Shared Office Printer" - originally published
4/24/2013
For the latest news in PHD Comics, CLICK HERE! |
||
RHETORIC AT 64% AND FALLING
| archive - contact - sexy exciting merchandise - cute - search - about | |||
 |
|||
| ← previous | April 24th, 2013 | next | |
|
April 24th, 2013: If you view source on this page and scroll waaaaay down you'll see a little surprise that comes courtesy of Ben! I've been posting a lot about the Adventure Time comic I write, but until now you couldn't read it online for free! THAT HAS ALL CHANGED, YO.. Also the sequel to Machine of Death, called This Is How You Die, is on the Publisher's Weekly Best Summer Books 2013 list! NICE. You can't get the book yet but it'll be available in July! I will be sure shout far and wide when it's available. – Ryan 
| |||
The Matasano Crypto Challenges
I recently took some time to work through the Matasano crypto challenges, a set of 48 practical programming exercises that Thomas Ptacek and his team at Matasano Security have developed as a kind of teaching tool (and baited hook).
Much of what I know (or think I know) about security has come from reading tptacek's comments on Hacker News, so I was intrigued when I first saw him mention the security challenges a few months ago. At the same time, I worried that I'd be way out of my depth attempting them.
As a programmer, my core strengths have always been knowing how to apologize to users, and composing funny tweets. While I can hook up a web template to a database and make the squigglies come out right, I cannot efficiently sort something for you on a whiteboard, or tell you where to get a monad. From my vantage point, crypto looms as high as Mount Olympus.
To my delight, though, I was able to get through the entire sequence. It took diligence, coffee, and a lot of graph paper, but the problems were tractable. And having completed them, I've become convinced that anyone whose job it is to run a production website should try them, particularly if you have no experience with application security.
Since the challenges aren't really documented anywhere, I wanted to describe what they're like in the hopes of persuading busy people to take the plunge.
You get the challenges in batches of eight by emailing cryptopals at Matasano, and solve them at your own pace, in the programming language of your choice. Once you finish a set, you send in the solutions and Sean unlocks the next eight. (Curiously, after the third set, Gmail started rejecting my tarball as malware.)
Most of the challenges take the form of practical attacks against common vulnerabilities, many of which will be sadly familiar to you from your own web apps. To keep things fun and fair for everyone, they ask you not to post the questions or answers online. (I cleared this post with Thomas to make sure it was spoiler-free.)
The challenges start with some basic string manipulation tasks, but after that they are grouped by theme. In most cases, you first implement something, then break it in several enlightening ways. The constructions you use will be familiar to any web programmer, but this may be the first time you have ever taken off the lid and looked at the moving parts inside.
Here are the cryptographic topics covered:
- basic substitution and XOR
- pseudo-random number generators
- stream and block ciphers, and their modes of operation
- message authentication codes
- Diffie-Hellman key exchange
- RSA (public-key cryptography)
Going into the challenges, I worried that my math wouldn't be up to the task. My impression of Serious Crypto was that it required all kinds of group theory, abstract algebra, elliptic curves, vector spaces, and other scary stuff. But while this may be true, the math content for the practical challenges was much gentler:
- working in base 2 and base 16
- modular arithmetic
- discrete exponentiation
- Hamming distance (& friends)
- primality testing
- basic stats (standard deviation & variance)
While the math concepts weren't hard, getting a real feel for them took work (and this was the point of the exercise).
If you're an experienced programmer, the Matasano challenges are also a terrific excuse to try a new programming language. It's always much more fun to solve real problems than it is to write a Manager object that inherits from Employee.
Here are the language features I found myself using most:
- string manipulation (ranges, substrings)
- bitwise operators
- lookup hashes
- conversion between string and number formats
- big integer operations
- packing and unpacking binary data
- pattern matching
- url manipulation
- client/server interaction over a socket
Altogether it took me about three weeks to do the full cycle, working pretty intensively. Skilled programmers will find the going much faster, especially if you're comfortable with bit twiddling. Very few of the problems were downright hard, though some required several hours of work. I spent most of my time stepping through algorithms in pursuit of bugs, and in the process really got a feel for the moving parts in various cryptographic constructions.
I would compare the experience to having only ever read cookbooks and watched cooking shows, and then being asked to fry an egg. You know exactly what to do... in principle.
Some of the challenges have a payoff, in that you decrypt a short bit of secret text. This is incredibly fun. Seeing a cracked message come up on the screen after an evening of bug chasing reminded me of how it felt to be a kid in front of my Apple ][, finally getting it to beep or draw a circle or print DONGS all over the screen. Some of the later challenges even display the answer 'Hollywood style', where you get to see it decrypt one letter at a time in a cascade of print statements.
While the rules don't stipulate it, I think it's a good idea not to look at anyone's code if you try the challenges. The goal here is to convert message-board levels of understanding into actual knowledge, and the only way that works is if you bang your head on the task without seeing how anyone else has done it. Sean was really helpful in helping me navigate difficult spots, and the challenges are not set up to intentionally trick you. But you will need the kind of graph paper with the small squares.
What surprised me most:
How practical these attacks were. A lot of stuff that I knew was weak in principle (like re-using a nonce or using a timestamp as a 'random' seed) turns out to be crackable within seconds by an art major writing crappy Python.
There is no difference, from the attacker's point of view, between gross and tiny errors. Both of them are equally exploitable. In at least three challenges, the mere fact of getting distinguishable error messages was enough to recover the entire message.
Timing attacks are much more effective than I imagined.
Someone who can muck with your ciphertext is halfway to reading it, possibly with your secret key for dessert.
Some mistakes are incredibly non-obvious. I had no idea you had to super-carefully pad RSA, for example.
Even on a laptop, in 10 minutes you can do a terrifying amount of computation. It really is 2013.
This lesson is very hard to internalize. In the real world, if you build a bookshelf and forget to tighten one of the screws all the way, it does not burn down your house
I mentioned earlier that I thought every web programmer should try their hand at these. It is very illuminating to look at your own web app from the vantage point of an attacker actually writing code. At the very least, you will never be confused about cipher block modes again, or have to worry that someone will ask you to explain how a public key works in an interview. And there is a whole slew of dumb mistakes you will now avoid (replacing them with smarter mistakes that will become the subject matter of challenges 48-96).
The best part, from a web app developer's perspective, is that you never once write a SQL statement or HTML tag.
Here are some specific lessons from the challenges that I will apply to my own work:
Keep meaningful data out of tokens (like cookies) that I hand out to clients. Use random values keyed against a database, memory store, or wherever.
If I have to put data in tokens, include an integrity check, and pay a real crypto person to vet it.
I must never seed a PRNG with a timestamp. I used to do this with microsecond precision thinking I was being clever. Then I went ahead and wrote a script that guessed the seed value in just a few seconds, and now I will never do that again.
Use constant-time string comparisons when testing incoming data against some target value for authentication purposes. This is easy enough to do in most languages to make it cheap insurance.
Anything related to authentication should only fail in one way. I must not provide distinguishable errors to the user.
If possible, find a way to log the fact that someone is making a lot of weird queries against my site. For extra points, try not to make the logger itself hackable.
No third-party javascript. I hated it already, now I hate it more.
Cut off one of my fingers each time I re-use a nonce.
Having read this post, you can go to Hacker News and comment in Talmudic detail about what is right or wrong in the conclusions I drew. But a much better idea is to just email Sean and have a crack at the challenges yourself. You will have a good time!
