Shared posts
Net neutrality comment fraud will be investigated by government

Enlarge / Rally organizers carry away props following a protest outside the Federal Communication Commission building against the end of net neutrality rules on December 14, 2017 in Washington, DC. (credit: Getty Images | Chip Somodevilla )
The US Government Accountability Office (GAO) will investigate the use of impersonation in public comments on the Federal Communications Commission's net neutrality repeal.
Congressional Democrats requested the investigation last month, and the GAO has granted the request.
While the investigation request was spurred by widespread fraud in the FCC's net neutrality repeal docket, Democrats asked the GAO to also "examine whether this shady practice extends to other agency rulemaking processes." The GAO will do just that, having told Democrats in a letter that it will "review the extent and pervasiveness of fraud and the misuse of American identities during federal rulemaking processes."
Senators ask social media execs to investigate “ReleaseTheMemo” hashtag

Enlarge / Sen. Dianne Feinstein (D-CA), center, at a November hearing on Russia's use of social media in the 2016 election. Feinstein and California congressman Adam Schiff have called on Facebook and Twitter to account for Russian troll's use of the #ReleaseTheMemo hashtag to influence opinion on the Mueller investigation into the Trump presidential campaign. (credit: Alex Wong / Getty Images)
Senator Dianne Feinstein and Congressman Adam Schiff, the ranking Democratic Party members of the Senate Judiciary Committee and House Permanent Select Committee on Intelligence, sent a joint letter to the executives of Facebook and Twitter yesterday urging them to further delve into ongoing Russian influence campaigns on their platforms around the "ReleaseTheMemo" hashtag. The hashtag references a memo written by House Intelligence Committee chairman Devin Nunes detailing alleged abuses of the Foreign Intelligence Surveillance Act by the FBI. WikiLeaks' Julian Assange offered on Twitter to pay anyone who leaked the memo to him.
According to a social media tracking project by the German Marshall Fund's Alliance for Securing Democracy, a significant part of the support on social media for declassification of Nunes' memo has come from accounts controlled by Russia-backed "troll" accounts—some of them automated "bots" that promote other posts for propaganda purposes.
The Alliance for Securing Democracy, the organization behind the social media tracking site Hamilton 68, reported last Friday that real-time data showed that #ReleaseTheMemo was largely being used by accounts identified as controlled by Russian influence campaigns.
The net neutrality testing app that Apple rejected is available now

Enlarge (credit: Getty Images | alexsl)
An iPhone application that attempts to detect whether ISPs are throttling online services is now available on Apple's App Store, despite Apple originally refusing to allow it onto iPhones and iPads.
The Wehe app has been available for iOS at this link since last night. It had already been available for Android on the Google Play store for at least a month.
Wehe tests the speeds of YouTube, Amazon, NBCSports, Netflix, Skype, Spotify, and Vimeo in different ways and uses variances in measured results to judge whether or not traffic is being throttled to your device. But Apple initially refused to let the app into the App Store, telling its creator that "your app has no direct benefits to the user."
DRM: You have the right to know what you're buying!
Today, the EFF and a coalition of organizations and individuals asked the US Federal Trade Commission (FTC) to explore fair labeling rules that would require retailers to warn you when the products you buy come locked down by DRM ("Digital Rights Management" or "Digital Restrictions Management").
These digital locks train your computerized devices to disobey you when you ask them to do things the manufacturer didn't specifically authorize -- even when those things are perfectly legal. Companies that put digital locks on their products -- ebook, games and music publishers, video companies, companies that make hardware from printers to TVs to cat litter trays -- insist that DRM benefits their customers, by allowing the companies to offer products at a lower price by taking away some of the value -- you can "rent" an ebook or a movie, or get a printer at a price that only makes sense if you also have to buy expensive replacement ink.
We don't buy it. We think that the evidence is that customers don't much care for DRM (when was the last time you woke up and said, "Gosh, I wish there was a way I could do less with my games?"). Studies agree.
