World of Warcraft Classic, the official "vanilla" server from Blizzard, is currently in development.
World of Warcraft Classic, the official "vanilla" server from Blizzard, is currently in development.
Corey G
Shared posts
Blizzard Announces World of Warcraft Classic, Official Vanilla Server
 World of Warcraft Classic, the official "vanilla" server from Blizzard, is currently in development.
World of Warcraft Classic, the official "vanilla" server from Blizzard, is currently in development.
Google serves 'Android Burger' for lunch in company cafeteria, stays true to its emoji and keeps the cheese below the patty
Last week, a tweet from a Danish media analyst contrasting Google and Apple's hamburger emoji designs set the internet ablaze. Google's take on the emoji, which places the cheese below the patty, drew the ire of many. Less than 12 hours later, Google CEO Sundar Pichai responded, reassuring everyone that the company would address the matter immediately. While the world waits to see whether Google changes (some would say, corrects) the architecture of its Android hamburger emoji, there is one update to share: Googlers were served "Android Burgers" on Friday – and, yes, the cheese was kept below the beef patty.
Read MoreGoogle serves 'Android Burger' for lunch in company cafeteria, stays true to its emoji and keeps the cheese below the patty was written by the awesome team at Android Police.
Facebook: upload your nudes to stop revenge porn
Keen Lab Takes Down iPhone 6S, Nexus 6P at Mobile Pwn2Own
Corey GUgh these guys are insane.
Samsung’s mobile division profits fall by 96% in wake of Note 7 disaster

Samsung's mobile division took a shellacking this past quarter thanks to the Note 7's double-recall, but the Korean company believes the problem is behind it, with no long-term impacts on its mobile divisions market share or popularity.
The post Samsung’s mobile division profits fall by 96% in wake of Note 7 disaster appeared first on ExtremeTech.
Critical vulnerability Pork Explosion revealed by jcase, cripples security on some phones
Security has been a hot topic on Android for many years, particularly as smartphones take on increasingly significant roles both at home and at work. A single device acts as your main form of communication, contains personal photos and confidential documents, and may even have access to your finances. Google and other companies have made significant investments in time and money to ensure these devices are very hard to break into.
Read MoreCritical vulnerability Pork Explosion revealed by jcase, cripples security on some phones was written by the awesome team at Android Police.
Samsung estimates it'll lose around $3.1 billion in the next two quarters because of the Galaxy Note7
Corey G$$
The Galaxy Note7 has been an absolute disaster for Samsung; although it was an excellent smartphone, its tendency to catch fire pretty much negates all of the praise that was heaped onto it. Case in point: Samsung's now estimating that the Note7's recalls and subsequent cancellation will cost them about $3.1 billion over the next two fiscal quarters.
This news comes shortly after Samsung reduced its profit forecast for Q3 of this year by $2.3 billion; back then, a full discontinuation of the Note7 hadn't been announced, although there already were rumors about it.
Read MoreSamsung estimates it'll lose around $3.1 billion in the next two quarters because of the Galaxy Note7 was written by the awesome team at Android Police.
Android 7.1 feature spotlight: Google Camera actually takes a photo on voice command
Corey GImagine if multiple people have their phones unlocked and listening in a room and someone says this.. weird
Trying to set a timer on cameras, both on smartphones and dedicated units, can be a pain. Google Camera 4.2, which currently can only be installed on Android 7.1 or higher, allows you to take photos with the "OK google, take a picture" voice command.
Once you say the magic words, the Camera app will open (if it isn't already) and start a 3-second timer. After the time is up, the photo will be taken.
Read MoreAndroid 7.1 feature spotlight: Google Camera actually takes a photo on voice command was written by the awesome team at Android Police.
Snoops can tell what you type while you Skype, researchers find
Corey Gweird
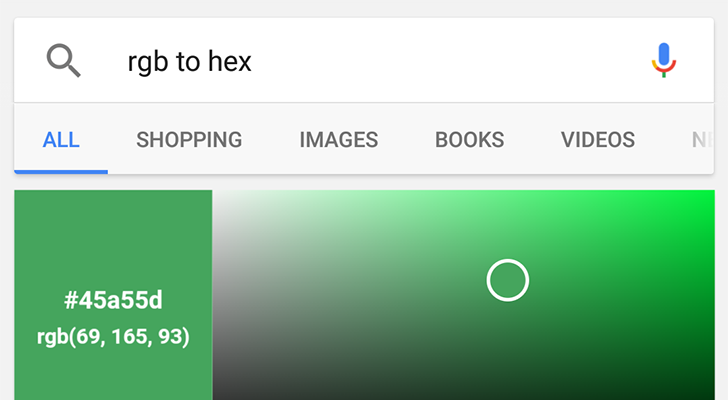
Google Search now has a RGB/Hex color converter
Google has been working to bring more and more functionality directly into search results, without the user having to visit a seperate site. You can now find your IP address, run a speed test, convert units, and more all from Search. Following that trend, now Google has added an RGB to Hex converter.