One final observation. Crypto is like catnip for programmers. It is hard to keep us away from it, because it's challenging and fun to play with. And programmers respond very badly to the insinuation that they're not clever enough to do something. We see the F-16 just sitting there, keys in the ignition, no one watching, lights blinking, ladder extended. And some infosec nerd is telling us we're can't climb in there, even though we just want to taxi around a little and we've totally read the manual.
Doing these challenges is a great way to 'shake your sillies out', as Raffi might say, without hurting yourself or your users. You get to put on the flight suit, climb into the simulator, and crash that plane in every conceivable way.
I would like to sincerely thank Thomas and Sean and everyone at Matasano who worked on these challenges, and implore people in other technical fields to consider offering something similar. It's the most fun I've had programming in years!
Cennydd Bowles on UX & Design: Hellish Other People
Childish, inaccurate, bizarre, and condescending? Perhaps—but you can’t just ignore articles like that. Tomas Chamorro-Premuzic’s Seven Rules for Managing Creative People1 has caused some serious ripples. The article sets lofty standards for missing the point, misrepresenting creative industries to the point of infantilization. At its nadir—“Creatives enjoy making simple things complex, rather than vice versa”—it ranks among the most baffling things ever written about creativity.
Commenters have heaped scorn on poor Chamorro-Premuzic, to the extent that I must almost apologize for adding to the criticism. But I’m intrigued by the views that prop up articles like this. Why do these misconceptions about creative work persist in an era of supposed innovative enlightenment?
The premise that underpins this and many similar articles is that creativity is a binary property: some people are blessed (or cursed) with it, others aren’t. This establishes a subtle, unwelcome construct. Creative types are “The Other”: fundamentally irregular people who don’t quite gel with the rest of society (“The Same”). Indeed, what it means to be Same is usually defined in part by not being Other.
While the language of Otherness is sometimes a deliberate tool of oppression, more often it reflects the unthinking bias of the speaker and era. Chamorro-Premuzic’s framing of creative people as The Other is no doubt unintentional. But the archetype is clear nonetheless.
Never, ever, ever let them call you a “creative”. It’s a way to be disenfranchised. You are a designer. It’s not magic, it’s a trade.
— Mike Monteiro (@Mike_FTW) April 7, 2013
On this stage, Chamorro-Premuzic plays the role of ethnographer. Having observed creative people in their natural environments, he uses the article to MBAsplain their aberrant behavior. Rather than recognizing the diverse individuality of creative workers, the author describes them as a homogenous group primarily defined by weakness—a motif that echoes throughout the history of Otherness.
Chamorro-Premuzic’s creative Other is self-centered and unable to play well with peers. He is “moody, erratic, eccentric, and arrogant.” He is unable to properly explain his process. His motivations are bizarre: money doesn’t matter to him, which at least gives you an opportunity to stiff him on pay. His neuroticism and narcissism make him a poor leader: that’s best left to the Sames.
Thankfully, the premise is flawed. Creativity is not a binary ability but a muscle that needs exercise. There is no Same and Other, no us and them; everyone has creative capacity. Personality, environment, and other pressures of life mean that some people do have less creative experience, but with simple tools—a pencil, a guitar, a hobby—it’s not hard to reverse the atrophy.
Modern creative work demands diverse perspectives. To suggest instead that it emanates from the abracadabras of an eccentric elite does a disservice to all parties. The article argues that companies should pass “trivial or meaningless work” to the clock-watchers who lack intrinsic motivation. In other words, some people are best handling the drudgery, while the unmanageables get the rewarding work to keep them quiet.
This situation, dare I say, could use some creative thinking. It can’t be healthy to encourage a cycle of disinterested employees and futile effort. Better to look closely at user needs, explore ideas that address them, and build a team that is inspired by those goals. Then no work should be meaningless.
So how can we counter the assertion that creative workers think and behave the same? By highlighting the diversity of our personalities and methods.
Both Mark Boulton and Chris Coyier have recently written about their introversion and how it affects their creative approaches. These are important, refreshing viewpoints, and no doubt many readers will identify with them. I too have noticed the subtle assumptions some people make about creative workers. Extraversion and arrogance are often presupposed.
Earlier in my career, bosses and peers encouraged me to use collaborative, extravert-friendly tools like design games. I never felt particularly comfortable with them, but persisted, believing them to be techniques that designers were meant to enjoy.
I’ve since realized these aren’t the right tools for me, at least for today. I’m more comfortable working with trusted teammates in managed environments, delving into people’s expectations, and exploring initial concepts alone. It was a relief to free myself from the process expectations of others, and I believe my results testify for my new approach.
After the lashing the article received in the comments, perhaps Chamorro-Premuzic will pause to reflect on his opinions. Perhaps the Harvard Business Review will also look more closely at its editorial policy, and consider whether it fell a little out of step with its audience. But there will be plenty more articles that treat creativity like a disorder, and more executives who brand creative workers as vain and immature.
With diversity issues rightly making headlines in our industry, we should also rejoice in the multitude of personalities and approaches that make up our disciplines. We are, of course, the best placed people of all to counter harmful stereotypes. Only variety can break us out of the Otherness box.
someone is NOT HELPING and that someone is ME
| archive - contact - sexy exciting merchandise - cute - search - about | |||
| dinosaur comics returns monday! but in the meantime you can read issue #1 of the adventure time comic i wrote! :o
|
|||
| ← previous | April 18th, 2013 | next | |
|
April 18th, 2013: I have heard from someone who was on Intel's 286 and 386 design teams, and he was able to confirm that there was NO insanity. However he was also able to confirm that the entire team all went to get ice cream together, which is almost the exact opposite but somehow JUST AS GOOD A STORY. Hey, out today is Adventure Time #15, a stand-alone story! It's available at your local comics shop and all sorts of places AND it's exciting because yesterday it was announced that the series is up for three different Eisner awards! And Meredith Gran's Adventure Time series is also nominated. IT IS A GOOD YEAR FOR COMICS You can read the first few pages of AT #15 here!
 – Ryan 
| |||
Hack Your Maps
Tommapbox is, btw, a great little api!
Web maps have come a long way. Improved data, cleaner design, better performance, and more intuitive controls have made web maps a ubiquitous and critical component of many apps. They’ve also become one of the mobile space’s most successful transplants as more and more apps are powered by location-aware devices. The core web map UI paradigm itself—a continuous, pannable, zoomable surface—has even spread beyond mapping to interfaces everywhere.
Despite all this, we’ve barely begun to work web maps into our design practice. We create icon fonts, responsive grids, CSS frameworks, progressive enhancement strategies, and even new design processes. We tear down old solutions and build new ones, and even take an extra second to share battle stories in prose and in person. Yet nearly five years since Paul Smith’s article, “Take Control of Your Maps,” web maps are still a blind spot for most designers.
Have you ever taken apart a map? Worked with a map as a critical part of your design? Developed tricks, hacks, workarounds, or progressive enhancements for maps?
This article is a long overdue companion to Paul’s piece. Where he goes on a whirlwind survey of the web mapping stack at 10,000 feet, we’re going to walk through a single design process and implement a modern-day web map. By walking this path, I hope to begin making maps part of the collective conversation we have as designers.
Opinionated about open
Paul makes a strong case for why you might want to use open mapping tools instead of the established incumbent. I won’t retread his reasons here, but I would like to expand on his last: Open tools are the ones we hack best.
There is nothing mysterious about web maps. Take any spatial plane, split it up into discrete tiles, position them in the DOM, and add event handlers for panning and zooming. The basic formula can be applied to Portland, Mars, or Super Mario Land. It works for displaying large street maps, but nothing stops us from tinkering with it to explore galleries of art, create fictional game worlds, learn human anatomy, or simply navigate a web page. Open tools bare the guts of this mechanism to us, allowing us to see a wider range of possibilities.