The FTC is in charge of making sure that Americans don't get ripped off when they buy things. We've written the Commission a letter, drafted and signed by a diverse coalition of public interest groups, publishers, and rightsholders, calling on the agency to instruct retailers to inform potential customers of the restrictions on the products they're selling. In a separate letter, we detail the stories of 22 EFF supporters who unwittingly purchased DRM-encumbered products and later found themselves unable to enjoy their purchases (a travel guide that required a live internet connection to unlock, making it unreadable on holiday), or locked into an abusive relationship with their vendors (a cat litter box that only worked if resupplied with expensive detergent), or even had other equipment they owned rendered permanently inoperable by the DRM in a new purchase (for example, a game that "bricked" a customer's DVD-RW drive).
Now the FTC has been equipped with evidence that there are real harms, and that rightsholders are willing to have fair labeling practices, the FTC should act. And if the DRM companies are so sure that their customers love their products, why would they object?
EFF is currently suing the US government to invalidate Section 1201 of the DMCA, a law that has been used to threaten research into the security risks of DRM and inhibit the development of products and tools that break digital locks -- again, even if the purpose is otherwise legal (like letting you read your books on an alternate reader, or put a different brand of perfume in your cat litter box). Until we win our lawsuit, people who buy DRM-locked products are unlikely to be rescued from their lock-in by add-ons that restore functionality to their property. That makes labeling especially urgent: it's bad enough to be stuck with product that is defective by design, but far worse if those defects can't be fixed without risking legal retaliation.
For the full letter to the FTC about labeling:
https://www.eff.org/document/eff-letter-ftc-re-drm-labeling
For the full letter to the FTC with the stories of people who've been harmed by DRM they weren't informed of:
https://www.eff.org/files/2016/08/06/eff_request_for_investigation_re_labeling_drm-limited_products.pdf
PLUS SIZE STYLE ICON: MS. FRIZZLE










Other odds and ends you may or may not need in your life:

Thermometer earrings
Another amazing galaxy dress (comes in all sizes)
School bus wristlet
CRYSTAL SET (grow 'em yourself!)
Now, it's your turn to suggest the next style icon in this series! Penelope Garcia from Criminal Minds has been suggested and I'm diggin' the idea of compiling a post of outfits inspired by Gabourey Sidibe as Becky from Empire.
What are your requests? Lay 'em on me.
Out-of-the-box exploitation possible on PCs from top 5 OEMs
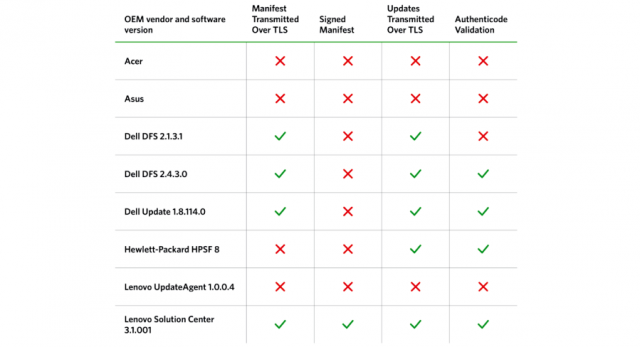
(credit: Duo Security)
The next time you're in the market for a new Windows computer, consider this: if it comes from one of the top five manufacturers, it's vulnerable to man-in-the-middle attacks that allow hackers to install malware.
That's the take-away from a report published Tuesday by researchers from two-factor authentication service Duo Security. It found third-party updating tools installed by default threatened customers of Dell, HP, Lenovo, Acer, and Asus. The updaters frequently expose their programming interfaces, making them easy to reverse engineer. Even worse, the updaters frequently fail to use transport layer security encryption properly, if at all. As a result, PCs from all five makers are vulnerable to exploits that allow attackers to install malware.