If you're unfamiliar, RGB and Hex are both color spaces used to identify colors. For example, #000000 in Hex and (0,0,0) in RGB both refer to Black.
Read MoreGoogle Search now has a RGB/Hex color converter was written by the awesome team at Android Police.
How Dolphin finally cracked the code on Star Wars: Clone Wars, now emulates every GameCube title

After extensive work, the GameCube and Wii emulator Dolphin can now emulate every single licensed title -- including one outlier that eluded the team for over a decade.
White House Hires First Federal CISO
HTC's broken 15-day update promise for the One A9 is a small symptom of a larger malady
Corey G:'(
Last year, HTC promised that the One A9 would receive Android OS updates within 15 [business] days of the first Nexus device to get that update. HTC almost immediately failed to meet its self set goal with security patches, and last I checked, my One A9 was rocking a June 1st security update in early August (it does now have the August security patch, though). Now HTC is seemingly implying the One A9 may not get Nougat until 2017, or: at least not until well after the end of August it would have under its 15-day no-longer-a-rule.
Read MoreHTC's broken 15-day update promise for the One A9 is a small symptom of a larger malady was written by the awesome team at Android Police.
CrossOver for Android runs Windows programs on x86 Android tablets and Chromebooks
Corey GThe idea of Windows running inside of CX/Wine inside of Android Runtime for Chrome inside of ChromeOS inside of a CPU that could just run Windows anyway blows my mind.

If you have ever used Linux, Mac, or another *nix operating system, you've probably heard of Wine. No, not the beverage - it's software that allows Windows programs to run on platforms that aren't Windows. Wine is one of my favorite open-source projects, under development since 1993 and having a massive community of developers and testers. Wine also maintains a database of compatible programs, which should give you an idea of the impressive compatibility.
Read MoreCrossOver for Android runs Windows programs on x86 Android tablets and Chromebooks was written by the awesome team at Android Police.
USB-IF announces new USB charger certification program
For the last year, Googler Benson Leung has been waging a one-man war on bad USB accessories. Going forward, he'll have some help in the form of the USB Implementers Forum itself. The USB-IF has announced a certification program complete with a handy little logo. If you see that logo, you'll know the accessory in question is in compliance with the spec and won't break your gear.
The USB-IF is a support organization that promotes the adoption of new USB standards.
Read MoreUSB-IF announces new USB charger certification program was written by the awesome team at Android Police.
Space Station View of the Chesapeake Bay
Google Play Family Library: Share what you love with the ones you love
Friday night is movie night at our home, and my wife and I look forward to our weekly ritual of putting the kids to bed, getting some takeout, and catching up on our movie wishlist. Whether it’s making the BLUE STEEL face from Zoolander, swapping tips on playing Monument Valley, or reading Dragons Love Tacos to the kids at bedtime, these shared moments bring us closer together.
For families like mine, who bond over shared entertainment, we’re introducing Family Library, a way for up to six family members to share purchases on Google Play. When you buy an eligible app, game, movie, TV show, or book in the Play Store, you can now share it with your family—across devices—with no additional sign-up fee.
Share across your family’s devices
Today’s families have a lot of devices, and it should be easy to share content no matter where we are or what we’re doing. Everyone in my family loves the Star Wars movies and we all want to be able to watch them, on our phones, tablets, laptops, or TV. All purchases added to Family Library are available across Android devices, and movies, TV shows, and books can be enjoyed on iOS devices and the web.
Easily manage sharing and family purchases
As with most family matters, flexibility and choice is important. With Family Library, you can choose which items you want to share and which to keep to yourself—for example, I’ll probably keep my collection of comic books in my personal library. Flexibility is also built into your purchasing options. When you sign up, you’ll select a credit card to share as your family payment method, but your family members will always have the option of buying stuff with their personal credit cards or gift cards. And for your younger family members, you’ll have the option to approve each of their purchases.
