My ZOMGTERRISTSGONNAKILLUSALLRUNHIDE TSA tee-shirt (of Poop Strong fame) is available in tote-bag form, a fact I had somehow missed!
Shared posts
ZOMGTERRISTSGONNAKILLUSALL tee, now in tote form
To beat this new video game, reprogram it

The only way to truly beat Hack 'n' Slash, a new video game from Double Fine Productions, is to reprogram it.
But playing the game—a sendup to traditional adventure games like The Legend of Zelda, which place players on quests that involve battling monsters, collecting artifacts, and solving puzzles—requires no programming knowledge whatsoever. Nor does it demand familiarity with coding tools. Instead, Hack 'n' Slash makes manipulating the game's source code part of the game itself. To play it is to hack it.
read more
Stand Up For ODF In The UK
Stuart.ward.ukAdvocate ODF
Originally posted on Meshed Insights & Knowledge:
“The software we use in government is still supplied by just a few large companies. A tiny oligopoly dominates the marketplace. I want to see a greater range of software used, so civil servants have access to the information they need and can get their work done without having to buy a particular brand of software.”
So ODF Advocates once again need to speak up for openness and diversity – there are links in the article.
Why the Government Should Help Leakers
In the Information Age, it's easier than ever to steal and publish data. Corporations and governments have to adjust to their secrets being exposed, regularly.
When massive amounts of government documents are leaked, journalists sift through them to determine which pieces of information are newsworthy, and confer with government agencies over what needs to be redacted.
Managing this reality is going to require that governments actively engage with members of the press who receive leaked secrets, helping them secure those secrets -- even while being unable to prevent them from publishing. It might seem abhorrent to help those who are seeking to bring your secrets to light, but it's the best way to ensure that the things that truly need to be secret remain secret, even as everything else becomes public.
The WikiLeaks cables serve as an excellent example of how a government should not deal with massive leaks of classified information.
WikiLeaks has said it asked US authorities for help in determining what should be redacted before publication of documents, although some government officials have challenged that statement. WikiLeaks' media partners did redact many documents, but eventually all 250,000 unredacted cables were released to the world as a result of a mistake.
The damage was nowhere near as serious as government officials initially claimed, but it had been avoidable.
Fast-forward to today, and we have an even bigger trove of classified documents. What Edward Snowden took -- "exfiltrated" is the National Security Agency term -- dwarfs the State Department cables, and contains considerably more important secrets. But again, the US government is doing nothing to prevent a massive data dump.
The government engages with the press on individual stories. The Guardian, the Washington Post, and the New York Times are all redacting the original Snowden documents based on discussions with the government. This isn't new. The US press regularly consults with the government before publishing something that might be damaging. In 2006, the New York Times consulted with both the NSA and the Bush administration before publishing Mark Klein's whistle-blowing about the NSA's eavesdropping on AT&T trunk circuits. In all these cases, the goal is to minimize actual harm to US security while ensuring the press can still report stories in the public interest, even if the government doesn't want it to.
In today's world of reduced secrecy, whistleblowing as civil disobedience, and massive document exfiltrations, negotiations over individual stories aren't enough. The government needs to develop a protocol to actively help news organizations expose their secrets safely and responsibly.
Here's what should have happened as soon as Snowden's whistle-blowing became public. The government should have told the reporters and publications with the classified documents something like this: "OK, you have them. We know that we can't undo the leak. But please let us help. Let us help you secure the documents as you write your stories, and securely dispose of the documents when you're done."
The people who have access to the Snowden documents say they don't want them to be made public in their raw form or to get in the hands of rival governments. But accidents happen, and reporters are not trained in military secrecy practices.
Copies of some of the Snowden documents are being circulated to journalists and others. With each copy, each person, each day, there's a greater chance that, once again, someone will make a mistake and some -- or all -- of the raw documents will appear on the Internet. A formal system of working with whistle-blowers could prevent that.
I'm sure the suggestion sounds odious to a government that is actively engaging in a war on whistle-blowers, and that views Snowden as a criminal and the reporters writing these stories as "helping the terrorists." But it makes sense. Harvard law professor Jonathan Zittrain compares this to plea bargaining.
The police regularly negotiate lenient sentences or probation for confessed criminals in order to convict more important criminals. They make deals with all sorts of unsavory people, giving them benefits they don't deserve, because the result is a greater good.
In the Snowden case, an agreement would safeguard the most important of NSA's secrets from other nations' intelligence agencies. It would help ensure that the truly secret information not be exposed. It would protect US interests.
Why would reporters agree to this? Two reasons. One, they actually do want these documents secured while they look for stories to publish. And two, it would be a public demonstration of that desire.
Why wouldn't the government just collect all the documents under the pretense of securing them and then delete them? For the same reason they don't renege on plea bargains: No one would trust them next time. And, of course, because smart reporters will probably keep encrypted backups under their own control.
We're nowhere near the point where this system could be put into practice, but it's worth thinking about how it could work. The government would need to establish a semi-independent group, called, say, a Leak Management unit, which could act as an intermediary. Since it would be isolated from the agencies that were the source of the leak, its officials would be less vested and -- this is important -- less angry over the leak. Over time, it would build a reputation, develop protocols that reporters could rely on. Leaks will be more common in the future, but they'll still be rare. Expecting each agency to develop expertise in this process is unrealistic.
If there were sufficient trust between the press and the government, this could work. And everyone would benefit.
This essay previously appeared on CNN.com.
Fighting patent trolls and corruption with the Magnificent Seven business-model
Stuart.ward.ukI hope this actually happens

My new Locus column, Collective Action, proposes a theory of corruption: the relatively small profits from being a jerk are concentrated, the much larger effects are diffused, which means that the jerks can afford better lawyers and lobbyists than any one of their victims. Since the victims are spread out and don't know each other, it's hard to fight back together.
