
Shared posts
Bill Cosby Attacks Disrespectful Behavior, Skyrocketing Crime Rate Among Elderly Black Male Comedians
Fucking Idiot Has Perfect GIF For That

SAN JOSE, CA—Reveling at the opportunity to respond to an online post with the quintessential short, silent video loop, local fucking idiot Greg Knott told reporters Thursday that he has the perfect GIF for that. “Oh, man, this is totally spot-on,” announced the knuckle-dragging dumbass whose very existence is a…
Unquestioned Alpha Of The Bathroom: This Guy Has BOTH Hands Up On The Wall Over The Urinal And Is Letting Loose A Kingly Sigh While Taking An Absolutely Marathon Piss

If you were wondering who exactly is the head honcho of this restroom, look no further, because we’ve officially found him: This guy has BOTH of his hands up on the wall over the urinal and is letting loose a kingly sigh while taking an absolutely marathon piss.
Job Candidate Awaiting Interviewer Just Smiling, Making Enthusiastic Eye Contact With Every Passerby In Lobby
Spider-Man: Far From Home to swing into theaters just 2 months after Avengers 4
adamczSpider-Man is swinging into theaters
We aren’t going to have to wait long to find out what the Marvel Cinematic Universe looks like in a post-Thanos world; Sony announced today that it’s setting a July 2019 release date for the upcoming Spider-Man sequel, Far From Home, the first MCU movie to take place in a post-Avengers 4, post-“Phase 3" world.
Melania Trump: ‘My Fat Piece-Of-Shit Husband Who Should Go Kill Himself Needs To Stop Bullying People Online’
Millions Of White Nationalists Gather In Streets, Offices Around Country To Normally Go About Day

WASHINGTON—In a massive, simultaneous nationwide demonstration of support for white ethnic supremacy, millions of white nationalists gathered in streets and offices around the United States Monday to go about their normal routines. Proponents of the nativist movement that promotes the racial superiority and purity of…
Windows Toolbar, Mouse Cursor Visible Throughout Memorial Service Slideshow
Qatar Unveils Indentured Mascot For 2022 World Cup
Old Lady At Parade Flapping Little American Flag Like A Motherfucker
FBI: Kindly Reboot Your Router Now, Please
The Federal Bureau of Investigation (FBI) is warning that a new malware threat has rapidly infected more than a half-million consumer devices. To help arrest the spread of the malware, the FBI and security firms are urging home Internet users to reboot routers and network-attached storage devices made by a range of technology manufacturers.
The growing menace — dubbed VPNFilter — targets Linksys, MikroTik, NETGEAR and TP-Link networking equipment in the small and home office space, as well as QNAP network-attached storage (NAS) devices, according to researchers at Cisco.

Experts are still trying to learn all that VPNFilter is built to do, but for now they know it can do two things well: Steal Web site credentials; and issue a self-destruct command, effectively rendering infected devices inoperable for most consumers.
Cisco researchers said they’re not yet sure how these 500,000 devices were infected with VPNFilter, but that most of the targeted devices have known public exploits or default credentials that make compromising them relatively straightforward.
“All of this has contributed to the quiet growth of this threat since at least 2016,” the company wrote on its Talos Intelligence blog.
The Justice Department said last week that VPNFilter is the handiwork of “APT28,” the security industry code name for a group of Russian state-sponsored hackers also known as “Fancy Bear” and the “Sofacy Group.” This is the same group accused of conducting election meddling attacks during the 2016 U.S. presidential race.
“Foreign cyber actors have compromised hundreds of thousands of home and office routers and other networked devices worldwide,” the FBI said in a warning posted to the Web site of the Internet Crime Complaint Center (IC3). “The actors used VPNFilter malware to target small office and home office routers. The malware is able to perform multiple functions, including possible information collection, device exploitation, and blocking network traffic.”
According to Cisco, here’s a list of the known affected devices:
LINKSYS DEVICES:
E1200
E2500
WRVS4400N
MIKROTIK ROUTEROS VERSIONS FOR CLOUD CORE ROUTERS:
1016
1036
1072
NETGEAR DEVICES:
DGN2200
R6400
R7000
R8000
WNR1000
WNR2000
QNAP DEVICES:
TS251
TS439 Pro
Other QNAP NAS devices running QTS software
TP-LINK DEVICES:
R600VPN
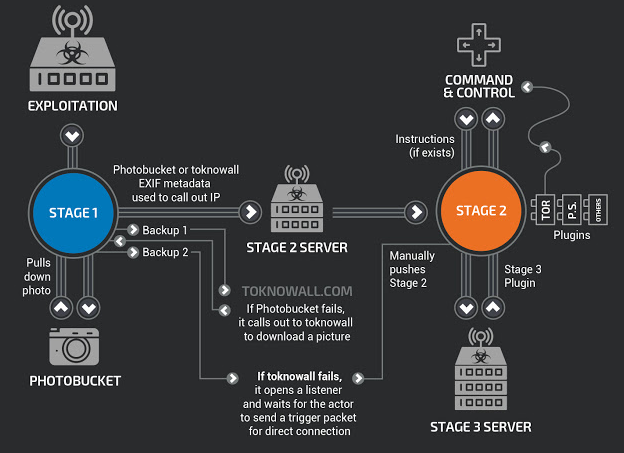
Image: Cisco
Unfortunately, there is no easy way to tell if your device is infected. If you own one of these devices and it is connected to the Internet, you should reboot (or unplug, wait a few seconds, replug) the device now. This should wipe part of the infection, if there is one. But you’re not out of the woods yet.
