
IMDB Rating: 5.8/10
Genre: Horror
Size: 1.85 GB
Runtime: 1hr 40 min
Horror invades the concrete corridors of a cursed apartment complex on the outskirts of Madrid.

The rising popularity of ChatGPT, an AI-powered language tool, has turned NVIDIA GPUs into literal gold for the booming AI business.
ChatGPT and other language/image/video generation tools rely heavily on AI processing power and that's where NVIDIA's main strength lies. The company may be known for its blistering-fast gaming GPUs but AI is another strong suit and one in which the company has seen more success in recent years. NVIDIA definitely has a major edge in AI over the competition which includes Intel and AMD.
There's no doubt that NVIDIA currently has the fastest AI GPUs on the planet with its Hopper H100 and Ampere A100 architecture. Both chips have been banned from the Russian & Chinese markets due to potential use in military assistance but the company still offers revised variants in the China market.

Not only these tools are where AI is a big deal but there's also a huge demand for faster AI power in the data center, cloud, and automotive segment where NVIDIA also dominates with its GPUs. The company has seen a massive growth of over 40% in just a single month & the current stock stands at an impressive 45%+ growth (this month).
With the rise of OpenAI's language tool, ChatGPT, Wall Street traders are increasingly betting on chip-makers like Nvidia, which has climbed more than 34% this month.
As a result, CEO Jensen Huang, who cofounded the company in 1993, has seen his wealth balloon by more than a third to $18.9 billion.
According to Bloomberg's Billionaire Index, the $5.1 billion gain gives Huang the largest percentage gain to his net-worth among US billionaires so far this year.
The 59-year-old Taiwanese immigrant is coming off a less memorable year, as he was among other tech moguls who lost big money, including Meta's Mark Zuckerberg and Tesla's Elon Musk.
This means that NVIDIA is putting its AI prowess to good use and turning gold into profits with Bloomberg reporting that CEO, Jensen Huang, added $5.1 Billion US to his wealth, the single most and "largest percentage gain" among other US billionaires, this year. Jensen Huang currently stands in the 80th spot on the US Billionaires list.
But that's not the end of NVIDIA's gain as Citi analysts have suggested that ChatGPT will continue to grow and that could further result in more NVIDIA GPU sales throughout 2023. Sales are estimated between $3 to $11 Billion. Other analysts from Bank of America and Wells Fargo have also said that NVIDIA is to gain from the popularity surrounding the AI / ChatGPT biz. Overall, this bodes well for NVIDIA in the coming quarters as they will have room to grow and post some positive earnings in a PC market that is currently in a recovering phase.
The post ChatGPT Has Turned NVIDIA’s AI GPUs Into Literal Gold, Company Stock Soars Over 40% This Month by Hassan Mujtaba appeared first on Wccftech.

In August 2022, amidst a bevy of other cost-cutting but callous decisions, Warner Brothers Discovery began removing shows and movies from HBO Max that couldn't be found anywhere else. It wasn't subtle; dozens of titles disappeared across the course of the month, including "Vinyl," which was created by Martin Scorsese, "Mrs. Fletcher," starring Kathryn Hahn, and an inordinate amount of animated and kids' shows. The streamer didn't stop there, though. By December, one of its former flagship shows, "Westworld," was gone, along with a total of 80 other movies and series according to IndieWire.
Even as creators began speaking openly about the broken trust between artists and a powerhouse network that was once known for letting creativity thrive, other streamers were already following in HBO Max's footsteps. In September, news broke that the Eli Roth-produced series "Hemlock Grove," which stars Bill Skarsgård as a rich kid vampire, would be leaving the streamer despite being one of its earliest Originals. And in January, Starz and Showtime both got on board with this troubling trend, with shows including the Michel Gondry-directed Jim Carrey vehicle "Kidding" and the new "Dangerous Liaisons" also disappearing.
While it eventually became clear that some of these shows would reappear via licensing to smaller free streamers called FAST platforms — "Hemlock Grove" reportedly struck a deal with FilmRise, HBO Max's "Generation" landed on Tubi, and WBD has plans for its own FAST streamer — most of them haven't resurfaced, and it seems unlikely that they all will. Equally troubling, the industry-wide programming purge for the sake of tax write-offs and cost-cutting has also meant there are now whole seasons of TV being scrapped before they ever air. Showtime's "Three Women," starring Shailene Woodley, DeWanda Wise, and Betty Gilpin is the latest victim of this trend.

Over the past year, the rug has been pulled out from under consumers and streaming creators, leaving artists, in particular, flat on their faces. As screenwriter C. Robert Cargill put it on Twitter when the news of the unceremonious cancelation of "Batgirl" broke, "Streamers have been selling us creatives on the virtues of platform exclusivity for some time now." He added, "The reason Hollywood is so shook by the HBO Max stories is that no one is sure whether this is an isolated incident or a canary in the coal mine."
It's clear now that it was, in fact, the canary. Since HBO Max kick-started the trend of canceling near-finished projects and (at least temporarily) erasing others from existence with a snap of their fingers, Thanos-style, many a commentator has called these practices "unprecedented." But unfortunately, the history of television is full of lost art, from its earliest days to the 21st century. So, considerable concerns about industry monopolies aside, why does this particular period of disappearing TV feel so harrowing?

