syndicatedragon
Shared posts
Get out the hand sanitizer, flu season gears up
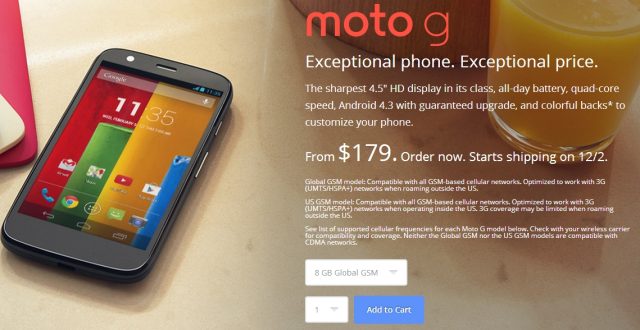
Review: Google’s $179 Moto G puts every single cheap Android phone to shame

The Moto G isn't much like the high-end handsets we spend most of our time with, but in many ways it's more interesting than Another 5-inch 1080p Android Flagship. It looks and feels a lot like a Moto X. It performs a lot like a high-end phone from a couple of years ago. But it costs only $179 off-contract, where most similar phones go for at least $400 unlocked.
This handset obviously isn't meant to compete with $600-and-up flagships, but it's trying to redefine a part of the market that's now served by years-old phones and barely-usable garbage. Look at the phones that an MVNO like Straight Talk Wireless offers for less than $400, and you'll see just how under-served this market is. With the Moto G, Google and Motorola have attempted to put together a basic smartphone that doesn't throw quality under the bus in the name of cheapness.
In giving this phone the review treatment, we'll hit all of the same stuff we usually test—benchmarks, battery life, and so on. However, we'll also spend quite a bit of time answering the biggest questions about the Moto G: where does this phone feel like it costs $179, and who is it for?
Read 46 remaining paragraphs | Comments
Hate your friends’ Facebook posts? Now you can unfollow them
syndicatedragonSo, what's the point of being someone's "friend" if you "unfollow" them?
Facebook has bowed to the concept of the “follow” in a change that started rolling out to profile pages Monday. It is now possible to remain friends with a person but to “unfollow” their updates, such that they no longer appear in one’s timeline.
Functionally, the unfollow button does not appear to do anything differently from what used to be unchecking the setting “show in News Feed” on someone’s profile. Facebook also used to offer a “hide all posts from [friend]” link when a user hid a single post from that person within their News Feed. Now hiding and un-showing appear to be transforming into “unfollowing,” for friends as well as pages that users have liked.
Facebook told TechCrunch that it hopes this option will encourage users to “curate their News Feeds.” Curation has become a bit of a problem for Facebook of late. The company has tried to stem the flow by automating and regulating the popularity and level of interaction that posts must have to appear on a user’s home page, to the occasional rage of brands.
Read 1 remaining paragraphs | Comments
Get it sooner: $179 Moto G now ships December 2 in the US
syndicatedragonIt will be interesting to see some reviews of this
The Moto G, cheaper cousin to the Moto X, is now available for pre-order in the US. The phone was announced on November 13th, and it launched in Europe and Brazil the same day; the ship date for American users will be December 2.
The Moto G is Motorola's bid to raise the bar for low-end phones. The device sports a 1.2GHz quad core Snapdragon 400, a 4.5-inch 720p display, and 1GB of RAM. Those mid-range specs come at a low-end price: $179 for the 8GB version and $199 for the 16GB version—off contract. Typical phones in that price range are devices like the Samsung Galaxy Fame, which has a 3.5-inch 480p display and a single core 1GHz processor. While the Moto G currently runs Android 4.3, Motorola promises an upgrade to KitKat in the "beginning of 2014."
The Moto X's gimmick was its fully customizable exterior, and while the Moto G doesn't go quite that far, the back pops off and can be replaced with a colored version.