Cisco said part of the code used by VPNFilter can still persist until the affected device is reset to its factory-default settings. Most modems and DVRs will have a tiny, recessed button that can only be pressed with something small and pointy, such as a paper clip. Hold this button down for at least 10 seconds (some devices require longer) with the device powered on, and that should be enough to reset the device back to its factory-default settings. In some cases, you may need to hold the tiny button down and keep it down while you plug in the power cord, and then hold it for 30 seconds.
After resetting the device, you’ll need to log in to its administrative page using a Web browser. The administrative page of most commercial routers can be accessed by typing 192.168.1.1, or 192.168.0.1 into a Web browser address bar. If neither of those work, try looking up the documentation at the router maker’s site, or checking to see if the address is listed here. If you still can’t find it, open the command prompt (Start > Run/or Search for “cmd”) and then enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
Once you’re there, make sure you’ve changed the factory-default password that allows you to log in to the device (pick something strong that you can remember).
You’ll also want to make sure your device has the latest firmware updates. Most router Web interfaces have a link or button you click to check for newer device firmware. If there are any updates available, install those before doing anything else.
If you’ve reset the router’s settings, you’ll also want to encrypt your connection if you’re using a wireless router (one that broadcasts your modem’s Internet connection so that it can be accessed via wireless devices, like tablets and smart phones). WPA2 is the strongest encryption technology available in most modern routers, followed by WPA and WEP (the latter is fairly trivial to crack with open source tools, so don’t use it unless it’s your only option).
But even users who have a strong router password and have protected their wireless Internet connection with a strong WPA2 passphrase may have the security of their routers undermined by security flaws built into these routers. At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
However, WPS also may expose routers to easy compromise. Read more about this vulnerability here. If your router is among those listed as using WPS, see if you can disable WPS from the router’s administration page. If you’re not sure whether it can be, or if you’d like to see whether your router maker has shipped an update to fix the WPS problem on their hardware, check this spreadsheet.
Turning off any remote administration features that may be turned on by default is always a good idea, as is disabling Universal Plug and Play (UPnP), which can easily poke holes in your firewall without you knowing it). However, Cisco researchers say there is no indication that VPNFilter uses UPnP.
For more tips on how to live with your various Internet of Things (IoT) devices without becoming a nuisance to yourself or the Internet at large, please see Some Basic Rules for Securing Your IoT Stuff.
Update, June 2, 10:30 a.m. ET: Netgear provided the following statement about VPNFilter:
To protect against this possible malware, we strongly advise all NETGEAR router owners to take the following steps:
• Make sure that you are running the latest firmware on your NETGEAR router. Firmware updates include important security fixes and upgrades. For more information, see How do I update my NETGEAR router firmware using the Check button in the router web interface?.
• Make sure that you have changed your default admin password. For more information, see How do I change the admin password on my NETGEAR router?.
• Make sure that remote management is turned off on your router. Remote management is turned off by default and can only be turned on in your router’s advanced settings.To make sure that remote management is turned off on your router:
1. On a computer that is part of your home network, type http://www.routerlogin.net in the address bar of your browser and press Enter.
2. Enter your admin user name and password and click OK.
If you never changed your user name and password after setting up your router, the user name is admin and the password is password.
3. Click Advanced > Remote Management.
4. If the check box for Turn Remote Management On is selected, clear it and click Apply to save your changes.
If the check box for Turn Remote Management On is not selected, you do not need to take any action.NETGEAR is investigating and will update this advisory as more information becomes available.
Study: Human Anxiety Highest When Sitting In Wrong Seat At Concert

CHAPEL HILL, NC—Confirming the long-theorized connection between human nervousness and the attempt to find a better view while in a public space, a study published Tuesday by the Department of Psychology and Neuroscience at the University of North Carolina found that human anxiety is highest when sitting in the wrong…
Man Silently Eating Personal Pan Pizza Alone In Corner Of Airport Unaware This Will Be Best Part Of 7-Day Vacation

INDIANAPOLIS—Quietly chewing on a piece of crust as he waited for his connecting flight to arrive, local man Brett Harding silently ate a personal pizza alone in a corner at the Indianapolis International Airport Wednesday, all while having no idea that it would be the best part of his upcoming seven-day vacation.…
why dose Mario were a hat because he is bold
why dose Mario were a hat
because he is bold
Half-Empty Bottle Of Olde English Left On Church Steps Must Be Offering To God
adamczSharing this because they messed up pairing the headline with the image and soon after took it down
Supply Chain Migration
Don’t Give Away Historic Details About Yourself
Social media sites are littered with seemingly innocuous little quizzes, games and surveys urging people to reminisce about specific topics, such as “What was your first job,” or “What was your first car?” The problem with participating in these informal surveys is that in doing so you may be inadvertently giving away the answers to “secret questions” that can be used to unlock access to a host of your online identities and accounts.
I’m willing to bet that a good percentage of regular readers here would never respond — honestly or otherwise — to such questionnaires (except perhaps to chide others for responding). But I thought it was worth mentioning because certain social networks — particularly Facebook — seem positively overrun with these data-harvesting schemes. What’s more, I’m constantly asking friends and family members to stop participating in these quizzes and to stop urging their contacts to do the same.