Share a Music subscription with your family
Finally, if your family loves music, you can also subscribe to the Google Play Music family plan. On this plan, up to six family members can stream millions of songs on demand for $14.99 a month. We launched the family plan late last year, and today we’re expanding it to Ireland, Italy, Mexico, and New Zealand. And you can now sign up on the web, in addition to your Android device.
Starting today, Family Library will be rolling out over the next few days and will be available in Australia, Brazil, Canada, France, Germany, Ireland, Italy, Japan, Mexico, New Zealand, the United Kingdom and the United States. To get started, sign up in Google Play, invite your family members, and start sharing what you love!
Posted by Raj Iyengar, Product Manager, Google Play
US Army Special Forces to dump Galaxy Note II for iPhone 6S because iPhones are "faster"
In what I am tempted to say may be the stupidest news I've read all morning (give me an hour, though, I just grabbed my coffee), the US Army's Special Operations Command is allegedly dumping its current Nett Warrior embedded tactical smartphone solution - a 4-year-old Galaxy Note II - for an iPhone 6S. Because, and I quote DoDBuzz's source here, the iPhone is "faster; smoother. Android freezes up." Wait, you're telling me a smartphone that's four years old trying to run a specialized government app isn't very fast or stable?
Read MoreUS Army Special Forces to dump Galaxy Note II for iPhone 6S because iPhones are "faster" was written by the awesome team at Android Police.
NIST Recommends Deprecation Of SMS Two-Factor Authentication
 The NIST recommended that SMS out of band authentication, a form of two-factor authentication done through a separate device from the one on which you login, should be deprecated in favor of more secure alternatives.
The NIST recommended that SMS out of band authentication, a form of two-factor authentication done through a separate device from the one on which you login, should be deprecated in favor of more secure alternatives.
BlackBerry announces $299 DTEK50 Android phone, but it's just a rebranded Alcatel Idol 4
Corey GIf Blackberry is rolling the ROMs too then this could be great. The Priv has been getting monthly patches quicker than Nexus.
BlackBerry is sticking with this Android thing despite sales for its first phone not being particularly stellar. Now, there's a second BlackBerry Android phone, the DTEK50. Unlike the PRIV, this one is mid-range and costs just $299. Also unlike the PRIV, it doesn't look like BlackBerry designed or built this one. The DTEK50 is a rebranded Alcatel Idol 4.
Externally, the DTEK50 is identical to the Idol 4, save for a custom back panel with BlackBerry branding.
Read MoreBlackBerry announces $299 DTEK50 Android phone, but it's just a rebranded Alcatel Idol 4 was written by the awesome team at Android Police.
Samsung's Galaxy S7 edge Olympic Games Edition is now available in the US, exclusively at Best Buy
Samsung, no stranger to special edition phones, has one just in time for this summer's Olympics in Rio. The S7 edge Olympic Games Edition is now on sale in the USA, where it is exclusively available at Best Buy. The unlocked phone will run you $849.99, an extra $100 above the non-Olympic equivalent.
For a closer look, Samsung has released an official unboxing video:
The Olympic Games Edition has an Olympics logo on the rear side of the phone along with a yellow telephone speaker grille and trim on the home button, red power button, green volume keys, and blue trim around the camera lens, each representing Olympic colors.
Read MoreSamsung's Galaxy S7 edge Olympic Games Edition is now available in the US, exclusively at Best Buy was written by the awesome team at Android Police.
Changes to Trusted Certificate Authorities in Android Nougat
[Cross-posted from the Android Developers Blog]
In Android Nougat, we’ve changed how Android handles trusted certificate authorities (CAs) to provide safer defaults for secure app traffic. Most apps and users should not be affected by these changes or need to take any action. The changes include:
- Safe and easy APIs to trust custom CAs.
- Apps that target API Level 24 and above no longer trust user or admin-added CAs for secure connections, by default.
- All devices running Android Nougat offer the same standardized set of system CAs—no device-specific customizations.