Read 2 remaining paragraphs | Comments
Cards deal Freese to Angels for Bourjos
syndicatedragonNo more dreamy Imo's commercials for you
NOAA's Winter Forecast: Drought and Warmth in the South
syndicatedragonI like the summary "flip a coin"
Picross Picross Picross. Play Some Picross. Picross

Today is the day when finally, FINALLY, Picross e3 comes out for the Nintendo 3DS in Europe. Why am I telling you this? Because oh my goodness, the PC is a perfect platform for picrossing, and yet seems so woefully starved of the joy. I’ll be downloading the new Jupiter Games puzzler to my 3DSXL tonight, and then likely not re-emerging until I’ve eaten them all up. But I’m now determined to find the things on PC too, so everyone can experience their pixel perfect magic. Here are the results of my searching:
The Battle for Power on the Internet
syndicatedragonMore long but interesting
We're in the middle of an epic battle for power in cyberspace. On one side are the traditional, organized, institutional powers such as governments and large multinational corporations. On the other are the distributed and nimble: grassroots movements, dissident groups, hackers, and criminals. Initially, the Internet empowered the second side. It gave them a place to coordinate and communicate efficiently, and made them seem unbeatable. But now, the more traditional institutional powers are winning, and winning big. How these two sides fare in the long term, and the fate of the rest of us who don't fall into either group, is an open question -- and one vitally important to the future of the Internet.
In the Internet's early days, there was a lot of talk about its "natural laws" -- how it would upend traditional power blocks, empower the masses, and spread freedom throughout the world. The international nature of the Internet circumvented national laws. Anonymity was easy. Censorship was impossible. Police were clueless about cybercrime. And bigger changes seemed inevitable. Digital cash would undermine national sovereignty. Citizen journalism would topple traditional media, corporate PR, and political parties. Easy digital copying would destroy the traditional movie and music industries. Web marketing would allow even the smallest companies to compete against corporate giants. It really would be a new world order.
This was a utopian vision, but some of it did come to pass. Internet marketing has transformed commerce. The entertainment industries have been transformed by things like MySpace and YouTube, and are now more open to outsiders. Mass media has changed dramatically, and some of the most influential people in the media have come from the blogging world. There are new ways to organize politically and run elections. Crowdfunding has made tens of thousands of projects possible to finance, and crowdsourcing made more types of projects possible. Facebook and Twitter really did help topple governments.
But that is just one side of the Internet's disruptive character. The Internet has emboldened traditional power as well.
On the corporate side, power is consolidating, a result of two current trends in computing. First, the rise of cloud computing means that we no longer have control of our data. Our e-mail, photos, calendars, address books, messages, and documents are on servers belonging to Google, Apple, Microsoft, Facebook, and so on. And second, we are increasingly accessing our data using devices that we have much less control over: iPhones, iPads, Android phones, Kindles, ChromeBooks, and so on. Unlike traditional operating systems, those devices are controlled much more tightly by the vendors, who limit what software can run, what they can do, how they're updated, and so on. Even Windows 8 and Apple's Mountain Lion operating system are heading in the direction of more vendor control.
I have previously characterized this model of computing as "feudal." Users pledge their allegiance to more powerful companies who, in turn, promise to protect them from both sysadmin duties and security threats. It's a metaphor that's rich in history and in fiction, and a model that's increasingly permeating computing today.
Medieval feudalism was a hierarchical political system, with obligations in both directions. Lords offered protection, and vassals offered service. The lord-peasant relationship was similar, with a much greater power differential. It was a response to a dangerous world.
Feudal security consolidates power in the hands of the few. Internet companies, like lords before them, act in their own self-interest. They use their relationship with us to increase their profits, sometimes at our expense. They act arbitrarily. They make mistakes. They're deliberately -- and incidentally -- changing social norms. Medieval feudalism gave the lords vast powers over the landless peasants; we're seeing the same thing on the Internet.
It's not all bad, of course. We, especially those of us who are not technical, like the convenience, redundancy, portability, automation, and shareability of vendor-managed devices. We like cloud backup. We like automatic updates. We like not having to deal with security ourselves. We like that Facebook just works -- from any device, anywhere.
Government power is also increasing on the Internet. There is more government surveillance than ever before. There is more government censorship than ever before. There is more government propaganda, and an increasing number of governments are controlling what their users can and cannot do on the Internet. Totalitarian governments are embracing a growing "cyber sovereignty" movement to further consolidate their power. And the cyberwar arms race is on, pumping an enormous amount of money into cyber-weapons and consolidated cyber-defenses, further increasing government power.
In many cases, the interests of corporate and government powers are aligning. Both corporations and governments benefit from ubiquitous surveillance, and the NSA is using Google, Facebook, Verizon, and others to get access to data it couldn't otherwise. The entertainment industry is looking to governments to enforce its antiquated business models. Commercial security equipment from companies like BlueCoat and Sophos is being used by oppressive governments to surveil and censor their citizens. The same facial recognition technology that Disney uses in its theme parks can also identify protesters in China and Occupy Wall Street activists in New York. Think of it as a public/private surveillance partnership.