On the surface, these simple questions may be little more than an attempt at online engagement by otherwise well-meaning companies and individuals. Nevertheless, your answers to these questions may live in perpetuity online, giving identity thieves and scammers ample ammunition to start gaining backdoor access to your various online accounts.
Consider, for example, the following quiz posted to Facebook by San Benito Tire Pros, a tire and auto repair shop in California. It asks Facebook users, “What car did you learn to drive stick shift on?”
I hope this is painfully obvious, but for many people the answer will be the same as to the question, “What was the make and model of your first car?”, which is one of several “secret questions” most commonly used by banks and other companies to let customers reset their passwords or gain access to the account without knowing the password.
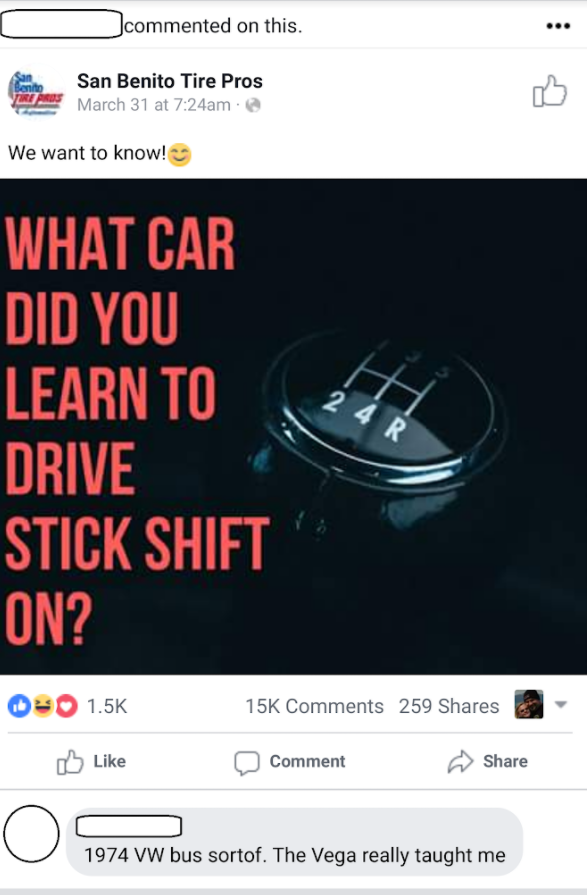
This simple one-question quiz has been shared more than 250 times on Facebook since it was posted a week ago. Thousands of Facebook users responded in earnest, and in so doing linked their profile to the answer.
Probably the most well-known and common secret question, “what was the name of your first pet,” comes up in a number of Facebook quizzes that, incredibly, thousands of people answer willingly and (apparently) truthfully. When I saw this one I was reminded of this hilarious 2007 Daily Show interview wherein Jon Stewart has Microsoft co-founder Bill Gates on and tries to slyly ask him the name of his first pet.

Almost 5,000 Facebook users answered this common password reset secret question.
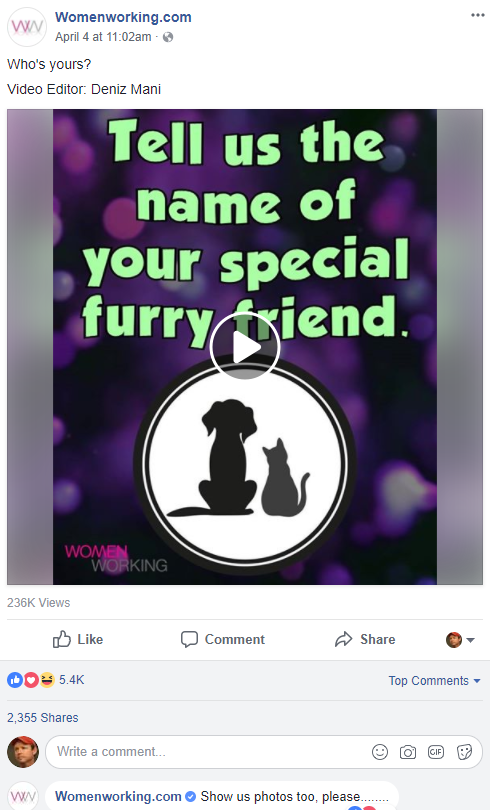
Womenworking.com asked a variation on this same question of their huge Facebook following and received an impressive number of responses:
Here’s a great one from springchicken.co.uk, an e-commerce site in the United Kingdom. It asks users to publicly state the answer to yet another common secret question: “What street did you grow up on?”
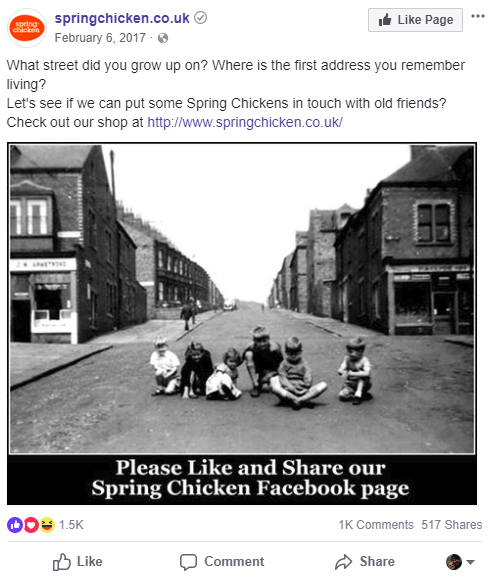
More than 500 Facebook users have shared this quiz with their network, and hundreds more shared the answer using their real names and links to their profiles.