We should know the conditions under which map images are loaded and destroyed; we should argue whether map tiles are best positioned with CSS transforms or not; and we should care whether vector elements are drawn with SVG or Canvas. Open tools let us know and experiment with these working details of our maps. If you wouldn’t have it any other way with your HTML5, CSS, or JavaScript libraries, then you shouldn’t settle for less when it comes to maps.
In short, we’ll be working with a fully open mapping stack. MapBox, where I work, has pulled together several open source libraries into a single API that we publish under mapbox.js. Other open mapping libraries that are worth your time include Leaflet and D3.js.
Starting out
I’m a big fan of Sherlock Holmes. Between the recent Hollywood movies starring Robert Downey Jr. and the BBC’s contemporary series, I’m hooked. But as someone who has never been to London, I know I’m missing the richness of place and setting that Sir Arthur Conan Doyle meant to be read into his short stories.
A typical approach would be to embed a web map with pins of various locations alongside one of the Sherlock stories. With this approach the map becomes an appendix—a dispensable element that plays little part in Doyle’s storytelling. Instead, we’re going to expand the role of our map, integrating it fully into the narrative. It will set the stage, provide pace, and affect the mood of our story.

A tale of places
To establish a baseline for our tale, I restructured The Adventure of the Bruce-Partington Plans to be told around places. I picked eight key locations from the original text, pulled out the essential details of the mystery, and framed them out with HTML, CSS, and JavaScript.