Safe and easy APIs
Apps have always been able customize which certificate authorities they trust. However, we saw apps making mistakes due to the complexities of the Java TLS APIs. To address this we improved the APIs for customizing trust.User-added CAs
Protection of all application data is a key goal of the Android application sandbox. Android Nougat changes how applications interact with user- and admin-supplied CAs. By default, apps that target API level 24 will—by design—not honor such CAs unless the app explicitly opts in. This safe-by-default setting reduces application attack surface and encourages consistent handling of network and file-based application data.Customizing trusted CAs
Customizing the CAs your app trusts on Android Nougat is easy using the Network Security Config. Trust can be specified across the whole app or only for connections to certain domains, as needed. Below are some examples for trusting a custom or user-added CA, in addition to the system CAs. For more examples and details, see the full documentation.Trusting custom CAs for debugging
To allow your app to trust custom CAs only for local debugging, include something like this in your Network Security Config. The CAs will only be trusted while your app is marked as debuggable.<network-security-config>
<debug-overrides>
<trust-anchors>
<!-- Trust user added CAs while debuggable only -->
<certificates src="user" />
</trust-anchors>
</domain-config>
</network-security-config>
Trusting custom CAs for a domain
To allow your app to trust custom CAs for a specific domain, include something like this in your Network Security Config.<network-security-config>
<domain-config>
<domain includeSubdomains="true">internal.example.com</domain>
<trust-anchors>
<!-- Only trust the CAs included with the app
for connections to internal.example.com -->
<certificates src="@raw/cas" />
</trust-anchors>
</domain-config>
</network-security-config>
Trusting user-added CAs for some domains
To allow your app to trust user-added CAs for multiple domains, include something like this in your Network Security Config.<network-security-config>
<domain-config>
<domain includeSubdomains="true">userCaDomain.com</domain>
<domain includeSubdomains="true">otherUserCaDomain.com</domain>
<trust-anchors>
<!-- Trust preinstalled CAs -->
<certificates src="system" />
<!-- Additionally trust user added CAs -->
<certificates src="user" />
</trust-anchors>
</domain-config>
</network-security-config>
Trusting user-added CAs for all domains except some
To allow your app to trust user-added CAs for all domains, except for those specified, include something like this in your Network Security Config.<network-security-config>
<base-config>
<trust-anchors>
<!-- Trust preinstalled CAs -->
<certificates src="system" />
<!-- Additionally trust user added CAs -->
<certificates src="user" />
</trust-anchors>
</base-config>
<domain-config>
<domain includeSubdomains="true">sensitive.example.com</domain>
<trust-anchors>
<!-- Only allow sensitive content to be exchanged
with the real server and not any user or
admin configured MiTMs -->
<certificates src="system" />
<trust-anchors>
</domain-config>
</network-security-config>
Trusting user-added CAs for all secure connections
To allow your app to trust user-added CAs for all secure connections, add this in your Network Security Config.<network-security-config>
<base-config>
<trust-anchors>
<!-- Trust preinstalled CAs -->
<certificates src="system" />
<!-- Additionally trust user added CAs -->
<certificates src="user" />
</trust-anchors>
</base-config>
</network-security-config>
Standardized set of system-trusted CAs
To provide a more consistent and more secure experience across the Android ecosystem, beginning with Android Nougat, compatible devices trust only the standardized system CAs maintained in AOSP.Previously, the set of preinstalled CAs bundled with the system could vary from device to device. This could lead to compatibility issues when some devices did not include CAs that apps needed for connections as well as potential security issues if CAs that did not meet our security requirements were included on some devices.
What if I have a CA I believe should be included on Android?
First, be sure that your CA needs to be included in the system. The preinstalled CAs are only for CAs that meet our security requirements because they affect the secure connections of most apps on the device. If you need to add a CA for connecting to hosts that use that CA, you should instead customize your apps and services that connect to those hosts. For more information, see the Customizing trusted CAs section above.If you operate a CA that you believe should be included in Android, first complete the Mozilla CA Inclusion Process and then file a feature requestagainst Android to have the CA added to the standardized set of system CAs.
Exclusive: this is what the 2016 Nexus phones, Sailfish and Marlin, will look like
Corey G*continues hopelessly wishing for a ≥ 64GB and ≤ 5.2" nexus*
The moment you've all been waiting for, right? As you can see in the above image, Google's Nexus phones are taking on a decidedly cleaner design language for 2016, according to information we've received from a reliable source. The image you're seeing is not an actual press render, but our own recreation of the upcoming Nexus phones based on evidence from our source. So, let's do the rumor breakdown.
Confidence level
We give this rumor a confidence level of 8 out of 10.