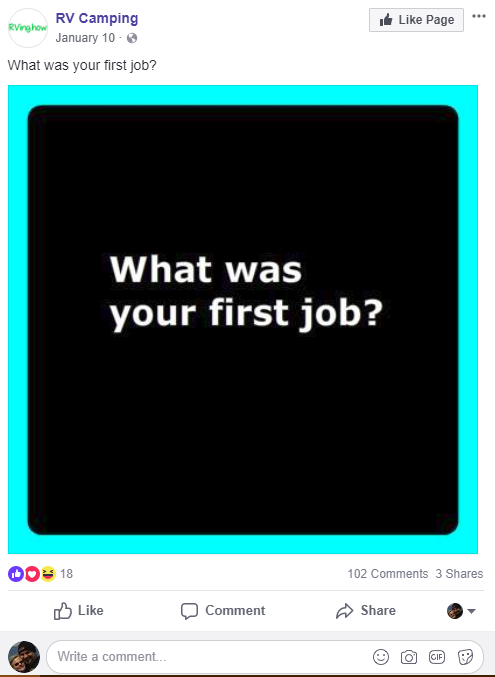
This question, from the Facebook account of Rving.how — a site for owners of recreational vehicles — asks: “What was your first job?” How the answer to this question might possibly relate to RV camping is beyond me, but that didn’t stop people from responding.
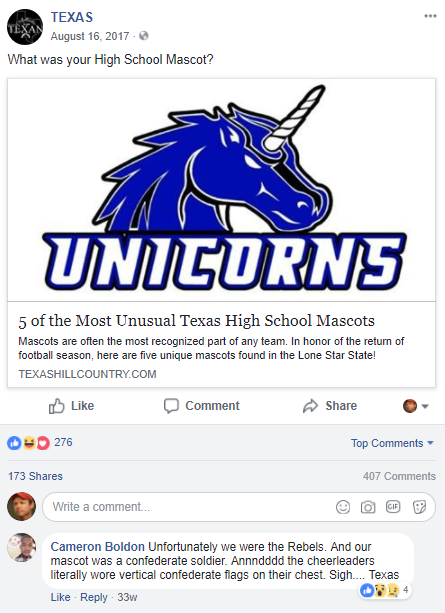
The question, “What was your high school mascot” is another common secret question, and yet you can find this one floating around lots of Facebook profiles:
Among the most common secret questions is, “Where did you meet your spouse or partner?” Loads of people like to share this information online as well, it seems:
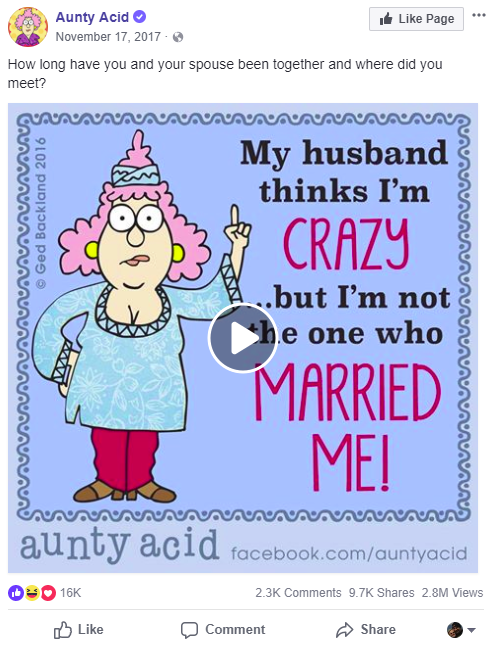
This common secret question has been shared on Facebook almost 10,000 times and has garnered more than 2,300 responses.
Here’s another gem from the Womenworking Facebook page. Who hasn’t had to use the next secret question at some point? Answering this truthfully — in a Facebook quiz or on your profile somewhere — is a bad idea.
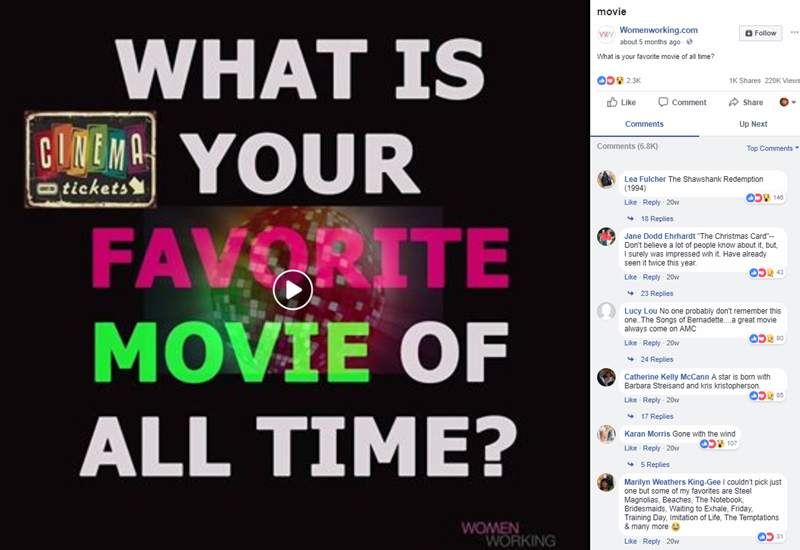
Incredibly, 6,800 Facebook users answered this question.