What happened? How, in those early Internet years, did we get the future so wrong?
The truth is that technology magnifies power in general, but rates of adoption are different. The unorganized, the distributed, the marginal, the dissidents, the powerless, the criminal: they can make use of new technologies very quickly. And when those groups discovered the Internet, suddenly they had power. But later, when the already-powerful big institutions finally figured out how to harness the Internet, they had more power to magnify. That's the difference: the distributed were more nimble and were faster to make use of their new power, while the institutional were slower but were able to use their power more effectively.
So while the Syrian dissidents used Facebook to organize, the Syrian government used Facebook to identify dissidents to arrest.
All isn't lost for distributed power, though. For institutional power, the Internet is a change in degree, but for distributed power, it's a qualitative one. The Internet gives decentralized groups -- for the first time -- the ability to coordinate. This can have incredible ramifications, as we saw in the SOPA/PIPA debate, Gezi, Brazil, and the rising use of crowdfunding. It can invert power dynamics, even in the presence of surveillance, censorship, and use control. But aside from political coordination, the Internet allows for social coordination as well -- to unite, for example, ethnic diasporas, gender minorities, sufferers of rare diseases, and people with obscure interests.
This isn't static: Technological advances continue to provide advantage to the nimble. I discussed this trend in my book Liars and Outliers. If you think of security as an arms race between attackers and defenders, any technological advance gives one side or the other a temporary advantage. But most of the time, a new technology benefits the nimble first. They are not hindered by bureaucracy -- and sometimes not by laws or ethics, either. They can evolve faster.
We saw it with the Internet. As soon as the Internet started being used for commerce, a new breed of cybercriminal emerged, immediately able to take advantage of the new technology. It took police a decade to catch up. And we saw it on social media, as political dissidents made use of its organizational powers before totalitarian regimes did.
This delay is what I call a "security gap." It's greater when there's more technology, and in times of rapid technological change. Basically, if there are more innovations to exploit, there will be more damage resulting from society's inability to keep up with exploiters of all of them. And since our world is one in which there's more technology than ever before, and a faster rate of technological change than ever before, we should expect to see a greater security gap than ever before. In other words, there will be an increasing time period during which nimble distributed powers can make use of new technologies before slow institutional powers can make better use of those technologies.
This is the battle: quick vs. strong. To return to medieval metaphors, you can think of a nimble distributed power -- whether marginal, dissident, or criminal -- as Robin Hood; and ponderous institutional powers -- both government and corporate -- as the feudal lords.
So who wins? Which type of power dominates in the coming decades?
Right now, it looks like traditional power. Ubiquitous surveillance means that it's easier for the government to identify dissidents than it is for the dissidents to remain anonymous. Data monitoring means easier for the Great Firewall of China to block data than it is for people to circumvent it. The way we all use the Internet makes it much easier for the NSA to spy on everyone than it is for anyone to maintain privacy. And even though it is easy to circumvent digital copy protection, most users still can't do it.
The problem is that leveraging Internet power requires technical expertise. Those with sufficient ability will be able to stay ahead of institutional powers. Whether it's setting up your own e-mail server, effectively using encryption and anonymity tools, or breaking copy protection, there will always be technologies that can evade institutional powers. This is why cybercrime is still pervasive, even as police savvy increases; why technically capable whistleblowers can do so much damage; and why organizations like Anonymous are still a viable social and political force. Assuming technology continues to advance -- and there's no reason to believe it won't -- there will always be a security gap in which technically advanced Robin Hoods can operate.
Most people, though, are stuck in the middle. These are people who don't have the technical ability to evade large governments and corporations, avoid the criminal and hacker groups who prey on us, or join any resistance or dissident movements. These are the people who accept default configuration options, arbitrary terms of service, NSA-installed back doors, and the occasional complete loss of their data. These are the people who get increasingly isolated as government and corporate power align. In the feudal world, these are the hapless peasants. And it's even worse when the feudal lords -- or any powers -- fight each other. As anyone watching Game of Thrones knows, peasants get trampled when powers fight: when Facebook, Google, Apple, and Amazon fight it out in the market; when the US, EU, China, and Russia fight it out in geopolitics; or when it's the US vs. "the terrorists" or China vs. its dissidents.