Then I propose a solution: using Kickstarter-like mechanisms to fight corruption: a website where victims of everything from patent trolls and copyright trolls, all the way up to pollution and robo-signing foreclosures, can find each other and pledge to fund a group defense, rather than paying off the bandits.
It's the Magnificent Seven business model: one year, the villagers stop paying the robbers, and use the money to pay mercenaries to fight the robbers instead.
What would a Kickstarter for Class Action Defense look like? Imagine if you could pledge, ‘‘I promise that I will withhold license fees/settlements for [a bad patent/a fraudulent copyright fee/a copyright troll’s threat] as soon as 100 other victims do the same.’’ Or 1,000. Or 10,000. Hungry, entrepreneurial class-action lawyers could bid for the business, offer opinions on the win-ability of the actions, or even start their own kickstarters (‘‘I promise I will litigate this question until final judgment if 1,000 threat-letter recipients promise to pay me half of what the troll is asking.’’)
Basically, it’s the scene where the villagers decide to stop paying the bandits and offer the next round of protection money to the Magnificent Seven to defend them.
There’s a lot to like about this solution. Once a troll is worried about a pushback from his victims, he’ll need to raise a war-chest, and since the only thing a troll makes is lawsuits, he’ll start sending more threats. Those threats will attract more people to the kickstarter, raising its profile and its search-rank. The more the troll wriggles, the more stuck he becomes.
We could spin out a thousand possible variations on this – a pro-rated refund if the lawyer wins without spending all the money, or preferential shares to early entrants; a traditional plaintiff’s side class-action sister-project that goes after trolls who’ve lost their suits and uses their defeat as the basis for stripping them of every asset to their underwear and redistributing it to victims (and lawyers, of course – though that’s not a bad outcome, since it means lawyers might be willing to spend more on the ‘‘defense’’ part of the action in the hopes of a bigger payout down the line).
Fixing ALL login issues for web service logins with SQRL [Martin]
In the past couple of years we've become accustomed to weekly news of grand scale username and password thefts at major web services. As many people use very insecure passwords that can be cracked in seconds and by using the same passwords for many web services, usernames and passwords have become very insecure. In addition, viruses and Trojan horses try to get username and password combinations directly on PCs to get access to banking web sites and other high value targets. To me it looks like the situation is getting more and more out of control. While two factor authentication (e.g. an SMS with an additional code being sent by the bank before a transaction is made) fixes some of the issues for some web services, it's too cumbersome for everyday logins. But now Steve Gibson, famous for his SpinRite product and perhaps even more for his weekly Security Now podcast has come up with a solution that fixes all of this. Too good to be true? I thought so, too, at first but it seems he's really figured it out.
The core of his solution that he named SQRL (Secure QR Code Login) is that web services no longer store usernames and passwords but just a public key that was sent from the user when he first registered to the web site. For login, the web site sends a random number that is encrypted on the client side with the users secret key to generate a response. On the web service's side the response is decrypted with the public key agreed during initial registration. In other words, the secret password is no longer in the hands of the web service but in the hand of the user. That means that there is no longer a password database with millions of entries worth stealing on the web service's side. As each web service gets a different public key with the SQRL method and a different random number is used for each login, there's no password leakage between services due to the user of the same username and password for different sites as done by many users today to make their life simpler. Also not to underestimate is the advantage that no password has to be typed in, which fixes the issues that simple to remember and easy to crack passwords are used.
On the client side the use of SQRL is straight forward. Either a smartphone is used to scan a QR code on the login page for an out-of-band authentication which is the most secure way to access a web service in case the secret key can be stored securely on the mobile device. Also, implementations are possible with a browser plugin that detects that a web service offers SQRL login and automatically generates the response.
For more, head over to Steve's page that explains the details or listen to the podcast /videocast on the topic where he introduces SQRL starting at around 38 minutes into the podcast. I am amazed and very enthusiastic about it and hope we'll see implementations of this in the wild soon.
On Secrecy
"When everything is classified, then nothing is classified."
I should suppose that moral, political, and practical considerations would dictate that a very first principle of that wisdom would be an insistence upon avoiding secrecy for its own sake. For when everything is classified, then nothing is classified, and the system becomes one to be disregarded by the cynical or the careless, and to be manipulated by those intent on self protection or self-promotion. I should suppose, in short, that the hallmark of a truly effective internal security system would be the maximum possible disclosure, recognizing that secrecy can best be preserved only when credibility is truly maintained.Justice Stewart, New York Times v. United States, 1971.
CCC bust Apple's fingerprint scanner?
Stuart.ward.ukThat was quick...
Conspiracy Theories and the NSA
I've recently seen two articles speculating on the NSA's capability, and practice, of spying on members of Congress and other elected officials. The evidence is all circumstantial and smacks of conspiracy thinking -- and I have no idea whether any of it is true or not -- but it's a good illustration of what happens when trust in a public institution fails.
The NSA has repeatedly lied about the extent of its spying program. James R. Clapper, the director of national intelligence, has lied about it to Congress. Top-secret documents provided by Edward Snowden, and reported on by the Guardian and other newspapers, repeatedly show that the NSA's surveillance systems are monitoring the communications of American citizens. The DEA has used this information to apprehend drug smugglers, then lied about it in court. The IRS has used this information to find tax cheats, then lied about it. It's even been used to arrest a copyright violator. It seems that every time there is an allegation against the NSA, no matter how outlandish, it turns out to be true.
Guardian reporter Glenn Greenwald has been playing this well, dribbling the information out one scandal at a time. It's looking more and more as if the NSA doesn't know what Snowden took. It's hard for someone to lie convincingly if he doesn't know what the opposition actually knows.