- The story is broken up into
sectionelements for each key location. A small amount of JavaScript implements a scrolling flow that highlights a single section at a time. - Our page is not responsive yet, but it contains scaffolding to guard against bad choices that could thwart us. The main text column is fluid at
33.33%and pins to amin-width: 320px. If our content and design flow reasonably within these constraints, we’re in good shape.
Next, we’ll get started mapping. Initially we’ll work on our map separately from our story page to focus on learning key elements of a new technology.
Maps are data
The mapping equivalent of our abridged Sherlock story is a dataset of eight geographic points. GeoJSON, a format for describing geographic data in JSON, is the perfect starting point for capturing this data:
{
"geometry": { "type": "Point", "coordinates": [-0.15591514, 51.51830379] },
"properties": { "title": "Baker St." }
}, {
"geometry": { "type": "Point", "coordinates": [-0.07571203, 51.51424049] },
"properties": { "title": "Aldgate Station" }
}, {
"geometry": { "type": "Point", "coordinates": [-0.08533793, 51.50438536] },
"properties": { "title": "London Bridge Station" }
}, {
"geometry": { "type": "Point", "coordinates": [0.05991101, 51.48752939] },
"properties": { "title": "Woolwich Arsenal" }
}, {
"geometry": { "type": "Point", "coordinates": [-0.18335806, 51.49439521] },
"properties": { "title": "Gloucester Station" }
}, {
"geometry": { "type": "Point", "coordinates": [-0.19684993, 51.5033856] },
"properties": { "title": "Caulfield Gardens" }
}, {
"geometry": { "type": "Point", "coordinates": [-0.10669358, 51.51433123] },
"properties": { "title": "The Daily Telegraph" }
}, {
"geometry": { "type": "Point", "coordinates": [-0.12416858, 51.50779757] },
"properties": { "title": "Charing Cross Station" }
}
Each object in our JSON array has a geometry—data that describe where this object is in space—and properties—freeform data of our own choosing to describe what this object is. Now that we have this data, we can create a very basic map.

- Note that the coordinates are a pair of latitude and longitude degrees. In the year 2013, it is still not possible to find a consistent order for these values across mapping APIs. Some use
lat,lonto meet our expectations from grade-school geography. Others uselon,latto match x,y coordinate order: horizontal, then vertical. - We’re using mapbox.js as our core open source mapping library. Each map is best understood as the key parameters passed into
mapbox.map():- A DOM element container
- One or more Photoshop-like layers that position tiles or markers
- Event handlers that bind user input to actions, like dragging to panning
- Our map has two layers. Our tile layer is made up of 256x256 square images generated from a custom map on MapBox. Our spots layer is made up of pin markers generated from the GeoJSON data above.
This is a good start for our code, but nowhere near our initial goal of using a map to tell our Sherlock Holmes story.
Beyond location
According to our first map, the eight items in our GeoJSON dataset are just places, not settings in a story full of intrigue and mystery. From a visual standpoint, pins anonymize our places and express them as nothing more than locations.
To overcome this, we can use illustrations for each location—some showing settings, others showing key plot elements. Now our audience can see right away that there is more to each location than its position in space. As a canvas for these, I’ve created another map with a custom style that blends seamlessly with the images.

- The main change here is that we define a custom factory function for our markers layer. The job of the factory function is to take each GeoJSON object and convert it to a DOM element—an
a,div,img, or whatever—that the layer will then position on the map. - Here we generate
divs and switch from using atitleattribute in our GeoJSON to anid. This provides us with useful CSS classes for displaying illustrations with our custom markers.
Bringing it all together
Now it’s time to combine our story with our map. By using the scroll events from before, we can coordinate sections of the story with places on the map, crafting a unified experience.

- The bridge between the story and the map is a revamped
setActive()function. Previously it only set an active class on a particularsectionbased on scrolling position. Now it also finds the active marker, sets an active class, and eases the map to the marker’s location. - Map animation uses the easey library in the
mapbox.jsAPI, which implements animations and tweening between geographic locations. The API is dead simple—we pass it thelon,latof the marker we want to animate to, and it handles the rest. - We disable all event handlers on our map by passing an empty array into
mapbox.map(). Now the map can only be affected by the scrolling position. If users wanted to deviate from the storyline or explore London freeform, we could reintroduce event handlers—but in this case, less is more.
Displaying our fullscreen map together with text presents an interesting challenge: our map viewport should be offset to the right to account for our story on the left. The solution I’m using here is to expand our map viewport off canvas purely using CSS. You could use JavaScript, but as we’ll see later, a CSS-only approach gives us elegant ways to reapply and adjust this technique on mobile devices.