"Hacking in practice means taking the path of least resistance, and OEM software is often a weak link in the chain," the Duo Security report stated. "All of the sexy exploit mitigations, desktop firewalls, and safe browsing enhancements can't protect you when an OEM vendor cripples them with pre-installed software."
Save iTunes!

I remember the launch of iTunes in 2001. Hurrying home from the MacWorld conference in San Francisco, downloading the app, making a stack of CDs next to my Powerbook, ripping them as fast as my machine would go. Rip, Mix, Burn, baby!
The other thing I remember is how the media industry viewed iTunes: they hated it. They hated people using iTunes to rip CDs, they hated mixing and burning. The only reason they let the iPod/iTunes ecosystem live was because when they sued the company that made the first MP3 players, they lost.
The record companies thought that anything that let listeners do more with their music had to be illegal. After all, they had big plans for the future of music and those plans hinged on being able to control how you and I used our music. They'd made big money selling cassettes to LP owners, and CDs to cassette owners, and they viewed selling digital versions of those same songs to us as their inalienable right. If we could rip our own CDs, how would they sell us that music again?
Luckily for us and for Apple, a company's preferences don't have the force of law. The record companies could gripe, but they couldn't stop iTunes.
Not until now, anyway.
Apple is a member of the World Wide Web Consortium (W3C), a body currently working to make a standard for restricting Web users' options while they view copyrighted works. This standard, Encrypted Media Extensions (EME), allows media companies to restrict the use of copyrighted works without regard to the limits of copyright law. Copyright lets you do all kinds of things with the works you lawfully access: record them to experience later, move them to a different device, pause them so you can get a snack or change a diaper.
EME would give giant media companies a veto over your use of your media—a veto that would have killed iTunes before it ever got started.
Worse: EME could let its creators invoke section 1201 of the Digital Millennium Copyright Act (DMCA), which prohibits you from getting around EME-style restrictions on copyrighted works. According to some U.S. courts, the law applies even if you're circumventing for a purpose allowed under copyright law. Even if you're making iTunes.
DMCA 1201 is so sloppily drafted and far-reaching that it even lets companies legally threaten security researchers who discover serious, dangerous bugs in products if they come forward with embarrassing news.
(And if you're not an American: the US trade representative is working hard to make DMCA-style laws a condition of trading with the USA, spreading them to every corner of the Earth.)
The Electronic Frontier Foundation asked the W3C not to do this. When they went ahead anyway, we asked them to compromise: at least ask your members to promise not to use the DMCA to attack new companies and researchers doing lawful things. Make them promise to let the next iTunes get a chance. After all, this is what the W3C did when it came to patents: to participate in the W3C's process, you must agree that people are allowed to implement its standards without worrying about undisclosed patents you may own. This safeguard has helped enable an enormous turnover in popular browsers over the past decade.
Despite hearing from a diverse coalition of its members who approved of the EFF compromise, the W3C overruled them, and is letting EME continue without a legal safeguard for the products that don't exist yet, for the companies that haven't had their iTunes moment yet.
It's heartbreaking.
Share this message, pass the word.
The W3C has a long, proud history of standing up for the open Web, the Web anyone can make. It should honor its history and continue to protect the open Web and the innovators and researchers who make it great.