The abuse will only get worse as technology continues to advance. In the battle between institutional power and distributed power, more technology means more damage. We've already seen this: Cybercriminals can rob more people more quickly than criminals who have to physically visit everyone they rob. Digital pirates can make more copies of more things much more quickly than their analog forebears. And we'll see it in the future: 3D printers mean that the computer restriction debate will soon involves guns, not movies. Big data will mean that more companies will be able to identify and track you more easily. It's the same problem as the "weapons of mass destruction" fear: terrorists with nuclear or biological weapons can do a lot more damage than terrorists with conventional explosives. And by the same token, terrorists with large-scale cyberweapons can potentially do more damage than terrorists with those same bombs.
It's a numbers game. Very broadly, because of the way humans behave as a species and as a society, every society is going to have a certain amount of crime. And there's a particular crime rate society is willing to tolerate. With historically inefficient criminals, we were willing to live with some percentage of criminals in our society. As technology makes each individual criminal more powerful, the percentage we can tolerate decreases. Again, remember the "weapons of mass destruction" debate: As the amount of damage each individual terrorist can do increases, we need to do increasingly more to prevent even a single terrorist from succeeding.
The more destabilizing the technologies, the greater the rhetoric of fear, and the stronger institutional powers will get. This means increasingly repressive security measures, even if the security gap means that such measures become increasingly ineffective. And it will squeeze the peasants in the middle even more.
Without the protection of his own feudal lord, the peasant was subject to abuse both by criminals and other feudal lords. But both corporations and the government -- and often the two in cahoots -- are using their power to their own advantage, trampling on our rights in the process. And without the technical savvy to become Robin Hoods ourselves, we have no recourse but to submit to whatever the ruling institutional power wants.
So what happens as technology increases? Is a police state the only effective way to control distributed power and keep our society safe? Or do the fringe elements inevitably destroy society as technology increases their power? Probably neither doomsday scenario will come to pass, but figuring out a stable middle ground is hard. These questions are complicated, and dependent on future technological advances that we cannot predict. But they are primarily political questions, and any solutions will be political.
In the short term, we need more transparency and oversight. The more we know of what institutional powers are doing, the more we can trust that they are not abusing their authority. We have long known this to be true in government, but we have increasingly ignored it in our fear of terrorism and other modern threats. This is also true for corporate power. Unfortunately, market dynamics will not necessarily force corporations to be transparent; we need laws to do that. The same is true for decentralized power; transparency is how we'll differentiate political dissidents from criminal organizations.
Oversight is also critically important, and is another long-understood mechanism for checking power. This can be a combination of things: courts that act as third-party advocates for the rule of law rather than rubber-stamp organizations, legislatures that understand the technologies and how they affect power balances, and vibrant public-sector press and watchdog groups that analyze and debate the actions of those wielding power.
Transparency and oversight give us the confidence to trust institutional powers to fight the bad side of distributed power, while still allowing the good side to flourish. For if we're going to entrust our security to institutional powers, we need to know they will act in our interests and not abuse that power. Otherwise, democracy fails.
In the longer term, we need to work to reduce power differences. The key to all of this is access to data. On the Internet, data is power. To the extent the powerless have access to it, they gain in power. To the extent that the already powerful have access to it, they further consolidate their power. As we look to reducing power imbalances, we have to look at data: data privacy for individuals, mandatory disclosure laws for corporations, and open government laws.
Medieval feudalism evolved into a more balanced relationship in which lords had responsibilities as well as rights. Today's Internet feudalism is both ad-hoc and one-sided. Those in power have a lot of rights, but increasingly few responsibilities or limits. We need to rebalance this relationship. In medieval Europe, the rise of the centralized state and the rule of law provided the stability that feudalism lacked. The Magna Carta first forced responsibilities on governments and put humans on the long road toward government by the people and for the people. In addition to re-reigning in government power, we need similar restrictions on corporate power: a new Magna Carta focused on the institutions that abuse power in the 21st century.
Today's Internet is a fortuitous accident: a combination of an initial lack of commercial interests, government benign neglect, military requirements for survivability and resilience, and computer engineers building open systems that worked simply and easily.
We're at the beginning of some critical debates about the future of the Internet: the proper role of law enforcement, the character of ubiquitous surveillance, the collection and retention of our entire life's history, how automatic algorithms should judge us, government control over the Internet, cyberwar rules of engagement, national sovereignty on the Internet, limitations on the power of corporations over our data, the ramifications of information consumerism, and so on.