Do you remember your first grade teacher’s name? Don’t worry, if you forget it after answering this question, Facebook will remember it for you:

I’ve never seen a “what was the first concert you ever saw” secret question, but it is unique as secret questions go and I wouldn’t be surprised if some companies use this one. “What is your favorite band?” is definitely a common secret question, however:
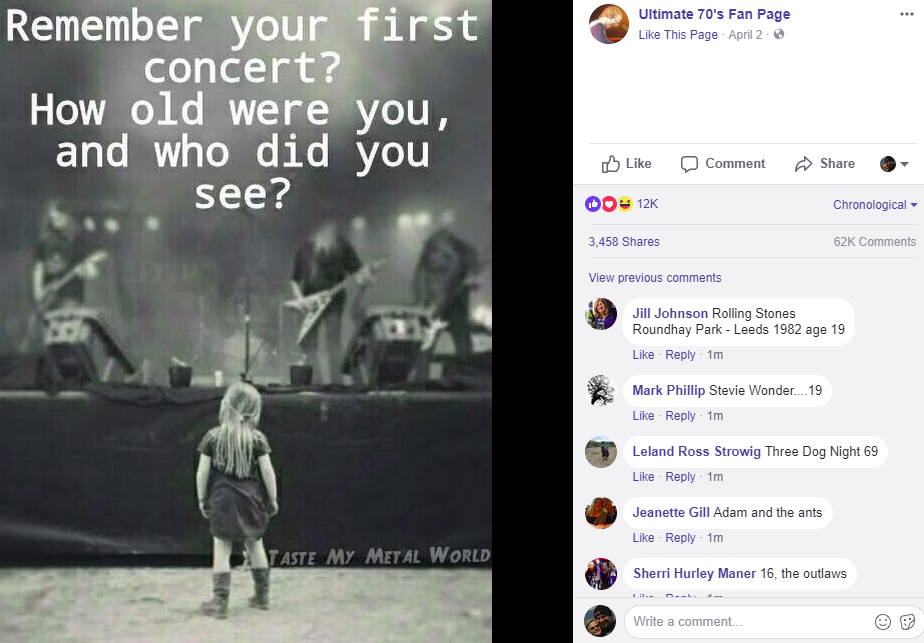
Giving away information about yourself, your likes and preferences, etc., can lead to all kinds of unexpected consequences. This practice may even help turn the tide of elections. Just take the ongoing scandal involving Cambridge Analytica, which reportedly collected data on more than 50 million Facebook users without their consent and then used this information to build behavioral models to target potential voters in various political campaigns.
I hope readers don’t interpret this story as KrebsOnSecurity endorsing secret questions as a valid form of authentication. In fact, I have railed against this practice for years, precisely because the answers often are so easily found using online services and social media profiles.
But if you must patronize a company or service that forces you to select secret questions, I think it’s a really good idea not to answer them truthfully. Just make sure you have a method for remembering your phony answer, in case you forget the lie somewhere down the road.
Many thanks to RonM for assistance with this post.
Panerabread.com Leaks Millions of Customer Records
Panerabread.com, the Web site for the American chain of bakery-cafe fast casual restaurants by the same name, leaked millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card number — for at least eight months before it was yanked offline earlier today, KrebsOnSecurity has learned.
The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com. The St. Louis-based company, which has more than 2,100 retail locations in the United States and Canada, allows customers to order food online for pickup in stores or for delivery.
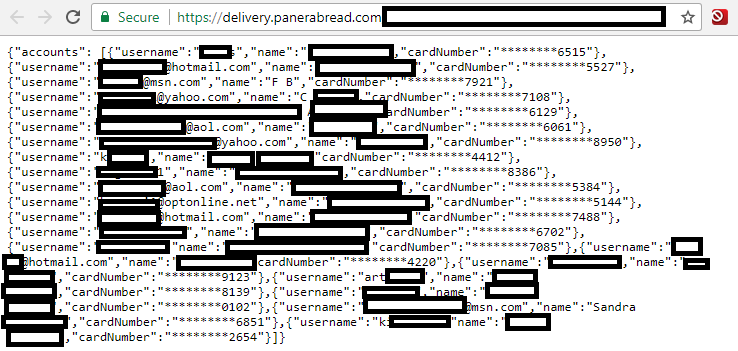
Redacted records from Panera’s site, which let anyone search by a variety of customer attributes, including phone number, email address, physical address or loyalty account number. In this example, the phone number was a main line at an office building where many different employees apparently registered to order food online.
KrebsOnSecurity learned about the breach earlier today after being contacted by security researcher Dylan Houlihan, who said he initially notified Panera about customer data leaking from its Web site back on August 2, 2017.
A long message thread that Houlihan shared between himself and Panera indicates that Mike Gustavison, Panera’s director of information security, initially dismissed Houlihan’s report as a likely scam. A week later, however, those messages suggest that the company had validated Houlihan’s findings and was working on a fix.
“Thank you for the information we are working on a resolution,” Gustavison wrote.
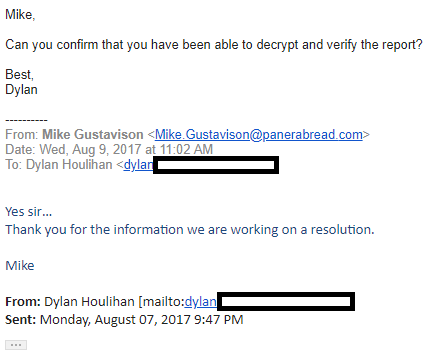
Panera was alerted about the data leakage in early August 2017, and said it was fixing the problem then.