A 25-Year Survey of Prosecutorial Misconduct and a Viable Solution
Caldwell, Harry M., Everybody Talks About Prosecutorial Conduct But Nobody Does Anything About It: A 25-Year Survey of Prosecutorial Misconduct and a Viable Solution (2016). U. Ill. L. Rev. (2016 Forthcoming); Pepperdine University Legal Studies Research Paper No. 10. Available for download at SSRN: http://ssrn.com/abstract=2761252
“Prosecutors, whom we trust to carry out the demanding and essential business of presenting the People’s case against alleged law-breakers, are free to commit misconduct with impunity. They suffer no disciplinary repercussions for their misdeeds. The only adverse consequence facing an erring prosecutor is the extremely rare prospect of having a conviction overturned due to his misconduct. Even then the prosecutor will not be subject to any sanction: no citation for contempt, no suspension of license, no civil liability, no fine, not so much as a censure. In an earlier article entitled The Prosecutor Prince, I proposed the creation of an independent commission empowered to investigate claims of alleged prosecutorial misconduct, and meter our discipline should the claims be warranted. As set forth in that article, the commission would be modeled after California’s Judicial Panel, which has proven effective in dealing with instances of judicial misconduct. The purpose of this current article is not to once again make the case that prosecutorial misconduct is prevalent and represents a stain on the American justice system — that purpose has been thoroughly accomplished in the earlier article and by countless others. The two-fold purpose of this article is to revise the earlier proposal to make it more fiscally and politically viable, and to use the findings from our recently completed twenty-five-year survey of prosecutorial misconduct as support for the revised proposal.”
The FCC Is Pushing A 'Nutrition Label' For Broadband Connections
They should, according to some samples provided by the FCC, look a little something like this:
 Interestingly, the FCC"s push for improved labeling includes some renewed attention on the disclosure of sneaky, below-the-line fees, which many ISPs use to jack up the advertised rate post sale. We've noted how many of these fees are simply pulled out of thin air and are pure profit, a practice the FCC (after fifteen years of apathy) is now showing some interest in:
Interestingly, the FCC"s push for improved labeling includes some renewed attention on the disclosure of sneaky, below-the-line fees, which many ISPs use to jack up the advertised rate post sale. We've noted how many of these fees are simply pulled out of thin air and are pure profit, a practice the FCC (after fifteen years of apathy) is now showing some interest in:"The FCC receives more than 2,000 complaints annually about surprise fees associated with consumers’ Internet service bills. The actual prices paid for broadband-related services can be as much as 40 percent greater than what is advertised after taxes and fees are added to a bill, according to consumer complaints to the Commission. With the average monthly cost of broadband service ranging between $60 and $70, consumers deserve to know what they are going to get for their money."While well intentioned, it's not exactly clear if ISPs will actually use the new labels. According to the FCC announcement, the labels are only "recommended" by the agency for ISPs concerned that they're not meeting the FCC's transparency requirements, which were part of last year's still-contested net neutrality rules:
"The FCC’s Open Internet transparency rules require broadband Internet access service providers to disclose this information to consumers in an accurate, understandable and easy-to-find manner. These formats, while not mandated by the agency, are recommended by the Commission and will serve as a “safe harbor” to meet those requirements."Knowing ISPs as most of you do, you'll probably know their definition of "accurate, understandable and easy to find" may not exactly match your own. The labels have the approval of the FCC's Consumer Advisory Committee, which includes companies like Verizon and CenturyLink. That these two companies find the labels acceptable could very well mean they have no intention of actually using them (possibly pointing to their existing website structure as good enough). Both companies also are busy trying to scrap the FCC's net neutrality rules entirely, which if successful would mean a quick death to the rules -- and these labels.
Another problem is that the use of hidden, manufactured fees to jack up the advertised price is considered false advertising and fraud by many. Many ISPs are so un-frightened of regulatory enforcement on this front they're barely trying any more. CenturyLink, for example, charges millions of its DSL customers a $2 "Internet Cost Recovery Fee" that its website explains as such:
"This fee helps defray costs associated with building and maintaining CenturyLink's High-Speed Internet broadband network, as well as the costs of expanding network capacity to support the continued increase in customers' average broadband consumption."And here you were thinking that's what your advertised existing monthly broadband bill was for. As such, given the obvious fraud on the hidden fee front, it may take a little more than a few labels to meaningfully improve ISP behavior and transparency.
Permalink | Comments | Email This Story
© enforcement/compliance is not the right mindset for libraries
Anne"We shouldn’t be doing the content industry’s work for them, especially when it comes to users, some of whom -only have access to content, connectivity, and technology- through us."