To understand the current period of television, it's important to go back to the medium's earliest days. Experimental television began in the 1920s, but TV wasn't available for consumers until years later. Until "I Love Lucy" pioneered the idea of reruns in the 1950s, programs would broadcast once and then never again. Much early television, from variety shows to musical performances to scripted TV, was never recorded for posterity in the first place. When it finally was, in the early days of videotape, the expensive format was used by networks to record TV shows for a short time before wiping the tapes to use over again. "Television meant being live, over, and done with," BBC historian Richard Molesworth says in a report by Mental Floss. The BBC alone lost as much as 70% of its programming from the mid-'50s to the mid-'70s, mostly due to intentional deletion, according to the outlet.
Many of us know the disappearance of original programming feels wrong, for one simple reason: we lived through a time when we were able to save the shows we loved with just a videotape. With the advent of home video in the '80s and '90s, TV viewers became amateur archivists capable of saving any TV show that we felt was worthy of a blank tape and some storage space. Some TV shows started to gain official releases on home video, and others didn't, but viewers had the chance to legally and easily curate whatever they wanted. One woman in Philadelphia, for example, recorded 71,000 VHS and Betamax tapes over the course of 30 years. Home video recordings were bulky, grainy, and not built to last forever, but they leveled the playing field, allowing TV to feel more permanent than it ever had before.

The dawn of streaming, which began in earnest when Netflix started cranking out original series in 2013, made home media largely obsolete for most Americans. Collectors and streaming skeptics still smartly extolled the virtues of buying your favorite show or movie on DVD or Blu-ray, sure, but that also quickly became an unrealistic expectation. After all, Netflix and other streamers almost immediately started making shows and films that they never released on physical media at all, a trend that continues to this day.
The unspoken expectation in this discreetly made deal with the devil was that if subscribers paid a monthly fee for a hub for all of our Netflix, HBO Max, or similarly branded favorites, we'd be able to pick them up and dust them off at any time like we would if they were on our own shelves. Home video recording died down, but DVD burning, which required more tech-savvy as well as a willingness to ignore stricter piracy laws, never caught on to the extent of its predecessor.
Netflix co-founder and former CEO Reed Hastings was pretty frank about his hope that subscribers would prioritize streaming way back in 2012, as a TechCrunch piece from the time quotes him as saying that "Profitability of each new streaming subscriber is almost twice what it is for DVDs." He continued, saying, "We'd obviously like them to do both, but if they're only going to use one, we'd much prefer they use streaming."
For a decade now, streaming has been the future, so all our shows went to streaming. But what's the future now, and where will TV go?

The failure to preserve art isn't okay just because it's happened before. There's something disorienting and alienating about the fact that viewers who once had the ability to act as at-home archivists now go to sleep one day unaware that their favorite show could disappear entirely the next. While the Criterion Collection increasingly incorporates streaming originals into their catalog, and now-vital conversations about piracy as preservation abound, companies continue to, as their memos so often put it, stop investing in titles that "underperform," which, somehow, often includes titles that haven't been released yet.
While HBO Max insists it's done with the slaughter, other streamers and networks have already picked up where they've left off, and creator trust has already been shattered. When news broke that the romantic anthology show "Love Life" would be leaving HBO Max, series creator Sam Boyd tweeted, "Bummed that this is now a thing that can happen! Gonna try to figure out somewhere else for it to live, so it doesn't just **not exist anymore**" Other showrunners and filmmakers echoed this sentiment, with "Dickinson" creator Alena Smith even revealing in a now-deleted tweet that she once had to beg for a single physical copy of her own series (which, luckily, is still available on Apple TV+).

In an article titled "Understanding the Preservation Challenge of Digital Television," authors quote a 1997 statement from the Library of Congress declaring that, "at present, chance determines what television programs survive. Future scholars will have to [rely] on incomplete evidence when they assess the achievements and failures of our culture." Over 25 years and multiple industry shake-ups later, it's a statement that seems truer than ever.
If there is an easy path forward for the legal, accessible preservation of television as an art form, it's clear that it doesn't lie in the hands of the viewers anymore. After a few decades that let us play home archivist, and another that taught us to dream of a digital TV world at our fingertips, that's a reality that's especially hard to accept -- precedented or not. We shouldn't have to, either; technology is constantly evolving, and our ability to preserve visual media should be improving in the 21st century, not degrading.
Unfortunately, there's never been any promise that business ethics will evolve alongside technology. The second any art starts to be discussed as a tax write-off, no art is safe anymore. Watch your favorite shows today, because who knows where they'll be tomorrow?
Read this next: The Moments That Defined TV In 2022
The post In the Age of Streaming, TV Preservation Matters More Than Ever appeared first on /Film.

The Anne Rice universe at AMC continues to expand. Today we found out that the network has officially greenlit the second season of "Mayfair Witches," the show based on the books by author Anne Rice. The television series centers around Rowan (Alexandra Daddario), a surgeon who becomes drawn to New Orleans after her adoptive mother dies, who finds out that she's part of a long line of witches who are intertwined with a mysterious, supernatural being named Lasher (John Huston).
"Mayfair Witches" is the second AMC Network show based on Anne Rice's work. The first series adaptation was "Interview With The Vampire," which had its first episode drop just a couple of months before "Mayfair." While "Mayfair Witches" wasn't as critically well-received as "Interview With The Vampire," the execs at AMC are apparently happy enough with it to give it at least one more season. "Interview With The Vampire" also has a second season in the works, which AMC announced before the first episode even aired.