At this stage, our map and story complement each other nicely. Our map adds spatial context, visual intrigue, and an interesting temporal element as it eases between long and short distances.
Maps in responsive design
The tiled, continuous spatial plane represented by web maps is naturally well-suited to responsive design. Web maps handle different viewport sizes easily by showing a bit more or a bit less map. For our site, we adjust the layout of other elements slightly to fit smaller viewports.

- With less screen real estate, we hide non-active text sections and pin the active text to the top of the screen.
- We use the bottom half of the screen for our map and use media queries to adjust the map’s center point to be three-fourths the height of the screen, using another version of our trick from Demo 4.
With a modest amount of planning and minimal adjustments, our Sherlock story is ready to be read on the go.
Solve your own case
If you’ve been following the code between these steps, you’ve probably noticed at least one or two things I haven’t covered, like the parameters of ease.optimal(), or how tooltips picked up on the title attribute of our GeoJSON data. The devil’s in the details, so post to this GitHub repository, where you will find the code and the design.
You should also check out:
- The MapBox site, which includes an overview of tiling and basic web map concepts, and MapBox.js docs and code examples.
- Leaflet, another powerful open source mapping library.
- D3.js, a library for powering data-driven documents that has a broad range of applications, including mapping.
This example shows just one path to integrating web maps into your designs. Don’t stick to it. Break it apart. Make it your own. Do things that might be completely genius or utterly stupid. Even if they don’t work out, you’ll be taking ownership of maps as a designer—and owning something is the only way we’ll improve on it.
Skycons: Unobtrustive Animated Weather Icons
Last year, Adam Whitcroft came out with his lovely Climacons: a comprehensive set of tastefully understated weather icons. You’ve probably seen them at one point or another, because virtually every weather app that has come out since then has been using them. (And for good reason: they’re gorgeous!)
For most of it’s development, Forecast also used them: they fit well with the aesthetic, and they were an easy way to bootstrap our design. They always seemed to be missing a certain je ne sais quoi, though, and we had a very difficult time identifying what, exactly, it was. Eventually, it dawned on us that, given the animations we had elsewhere in the app, the Climacons simply felt too flat, too static; we therefore set about making our own set of animated weather icons that felt more alive—but not so much so that they distract—which are the icons you now see on Forecast.
We are calling them Skycons, and they are now open source on GitHub.
Some Technical Highlights
- Skycons are animated in HTML5 Canvases using JavaScript. In browsers that support it, we use the recent RequestAnimationFrame API to animate them efficiently.
- Skycons are stateless: that is, the only information that is needed to render a frame is the current system time. It’s somewhat tricky to develop this way, but the benefit is that the animations degrade gracefully regardless of the framerate they are able to be displayed at, and we don’t have any data structures to maintain from frame-to-frame: this actually makes the animations lighter-weight, and hopefully less taxing on older or weaker devices, such as smartphones.
- We intentionally designed the more-interesting weather conditions (such as “rainy” or “windy”) to have much more motion in them than less-interesting weather conditions (such as “sunny” or “cloudy”), in order to naturally draw the eye to them.
- There is currently an icon for every possible “icon” value that the Forecast Data API can return. As values are added to the API, you can expect us to make new Skycons, as well.
What’s Next?
We’re pretty happy with how Skycons came out, but there’s always room for experimentation and improvement.
- The code for Skycons is rather sloppy at the moment, due to its rapid development. It could really use some refactoring!
- We developed Skycons in Canvas, because that’s what we know and it was quick for us, but we were quite interested in experimenting with animated SVG images. This would make the Skycons declarative and completely self-contained, hopefully making them better-suited to a wider range of uses.
- The set of icons was adequate for our uses, but there are quite a few weather conditions that aren’t covered: thunderstorms, hail, tornadoes, tsunamis, etc. Adding these icons would make the package more useful as a whole.
- Allowing dynamic customization of the animations, such as the angle of precipitation, could allow for any number of playful tricks, such as having the rain always fall towards the ground on your iPhone, using it’s internal accelerometer.
As we get more time for playing around, perhaps you’ll see some of these things pop up. Additionally, since Skycons are open-source, if you feel a burning desire to experiment with them, we invite you to do so! We’re making the source code available in the public domain, with no restrictions whatsoever on its use, so use them however you see fit. (Naturally, we’d appreciate being credited for our work and for any interesting contributions to also be made open source, but we don’t believe that either should be a legal requirement.)
So that’s Skycons! We hope you enjoy them and find them a useful tool in the weather design toolbox.
The DDoS That Almost Broke the Internet