Fast forward to early this afternoon — exactly eight months to the day after Houlihan first reported the problem — and data shared by Houlihan indicated the site was still leaking customer records in plain text. Worse still, the records could be indexed and crawled by automated tools with very little effort.
For example, some of the customer records include unique identifiers that increment by one for each new record, making it potentially simple for someone to scrape all available customer accounts. The format of the database also lets anyone search for customers via a variety of data points, including by phone number.
“Panera Bread uses sequential integers for account IDs, which means that if your goal is to gather as much information as you can instead about someone, you can simply increment through the accounts and collect as much as you’d like, up to and including the entire database,” Houlihan said.
Asked whether he saw any indication that Panera ever addressed the issue he reported in August 2017 until today, Houlihan said no.
“No, the flaw never disappeared,” he said. “I checked on it every month or so because I was pissed.”
Shortly after KrebsOnSecurity spoke briefly with Panera’s chief information officer John Meister by phone today, the company briefly took the Web site offline. As of this publication, the site is back online but the data referenced above no longer appears to be reachable.

Panera took its site down today after being notified by KrebsOnSecurity.
Another data point exposed in these records included the customer’s Panera loyalty card number, which could potentially be abused by scammers to spend prepaid accounts or to otherwise siphon value from Panera customer loyalty accounts.
It is not clear yet exactly how many Panera customer records may have been exposed by the company’s leaky Web site, but incremental customer numbers indexed by the site suggest that number may be higher than seven million. It’s also unclear whether any Panera customer account passwords may have been impacted.
In a written statement, Panera said it had fixed the problem within less than two hours of being notified by KrebsOnSecurity. But Panera did not explain why it appears to have taken the company eight months to fix the issue after initially acknowledging it privately with Houlihan.
“Panera takes data security very seriously and this issue is resolved,” the statement reads. “Following reports today of a potential problem on our website, we suspended the functionality to repair the issue. Our investigation is continuing, but there is no evidence of payment card information nor a large number of records being accessed or retrieved.”
Update, 8:40 p.m. ET: Almost minutes after this story was published, Panera gave a statement to Fox News downplaying the severity of this breach, stating that only 10,000 customer records were exposed. Almost in an instant, multiple sources — especially @holdsecurity — pointed out that Panera had basically “fixed” the problem by requiring people to log in to a valid user account at panerabread.com in order to view the exposed customer records (as opposed to letting just anyone with the right link access the records).
Subsequent links shared by Hold Security indicate that this data breach may be far larger than the 7 million customer records initially reported as exposed in this story. The vulnerabilities also appear to have extended to Panera’s commercial division which serves countless catering companies. At last count, the number of customer records exposed in this breach appears to exceed 37 million. Thank you to Panera for pointing out the shortcomings of our research. As of this update, the entire Web site panerabread.com is offline.
For anyone interested in my response to Panera’s apparent end-run around my reporting, see my tweets.
There’s Still No Such Thing As Sound Science
Last week saw a major development in how the Environmental Protection Agency plans to engage with scientific evidence. On Friday, EPA Administrator Scott Pruitt gave The Daily Caller an exclusive interview and said he would soon end the agency’s use of what he called “secret science” — research whose underlying, raw data sets are not released publicly. That sounds simple enough, but it would preclude the agency from relying on a great deal of scientific knowledge.
According to the Daily Caller story, Pruitt’s upcoming policy is inspired by the Honest Act, a congressional bill championed by Republican Rep. Lamar Smith of Texas. If that’s the case — the EPA has not responded to a request for comment — it would drastically limit the kind of evidence the agency uses for its decision-making. For example, it appears as though the policy would preclude the use of public health research that included confidential personal information about study subjects.
An editorial in the journal Science concluded that the Honest Act is, ironically, “dishonest—an attempt by politicians to override scientific judgment and dictate narrow standards by which science is deemed valuable for policy.” The legislation is opposed by more than a dozen scientific organizations. It appears that Pruitt is now moving ahead with this approach, even as the legislation has stalled.
Pruitt’s planned move appears to be a continuation of many conservatives’ push for “sound science.” We took an in-depth look at the concept of “sound science” in December: The problem is that there’s no such thing. The idea was pioneered by the tobacco industry to undercut research showing that its products were harmful. The doubt-makers’ trick was to insist that policy be based solely on “sound science,” and then to define “sound” in a way that ensures that nothing will ever qualify.
“Under Mr. Pruitt’s approach to science, the E.P.A. would be turning its back on its mandate to ‘protect human health and the environment,’” wrote two former top EPA officials — Gina McCarthy and Janet McCabe — in the New York Times.
Although Pruitt’s new policy is ostensibly about transparency, his agency has not been transparent in disclosing it to the public. Rather than put out a traditional news release with information about the change, the EPA published a two-sentence press release saying that “Environmental Protection Agency (EPA) Administrator Scott Pruitt will soon end his agency’s use of ‘secret science’ to craft regulations,” and pointed readers to the Daily Caller’s story.
In response, the National Association of Science Writers27, sent a letter to EPA Associate Administrator Liz Bowman asking her to “take steps immediately to prevent this unprofessional and unethical behavior from occurring again.” The EPA’s promotion of a media outlet’s article in place of answering questions from reporters, the NASW letter said, blocks “the dissemination of information about a potentially significant policy change.”