The first season of "Mayfair Witches" followed the events in Anne Rice's thousand-page tome, "The Witching Hour." The second season will adapt the second book, "Lasher," a much shorter book of 400 pages that will unsurprisingly feature the sexy and enigmatic Lasher in a new light.
Here's what showrunner Esta Spalding told me about season 2 when I interviewed her and executive producer Michelle Ashford in early January during the Television Critics Association winter press event:
"Rowan is the lead of the second season. It's still Rowan's story. She's driving it, but Lasher is very present and has a very distinctive point of view in a way that he does not in the first season. In the first season, he's usually enigmatic and in other people's scenes, in a way. I mean, not to say he doesn't own the scenes, he does, but he doesn't drive storylines in the same way. In the second season, he really does. He's much more like a traditional character. I guess maybe the better way to say it is he's much more of an antagonist in the first season and he's really one of the protagonists in the second season."
We don't have news yet on when the second season of the show will cast its spell upon us. The first season of "Anne Rice's Mayfair Witches," however, is now streaming on AMC+.
Read this next: The 15 Best Horror Movie Directors Of All Time
The post AMC's Mayfair Witches Conjures Up a Second Season appeared first on /Film.
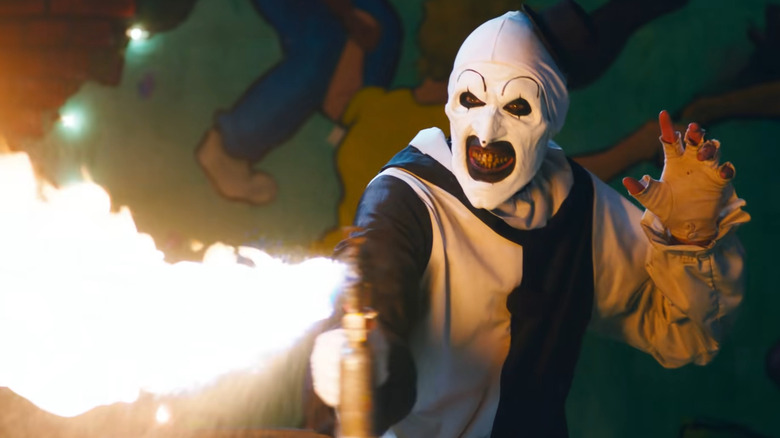
One of last year's most unexpected hits was that of "Terrifier 2," an epic-length splatter film that garnered bold headlines for its impressively sickening gore effects. On top of that, its $250,000 budget went on to gross a pretty insane $14.7 million at the box office. When an ode to exploitation cinema rakes in that kind of money, it wasn't a matter of "if" a "Terrifier 3" was happening, and more of a "when." Director Damien Leone is already hard at work writing the threequel, with the possibility of expanding it into a fourth film. "There may be two to tell this story and tackle all the ideas that I have in my head," says Leone (via Insider).
Given the dangling plot threads of "Terrifier 2" that were left open-ended, there's plenty of room to play around with where this demented story could go. Leone has assured that the sequel will pick up with the sequel's newcomers, as Lauren LaVera's Sienna has become just as important to this series as her interdimensional tormenter. "There's a lot more to explore with Art the Clown, the pale girl, Victoria, and certainly Sienna as our final girl. We will be following her journey to the end of this franchise," says Leone.
One of the most notable criticisms of the first film was that there wasn't someone to follow throughout the bloody journey besides Art the Clown (David Howard Thornton). Thankfully, "Terrifier 2" rectifies this with an awesome performance from LaVera, who gives the kind of Scream Queen performance that turns actors into horror mainstays. But while Leone seems committed to getting the third "Terrifier" out sooner than later, he might be a bit busy working with a horror legend.

When you make the kind of numbers that "Terrifier 2" did, it grabs the attention of bigger names. For Leone, one of those names was Sam Raimi. According to a report from Insider, Leone says he's met with the "Evil Dead" scribe to develop a secretive new project:
"There is an original project I have in development with Ghost House Pictures, which is Sam Raimi's production company [...] So if that happens, that would be amazing. I'm really hoping that that could happen before 'Terrifier 3,' or it might happen right after, we'll see."
Ghost House has been responsible for releasing Raimi's "Drag Me to Hell," in addition to "30 Days of Night" and "The Grudge." One of Hollywood's lasting trends is plucking independent filmmakers and giving them a big-budget production as a sort of way to usher them into the big leagues. Last year, Paramount took a gamble on Parker Finn, who had only directed a few shorts, to helm the urban legend chiller "Smile." In addition to being a pretty great horror movie, it grossed over $216 million against a $17 million budget.
For someone who also built their way through the indie horror scene, it's really heartening to see Raimi reaching out to a new generation of horror filmmakers. We may not have any idea of what Leone is developing, but given his admiration for practical effects, I wouldn't count out another bloody spectacle.
"Terrifier 2" is currently streaming on Screambox.
Read this next: The 31 Scariest Movie Scenes Ever
The post Damien Leone is Writing Terrifier 3, and then Hopes to Work With Sam Raimi appeared first on /Film.