Read MoreExclusive: this is what the 2016 Nexus phones, Sailfish and Marlin, will look like was written by the awesome team at Android Police.
Hey Google, a warez market called BlackMart has been in the Play Store for months and has over 100k downloads [Updated]
Corey GWow..
We occasionally see apps pulled from the Play Store for trivial (but valid) violations of the rules. Google has been more proactive about enforcing its guidelines, but it's often pointed out it could be more consistent. Case in point: there are, right now, two listings on the Play Store from a warez site called BlackMart that offers paid apps for free. One of them has been up for months and has more than 100,000 downloads.
Read MoreHey Google, a warez market called BlackMart has been in the Play Store for months and has over 100k downloads [Updated] was written by the awesome team at Android Police.
GPRS Sniffing using OpenBTS
Having the ability to sniff cellular traffic can be very helpful when analyzing certain mobile and IoT devices. One of the tools that we use to do this is a Range Networks OpenBTS 5150 unit. OpenBTS is open source software that simulates a GSM network-in-a-box using a Software Defined Radio (SDR) to transmit/receive GSM protocols, and route them appropriately to other phones and the internet. Inside the 5150, OpenBTS converts voice calls from your mobile phone into SIP messages and uses Asterisk to route calls to real phones using a VoIP provider or route locally to other phones connected to the OpenBTS. It also has software to send, queue, and receive SMS messages and to let you connect to the internet over GPRS. This allows you to create your own (small) GSM network enabling voice, SMS, and GPRS services.
RangeNetworks now calls the 5150 their "OpenCell" product. The 5150 is a small PC ITX board running Ubuntu connected to a custom SDR. The PC runs the open source OpenBTS software and allows us to create a small 2G GSM network supporting GPRS in the 1900 frequency band (which is what the SDR came tuned to). This turned out to be perfect for testing in our lab to find a way to intercept the GPRS connection and to create a .pcap of collected traffic.
Note: If you are not familiar with GSM or telecommunications, you should know that every service provider (AT&T, T-Mobile, Verizon, etc) internationally has assigned Mobile Country Codes (MCCs) and Mobile Network Codes (MNCs). MCCs are a standard code defined by the International Telecommunications Union to allocate numeric codes to every country with cellular networks in order to distinguish between them, along with the help of the MNC. The MNC is used to identify network providers within a country (within a MCC). A MCC with 001 is used as a test network code, so for our setup, we used that. We were also keeping the RF power attenuated so we did not disrupt our neighbors.
Warning: Following these steps, you may disrupt cellular service to phones in the area. I take no responsibility for anything that happens to you or your neighbors if you try these steps. You do so at your own risk.
Here are the basic steps I went through:
- Get OpenBTS running and connected to the Internet
- Have a smartphone attached & registered on the voice and GPRS sides of OpenBTS
- Sniff all the phone's packets and get a .pcap
- Win.
Here's how we set it up to sniff GPRS traffic.
Equipment:
- OpenBTS 5150 unit (aka OpenCell)
- VGA Monitor
- USB Keyboard
- Wired internet connection
- SIM Cards
- SIM reader/writer
- GSM compatible tri/quad-band phone
Step 1 - Get OpenBTS running and on the Internet
If you have never worked with OpenBTS, I recommend starting with their free O'Reilly book to get comfortable installing, configuring, and running the system. The book is well written and should help you get it up and running using a standard SDR, like an Ettus Research B210, foe example. We opted for a hardware solution using the 5150.

Image 1 - OpenBTS 5150 opened up in our lab and connected to a VGA monitor and USB keyboard (not pictured). Note the PC on the left & the custom SDR on the right.
The 5150 should automatically start the OpenBTS software. Once the system boots up, you can configure networking for Ubuntu by modifying /etc/services/networking to use static or dynamic IPs. We have DHCP in our lab so we left this alone. Note the last "pre-up" line was added, and is referenced, in the OpenBTS book:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet dhcp
pre-up iptables-restore < /etc/OpenBTS/iptables.rules
Once you've got it on the network, you can SSH to it for remote administration and the OpenBTS CLI. On to step 2!