But the policy’s rollout aside, Pruitt’s move is an example of a strategy that has a long history: Turning scientific values against science.
Read more: There’s No Such Thing As ‘Sound Science’
Woman In Commercial Doing Yoga To Narration Of Drug's Fatal Side Effects
Kansas Man Killed In ‘SWATting’ Attack
A 28-year-old Kansas man was shot and killed by police officers on the evening of Dec. 28 after someone fraudulently reported a hostage situation ongoing at his home. The false report was the latest in a dangerous hoax known as “swatting,” wherein the perpetrator falsely reports a dangerous situation at an address with the goal of prompting authorities to respond to that address with deadly force. This particular swatting reportedly originated over a $1.50 wagered match in the online game Call of Duty. Compounding the tragedy is that the man killed was an innocent party who had no part in the dispute.
The following is an analysis of what is known so far about the incident, as well as a brief interview with the alleged and self-professed perpetrator of this crime.
It appears that the dispute and subsequent taunting originated on Twitter. One of the parties to that dispute — allegedly using the Twitter handle “SWauTistic” — threatened to swat another user who goes by the nickname “7aLeNT“. @7aLeNT dared someone to swat him, but then tweeted an address that was not his own.
Swautistic responded by falsely reporting to the Kansas police a domestic dispute at the address 7aLenT posted, telling the authorities that one person had already been murdered there and that several family members were being held hostage.
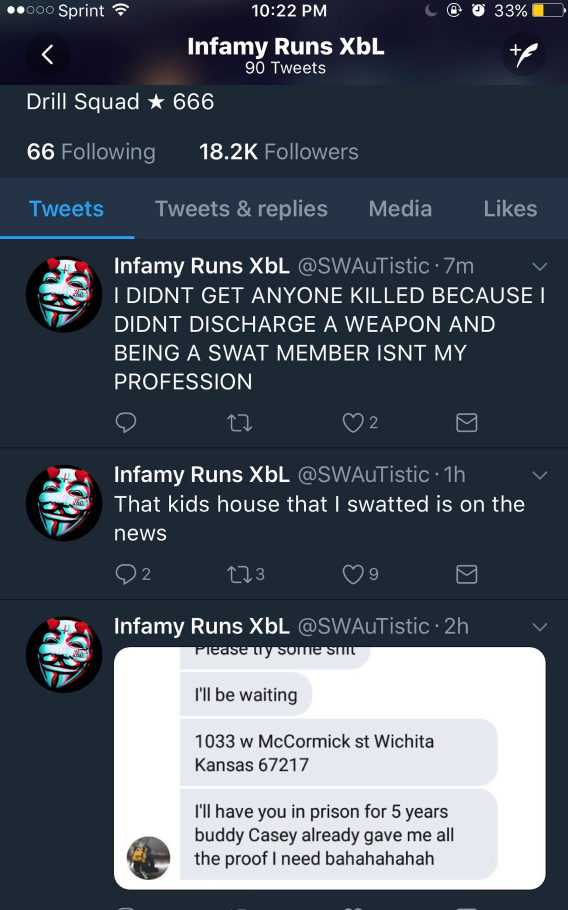
Image courtesey @mattcarries
A story in the Wichita Eagle says officers responded to the 1000 block of McCormick and got into position, preparing for a hostage situation.
“A male came to the front door,” Livingston said. “As he came to the front door, one of our officers discharged his weapon.”
“Livingston didn’t say if the man, who was 28, had a weapon when he came to the door, or what caused the officer to shoot the man. Police don’t think the man fired at officers, but the incident is still under investigation, he said. The man, who has not been identified by police, died at a local hospital.
“A family member identified that man who was shot by police as Andrew Finch. One of Finch’s cousins said Finch didn’t play video games.”
Not long after that, Swautistic was back on Twitter saying he could see on television that the police had fallen for his swatting attack. When it became apparent that a man had been killed as a result of the swatting, Swautistic tweeted that he didn’t get anyone killed because he didn’t pull the trigger (see image above).
Swautistic soon changed his Twitter handle to @GoredTutor36, but KrebsOnSecurity managed to obtain several weeks’ worth of tweets from Swautistic before his account was renamed. Those tweets indicate that Swautistic is a serial swatter — meaning he has claimed responsibility for a number of other recent false reports to the police.
Among the recent hoaxes he’s taken credit for include a false report of a bomb threat at the U.S. Federal Communications Commission (FCC) that disrupted a high-profile public meeting on the net neutrality debate. Swautistic also has claimed responsibility for a hoax bomb threat that forced the evacuation of the Dallas Convention Center, and another bomb threat at a high school in Panama City, Fla, among others.
After tweeting about the incident extensively this afternoon, KrebsOnSecurity was contacted by someone in control of the @GoredTutor36 Twitter account. GoredTutor36 said he’s been the victim of swatting attempts himself, and that this was the reason he decided to start swatting others.
He said the thrill of it “comes from having to hide from police via net connections.” Asked about the FCC incident, @GoredTutor36 acknowledged it was his bomb threat. “Yep. Raped em,” he wrote.
“Bomb threats are more fun and cooler than swats in my opinion and I should have just stuck to that,” he wrote. “But I began making $ doing some swat requests.”
Asked whether he feels remorse about the Kansas man’s death, he responded “of course I do.”
But evidently not enough to make him turn himself in.