Michael Ironside has been the face of some of cinema's great villains and antiheroes. Whether playing a ruthless armed henchman in Paul Verhoeven's "Total Recall," an evil telepath in David Cronenberg's "Scanners," or the one-armed leader and namesake of Rasczak's Roughnecks in Verhoeven's sci-fi satire "Starship Troopers," the actor's husky baritone and intense presence commands every frame he's in.
Call him a method actor, though, and he will gently correct you. "Method I am," he told Screen Anarchy in a 2016 interview, "and not the misunderstood idea of method." The Canadian multi-hyphenate defined his practice of the method –- that is, finding the framework of identification with the character –- as more in-depth, beyond simply finding an emotion and replicating it:
"I know how to find an emotion, find the behavior with that emotion and recreate the behavior. A lot of people never went that far with the method. They only know how to find the emotion. And if you don't get it, you have to wait and get it because they can't recreate."
For Ironside, the recreation process is known by a simple name, dubbed by his oldest daughter: Binkie. According to the "Top Gun" star, Binkie is "a raincoat I throw over the characters" that allows him to find the emotional center while avoiding the sort of extreme behavior that's given the method a rotten name these days. This, he explained, diverges from the "misunderstood" perception of method, "because if I walk around in character, it's not going to be very useful."

Many of cinema's most beloved actors practice some systematic approach to finding their character. In New York City, theater director and acting coach Lee Strasberg trained the likes of Anne Bancroft, Jane Fonda, Dustin Hoffman, Ellen Burstyn, and Paul Newman at his Actor's Studio. There they would learn, as laid out by filmmaker Elia Kazan in his autobiography, "to launch their work on every scene by taking a minute to remember the details surrounding the emotional experience in their lives that would correspond to the emotion of the scene they were about to play."
Sometimes, as Newman would come to find out after eating 50 boiled eggs on the set of "Cool Hand Luke," method acting can only take you so far. Other times, as "American Gigolo" star Jon Bernthal has observed, "making everybody call you by your character name and not showering for eight months was not what [Russian theater practitioner Konstantin] Stanislavski had in mind with the Method." Michael Ironside leans more toward the latter sentiment:
"Never make your character the responsibility of somebody else to have to deal with. Your job is to go in there and be a professional, find some way, whatever horrific thing you're working on, not to let it spill over. It shouldn't be the cameraman's responsibility to have to deal with you or the directors or something like that. That's hysteria, that's not f***ing acting, that's not craft. So I throw this raincoat over the misogynistic character or over the bloodthirsty, and they're all derivatives of me. You take the checks and balances out."
If that's how we get the iconic bug-killer Jean Rasczak on the big screen, then perhaps more actors should embrace the Binkie.
Read this next: The 10 Best Sci-Fi Movie Villains
The post Michael Ironside Is The Furthest Thing From A Fan Of Method Acting appeared first on /Film.

The Taylor Sheridan series "1923" was just renewed by Paramount+ for a second season, bringing us the further adventures of the Dutton family. We began following their journey in "Yellowstone," which is set in the present day, then got the prequel series "1883." In "1923" we meet Jacob Dutton (Harrison Ford), the brother of James Dutton (Tim McGraw) from "1883" who has since passed. Jacob and his wife Cara (Helen Mirren) are running the Yellowstone ranch in his place. They are battling it out with sheepherders who have enlisted mining tycoon Donald Whitfield (Timothy Dalton) to try to take the land from the Duttons.
The series shoots in Montana, which is not the easiest environment to work in. Sheridan famously puts his actors through cowboy camp training, and there is a lot of physical work from riding to fight scenes. Not only that, but the weather is pretty brutal. It's something Dalton ("License to Kill," "Penny Dreadful") says he had a rough time dealing with in an interview with The New York Times. It's also something that co-star Harrison Ford apparently handled better than he did.

According to the story, the shooting conditions included blizzards and incredibly cold 10-hour shoot days, which were all outside. Dalton says, "It was a nightmare. We are on top of a hill with a blasting wind coming at us. The cameras freeze up. Your toes freeze up." Though I'm sure it's all good-natured, one person who apparently doesn't complain about any of the conditions is Harrison Ford.
Director and cinematographer Ben Richardson ("1883," "Mayor of Kingstown," "Tulsa King"), who directed most of the "1923" episodes, tells the publication that Ford was a great sport. He explains:
"I've never had a complaint from him. I can't express how much of a team player he is — to the point that it's shocking. He's Harrison Ford. He could be doing anything. I'm sure there are people who would prefer to have a double standing in. He did not."
That's a lovely thing to hear, and Richardson isn't the first person to say it. Before the series premiere, I spoke to Brian Geraghty, who plays the Dutton's ranch foreman Zane. Geraghty says that Ford was great at riding in cowboy camp, and they all had to work hard to keep up with him. He echoed Richardson's thoughts about Ford being a team player. He says:
"It's not that Harrison's down, and we're freezing — we're all in a van together, trying to get warm. He's very inclusive. He's very funny. And Helen's just a dream to work with, really, and to watch act. So you just try to hang in there with them. That's my best hope."
There are two episodes left in season 1 of "1923," which airs on Paramount+.
Read this next: The 18 Best Crime Dramas In TV History
The post Harrison Ford Handled Yellowstone's 'Nightmare' Weather A Bit Better Than Timothy Dalton appeared first on /Film.