Step 2 - Get a smartphone attached & registered on OpenBTS for voice and GPRS
Now the fun begins. I used the OpenBTSCLI (also documented well in the OpenBTS book) for configuring the GSM parameters so that we could connect actual phones. The RangeNetworks 5150 version of OpenBTS included a small web server and web application you could use to modify each of the parameters directly from a browser (which manipulates the underlying sqlite configuration database in /etc/OpenBTS/). This provides the easiest interface for configuring the system and adding subscribers, however you can achieve all this manually using the OpenBTSCLI (located at /OpenBTS/OpenBTSCLI). Here is a screenshot of the web GUI:

Image 2 - Screenshot of the "Wizard" browser based configuration showing the basic parameters.
The most important parameters here are GSM.Identity.MCC and GSM.Identity.MNC. I ensured these were set to our test network, 001 and 04, respectively. Our 5150 only supports one GSM frequency (Band 1900), so everything else can stay at default.
If you click "Full" at the top of the GUI, you can modify a LOT more of the parameters, including those specific to the GGSN. The GGSN is a node in the GSM core network, simulated by software in OpenBTS. The GGSN is essentially the router running DHCP & NAT inside the core network, and sits between the cell network and the Internet. It is what allocates an IP address to your phone when you are connected to your provider.
Each of the configuration parameters can be directly configured in the OpenBTSCLI using the 'config' command and a value, like so:
> config <param> <value>
# example
> config GSM.Identity.MNC 04
# Running config GSM.Identity.MNC simply prints the current value
The "Full" configuration window looks like this once you click "GGSN":

Image 3 - Screenshot of the "Full" wizard, under the "GGSN" tab. Highlighted in yellow are the critical parameters that must be set.
I highlighted in orange two parameters you should verify and change if incorrect: GPRS.Enable which must be "1", and GGSN.DNS which must be set to the IP for the router/DNS server for your network.
The last thing you need to verify is the GSM.LUR.OpenRegistration parameter. This parameter is crucial to configuring who and who is not allowed to attach and register to the network. This parameter's value must be a string that represents a regular expression for the IMSI number series allowed to attach. Below, I only want the IMSIs which start with 00104 (MCCMNC) to be able to connect to our system and no one else.
If you set this to ".*", the system will attach and register ANY IMSI in a phone with the correct frequency range. This would be "A Bad Thing"®, but great for testing and debugging purposes if you are having issues.

Image 4 - Control.LUR.OpenRegistration regex as seen in the web GUI. This can also be configured via command line as shown above using OpenBTSCLI.
The next step is to program a SIM using your SIM reader/writer to use the 001 04 network, cut it (if necessary for your phone), and pop it into your phone and power it on.
We used an Android Nexus 5 for testing. Once we put the SIM in, we had one last thing to do before sweet internet access at 2.5G speeds: we had to set the Access Point Name (APN) in "Settings ➝ Mobile Networks ➝ Access Point Names". An APN is what configures the connection to the gateway between the carrier's cellular network (or in our case, our test network) and the public Internet. The OpenBTS software requires an APN, but it can be anything, it just has to exist and must be enabled. I created a new APN since none existed on my phone, set the name to "test" and APN to "test", saved it, and enabled it. Also make sure "Data enabled" and "Data roaming" are enabled. See this Google page for reference. Here is how to verify & set your APN for iPhones.
To test if your phone attaches & registers on the network, try connecting to the network first (if your phone did not already automatically—it may if the other settings are automatically correct). Go to "Settings ➝ Under Wireless & Networks touch More ➝ Cellular/Mobile networks ➝ Network Operators" and select your OpenBTS's network. Ours is called "Range", but on some phones it simply appears as "001 04". If you select your new network and the phone says "Registered", congratulations! You have attached and registered your phone successfully.
You can easily test voice calls by dialing "2600", which is an echo test number setup in Asterisk by the OpenBTS software by default. If the call connects, you should be able to hear an echo of your voice. Success!
Lastly, let's try the Internet. This gave us some trouble and was a little flakey, but we were able to see it work. Make sure you are attached and registered, and on Android we looked for the "G" in the corner next to the signal strength bars. The G for GPRS shows the phone has registered a data connection and you can start browsing! Really really slowly. Try it! We noticed our OpenBTS did not maintain the GPRS connection for a long time (over 1-2 hours) consistently, but did work reliably if continued to be used. Rebooting the phone and rebooting the OpenBTS sometimes did the trick, but I found cold booting the OpenBTS was the most reliable method to get the GPRS connection to work properly.