All of this denying and lying results in us not trusting anything the NSA says, anything the president says about the NSA, or anything companies say about their involvement with the NSA. We know secrecy corrupts, and we see that corruption. There's simply no credibility, and -- the real problem -- no way for us to verify anything these people might say.
It's a perfect environment for conspiracy theories to take root: no trust, assuming the worst, no way to verify the facts. Think JFK assassination theories. Think 9/11 conspiracies. Think UFOs. For all we know, the NSA might be spying on elected officials. Edward Snowden said that he had the ability to spy on anyone in the U.S., in real time, from his desk. His remarks were belittled, but it turns out he was right.
This is not going to improve anytime soon. Greenwald and other reporters are still poring over Snowden's documents, and will continue to report stories about NSA overreach, lawbreaking, abuses, and privacy violations well into next year. The "independent" review that Obama promised of these surveillance programs will not help, because it will lack both the power to discover everything the NSA is doing and the ability to relay that information to the public.
It's time to start cleaning up this mess. We need a special prosecutor, one not tied to the military, the corporations complicit in these programs, or the current political leadership, whether Democrat or Republican. This prosecutor needs free rein to go through the NSA's files and discover the full extent of what the agency is doing, as well as enough technical staff who have the capability to understand it. He needs the power to subpoena government officials and take their sworn testimony. He needs the ability to bring criminal indictments where appropriate. And, of course, he needs the requisite security clearance to see it all.
We also need something like South Africa's Truth and Reconciliation Commission, where both government and corporate employees can come forward and tell their stories about NSA eavesdropping without fear of reprisal.
Yes, this will overturn the paradigm of keeping everything the NSA does secret, but Snowden and the reporters he's shared documents with have already done that. The secrets are going to come out, and the journalists doing the outing are not going to be sympathetic to the NSA. If the agency were smart, it'd realize that the best thing it could do would be to get ahead of the leaks.
The result needs to be a public report about the NSA's abuses, detailed enough that public watchdog groups can be convinced that everything is known. Only then can our country go about cleaning up the mess: shutting down programs, reforming the Foreign Intelligence Surveillance Act system, and reforming surveillance law to make it absolutely clear that even the NSA cannot eavesdrop on Americans without a warrant.
Comparisons are springing up between today's NSA and the FBI of the 1950s and 1960s, and between NSA Director Keith Alexander and J. Edgar Hoover. We never managed to rein in Hoover's FBI -- it took his death for change to occur. I don't think we'll get so lucky with the NSA. While Alexander has enormous personal power, much of his power comes from the institution he leads. When he is replaced, that institution will remain.
Trust is essential for society to function. Without it, conspiracy theories naturally take hold. Even worse, without it we fail as a country and as a culture. It's time to reinstitute the ideals of democracy: The government works for the people, open government is the best way to protect against government abuse, and a government keeping secrets from its people is a rare exception, not the norm.
This essay originally appeared on TheAtlantic.com.
More on the NSA Commandeering the Internet
If there's any confirmation that the U.S. government has commandeered the Internet for worldwide surveillance, it is what happened with Lavabit earlier this month.
Lavabit is -- well, was -- an e-mail service that offered more privacy than the typical large-Internet-corporation services that most of us use. It was a small company, owned and operated by Ladar Levison, and it was popular among the tech-savvy. NSA whistleblower Edward Snowden among its half-million users.
Last month, Levison reportedly received an order -- probably a National Security Letter -- to allow the NSA to eavesdrop on everyone's e-mail accounts on Lavabit. Rather than "become complicit in crimes against the American people," he turned the service off. Note that we don't know for sure that he received a NSL -- that's the order authorized by the Patriot Act that doesn't require a judge's signature and prohibits the recipient from talking about it -- or what it covered, but Levison has said that he had complied with requests for individual e-mail access in the past, but this was very different.
So far, we just have an extreme moral act in the face of government pressure. It's what happened next that is the most chilling. The government threatened him with arrest, arguing that shutting down this e-mail service was a violation of the order.
There it is. If you run a business, and the FBI or NSA want to turn it into a mass surveillance tool, they believe they can do so, solely on their own initiative. They can force you to modify your system. They can do it all in secret and then force your business to keep that secret. Once they do that, you no longer control that part of your business. You can't shut it down. You can't terminate part of your service. In a very real sense, it is not your business anymore. It is an arm of the vast U.S. surveillance apparatus, and if your interest conflicts with theirs then they win. Your business has been commandeered.
For most Internet companies, this isn't a problem. They are already engaging in massive surveillance of their customers and users -- collecting and using this data is the primary business model of the Internet -- so it's easy to comply with government demands and give the NSA complete access to everything. This is what we learned from Edward Snowden. Through programs like PRISM, BLARNEY and OAKSTAR, the NSA obtained bulk access to services like Gmail and Facebook, and to Internet backbone connections throughout the US and the rest of the world. But if it were a problem for those companies, presumably the government would not allow them to shut down.
To be fair, we don't know if the government can actually convict someone of closing a business. It might just be part of their coercion tactics. Intimidation, and retaliation, is part of how the NSA does business.
Former Qwest CEO Joseph Nacchio has a story of what happens to a large company that refuses to cooperate. In February 2001 -- before the 9/11 terrorist attacks -- the NSA approached the four major US telecoms and asked for their cooperation in a secret data collection program, the one we now know to be the bulk metadata collection program exposed by Edward Snowden. Qwest was the only telecom to refuse, leaving the NSA with a hole in its spying efforts. The NSA retaliated by canceling a series of big government contracts with Qwest. The company has since been purchased by CenturyLink, which we presume is more cooperative with NSA demands.
That was before the Patriot Act and National Security Letters. Now, presumably, Nacchio would just comply. Protection rackets are easier when you have the law backing you up.