Data is the pollution problem of the information age. All computer processes produce it. It stays around. How we deal with it -- how we reuse and recycle it, who has access to it, how we dispose of it, and what laws regulate it -- is central to how the information age functions. And I believe that just as we look back at the early decades of the industrial age and wonder how society could ignore pollution in their rush to build an industrial world, our grandchildren will look back at us during these early decades of the information age and judge us on how we dealt with the rebalancing of power resulting from all this new data.
This won't be an easy period for us as we try to work these issues out. Historically, no shift in power has ever been easy. Corporations have turned our personal data into an enormous revenue generator, and they're not going to back down. Neither will governments, who have harnessed that same data for their own purposes. But we have a duty to tackle this problem.
I can't tell you what the result will be. These are all complicated issues, and require meaningful debate, international cooperation, and innovative solutions. We need to decide on the proper balance between institutional and decentralized power, and how to build tools that amplify what is good in each while suppressing the bad.
This essay previously appeared in the Atlantic.
EDITED TO ADD (11/5): This essay has been translated into Danish.
Unlocked Moto G handset offers quad-core Snapdragon for $179
syndicatedragonNot as "high end" as the Nexus 5 but impressive specs for the price.
Well hello, Moto. Google-owned Motorola Mobility has introduced a budget handset that looks quite impressive considering the price. The Moto G starts at just $179 for the 8GB version, and bumping up to 16GB raises the price by only $20. Those are all-in prices, by the way; the Moto G will be sold sans contract. It has an unlocked SIM slot and and unlocked bootloader, too.
 ...
...
Google shows off new version of Google Glass, complete with earbud
syndicatedragonShared for glass-wearing DB
Google had previously announced that a hardware revision of Glass was in production and that Google Glass Explorers would be eligible to trade in their existing headsets for the updated version. Now the company is showing off just what the new version of Google Glass will look like.
There really doesn't seem to be much that's new. The pictured design looks identical to the current version of Glass, except for a mono earbud that plugs into the middle of the device. With Googlers frequently offering quotes like “This is the bulkiest version of Glass we’ll ever make” and with Glass being available for over six months, many expected a more drastic design change than what is pictured.
Google says the earbud will be removable, and Glass will keep its current bone conduction speaker. Other than that, there doesn't seem to be much difference. Glass Explorers should be a eligible to trade up to the new version sometime in November.
Read 2 remaining paragraphs | Comments
Zelda 3DS XL launching in the US too
syndicatedragonI don't want an XL but I thought this was a pretty neat design
Nintendo is set to release a limited edition The Legend of Zelda: A Link Between Worlds 3DS XL in the US on November 22.


Click here to read the full article
Most Powerful Storm in 14 Years Sweeps Northwestern Europe
syndicatedragonShared for the crazy surfer
An extra-tropical cyclone, variously named St. Jude (The Weather Channel and the U.K. Met Office), Christian (Free Univ. of Berlin), Carmen (European Windstorm Centre, UK), and Simone (Swedish Meteorological and Hydrological Institute), swept across northwestern Europe October 27-29 with the strongest winds ever recorded for some locations and resulting in at least 16 fatalities as well as causing...<br /><a href="http://www.wunderground.com/blog/weatherhistorian/comment.html?entrynum=209">Read More</a>
NFL players benched due to head injuries have altered brain connections

So far, the long-term effects of repeated head injuries in professional football have been hard to pin down. There are a whole host of economic and social reasons for this, but the simple truth is that the scientific research itself just isn’t clear-cut. While some studies have found decreased cognitive function and an increased risk of Alzheimer’s disease in NFL players, others haven’t found strong evidence linking careers in professional football to long-lasting cognitive decline.
The problem, researchers argue, may be “ecological validity.” In other words, the skills and competencies that scientists test may not accurately represent those required in real life. The psychological tests used in laboratory settings are highly controlled and standardized, while real-world situations are much messier. Players with brain injuries might retain enough cognitive control mechanisms to pass lab-based tests yet fail miserably at the complex scenarios they face in everyday life.
A new study in Scientific Reports clears up some of this confusion, using a combination of cognitive tests and neuroimaging to get a better picture of what happens to football players’ brains as a result of repetitive traumatic brain injuries (TBIs).