3. Sniff all the phone's packets and get a .pcap
Now we can have some fun. Login to the OpenBTS over ssh and have your connected phone handy. As root on your OpenBTS host, you simply have to use tcpdump to sniff GPRS traffic and create a pcap of phone's traffic. Note: If you have multiple phones attached and registered on GPRS with your OpenBTS, this procedure will collect ALL of their traffic as it sniffs the OpenBTS tunneling GPRS network interface. Fortunately, you can filter by IP address in Wireshark later.
Here, you must specify the special sgsntun interface.
tcpdump -i sgsntun -s 1514 -w /path/to/file.pcap
This will run tcpdump until stopped, with a snaplen of 1514 bytes for standard packets, and write all the data collected to a .pcap specified with -w. Hit Ctrl-C to finish and save the .pcap. You can use scp/sftp to copy the file off to your local machine for analysis using Wireshark or your favorite pcap tool. That's it! You have successfully sniffed GPRS traffic from a smartphone over a GSM network.
4. Win.
That's all you have to do, which is quite a lot. This may seem a tedious process, and that's because it is, but it is a good method to obtain cellular traffic for testing and research. Be cautious to not turn your power too high, so as to not affect those around you, and remember to use test IMSIs and test MCC and MNC.
Amazon is now selling unlocked phones at a discount in exchange for giving you bloatware and ads
Corey GThis is kind of interesting. I wonder the builds are going to lag behind the general moto G4 like a carrier variant would?
I can't say I saw this coming: Amazon is getting into the unlocked smartphone business in a big way starting today. By selling you phones for a lower price... in exchange for bloatware and lockscreen ads. Yep, seriously.
Amazon announced today that the BLU R1 HD and the Moto G4 (not the Plus, though) are the first Amazon Prime Exclusive smartphones in the US. Both phones are $50 off their standard retail prices, making the BLU R1 HD just $49.99 and Moto G4 just $149.99 (the 32GB is $179.99).
Read MoreAmazon is now selling unlocked phones at a discount in exchange for giving you bloatware and ads was written by the awesome team at Android Police.
Dell says it's done making Android tablets, won't push new updates to existing ones
Corey GGood riddance, their software was so hacky
After dabbling in Android tablets for years, Dell is finally throwing in the towel on Google's mobile OS. The company won't be making any more Android tablets, and it's ending update support for the Venue tablets that already exist. That's a bummer for anyone holding out hope that the Venue 8 would make it to Android 6.0.
Dell says this decision was made because the tablet market is over-saturated and demand is declining.
Read MoreDell says it's done making Android tablets, won't push new updates to existing ones was written by the awesome team at Android Police.
Autorooting Malware 'LevelDropper' Silently Installs Apps On Android Devices
 Lookout's security researchers uncovered a new autorooting malware called "LevelDropper" on the Play Store that can silently install apps on users' devices. The company already notified Google, which promptly banned the malware from the store.
Lookout's security researchers uncovered a new autorooting malware called "LevelDropper" on the Play Store that can silently install apps on users' devices. The company already notified Google, which promptly banned the malware from the store.
Samsung announces unlocked Galaxy S7 and Galaxy S7 Edge devices for the US
Corey GFinally, 4 months late...
Some OEMs thrive on selling unlocked phones, but Samsung has always been very chummy with carriers as a way to move its phones in the US. That has traditionally meant unlocked versions of the Galaxy phones on sale in the US were actually imported international models. Today, Samsung is announcing an unlocked version of the Galaxy S7 and Galaxy S7 Edge for the US, and it'll work on virtually all carriers.
Samsung was a little light on actual specs in the PR, but we do know the US unlocked GS7 will support both GSM and CDMA-based networks.
Read MoreSamsung announces unlocked Galaxy S7 and Galaxy S7 Edge devices for the US was written by the awesome team at Android Police.
Chrome Developer channel 53 rolling out to ASUS Chromebook Flip now, Play Store in tow
Corey GThe beginning of good things
Have a Chromebook Flip? Get it on the developer channel ASAP - the Play Store update is rolling out now. I've had very little chance to mess with it, but the apps I have used (Hangouts, Maps, Search, the Play Store) all seem to run pretty well. Funnily, the Play Store still allowed to install Google Now Launcher... but you can't change the launcher, since the launcher is the windowed app mode.
Read MoreChrome Developer channel 53 rolling out to ASUS Chromebook Flip now, Play Store in tow was written by the awesome team at Android Police.