As the Snowden whistleblowing documents continue to be made public, we're getting further glimpses into the surveillance state that has been secretly growing around us. The collusion of corporate and government surveillance interests is a big part of this, but so is the government's resorting to intimidation. Every Lavabit-like service that shuts down -- and there have been several -- gives us consumers less choice, and pushes us into the large services that cooperate with the NSA. It's past time we demanded that Congress repeal National Security Letters, give us privacy rights in this new information age, and force meaningful oversight on this rogue agency.
This essay previously appeared in USA Today.
Who Wrote the Pincer Android Trojan?
Stories in this blog’s Breadcrumbs series have sought to comb through clues that point to the possible location and identities of malware authors and purveyors. But from time to time those clues lead definitively back to an individual. In today’s post, we’ll talk with the author of the Pincer Trojan for Android — a 32-year-old programmer at a mobile app development firm in Russia.
 In April, Finnish security firm F-Secure first warned about Trojan:Android/Pincer.A, which comes disguised as a security certificate and is designed to surreptitiously intercept and forward text messages. As F-Secure notes, previous malicious mobile apps pretending to be certificates have been mobile components of banking Trojans aimed at defeating two-factor authentication.
In April, Finnish security firm F-Secure first warned about Trojan:Android/Pincer.A, which comes disguised as a security certificate and is designed to surreptitiously intercept and forward text messages. As F-Secure notes, previous malicious mobile apps pretending to be certificates have been mobile components of banking Trojans aimed at defeating two-factor authentication.
F-Secure researchers observed that Pincer used the IMEI of the victim’s phone as an identifier, and that the Trojan would call home to a control server and report the device’s phone and serial numbers, phone model, carrier and OS version. They also found that Pincer checks to see if it’s being run in a virtual environment, which is a common trick designed to frustrate malware analysis tools used by security researchers.
Interestingly, F-Secure noted that the code within the trojan includes a class called “USSDDumbExtendedNetworkService” — a component that was assigned a seemingly arbitrary variable that F-Secure researchers said was probably either associated with a French Canadian concrete company or the Twitter handle of a young Russian whose Google+ page lists employment as “Android developer”.
I followed up with F-Secure about this post, and learned that the redacted portion of that post — the variable included in that first variant of the Pincer Trojan — was “senneco.com” (Virustotal’s analysis lists it as “com.senneco”). A quick search on Google turns up Twitter and Google+ accounts by this name belonging to a Yuri Shmakov from Novosibirsk, Russia. Shmakov’s Google+ page says he is a developer at Arello-Mobile, a mobile app development firm also in Novosibirsk.
A scan of Shmakov’s accounts turned up the email address senneco@gmail.com. I sent an email to that address, explaining F-Secure’s findings and asking whether the recipient had anything to do with the Pincer Trojan. To my surprise, Shmakov promptly replied that, why yes he had indeed created it as a freelance project.
Shmakov told me that, based on the client’s specifications, he suspected it might ultimately be put to nefarious uses. Even so, he completed the job and signed his work by including his nickname in the app’s code.
“I was working on this app for some months, and I was hoping that it would be really helpful,” Shmakov wrote. “[The] idea of this app is that you can set it up as a spam filter…block some calls and SMS remotely, from a Web service. I hoped that this will be [some kind of] blacklist, with logging about blocked [messages/calls]. But of course, I understood that client [did] not really want this.”
Shmakov said the guy who hired him to write the Android application used the email address alexbort@hush.com. But Shmakov declined to say why he decided to take the job even though he understood that his creation would be used for malicious purposes.
“The most difficult task to understand and to implement was to intercept the USSD execution value without root access,” Shmakov continued, switching to Russian in a second, more academic reply via email. “The related algorithm was a rather complicated one. For example, should you not succeed in transmitting the intercepted SMS over the Internet, then add it to the queue; had it spent too much time in the queue, then send it by SMS, etc. That being said, this is not really relevant to our case. By the way, it may indeed be worth creating such a service – the way I originally imagined it. Especially, having considered the fact that the mobile spam has finally taken over Russia.”
Whoever owns the address alexbort@hush.com did not respond to requests for comment. Update, Aug. 28, 8:55 a.m. ET: Heard from alexbort@hush.com, who was none too happy that I’d posted his email address. Alex wanted me to know that he was the one who really weaponized the Android application that Shmakov created.
“dear Brian., thank you for your email.The developer did not create the malware as his task was to create the legitimate application. having received the source codes i personally redesigned it into malware ( changed interface and added some features and tricks to it as well ). I am professional developer, but dont have sufficient experience in android applications development. P.S. i am very disappointed that you posted contact information in public, Now am receiving bulk spam emails on my email thank you very much for that.”
Original post:
It is extremely common to find malware and cybercrime jobs that are outsourced to freelancers. In their excellent 2011 paper, “Dirty Jobs: The Role of Freelance Labor in Web Service Abuse,” (PDF), researchers from The University of California, San Diego delved into how cybercriminals crowdsource Web abuse. Also, it’s not unusual to see on underground forums individuals hiring out services to design various components of malware operations, from back-end administrative panels to user interfaces for point-and-click malware creation tools. This was the case with the Styx Exploit Pack, although the designers of that crimeware kit clearly had more personal ties to the individuals who were selling the malware.
In the United States, writing malware is a protected form of free speech, but only up to a point. Prosecutors have gone after malware writers who seek to spread their creations or who have created malicious software with full knowledge of how it will be used.
This seems to also be the case in Russia, albeit in a case involving the theft of hundreds of millions of dollars. Earlier this year, authorities there sentenced to prison a number of programmers who were hired to create individual components of the Carberp banking Trojan.” According to an account of the law enforcement action in the Russian news outlet Kommersant, Carberp was coded by a team of about 20-25 people under the age of 30. Most of the men had never met face-to-face. Each worked remotely and was responsible for developing specific modules of the Carberp code, components that were then transmitted to a main development server in Odessa, Ukraine.