I got a question from a libraryperson recently, about user activities that had never occurred to me as copyright concerns before. This spurred some thoughts, also connected to some talks I have given about how libraries can support our users with respect to copyright.
To be clear, this wasn’t a situation where I wasn’t sure if this copyright-implicating activity was permitted. This was an activity -I was not sure actually touched on any of the rights of a copyright holder-. Since I can’t give legal advice, I did not offer a final opinion. (Offering one publicly here would still be inappropriate because the questioner may be able to identify themself in this description.)
It’s also worth noting here that “actively gives you info that they’re going to infringe” requires -knowing which activities are unquestionably infringing. There are VERY FEW of those. (“I am ripping these DVDs to sell copies on the street” = pretty unquestionably infringing. “I am ripping these DVDs to make remix videos” = quite possibly legal. “I am ripping these DVDs” = not enough information to know anything!) Many of the enforce-y questions libraryfolk send my way are based on the idea that “infringing” is easily defined and easily avoided, and that any uncertainty on either front is a sign of some sort of moral failing.
My questioner’s creative copyright thinking was, on it’s own, a good thing! We should think creatively or speculatively about possible copyright infringement theories, because it’s good to try to anticipate problems. But creative anticipation of copyright problems -in conjunction with- an abundance of caution is not a good thing. We shouldn’t be doing the content industry’s work for them, especially when it comes to users, some of whom -only have access to content, connectivity, and technology- through us.
Beyond Flint: Excessive lead levels found in almost 2,000 water systems across all 50 states
“While a harsh national spotlight focuses on the drinking water crisis in Flint, Mich., a USA TODAY NETWORK investigation has identified almost 2,000 additional water systems spanning all 50 states where testing has shown excessive levels of lead contamination over the past four years. The water systems, which reported lead levels exceeding Environmental Protection Agency standards, collectively supply water to 6 million people. About 350 of those systems provide drinking water to schools or day cares. The USA TODAY NETWORK investigation also found at least 180 of the water systems failed to notify consumers about the high lead levels as federal rules require…In all, the USA TODAY NETWORK analysis of EPA enforcement data identified 600 water systems in which tests at some taps showed lead levels topping 40 parts per billion (ppb), which is more than double the EPA’s action level limit. While experts caution Flint is an extreme case of pervasive contamination, those lead levels rival the 400-plus of the worst samples in far more extensive testing of around 15,000 taps across Flint. The 40 ppb mark also stands as a threshold that the EPA once labeled on its website an “imminent” health threat for pregnant women and young children.”
Cybersquatting Cases Up in 2015, Driven by New gTLDs
Via WIPO – Geneva, March 18, 2016 PR/2016/789 – “Amid the roll-out of hundreds of new generic Top-Level Domains (gTLDs) such as .GURU, .NINJA and .NYC, trademark owners filed 2,754 cases under the Uniform Domain Name Dispute Resolution Policy (UDRP) with WIPO in 2015, an increase of 4.6 % over the previous year. Videos: Highlights Video/YouTube | Press Conference Video/YouTube. Cybersquatting disputes relating to new gTLDs accounted for 10.5% of WIPO’s UDRP caseload in 2015, which covered a total of 4,364 domain names. Among these names, .XYZ, .CLUB and .EMAIL were the most common new gTLDs…”
Annual Report to Congress: Federal Information Security Modernization Act
Submitted by OMB, March 18, 2016 – “The attached report is submitted pursuant to Section 3553 of the Federal Information Security Modernization Act of 2014 (P.L. 113-283), which requires the Office of Management and Budget (OMB) to submit an annual report on the effectiveness of information security policies and practices during the preceding year and a summary of the evaluations conducted by agency Inspectors General. This report covers the period from October 1, 2014, through September 30, 2015, and provides an update of ongoing informati on security initiatives, a review of Fiscal Year 2015 information security incidents, Inspector General assessments of agencies’ progress in implementing information security capabilities, and the Federal Government’s progress in meeting key information security performance measures based on agency submitted data. As you will note, progress has been made in key areas of information security.”