M. Night Shyamalan is a busy man right now. Not only did he just release his new apocalyptic horror film "Knock the Cabin," but he also completed the fourth and final season of the television show "Servant," currently airing on Apply TV+. Unlike a movie, which is guaranteed to have a complete story whether it booms or busts at the box office, a TV series presents the unique problem of leaving the large narrative unfinished between seasons. The format's penchant for being potentially open-ended means that there's a chance the story will never end if the show gets canceled, but Shyamalan was willing to take the risk for the sake of broadening his creative horizons.
"Servant" is a mystery box show, a supernatural thriller that constantly presents questions and encourages audience theories as it moves along. Although Shyamalan serves as showrunner, it's British TV writer Tony Basgallop who created and largely penned the series. The narrative follows a couple (Lauren Ambrose and Toby Kebbell) from Shyamlan's signature favorite setting of Philadelphia who "adopt" a doll to cope with the tragic death of their infant son. They hire a mysterious nanny (Nell Tiger Free) to look after Jericho the doll and supernatural intensity ensues. Originally planned as a 60-episode run, according to Shyamalan, the series will wrap up its 40 episodes in the coming weeks, with the finale planned to air on March 17, 2023.

Filmmakers who migrate or dabble in television aren't a rarity at all anymore. The medium has provided room for interwoven, complex stories that even the longest movies don't have time for. On the other hand, the web of narrative threads inevitably gets more tangled as a show progresses, so it helps to meticulously plan out the structure over the length of several seasons. That's why Shyamalan wanted to have the entire plot of "Servant" planned out from start to finish, even with the knowledge that Apple may not renew the series.
In an interview with The Verge, he said:
"You can't tell this suspenseful story with no ending. It is a gamble that my partners, Apple, and — more importantly — the audience would be interested and supportive, which is what has happened with 'Servant.' It was a risk. I love taking risks when the only mitigating factor is our execution. That's been my approach to the industry for the last eight years. [...] Unless I put myself in jeopardy, I am not going to be the storyteller that I want to be."
Instead of writing each season as if it was going to be the last, Shyamalan made sure that an entire four-season-long story was set in stone. It was essential that contingency endings wouldn't muddle the already complicated narrative flow of the series, even if that meant a potential cancellation would make for an extremely dissatisfying and wholly incomplete run. This calculated gamble paid off in the end as "Servant" nears a conclusion at least five years in the making, a payoff that the show's creators had planned from the start.
Read this next: The Best TV Episodes Of 2022, Ranked
The post M. Night Shyamalan Knew Servant Was A Risk That He Had To Take appeared first on /Film.

Valentine's Day means different things to different people. For some, it's a joyous celebration of the people in their lives. For others, it's a painful reminder of loves lost and broken hearts. Then, for the rest of us, it's a springboard for silly slashers about lovesick killers. Second only to Christmas, Valentine's Day might well be the most popular holiday in slasher flicks. The innate tension between treacly intimacy and gonzo gore is too good an opportunity to pass up, and for time immemorial, creatives have merged both love and fear in increasingly twisted ways.
Some recent editions to the horror canon, like "Bones and All" and "Spring," while not strictly speaking Valentine's Day-themed, are deeply romantic, reminding audiences of how perfectly the two disparate emotions can coalesce into something amazing. Here, we'll be looking at horror movies specifically about the most romantic day of the year. From old school slashers to creepy, slow burn zombie frighteners, there's something here to ignite a spark in everyone's heart.

There's something to be said for schlocky, SyFy Channel-esque CG creature features. "Ice Spiders" has, well, spiders in ice. "Crooked Man" arrived long before James Wan's still-gestating "The Conjuring" spinoff. And, of course, "Cupid" takes a holiday staple and corrupts a longstanding myth to ridiculous effect. After an animated introduction reveals how Cupid came to be a homicidal maniac, the audience is plunged into a high school drama that's about to become deadly.
Following a humiliating prank, Faye (Georgina Jan) vows to take revenge on her peers. Luckily, Faye just so happens to be a practicing witch — because why not? — and summons Cupid to target the girls who wronged her. While the effects are a combination of both practical and digital — par for the course with low-budget horror films — "Cupid" looks better than most of its ilk. Some of the deaths are grislily effective. "Cupid" is mostly in on the joke, too. While the pacing lags at times, there's always another death right around the bend. "Cupid" might not be a masterpiece, but in giving the titular god his due it merits a watch.