Bezos-Backed 10,000 Year Clock Site Preparation and Fabrication Underway
If you were worth a million dollars, you might buy a fine watch to measure time. Rolex, Breitling, Seiko, this watch could run a couple thousand dollars. If you’re Jeff Bezos, you spend $42 million on a 200-foot clock inside a mountain, engineered to withstand Armageddon and tick 10,000 years.
That sounds like a lot of money, but compared to Bezos’ $25.2 billion, it’s akin to our millionaire buying a single Rolex. No big deal for Bezos.
The last time we covered the 10,000 Year Clock project, Bezos was freshly aboard. Along with 3,300 smaller investors, the Long Now Foundation finally had enough money to make their clock tick. Bezos even provided a mountain in Texas for the clock’s setting.
The 10,000 Year Clock will have an 8-foot face, 700-pound gear wheel, 300-pound steel pendulum, and a never-repeating set of 3.65 million distinct chime sequences programmed by 10,000 Year Clock inventor and co-founder, Danny Hillis. Perched atop this apparatus, an orrery will display astronomical positions and the year.
So how close is the foundation to fulfilling their vision? In late 2011, the Long Now team successfully drilled a 500-foot deep, 12.5-foot wide shaft in their Texas mountain. Meanwhile, the foundation’s website is a wealth of clock parts—giant steel wheels and spinning gears—built on a Jack-and-the-Beanstalk scale.
The winder and main differential, key components of the power storage system, were the first parts completed. The clock derives power from visitors physically winding it or from a series of rods that change length as the temperature varies between day and night.
The steel power storage wheels wind a 75-foot geared steel spine, 20 feet of which is already built. Smaller elements (gears and rollers) are titanium with ceramic bearings. Although the system isn’t lubricated, it efficiently converts over 90% of the supplied outside energy into clock energy.
The foundation says they’ll build and install another clock for installation in a mountain in Nevada. But there’s no end date in sight for either location. These clockmakers take the long view—which is, of course, the point. The Long Now Foundation hopes their projects will get people to think about a much longer “now” than they do currently.
For some, the 10,000 Year Clock may frame our place in time like Voyager and Carl Sagan’s “pale blue dot” framed our place in space. (See here for author Michael Chabon’s clock meditation.) More importantly, the Clock of the Long Now gets people thinking about the future.
If the clock’s construction marks civilization’s middle age—halfway between its birth 10,000 years ago and the clock’s 10,000-year future lifespan—are we at the graph’s apex or the midpoint of an upward slope? The late 19th and early 20th centuries were optimistic about the future. Perhaps naively so. But most of the last few decades have been fixated on a “no future” or end of civilization scenario.
Maybe the doomsayers are right, and after civilization’s ultimate demise, some lone druid will live in the mountain, the caretaker of a magical device whose art has long been forgotten. Then again, maybe not. We can’t know the future, but we can imagine it, and in the imagining, create its likeness.
The NSA is Commandeering the Internet
It turns out that the NSA's domestic and world-wide surveillance apparatus is even more extensive than we thought. Bluntly: The government has commandeered the Internet. Most of the largest Internet companies provide information to the NSA, betraying their users. Some, as we've learned, fight and lose. Others cooperate, either out of patriotism or because they believe it's easier that way.
I have one message to the executives of those companies: fight.
Do you remember those old spy movies, when the higher ups in government decide that the mission is more important than the spy's life? It's going to be the same way with you. You might think that your friendly relationship with the government means that they're going to protect you, but they won't. The NSA doesn't care about you or your customers, and will burn you the moment it's convenient to do so.
We're already starting to see that. Google, Yahoo, Microsoft and others are pleading with the government to allow them to explain details of what information they provided in response to National Security Letters and other government demands. They've lost the trust of their customers, and explaining what they do -- and don't do -- is how to get it back. The government has refused; they don't care.
It will be the same with you. There are lots more high-tech companies who have cooperated with the government. Most of those company names are somewhere in the thousands of documents that Edward Snowden took with him, and sooner or later they'll be released to the public. The NSA probably told you that your cooperation would forever remain secret, but they're sloppy. They'll put your company name on presentations delivered to thousands of people: government employees, contractors, probably even foreign nationals. If Snowden doesn't have a copy, the next whistleblower will.
This is why you have to fight. When it becomes public that the NSA has been hoovering up all of your users' communications and personal files, what's going to save you in the eyes of those users is whether or not you fought. Fighting will cost you money in the short term, but capitulating will cost you more in the long term.
Already companies are taking their data and communications out of the US.
The extreme case of fighting is shutting down entirely. The secure e-mail service Lavabit did that last week, abruptly. Ladar Levison, that site's owner, wrote on his homepage: "I have been forced to make a difficult decision: to become complicit in crimes against the American people or walk away from nearly ten years of hard work by shutting down Lavabit. After significant soul searching, I have decided to suspend operations. I wish that I could legally share with you the events that led to my decision."
The same day, Silent Circle followed suit, shutting down their e-mail service in advance of any government strong-arm tactics: "We see the writing the wall, and we have decided that it is best for us to shut down Silent Mail now. We have not received subpoenas, warrants, security letters, or anything else by any government, and this is why we are acting now." I realize that this is extreme. Both of those companies can do it because they're small. Google or Facebook couldn't possibly shut themselves off rather than cooperate with the government. They're too large; they're public. They have to do what's economically rational, not what's moral.
But they can fight. You, an executive in one of those companies, can fight. You'll probably lose, but you need to take the stand. And you might win. It's time we called the government's actions what they really are: commandeering. Commandeering is a practice we're used to in wartime, where commercial ships are taken for military use, or production lines are converted to military production. But now it's happening in peacetime. Vast swaths of the Internet are being commandeered to support this surveillance state.