Washington DC metro area now sixth most populous in US
“Census statistics released today provide population estimates for our nation’s 381 metropolitan statistical areas, 536 micropolitan statistical areas and 3,142 counties…Between July 1, 2014, and July 1, 2015, Washington-Arlington-Alexandria, D.C.-Va.-Md.-W.Va., surpassed Philadelphia-Camden-Wilmington, Pa.-N.J.-Del.-Md., to become the sixth most populous metro area. New York-Newark-Jersey City, N.Y.-N.J.-Pa., remained the most populous, followed by Los Angeles, Chicago-Naperville-Elgin, Ill.-Ind.-Wis., Dallas and Houston…”
Paper – Cryptopolitik and the Darknet
Cryptopolitik and the Darknet By Daniel Moore, Thomas Rid, Publication: Survival: Global Politics and Strategy, February–March 2016, Pages: 7-38, Volume: 58. Edition number: 1. Date: 19 January 2016
“Encryption policy is becoming a crucial test of the values of liberal democracy in the twenty-first century. The trigger is a dilemma: the power of ciphers protects citizens when they read, bank and shop online – and the power of ciphers protects foreign spies, terrorists and criminals when they pry, plot and steal. Encryption bears directly on today’s two top threats, militant extremism and computer-network breaches – yet it enables prosperity and privacy. Should the state limit and regulate the fast-growing use of cryptography? If so, how? In September 2013, the New York Times and the Guardian jointly revealed Bullrun, a $250-million-per-year programme to make encrypted internet traffic accessible to the United States’ and United Kingdom’s intelligence agencies. A few weeks later, another story broke: the US National Security Agency (NSA) had successfully intercepted Google traffic; data had been securely encrypted between Google and its users, but sent in clear text between the company’s data centres. On a now-famous yellow Post-it note, one NSA spy outlined how to trick Google at the spot where the public internet meets Google’s cloud, cheekily drawing a smiley face and scribbling that encryption was ‘added and removed here!’. When the Washington Post showed the drawing to two engineers close to Google, they ‘exploded in profanity’. Even worse, just before Christmas that year, Reuters reported that the NSA had worked with the pioneering security company RSA to undermine the standard for a random-number generator, an engine that powers encryption. Cryptographers were shocked, and trust in the US government evaporated. The Crypto Wars of the early 1990s, it became clear, had never ended; the fight simply entered the next round, with stakes raised and gloves off.”
faggotxvx: i-peed-so-hard-i-laughed: continuants: invisiblespo...
[Narrator: A scientist in Peru [pause for peep] captured this, escaping from the tiny body [pause for peep] of a sleeping hummingbird. [pause for peep] A high-pitched [pause for peep] but unmistakable snore. [pause for peep] Hummingbirds are loved for their beauty and speed [pause for peep] but this one was behaving a little bit like a human. [pause for peep] The perfect cute-response trigger.]
[pause for peep]
IT PEEP WHEN IT SLEEP!!!!!!!!!!!!
i forgot about this. i love this so much.
Monday Cute: New Rhino Calf at Toronto Zoo Falls Asleep
The Toronto Zoo’s Indian rhino Ashakiran gave birth to a male calf last week, who appears healthy and super adorable. Look at the way his little ears tuck back when he’s getting ready to sleep!
Indian rhinos are listed as Vulnerable with “approximately only 2,000 left in the wild,” and for the purpose of monitoring them Asha and her calf are not currently in public viewing (but their lion cubs and pandas are!). You can follow The Toronto Zoo for more #TORhinoBaby updates!
(via Buzzfeed)
—Please make note of The Mary Sue’s general comment policy.—
Do you follow The Mary Sue on Twitter, Facebook, Tumblr, Pinterest, & Google +?