Read 12 remaining paragraphs | Comments
A (relatively easy to understand) primer on elliptic curve cryptography
syndicatedragonReally great article
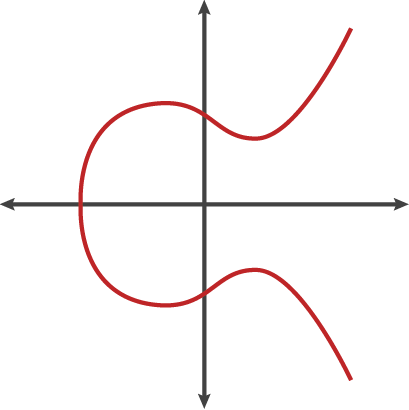
Author Nick Sullivan worked for six years at Apple on many of its most important cryptography efforts before recently joining CloudFlare, where he is a systems engineer. He has a degree in mathematics from the University of Waterloo and a Masters in computer science with a concentration in cryptography from the University of Calgary. This post was originally written for the CloudFlare blog and has been lightly edited to appear on Ars. Readers are reminded that elliptic curve cryptography is a set of algorithms for encrypting and decrypting data and exchanging cryptographic keys. Dual_EC_DRBG, the cryptographic standard suspected of containing a backdoor engineered by the National Security Agency, is a function that uses elliptic curve mathematics to generate a series of random-looking numbers from a seed. This primer comes two months after internationally recognized cryptographers called on peers around the world to adopt ECC to avert a possible "cryptopocalypse."
Elliptic curve cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use today. An increasing number of websites make extensive use of ECC to secure everything from customers' HTTPS connections to how they pass data between data centers. Fundamentally, it's important for end users to understand the technology behind any security system in order to trust it. To that end, we looked around to find a good, relatively easy-to-understand primer on ECC in order to share with our users. Finding none, we decided to write one ourselves. That is what follows.
Be warned: this is a complicated subject, and it's not possible to boil it down to a pithy blog post. In other words, settle in for a bit of an epic because there's a lot to cover. If you just want the gist, here's the TL;DR version: ECC is the next generation of public key cryptography, and based on currently understood mathematics, it provides a significantly more secure foundation than first-generation public key cryptography systems like RSA. If you're worried about ensuring the highest level of security while maintaining performance, ECC makes sense to adopt. If you're interested in the details, read on.
Read 88 remaining paragraphs | Comments
The custom pinball machines of Chicago’s Pinball Expo 2013
No matter if you're a fan, game maker, or game distributor, every pinhead marks the annual Chicago Pinball Expo on their calendar. The annual event is filled with seminars, tours, parts, game sales, and booths showing off the latest toys.
This year's expo, the 29th annual, wrapped up over the weekend. Ars was there to check out the main attraction on the show floor, a section devoted to custom games built using the P-ROC controller board. Some of these games are one-offs that will live on only as cool projects, while others are readying for commercial production. The following gallery has a selection of the custom games plus some other fun elements found on the show floor.
Read on Ars Technica | Comments
Square drastically simplifies Internet cash transfers
syndicatedragonI guess it might go without saying, but NEVER use this for ANYTHING. Square is just a terrible, terrible company, and I have serious doubts about the security of this. Check out the comments, they seem to agree with me.

Financial startup Square launched a new arm of its business Tuesday that allows two parties to transfer cash between themselves using only their debit card numbers and e-mail. Square Cash may trump similar services like PayPal in ease of use in that it doesn’t require extra bank info, and transactions can happen directly via e-mail.
Competitors like PayPal have been able to handle direct debit transactions for some time, though setup is a bit more of a hassle. Users have to enter their checking account numbers and routing numbers and then verify their accounts with two small deposits, so the process can take a few days.
With Square Cash, the process begins in e-mail: users send an e-mail to the person they want to pay, cc cash@square.com, and enter the amount in the subject line. If it’s their first transaction, Square sends a second e-mail that leads the user to a screen where they enter their debit card number, expiration date, and ZIP code. Once the person on the other end gets the e-mail and fills out the same form, the transaction is completed in 1-2 days.
Read 2 remaining paragraphs | Comments
Government spending charts for the USA
I found this fairly dry looking site that goes over all kinds of interesting financial stats:
http://www.usgovernmentspending.com
It’s non-partisan (it’s non political, it’s a glorified spread sheet).
But it’s interesting to look at snap shots of what the federal government spents its money on.
Starting in 1800..
Pretty boring still…
..
and next…
The 16th amendment passes allowing for direct income taxes…
Holly shit! World War I + new amendment brings a ton of new money.