If this is happening to your company, do what you can to isolate the actions. Do you have employees with security clearances who can't tell you what they're doing? Cut off all automatic lines of communication with them, and make sure that only specific, required, authorized acts are being taken on behalf of government. Only then can you look your customers and the public in the face and say that you don't know what is going on -- that your company has been commandeered.
Journalism professor Jeff Jarvis recently wrote in the Guardian: "Technology companies: now is the moment when you must answer for us, your users, whether you are collaborators in the US government's efforts to 'collect it all -- our every move on the internet -- or whether you, too, are victims of its overreach."
So while I'm sure it's cool to have a secret White House meeting with President Obama -- I'm talking to you, Google, Apple, AT&T, and whoever else was in the room -- resist. Attend the meeting, but fight the secrecy. Whose side are you on?
The NSA isn't going to remain above the law forever. Already public opinion is changing, against the government and their corporate collaborators. If you want to keep your users' trust, demonstrate that you were on their side.
This essay originally appeared on TheAtlantic.com.
Slashdot thread. And a good interview with Lavabit's founder.
FSF raising funds for the Replicant project
Open Letter to David Cameron: Internet Filtering

The Rt Hon David Cameron, MP, Prime Minister
Tuesday the 23rd July 2013
Dear Mr Cameron,
As a movement that includes many technically literate individuals, parents and young people, we are writing to you to express our concerns about your recent announcements about internet filtering. It is the wrong way to tackle the impact that you believe the internet is having on, as you put it, "the innocence of our children".
It is striking that your approach makes dealing with a social problem into a primarily technical exercise to be solved by Internet Service Providers. Many experts have already made clear that the issues you have raised are not just complex, but impossible to deal with effectively with technology alone.
The suggestion that fool-proof filters can be provided to deal with something as difficult to define as obscenity online is foolhardy at best, misleading and damaging at worst. Your proposals will ensure that we don't properly deal with the problems you claim to want to address.
It should have been made clear to you from your advisers that filters will be ineffective and that they cause a number of serious issues in accomplishing what you aim to achieve. Filters will either fail to block the content you would prefer they blocked, leaving parents with a false sense of security, or they will block far more than intended, and will be turned off by many parents so that they can continue to access legitimate content in an unhindered manner.
These points appear to have been accepted in the Government's response to the consultation on parental internet controls, published in December of 2012¹. The approaches outlined in that document; that the government would work with industry, charities and experts in relevant fields through UKCCIS to promote parental engagement and ensure that that parents have options, are the right ones. They are based on your own evidence and seem to be supported by industry. It is also noteworthy that most parents who responded rejected a default-on approach to filtering.
The result of that consultation was one that emphasised informed choice; that the Government would not prescribe detailed solutions to ISPs or parents. Instead it would expect industry to adapt the principles of this approach to their services, systems and devices and would empower parents rather than giving them a false sense of security. We do not understand why you have abandoned this direction.
We urge you to reconsider and refocus your efforts into areas where they can really have an impact. It is vital that you accept the recommendations from your own consultation to ensure parents are well equipped to deal with the issues that you have outlined, using evidence not insinuation to support your assumptions. We would also argue that rather than the potentially harmful and narrow route you seem to be taking, even if it grabs the headlines, you need to ensure that your approach is a holistic one.
It may be more complex, but ensuring that sex education and the teaching of technology in schools is fit for purpose is vital, and needs real support. Ensuring that parents are equipped to properly guide and supervise their children online may be less eye-catching in the media than imposing filters, but it will work.
We would also ask that you provide more support to organisations like the Child Exploitation & Online Protection Centre to track down offenders and bolster support for local government departments that provide support for victims of abuse.
The Internet has been a driver of massive societal change over the last two decades; as a result we have a society that has far more access to information and media than ever before. That situation is not going to change. Ensuring that we give our young people the skills to deal with this new reality, and supporting parents to ensure they are able to properly guide their children in an informed manner is vital.
It is becoming clear to many people that your Coalition, both Conservative and Liberal Democrat members of your government, are failing when it comes to the digital age. You have failed to deliver the frameworks required in education to ensure that we are bringing up a new generation of innovators in technical fields. You have failed to properly invest in the few initiatives that do show promise in developing the UK's digital scene, leaving those that do succeed doing so despite, not because of, your best efforts.
We would ask that you not compound those failures by suggesting technical solutions to societal problems that they cannot solve, but instead listen to those with whom you have consulted. It is right that you should work ensure that there are options available to parents, but to deal with legitimate problems that arise from our society being more connected than ever before, you must adopt an approach that will actually do some good in the long term.
Yours sincerely,

Loz Kaye
Leader
Pirate Party UK
¹ Government Response to Parental Internet Controls (PDF)
--
This letter is also available as a PDF here.
More NSA Code Names
We don't know what they mean, but there are a bunch of NSA code names on LinkedIn profiles.
ANCHORY, AMHS, NUCLEON, TRAFFICTHIEF, ARCMAP, SIGNAV, COASTLINE, DISHFIRE, FASTSCOPE, OCTAVE/CONTRAOCTAVE, PINWALE, UTT, WEBCANDID, MICHIGAN, PLUS, ASSOCIATION, MAINWAY, FASCIA, OCTSKYWARD, INTELINK, METRICS, BANYAN, MARINA
An entirely 3D printed room with crazy patterns and 80 million surfaces
US Offensive Cyberwar Policy
Today, the United States is conducting offensive cyberwar actions around the world.
More than passively eavesdropping, we're penetrating and damaging foreign networks for both espionage and to ready them for attack. We're creating custom-designed Internet weapons, pretargeted and ready to be "fired" against some piece of another country's electronic infrastructure on a moment's notice.
This is much worse than what we're accusing China of doing to us. We're pursuing policies that are both expensive and destabilizing and aren't making the Internet any safer. We're reacting from fear, and causing other countries to counter-react from fear. We're ignoring resilience in favor of offense.