"Into the Dark," Hulu's series of feature-length horror films, might well be the televised adaptation of the underrated 2016 anthology "Holidays." It's covered Thanksgiving, it's covered Christmas, and it's rendered Valentine's Day anew not once, but twice. In "Down," the fifth episode of the show's first season, Guy (Matt Lauria) and Jennifer (Natalie Martinez) play the last two workers inside a high-rise office building on the night before Valentine's Day. As they take the elevator to the lobby before a long weekend, it abruptly stops, trapping them inside. They hit it off. Soon, their friendship gives way to intimacy. Then, the terror arrives.
With heaps of deception, claustrophobia, and a smattering of "P2"-esque corporate terror, "Down" is an exceptionally self-contained story, an early augur of just how fantastic "Into the Dark" could be when firing on all cylinders. It's tense, terrifying, and strangely nostalgic. Like the other films on this list, it takes a famous holiday and mixes it with an ingenious concept to create something both familiar and new.
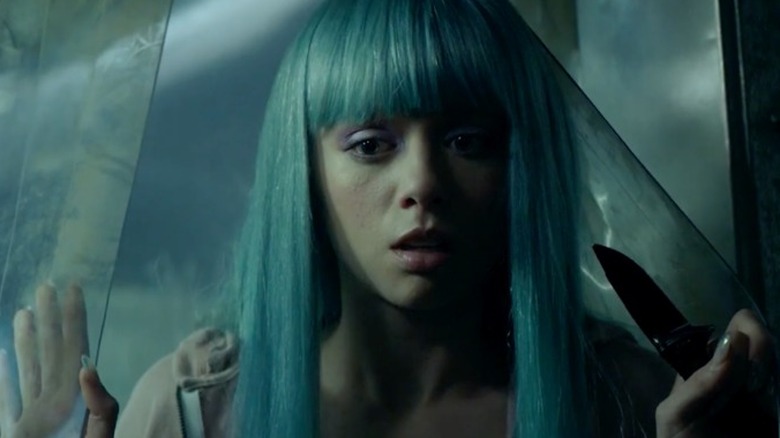
As good as "Down" is, season 2's "My Valentine" is just a smidge better. While both installments of "Into the Dark" address toxic masculinity and the innate terror some men strike into the hearts of women, "My Valentine" does so with a smidge more pizazz, and a smattering of more stylistic embellishments. Britt Baron stars here as Valentine, a pop star embroiled in a controversy involving stolen songs, rival star Trezzure (Anna Lore), and shady music manager Royal (Benedict Samuel), who's likely responsible for the whole ordeal.
Inevitably, "My Valentine" arrives at violence. While its tone is unwieldy at times, the film has one of the better depictions of toxic masculinity in recent memory. By literalizing the idea that, to some men, women are exchangeable, blank visages onto which they can project their own desires, "My Valentine" has a sinister, all-too-relevant urgency. That it manages to balance its message with the expected thrills is a feat unto itself.

Barbi Benton was many things. A former Playboy model, a recording artist, and a co-star on the long-running series "Hee Haw," Benton finally made the shift into horror genre the 1982's "X-Ray," otherwise known as "Hospital Massacre." Benton stars as Susan, a divorcee who's now dating Jack (Jon Van Ness). After she purchases a new health insurance plan, Susan arrives at the local hospital for a routine physical exam, but her visit proves to be anything but ordinary.
See, years prior, Susan's friend was murdered by Harold (Billy Jayne), a lovesick young boy pushed over the edge by Susan's Valentine's Day rejection. Is there a chance that Harold, with a new identity, is stalking the hospital halls, doing anything he can to get close to Susan? There sure is. While I won't spoil Harold's feigned identity, "X-Ray" manages to target the best of the post-"Halloween" slashers. It's silly, ridiculously violent, and features contrivance upon contrivance. Thanks to clerical errors and other obstacles, Susan simply cannot leave the hospital, ambling about while doctors, custodians, and others are killed and stashed away until the final confrontation. While slashers like "X-Ray" only appeal to a particular style of horror fan, those who appreciate a good, bloody yarn will find a ton to love here.

Freddie Francis' "Tales from the Crypt" is one of the greatest horror anthologies ever made. Like 1945's "Dead of Night" and 1971's "The House That Dripped Blood," it's one of the premier compendiums of horror, one that paved the way for every subsequent anthology. Its first entry, "...And All Through the House," features the inimitable Joan Collins murdering her husband while simultaneously evading a homicidal Santa Claus. "Blind Alleys" is a sensationally claustrophobic tale of medical malpractice and revenge. Then, of course, there's "Poetic Justice," a "Tales from the Crypt" spin on a Valentine's Day yarn.
Adapted from the 12th issue of the comic "The Haunt of Fear," "Poetic Justice" follows David Markham's and Robin Phillips' father and son, Edward and James, and their ongoing feud with their elderly neighbor, Arthur Edward Grimsdyke (Peter Cushing). Grimsdyke, a former waste collector, keeps several dogs and regularly entertains the neighborhood's children. James takes umbrage with Grimsdyke and embarks on a series of callous acts against him, including insinuating that Grimsdyke is a predator, having his dogs taken away, and sending him a series of abusive letters on Valentine's Day. Grimsdyke dies, but like "Cupid" hero Faye, he dabbles in the occult. So, a year later, he rises from the dead on Valentine's Day. It's all gorgeously gothic, and it's never anything but a delight to see Cushing in action. A cautionary tale of petty revenge gone awry," Poetic Justice" is the best of what "Tales from the Crypt" has to offer.