“I won’t disclose my identity until it happens on its own,” the user said in a long series of direct messages on Twitter. “People will eventually (most likely those who know me) tell me to turn myself in or something. I can’t do that; though I know its [sic] morally right. I’m too scared admittedly.”
Update, 7:15 p.m.: A recording of the call to 911 operators that prompted this tragedy can be heard at this link. The playback of the recorded emergency calls starts around 10 minutes into the video.
Update, Dec. 30, 8:06 a.m. ET: Police in Los Angeles reportedly have arrested 25-year-old Tyler Raj Barriss in connection with the swatting attack.
ANALYSIS
As a victim of my own swatting attack back in 2013, I’ve been horrified to watch these crimes only increase in frequency ever since — usually with little or no repercussions for the person or persons involved in setting the schemes in motion. Given that the apparent perpetrator of this crime seems eager for media attention, it seems likely he will be apprehended soon. My guess is that he is a minor and will be treated with kid gloves as a result, although I hope I’m wrong on both counts.
Let me be crystal clear on a couple of points. First off, there is no question that police officers and first responders across the country need a great deal more training to bring the number of police shootings way down. That is undoubtedly a giant contributor to the swatting epidemic.
Also, all police officers and dispatchers need to be trained on what swatting is, how to spot the signs of a hoax, and how to minimize the risk of anyone getting harmed when responding to reports about hostage situations or bomb threats. Finally, officers of the peace who are sworn to protect and serve should use deadly force only in situations where there is a clear and immediate threat. Those who jump the gun need to be held accountable as well.
But that kind of reform isn’t going to happen overnight. Meanwhile, knowingly and falsely making a police report that results in a SWAT unit or else heavily armed police response at an address is an invitation for someone to get badly hurt or killed. These are high-pressure situations and in most cases — as in this incident — the person opening the door has no idea what’s going on. Heaven protect everyone at the scene if the object of the swatting attack is someone who is already heavily armed and confused enough about the situation to shoot anything that comes near his door.
In some states, filing a false police report is just a misdemeanor and is mainly punishable by fines. However, in other jurisdictions filing a false police report is a felony, and I’m afraid it’s long past time for these false reports about dangerous situations to become a felony offense in every state. Here’s why.
If making a fraudulent report about a hostage situation or bomb threat is a felony, then if anyone dies as a result of that phony report they can legally then be charged with felony murder. Under the doctrine of felony murder, when an offender causes the death of another (regardless of intent) in the commission of a dangerous crime, he or she is guilty of murder.
Too often, however, the perpetrators of these crimes are minors, and even when they’re caught they are frequently given a slap on the wrist. Swatting needs to stop, and unfortunately as long as there are few consequences for swatting someone, it will continue to be a potentially deadly means for gaining e-fame and for settling childish and pointless ego squabbles.
Black Panther is leaping over ticket presale records
adamczBlack Panther is leaping into theaters

If beating advance ticket sales for previous buzzed-about superhero films are like flipping over cars during a late-night road chase sequence in a movie trailer, then Black Panther is like...Black Panther, leaping ahead of those vehicles while a Run The Jewels track plays behind it.
T.J. Miller accused of physical and sexual assault in disturbing Daily Beast exposé
adamczNO WAY. THIS GUY?
New ‘Star Wars’ Film Once Again Disappoints Die-Hard Nien Nunb Fans

BOSTON—Expressing frustration at the science fiction franchise’s repeated failure to deliver on their expectations, die-hard fans of Star Wars character Nien Nunb were once again disappointed by new film The Last Jedi, sources confirmed Thursday. “Christ, I came into Episode VIII thinking they’d at least delve deeper…
By Yourself
what is the best thing to say when you live by yourself and you get home?
honey i’m home, just kiding, i live on my own.
MacOS High Sierra Users: Change Root Password Now
A newly-discovered flaw in macOS High Sierra — Apple’s latest iteration of its operating system — allows anyone with local (and, apparently in some cases, remote) access to the machine to log in as the all-powerful “root” user without supplying a password. Fortunately, there is a simple fix for this until Apple patches this inexplicable bug: Change the root account’s password now.
Update, Nov. 29, 11:40 a.m. ET: Apple has released a patch for this flaw. More information on the fix is here. The update is available via the App Store app on your Mac. Click Updates in the App Store toolbar, then use the Update buttons to download and install any updates listed.
Original story:
For better or worse, this glaring vulnerability was first disclosed today on Twitter by Turkish software developer Lemi Orhan Ergin, who unleashed his findings onto the Internet with a tweet to @AppleSupport:
“Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as “root” with empty password after clicking on login button several times. Are you aware of it @Apple?”
High Sierra users should be able to replicate the exploit by accessing System Preferences, then Users & Groups, and then click the lock to make changes. Type “root” with no password, and simply try that several times until the system relents and lets you in.
How does one change the root password? It’s simple enough. Open up a Terminal (in the Spotlight search box just type “terminal”) and type “sudo passwd root”.
Many people responding to that tweet said they were relieved to learn that this extremely serious oversight by Apple does not appear to be exploitable remotely. However, sources who have tested the bug say it can be exploited remotely if a High Sierra user a) has not changed the root password yet and b) has enabled “screen sharing” on their Mac.
Likewise, multiple sources have now confirmed that disabling the root account does not fix the problem because the exploit actually causes the account to be re-enabled.
There may be other ways that this vulnerability can be exploited: I’ll update this post as more information becomes available. But for now, if you’re using macOS High Sierra, take a moment to change the root password now, please.