Welcome to the cyberwar arms race, an arms race that will define the Internet in the 21st century.
Presidential Policy Directive 20, issued last October and released by Edward Snowden, outlines US cyberwar policy. Most of it isn't very interesting, but there are two paragraphs about "Offensive Cyber Effect Operations," or OCEO, that are intriguing:
OECO can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging. The development and sustainment of OCEO capabilities, however, may require considerable time and effort if access and tools for a specific target do not already exist.The United States Government shall identify potential targets of national importance where OCEO can offer a favorable balance of effectiveness and risk as compared with other instruments of national power, establish and maintain OCEO capabilities integrated as appropriate with other US offensive capabilities, and execute those capabilities in a manner consistent with the provisions of this directive.
These two paragraphs, and another paragraph about OCEO, are the only parts of the document classified "top secret." And that's because what they're saying is very dangerous.
Cyberattacks have the potential to be both immediate and devastating. They can disrupt communications systems, disable national infrastructure, or, as in the case of Stuxnet, destroy nuclear reactors; but only if they've been created and targeted beforehand. Before launching cyberattacks against another country, we have to go through several steps.
We have to study the details of the computer systems they're running and determine the vulnerabilities of those systems. If we can't find exploitable vulnerabilities, we need to create them: leaving "back doors," in hacker speak. Then we have to build new cyberweapons designed specifically to attack those systems.
Sometimes we have to embed the hostile code in those networks -- these are called "logic bombs" -- to be unleashed in the future. And we have to keep penetrating those foreign networks, because computer systems always change and we need to ensure that the cyberweapons are still effective.
Like our nuclear arsenal during the Cold War, our cyberweapons arsenal must be pretargeted and ready to launch.
That's what Obama directed the US Cyber Command to do. We can see glimpses of how effective we are in Snowden's allegations that the NSA is currently penetrating foreign networks around the world: "We hack network backbones -- like huge Internet routers, basically -- that give us access to the communications of hundreds of thousands of computers without having to hack every single one."
The NSA and the US Cyber Command are basically the same thing. They're both at Fort Meade in Maryland, and they're both led by Gen. Keith Alexander. The same people who hack network backbones are also building weapons to destroy those backbones. At a March Senate briefing, Alexander boasted of creating more than a dozen offensive cyber units.
Longtime NSA watcher James Bamford reached the same conclusion in his recent profile of Alexander and the US Cyber Command (written before the Snowden revelations). He discussed some of the many cyberweapons the US purchases:
According to Defense News' C4ISR Journal and Bloomberg Businessweek, Endgame also offers its intelligence clients -- agencies like Cyber Command, the NSA, the CIA, and British intelligence -- a unique map showing them exactly where their targets are located. Dubbed Bonesaw, the map displays the geolocation and digital address of basically every device connected to the Internet around the world, providing what's called network situational awareness. The client locates a region on the password-protected web-based map, then picks a country and city -- say, Beijing, China. Next the client types in the name of the target organization, such as the Ministry of Public Security's No. 3 Research Institute, which is responsible for computer security -- or simply enters its address, 6 Zhengyi Road. The map will then display what software is running on the computers inside the facility, what types of malware some may contain, and a menu of custom-designed exploits that can be used to secretly gain entry. It can also pinpoint those devices infected with malware, such as the Conficker worm, as well as networks turned into botnets and zombies -- the equivalent of a back door left open...The buying and using of such a subscription by nation-states could be seen as an act of war. 'If you are engaged in reconnaissance on an adversary's systems, you are laying the electronic battlefield and preparing to use it' wrote Mike Jacobs, a former NSA director for information assurance, in a McAfee report on cyberwarfare. 'In my opinion, these activities constitute acts of war, or at least a prelude to future acts of war.' The question is, who else is on the secretive company's client list? Because there is as of yet no oversight or regulation of the cyberweapons trade, companies in the cyber-industrial complex are free to sell to whomever they wish. "It should be illegal," said the former senior intelligence official involved in cyberwarfare. "I knew about Endgame when I was in intelligence. The intelligence community didn't like it, but they're the largest consumer of that business."
That's the key question: How much of what the United States is currently doing is an act of war by international definitions? Already we're accusing China of penetrating our systems in order to map "military capabilities that could be exploited during a crisis." What PPD-20 and Snowden describe is much worse, and certainly China, and other countries, are doing the same.
All of this mapping of vulnerabilities and keeping them secret for offensive use makes the Internet less secure, and these pretargeted, ready-to-unleash cyberweapons are destabilizing forces on international relationships. Rooting around other countries' networks, analyzing vulnerabilities, creating back doors, and leaving logic bombs could easily be construed as acts of war. And all it takes is one overachieving national leader for this all to tumble into actual war.
It's time to stop the madness. Yes, our military needs to invest in cyberwar capabilities, but we also need international rules of cyberwar, more transparency from our own government on what we are and are not doing, international cooperation between governments, and viable cyberweapons treaties. Yes, these are difficult. Yes, it's a long, slow process. Yes, there won't be international consensus, certainly not in the beginning. But even with all of those problems, it's a better path to go down than the one we're on now.
We can start by taking most of the money we're investing in offensive cyberwar capabilities and spend them on national cyberspace resilience. MAD, mutually assured destruction, made sense because there were two superpowers opposing each other. On the Internet there are all sorts of different powers, from nation-states to much less organized groups. An arsenal of cyberweapons begs to be used, and, as we learned from Stuxnet, there's always collateral damage to innocents when they are. We're much safer with a strong defense than with a counterbalancing offense.
This essay originally appeared on CNN.com. It had the title "Has U.S. Started an Internet War?" -- which I had nothing to do with. Almost always, editors choose titles for my essay without asking my opinion -- or telling me beforehand.