3D gimmick aside, longtime Wes Craven editor Patrick Lussier's "My Bloody Valentine" is a pitch-perfect example of how to do a horror remake correctly. Rather than kowtowing to shifting audience demands, 2009's "My Bloody Valentine" is a love letter — sometimes quite literally — to the gonzo gore and ludicrous plotting of the best '80s slashers. With heaps of gratuitous nudity and dismemberments, many of which are augmented by the in-your-face 3D element, lovesick slashers have never been quite as much fun as they are here.
Jensen Ackles, at the height of his "Supernatural" fame, stars in "My Bloody Valentine" as Tom Hanniger, the inheritor of rural Harmony's sole mine. Years prior, Harry Warden twice embarked on a Valentine's Day massacre, at one point nearly killing Tom. Tom intends to sell the mine and be done with Harmony for good, but after a decade away, someone else has taken up Harry Warden's mantle, slashing their way through dozens of people during the season of love. Lussier wisely changes not only the story's ending but also several key beats along the way, rendering his "My Bloody Valentine" less a redux and more of a contemporary update to one of the grisliest slashers around. It's not that scary, but unlike most remakes, it reeks of genuine adoration for its source material. That makes it worth falling in love with, severed heads and all.

Slasher fans finally have a chance to check out Jon Steven Ward's "Lover's Lane," a forgotten late-'90s slasher that's getting the Arrow Video treatment. Once relegated to a single DVD print and grainy online bootlegs, "Lover's Lane" doesn't necessarily do anything remarkable within the slasher template, with Jon Condit of Dread Central remarking that it's a throwback to "simpler times." However, alongside the likes of "Valentine," it shows just how fervent the last century was about subverting holiday expectations.
As is often the case, The Hook (Ed Bailey) murders several young teens at the titular lovers lane on Valentine's Day. He's incarcerated, but he escapes years later for a new series of killings, one that puts Chloe (Sarah Lancaster) and Mandy (Erin J. Dean) in his crosshairs. The real draw of "Lover's Lane," however, is an early performance by Anna Faris as Janelle, a cheerleader who'll almost certainly meet her end at the hands of The Hook. Like 2001's "The Pool," a German slasher bursting with future A-list talent, "Lover's Lane" is a straightforward, simple slasher. It eschews the post-modernity of "Scream" for a silly and fun tale of revenge. There's a purity to its modest aspirations; luckily, audiences everywhere can finally see why.

The domestic thrillers of the 1990s were something else. This was a decade when "The Hand That Rocks the Cradle," "The Good Son," and, yes, "Hush" were released to a wide audience, ably recouping their budget thanks to big name stars and outrageous terrors. Brian De Palma, perhaps the master of New Hollywood subversion, stamped one the decade's very best, "Raising Cain," with his inimitable style. John Lithgow stars as Dr. Carter Nix, a child psychologist plagued by multiple personalities, including the titular Cain, a young kid with a propensity for murder. As is often the case in De Palma's films, "Raising Cain" is a maelstrom of sexuality, violence, and obsession. Better still, it's set around Valentine's Day.
However, there's nothing all that romantic about "Raising Cain." A conspicuous Hitchcock homage, "Raising Cain" is preeminently interested in generating tension, not adhering to logic. Still, it's a remarkably accomplished feature, one that further solidifies De Palma's status as a master of psychological terror.

It's hard to argue that "Valentine" is a good movie. Jamie Blanks' slasher isn't the subversive, distinctly millennial treat that his own "Urban Legend" was three years before. However, "Valentine" has the distinct honor of being one of the last true slasher films released following the metatextual post-"Scream" boom. Sure, "Valentine" is exactly the kind of slasher movie "Scream" worked so hard to detangle, but in the years since its release our feelings about it have only grown fuzzier. With a stacked cast that includes Marley Shelton, Denise Richards, and future "Grey's Anatomy" alum Jessica Capshaw, "Valentine" is a violent tale of unrequited love and brutal murder.
Shelton stars as Kate Davies, the ringleader of a group of old middle school friends, now navigating the Los Angeles dating scene. Years before, they tormented Jeremy Melton at a school dance, though none of them have thought about him since — at least not until they get a series of strange, bloody Valentine's Day cards bearing the initials "JM." To its credit, "Valentine" tries to be more than just a body count movie. There's genuine pathos at play as "Valentine" explores the roots of body insecurity, bullying, and the shifting gender dynamics at the turn of the century. Also, it features Richards' Paige Prescott in a standout hot tub set piece. That alone makes "Valentine" worth viewing.

Certain movies linger in the mind long after they've finished, entrenching themselves into the viewer's psyche and haunting them days, weeks, or months later. They're impossible to shake. Peter Weir's "Picnic at Hanging Rock" is one such film, a haunting exploration of missing young women, burgeoning sexuality, and an ever-changing Australian landscape. Arguably one of the most famous Australian movies ever made, "Picnic at Hanging Rock" is an enigma wrapped in enigma. It's a masterpiece.
In it, several young schoolgirls and their teachers take a jaunt to Hanging Rock, a geological formation at the site of a former volcano, for a Valentine's Day picnic. They never return. The local community grapples with the inexplicable disappearances, including Dominic Guard's Michael, a young man obsessed with finding out what happened. However, Weir (as well as author Joan Lindsay, who wrote the original novel) never reveals the truth. While the lack of concrete answers might frustrate some viewers, this choice makes for a chilling ending, cementing the film's legacy as one of the eeriest films of all time.