The New York Times this morning published a story about the Spamhaus DDoS attack and how CloudFlare helped mitigate it and keep the site online. The Times calls the attack the largest known DDoS attack ever on the Internet. We wrote about the attack last week. At the time, it was a large attack, sending 85Gbps of traffic. Since then, the attack got much worse. Here are some of the technical details of what we've seen.
Growth Spurt
On Monday, March 18, 2013 Spamhaus contacted CloudFlare regarding an attack they were seeing against their website spamhaus.org. They signed up for CloudFlare and we quickly mitigated the attack. The attack, initially, was approximately 10Gbps generated largely from open DNS recursors. On March 19, the attack increased in size, peaking at approximately 90Gbps. The attack fluctuated between 90Gbps and 30Gbps until 01:15 UTC on on March 21.
The attackers were quiet for a day. Then, on March 22 at 18:00 UTC, the attack resumed, peaking at 120Gbps of traffic hitting our network. As we discussed in the previous blog post, CloudFlare uses Anycast technology which spreads the load of a distributed attack across all our data centers. This allowed us to mitigate the attack without it affecting Spamhaus or any of our other customers. The attackers ceased their attack against the Spamhaus website four hours after it started.
Other than the scale, which was already among the largest DDoS attacks we've seen, there was nothing particularly unusual about the attack to this point. Then the attackers changed their tactics. Rather than attacking our customers directly, they started going after the network providers CloudFlare uses for bandwidth. More on that in a second, first a bit about how the Internet works.
Peering on the Internet
The "inter" in Internet refers to the fact that it is a collection of independent networks connected together. CloudFlare runs a network, Google runs a network, and bandwidth providers like Level3, AT&T, and Cogent run networks. These networks then interconnect through what are known as peering relationships.
When you surf the web, your browser sends and receives packets of information. These packets are sent from one network to another. You can see this by running a traceroute. Here's one from Stanford University's network to the New York Times' website (nytimes.com):
1 rtr-servcore1-serv01-webserv.slac.stanford.edu (134.79.197.130) 0.572 ms 2 rtr-core1-p2p-servcore1.slac.stanford.edu (134.79.252.166) 0.796 ms 3 rtr-border1-p2p-core1.slac.stanford.edu (134.79.252.133) 0.536 ms 4 slac-mr2-p2p-rtr-border1.slac.stanford.edu (192.68.191.245) 25.636 ms 5 sunncr5-ip-a-slacmr2.es.net (134.55.36.21) 3.306 ms 6 eqxsjrt1-te-sunncr5.es.net (134.55.38.146) 1.384 ms 7 xe-0-3-0.cr1.sjc2.us.above.net (64.125.24.1) 2.722 ms 8 xe-0-1-0.mpr1.sea1.us.above.net (64.125.31.17) 20.812 ms 9 209.249.122.125 (209.249.122.125) 21.385 ms
There are three networks in the above traceroute: stanford.edu, es.net, and above.net. The request starts at Stanford. Between lines 4 and 5 it passes from Stanford's network to their peer es.net. Then, between lines 6 and 7, it passes from es.net to above.net, which appears to provide hosting for the New York Times. This means Stanford has a peering relationship with ES.net. ES.net has a peering relationship with Above.net. And Above.net provides connectivity for the New York Times.
CloudFlare connects to a large number of networks. You can get a sense of some, although not all, of the networks we peer with through a tool like Hurricane Electric's BGP looking glass. CloudFlare connects to peers in two ways. First, we connect directly to certain large carriers and other networks to which we send a large amount of traffic. In this case, we connect our router directly to the router at the border of the other network, usually with a piece of fiber optic cable. Second, we connect to what are known as Internet Exchanges, IXs for short, where a number of networks meet in a central point.
Most major cities have an IX. The model for IXs are different in different parts of the world. Europe runs some of the most robust IXs, and CloudFlare connects to several of them including LINX (the London Internet Exchange), AMS-IX (the Amsterdam Internet Exchange), and DE-CIX (the Frankfurt Internet Exchange), among others. The major networks that make up the Internet --Google, Facebook Yahoo, etc. -- connect to these same exchanges to pass traffic between each other efficiently. When the Spamhaus attacker realized he couldn't go after CloudFlare directly, he began targeting our upstream peers and exchanges.
Headwaters
Once the attackers realized they couldn't knock CloudFlare itself offline even with more than 100Gbps of DDoS traffic, they went after our direct peers. In this case, they attacked the providers from whom CloudFlare buys bandwidth. We, primarily, contract with what are known as Tier 2 providers for CloudFlare's paid bandwidth. These companies peer with other providers and also buy bandwidth from so-called Tier 1 providers.

There are approximately a dozen Tier 1 providers on the Internet. The nature of these providers is that they don't buy bandwidth from anyone. Instead, they engage in what is known as settlement-free peering with the other Tier 1 providers. Tier 2 providers interconnect with each other and then buy bandwidth from the Tier 1 providers in order to ensure they can connect to every other point on the Internet. At the core of the Internet, if all else fails, it is these Tier 1 providers that ensure that every network is connected to every other network. If one of them fails, it's a big deal.
Anycast means that if the attacker attacked the last step in the traceroute then their attack would be spread across CloudFlare's worldwide network, so instead they attacked the second to last step which concentrated the attack on one single point. This wouldn't cause a network-wide outage, but it could potentially cause regional problems.
We carefully select our bandwidth providers to ensure they have the ability to deal with attacks like this. Our direct peers quickly filtered attack traffic at their edge. This pushed the attack upstream to their direct peers, largely Tier 1 networks. Tier 1 networks don't buy bandwidth from anyone, so the majority of the weight of the attack ended up being carried by them. While we don't have direct visibility into the traffic loads they saw, we have been told by one major Tier 1 provider that they saw more than 300Gbps of attack traffic related to this attack. That would make this attack one of the largest ever reported.
The challenge with attacks at this scale is they risk overwhelming the systems that link together the Internet itself. The largest routers that you can buy have, at most, 100Gbps ports. It is possible to bond more than one of these ports together to create capacity that is greater than 100Gbps however, at some point, there are limits to how much these routers can handle. If that limit is exceeded then the network becomes congested and slows down.
Over the last few days, as these attacks have increased, we've seen congestion across several major Tier 1s, primarily in Europe where most of the attacks were concentrated, that would have affected hundreds of millions of people even as they surfed sites unrelated to Spamhaus or CloudFlare. If the Internet felt a bit more sluggish for you over the last few days in Europe, this may be part of the reason why.
Attacks on the IXs
In addition to CloudFlare's direct peers, we also connect with other networks over the so-called Internet Exchanges (IXs). These IXs are, at their most basic level, switches into which multiple networks connect and can then pass bandwidth. In Europe, these IXs are run as non-profit entities and are considered critical infrastructure. They interconnect hundreds of the world's largest networks including CloudFlare, Google, Facebook, and just about every other major Internet company.
Beyond attacking CloudFlare's direct peers, the attackers also attacked the core IX infrastructure on the London Internet Exchange (LINX), the Amsterdam Internet Exchange (AMS-IX), the Frankfurt Internet Exchange (DE-CIX), and the Hong Kong Internet Exchange (HKIX). From our perspective, the attacks had the largest effect on LINX which caused impact over the exchange and LINX's systems that monitor the exchange, as visible through the drop in traffic recorded by their monitoring systems. (Corrected: see below for original phrasing.)