War is over but the spending is still much higher than it was.
1929, the year the great depression starts.
So 4 years later, we’ve doubled our spending, no doubt to stimulate the economy. The depression must have ended in 1934 then right? Because, look at that massive stimulus.
No. Holy cow, we spend even more. And nowa new item, for the first time ever, has been added: Welfare.
Growing and growing. Note that we are now almost 3X the spending we were when the stock market crashed in 1929. That’s an incredible federal stimulus program. This is 1935 so this is pre-World War II.
World War II comes to the United States. Welfare disappears but we nearly double the budget again.
Holy shit. So 20 years since 1929 and the federal budget is nearly 10X bigger than it was. That’s incredible.
Marty McFly travels back to 1955 and the federal budget has massively increased still in just 6 years ($278 to $443!!!). Pensions (social security) are now part of life.
So now we have pensions (social security) AND welfare. This is the year I was born.
What the fuck is health? We went 200 years with only defense and “remainder” and now we have pensions, welfare and health?
The year I graduated high school
That social security and medicare thing sure sure took over. How did the federal government get into this?
Bush leaves office.
Christ, spending went from 2.7 to 3.2 on one year? Right, the Stimulus.
Spending goes down.
Acer’s $249 C720 Chromebook launched: Thinner, longer lasting, and Haswell
syndicatedragon8hr battery life - amazing.

Chrome OS afficionados have long pined for a Haswell processor to drive one of their Chromebooks, imbuing the line with the longevity they've been missing out on. That wait has come to an end. Launched this morning, and previewed at IDF, the Acer C720 Chromebook promises 8.5 hours of battery life in a new, thinner body and with an all-new, Haswell-based Intel Celeron 2955U processor inside. The 1.4GHz dual-core CPU will boost performance over the 1.1GHz Sandy Bridge-based Celeron that preceded it, while cutting power consumption. The 11.6-inch clamshell has a matte display with a screen resolution of 1366×768, a step down from the pricier Chromebook Pixel, and unlike the just-announced HP Chromebook 11, Acer makes no mention of an IPS panel.
The refreshed chassis is 0.75 inches thick and weighs in at 2.76 pounds, slightly thicker and heavier than the 0.69-inch 2.3 pound Chromebook 11. Paired with a 16GB SSD, 4GB of RAM, and dual-band 802.11n, it'll be available for pre-order at Amazon and Best Buy today for $249. Not on offer is a touchscreen model, though Acer noted in its release that this is just the first configuration that will be available.
This update gives us the broadest collection of platforms for Google's desktop OS to be offered in, with everything from Atom to ARM to Haswell having now been sampled. Performance hasn't been as much of an issue since the Sandy Bridge-based solutions of last year, so it's battery life that'll stand to see the biggest gains. And with so many new models shuffling out, expect full reviews of them all soon.
Read on Ars Technica | Comments
iKettle, A Wi-Fi Kettle That Lets You Boil Water From Your Phone And Pings You When It's Ready, Is Available For Pre-Order
 You know you probably have it well when your biggest inconvenience is having to wait for the kettle to boil each morning. But hey, pain is relative, and I'm not going to pretend like it's not annoying. But thanks to that Android phone on your bedside table, you won't be stuck with this burden for long. No, there isn't an app that will solve this problem for you, there's a kettle - a Wi-Fi kettle that you can control from your Android device.
You know you probably have it well when your biggest inconvenience is having to wait for the kettle to boil each morning. But hey, pain is relative, and I'm not going to pretend like it's not annoying. But thanks to that Android phone on your bedside table, you won't be stuck with this burden for long. No, there isn't an app that will solve this problem for you, there's a kettle - a Wi-Fi kettle that you can control from your Android device.

- The Sony Xperia Z Can Survive Being Boiled Alive In A Pot Of Soup (But You Probably Shouldn't Drop A Hammer On It)
- [Poll] Some Samsung Galaxy Tab 10.1s Experiencing 'Newton's Rings' - Is Yours?
- Disney Releases Where's My Perry? A Puzzle Game Based On The World's Most Popular Platypus Detective
- Tower Raiders 2 GOLD Released, Let’s Blow Something Up!
iKettle, A Wi-Fi Kettle That Lets You Boil Water From Your Phone And Pings You When It's Ready, Is Available For Pre-Order was written by the awesome team at Android Police.