EDITED TO ADD: Here's an essay on the NSA's -- or Cyber Command's -- TAO: the Office of Tailored Access Operations. This is the group in charge of hacking China.
According to former NSA officials interviewed for this article, TAO's mission is simple. It collects intelligence information on foreign targets by surreptitiously hacking into their computers and telecommunications systems, cracking passwords, compromising the computer security systems protecting the targeted computer, stealing the data stored on computer hard drives, and then copying all the messages and data traffic passing within the targeted email and text-messaging systems. The technical term of art used by NSA to describe these operations is computer network exploitation (CNE).TAO is also responsible for developing the information that would allow the United States to destroy or damage foreign computer and telecommunications systems with a cyberattack if so directed by the president. The organization responsible for conducting such a cyberattack is US Cyber Command (Cybercom), whose headquarters is located at Fort Meade and whose chief is the director of the NSA, Gen. Keith Alexander.
None of this is new. Read this Seymour Hersh article on this subject from 2010.
Tiny Linux device offers free unlimited DropBox alternative
Crawford: Why mobile web apps are slow
Why privacy regulators are ineffective: an anthropologist’s view
Privacy activists have complained for years that the Information Commissioner is useless, and compared him with captured regulators like the FSA and the Financial Ombudsman. However I’ve come across a paper by a well-known anthropologist that gives a different take on the problem.
Alan Fiske did fieldwork among a tribe in northern Nigeria that has different boundaries for which activities are regulated by communal sharing, authority, tit-for-tat or monetary exchange. For example,labour within the village is always communal; you expect your neighbours to help you fix your house, and you later help them fix theirs. (This exasperated colonialists who couldn’t get the locals to work for cash; the locals for their part imagined that Europeans must present their children with an itemised bill for child-rearing when they reached adulthood.) He has since written several papers on how many of the tensions in human society arise on the boundaries of these domains of sharing, authority, tit-for-tat and the market. The boundaries can vary by culture, by generation and by politics; libertarians are happy to buy and sell organs for transplant, where many people prefer communal sharing, while radical socialists object to some routine market transactions. Indeed regulatory preferences may drive political views.
So far so good. Where it gets interesting is his extensive discussion of taboo transactions across a variety of cultures, and the institutions created to mitigate the discomfort that people feel when something affects more than one sphere of regulation: from extreme cases such as selling a child into slavery so you can feed your other children, through bride-price and blood money, to such everyday things as alimony and deconsecrating a cemetery for development. It turns out there’s a hierarchy of spheres, with sharing generally taking precedence over authority and authority over tit-for-tat, and market pricing following along last. This ordering makes “downhill” transactions easier. Alimony works (you once loved me, so pay me money!) but buying love doesn’t.
It follows that the most toxic trade-offs for politicians to navigate are those that go the wrong way up the hierarchy: increasing the speed limit from 70 to 80 to improve economic efficiency, but at the cost of a few lives, is just too hard. So you obfuscate (ACPO guidelines say you ticket a driver when he exceeds the speed limit by 10%+2 mph; these have the same effect, but don’t seem to come from the minister). But even these are tricky; the road-safety pressure groups can always kick up a fuss as they don’t themselves ever expect to be in a position to have to take such decisions. Criticism is easy and natural.
But in parliaments where parties alternate in power, a growing trend is to create a “sanctuary” for the taboo trade-off to be conducted without the minister touching it. The courts are the oldest such, and in the USA they still do a wider range of things than here. In the UK, new governments set up quangos to give out jobs to their clients, and abolish their predecessor’s. But the issues dealt with by the ICO are maybe too toxic to become part of the spoils system, and the courts might be insufficiently pliable in the face of industry lobbying. Government would not like Facebook to come back to parliament every few years for a new Privacy Act!
So how should a “sanctuary” be run? Alan suggests it should have open consensual decision-making processes involving all the stakeholders, which should be invited to put forward solutions to the problem under consideration from each of the four viewpoints. Thus the organ-donation quango should openly discuss selling organs for cash; barring people who don’t carry a donor card from receiving an organ; making donation compulsory and allocating organs by social status; and appealing to our common humanity. Perhaps I’m old and cynical; but doesn’t that just replicate the social choice problem in a mini-parliament, the selection of whose members now becomes the effective decider? Imagine what it would be like if the ICO were replaced by a jury of three industry lobbyists, three privacy advocates and three retired politicians …
Anyway, I much enjoyed the anthropological viewpoint.
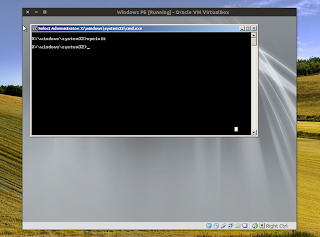
How To Create A Bootable Windows PE ISO Under Linux
Create a bootable Windows PE ISO in Linux
sudo add-apt-repository ppa:nilarimogard/webupd8
sudo apt-get update
sudo apt-get install wimtoolscd
mkdir waiksudo mount KB3AIK_EN.iso $HOME/waika) If you've used a Windows 7 or 8 DVD:
mkwinpeimg --iso --windows-dir=/mnt/windows winpe.isob) If you've used the WAIK (KB3AIK_EN.iso) ISO:
mkwinpeimg --iso --waik-dir=$HOME/waik winpe.isosudo umount $HOME/waikHere's what the "mkwinpeimg" options above do:
- "--iso" - it specifies the tool to make an ISO image instead of a disk image
- "--windows-dir=/mnt/windows" - if using the Windows 7 or 8 DVD only: this is the Windows mount path, usually /mnt/Windows or /mnt/Windows7 but check the path to make sure
- "--waik-dir=$HOME/waik" - if using the WAIK ISO only: this specifies the path to where the WAIK ISO was mounted, $HOME/waik in our case.