The congestion impacted many of the networks on the IXs, including CloudFlare's. As problems were detected on the IX, we would route traffic around them. However, several London-based CloudFlare users reported intermittent issues over the last several days. This is the root cause of those problems.
The attacks also exposed some vulnerabilities in the architecture of some IXs. We, along with many other network security experts, worked with the team at LINX to better secure themselves. In doing so, we developed a list of best practices for any IX in order to make them less vulnerable to attacks.
Two specific suggestions to limit attacks like this involve making it more difficult to attack the IP addresses that members of the IX use to interchange traffic between each other. We are working with IXs to ensure that: 1) these IP addresses should not be announced as routable across the public Internet; and 2) packets destined to these IP addresses should only be permitted from other IX IP addresses. We've been very impressed with the team at LINX and how quickly they've worked to implement these changes and add additional security to their IX and are hopeful other IXs will quickly follow their lead.
The Full Impact of the Open Recursor Problem
At the bottom of this attack we once again find the problem of open DNS recursors. The attackers were able to generate more than 300Gbps of traffic likely with a network of their own that only had access 1/100th of that amount of traffic themselves. We've written about how these mis-configured DNS recursors as a bomb waiting to go off that literally threatens the stability of the Internet itself. We've now seen an attack that begins to illustrate the full extent of the problem.
While lists of open recursors have been passed around on network security lists for the last few years, on Monday the full extent of the problem was, for the first time, made public. The Open Resolver Project made available the full list of the 21.7 million open resolvers online in an effort to shut them down.
We'd debated doing the same thing ourselves for some time but worried about the collateral damage of what would happen if such a list fell into the hands of the bad guys. The last five days have made clear that the bad guys have the list of open resolvers and they are getting increasingly brazen in the attacks they are willing to launch. We are in full support of the Open Resolver Project and believe it is incumbent on all network providers to work with their customers to close any open resolvers running on their networks.
Unlike traditional botnets which could only generate limited traffic because of the modest Internet connections and home PCs they typically run on, these open resolvers are typically running on big servers with fat pipes. They are like bazookas and the events of the last week have shown the damage they can cause. What's troubling is that, compared with what is possible, this attack may prove to be relatively modest.
As someone in charge of DDoS mitigation at one of the Internet giants emailed me this weekend: "I've often said we don't have to prepare for the largest-possible attack, we just have to prepare for the largest attack the Internet can send without causing massive collateral damage to others. It looks like you've reached that point, so... congratulations!"
At CloudFlare one of our goals is to make DDoS something you only read about in the history books. We're proud of how our network held up under such a massive attack and are working with our peers and partners to ensure that the Internet overall can stand up to the threats it faces.
Correction: The original sentence about the impact on LINX was "From our perspective, the attacks had the largest effect on LINX which for a little over an hour on March 23 saw the infrastructure serving more than half of the usual 1.5Tbps of peak traffic fail." That was not well phrased, and has been edited, with notation in place.
Chameleon Riding a Bicycle

A fish may not need a bicycle, but a chameleon? Why, that worked out quite well, as CuteOverload reader Linsay E. wrote: "This is Porkey, she’s an African Pygmy Chameleon. She’s in a bike gang with me (her mom.) Porkey is in such good shape and likes to eat fruit flies."
This is Not a Game, Sculpture of Giant Hands Playing with Life-Sized Tank and Toy Soldiers

“This is not a game” by artist Lorenzo Quinn is a large-scale sculptural installation of giant hands playing with a life-sized tank and toy soldiers. Exhibited on a floating platform at the 2011 Venice Bienalle, the installation featured a 37-ton Russian T-55 tank.
The human figure and especially hands show up frequently in Quinn’s work. In recent years he has created two other more playful installations of hands playing with life-sized toys. The 2010 installation “Vroom Vroom” features a giant hand playing with a Fiat Cinquecento car. “La Dolce Vita” is a 2011 installation of a giant hand playing with a Vespa scooter.



“Vroom Vroom”

“La Dolce Vita”
via My Modern Metropolis, Ian Brooks
Han Solo’s DL-44 Blaster Pistol Built With LEGOs
Captain Infinity recreated Han Solo’s DL-44 heavy blaster pistol using LEGO bricks for the 2013 MOCathalon contest.
images via Captain Infinity
via Brother’s Brick
the day t-rex felt shouty AND horny
| archive - contact - sexy exciting merchandise - cute - search - about | |||
| dinosaur comics returns monday!
|
|||
| ← previous | April 11th, 2013 | next | |
|
April 11th, 2013: GUYS did you know I will sell you the last apron you'll ever need?

That last photo is of Emily and both she AND the apron are awesome! Anyway, I'm PRETTY SURE that's the last apron you'll ever need. In closing, here is a poem!
Cats are fun to own I suppose
– Ryan 
| |||
Gas masks for babies, 1940

 From the Imperial War Museum in London, a couple of incredible photos of nurses testing out infant gas-masks: "Three nurses carry babies cocooned in baby gas respirators down the corridor of a London hospital during a gas drill. Note the carrying handle on the respirator used to carry the baby by the nurse in the foreground."
From the Imperial War Museum in London, a couple of incredible photos of nurses testing out infant gas-masks: "Three nurses carry babies cocooned in baby gas respirators down the corridor of a London hospital during a gas drill. Note the carrying handle on the respirator used to carry the baby by the nurse in the foreground."
GAS DRILL AT A LONDON HOSPITAL: GAS MASKS FOR BABIES ARE TESTED, ENGLAND, 1940 (via Kadrey) ![]()
 |
 |
Loving them into hell?
TomThe hypocrisy inherent in "love the sinner, hate the sin and be VERY VOCAL ABOUT IT" is not lost on me.
 The other day, I posted about why “speaking the truth in love” isn’t an excuse for theological debates. I said that real love needs to be evident through grace, not just trying to make me agree with you.
The other day, I posted about why “speaking the truth in love” isn’t an excuse for theological debates. I said that real love needs to be evident through grace, not just trying to make me agree with you.
One of my Facebook friends responded with this comment:
I have been told that by loving people and not telling them the truth I am loving them into hell. Then they told me some famous Christian artist wrote a song saying that. It just made me feel like poo.
If a Christian singer said it, it must be true!
After I stopped my inner child from giggling at the word “poo,” I thought about this. Many of you may have been subjected to the same pressures. But I think this person’s friend has it all wrong.
Some of you will no doubt want to respond right away by pointing out that you either don’t believe in a literal hell or don’t view it the same way this person’s friend does. I don’t really want to get into a debate about hell, though, so for the sake of argument, let’s say that this person is right that gay sex is sinful and that hell is a place of eternal torment for people who die without repenting of their sins and giving their lives to Christ.
Well, if that’s true, then I can tell you right now that the American church—particularly those conservative and evangelical segments of it, like the ones I grew up in—has already developed the most effective strategy I can imagine… for sending gay people straight to hell.
Yeah, I said it.
What many people would consider “loving me by telling me the truth” I would call “constantly harassing me with Bible passages and arguments about sin until I’m sick of listening to anything they have to say.”
“Wait, that’s not fair,” some Christians might say. “I’m not constantly harassing you. I only bring it up sometimes.”
True, maybe you don’t bring it up constantly, but you are one of many Christians I know, all of whom think they’re only bringing it up “sometimes”—to the point that I have to listen to it… ALL. THE. TIME.
Imagine waking up with a large, very noticeable zit on your face. All day long, as you interact with people, one person after another takes the opportunity to say, “Hey, did you know you’ve got a big zit?” It’s a bit uncomfortable when the first or second person mentions it, but by the tenth person, you’re ready to bite someone’s head off:
“Yes, I know!!!!! Shut up about it already!!!!!!”

On the other hand, what if you have food in your teeth and no one bothers to tell you? You might be a bit embarrassed, but you’d surely be grateful for the friend who loves you enough to (privately) tell you the truth: “Hey, there’s a bit of spinach in there. Also, your zipper’s undone.”
The key is knowing the difference. When you “share the truth in love,” are you the lone person offering a new perspective? Or are you just piling on?
When it comes to gay people in our culture, I can guarantee you that you’re piling on. There is not a single gay person in the United States—no matter how many affirming friends they have, and no matter how liberal an area they live in—who hasn’t already heard time and time again that many Christians believe them to be abominable. If people get irritated about being reminded of a silly pimple, how do you think they feel about being reminded that others believe they’re going to hell?
I know I find it painful. And I’m a Christian who actually cares about this stuff, so if I’m sick of it, you know my agnostic, atheist, and other non-Christian friends are ready to pull their hair out. (I have an advantage in that my hair is already out.)
It’s no secret that I don’t think being gay is a sin or that gay relationships are sinful. But if you do, and you’re concerned about my eternal destiny, a strategy where you keep your emotional distance and regularly remind me of your disapproval isn’t going to change my mind. If anything, it’s going to make me less likely to believe anything you say, and less likely to be interested in being a Christian.
“Tough love” is a good strategy sometimes. But this isn’t an intervention for a drug addict, and if you don’t see the difference between drug addiction and being gay, you haven’t spent very much time listening to gay people.
The irony, you see, is that the person who is supposedly “loving me into hell” by just being my friend and showing me the grace and love of Christ is the person I’m much more likely to listen to when it comes to big decisions in my life.
But in the end, if I don’t ask them for their opinion on the issue, it ultimately won’t be because they were too loving. It’ll be because I’m so sick of hearing the ungracious messages from the “truth-telling” crowd.