"Pontypool" is incidentally set on Valentine's Day, but it's still the second-best horror movie set on the day of love. More than that, though, it's arguably one of the best zombie movies of all time, a slick, lean, and mean indie that's aware of its own constraints and uses them to elevate the tension and claustrophobia to masterclass levels.
In "Pontypool," a group of people are trapped in a soundproof radio booth after a virus breaks out in the world outside. This isn't a conventional disease, though. Instead, like a kind of zombified "Arrival," its power comes from language: Certain words — terms of endearment, for instance — have the capacity to infect others. Different terms infect different people, so to stay alive, the survivors must mitigate their dire straits by any means necessary without talking. On the surface, this sounds like it shouldn't work. However, as a metaphor for the power of language and its capacity to convey love, pain, and violence, it's a phenomenal achievement.

As great as Patrick Lussier's remake is, there's no topping the original. George Mihalka's "My Bloody Valentine" is infamously violent. It was so violent, in fact, that the MPAA demanded extensive cuts, with editors ultimately severing nearly nine minutes of footage from the final product. Over the years, efforts have been made to restore "My Bloody Valentine" to its original state. While Scream Factory's 2020 release is the closest the film has come to feeling complete, it's still obvious that the once-removed footage has been stitched into the theatrical cut.
Whether the censored gore is there or not, however, "My Bloody Valentine" remains a revelation. It's unusually tender, genuinely well-acted, and, like its most obvious inspirations, scary where it counts. Where the remake trades in camp, the original is an unforgiving and brutal slasher. The deaths come fast and hard, especially with the restored footage, and the climactic chase through a mine is unlike anything the horror genre has seen since. "My Bloody Valentine" stands tall as the premier Valentine's Day slasher.
Read this next: Horror Remakes That Are Better Than The Originals
The post The 12 Best Valentine's Day Horror Movies appeared first on /Film.

Aubrey Plaza is one of the most lovable celebrities out there, but she isn't just a famous personality — she's an incredible actress, and she loves her craft. Plaza totally embodies her characters in every role, including her 2022 film "Emily the Criminal," where she dons a Jersey accent and a baseball cap to play the titular protagonist.
The actress doesn't mind playing a character with complex morals; in fact, she actually prefers it. Emily might be a criminal, but she instantly charmed Plaza. Emily runs credit card scams that put a lot of people in danger, but her motivations are grounded in her unfair lot in life and a yearning for freedom.
"I think I am drawn to complicated characters that have a lot going on," Plaza admitted to The A.V. Club. "I only have myself to bring to any role that I'm playing. And I think for better or for worse, I guess I have a certain edge or something, whatever you want to call it. And so I can't help but bring myself to the part."
Just because Plaza grounds her roles in herself doesn't mean she's interested in playing characters just like herself. "I still feel a separation between me and the character," she added. "But think I try to ground every character in truth, try to relate to them and not judge what they're doing. I think a part of me comes out in everything I do, but it's not on purpose."
Plaza likes pretending to be other people. So when she read the screenplay for "Emily the Criminal," she knew she wanted to be Emily. "I didn't really think about how I was going to play it," she told The Los Angeles Times. "I just knew that I wanted to be her."

The only thing that Plaza fears when she signs onto a new project is that the writers will change the character that she fell in love with to be more like her.
"A lot of times, I'll be talking about a project with someone, and they'll go," the 'We'll tailor it just for you! We'll rewrite it just for you!' And that's my nightmare. I'm like, 'I don't want you to do that. You don't know who I am — you think you know, but you don't.' I'm an actor — just let me act."
Luckily, "Emily the Criminal" writer-director John Patton Ford didn't alter his protagonist to suit Plaza. Perhaps this is why the actress agreed to sign on as a producer as well. She didn't care that Emily was morally reprehensible -- that was just another difference she could work to embody.
"I don't judge the characters that I play, ever. It's not helpful to do that," the "Parks and Recreation" actress explained to Entertainment Weekly. "You have to understand why they're doing something, and then you have to empathize with it. And I found her to be incredibly sympathetic because she's just surviving and she's up against a system that is broken."

Plaza wasn't totally able to relate with Emily at every point in her story, and she doesn't expect you to either — she's actually counting on it. She told the L.A. Times:
"I liked how unapologetic she is in the film. I think that it's rare to have a female character like that. We're used to seeing male characters that we're watching and we don't question whether they're likable or not. So yeah, I think it's cool to have a female character that doesn't really care if people like her or not. She's doing what she's got to do."
Emily's intensity and her loaded past also enticed Plaza as an actress.
"When I read the script and when I went in to shoot that scene, I had a very clear idea of a woman who has already had enough," Plaza told Awards Daily. "She's up to here. Normally when movies start, you're down here, and you slowly get to the point where you've had enough. This movie starts when she's already had enough."
The "Ingrid Goes West" actress often plays women that seize power on the verge of a nervous breakdown, just like Harper in "The White Lotus." That doesn't mean that Plaza is like these women in real life, it just means she's a talented actress that is attracted to a particular type of role. She may bring small parts of herself to her characters, but screenwriters hoping to work with Plaza should know that the quickest way to this actress' heart is to stick to your guns.
Read this next: The Best Movies Of 2022
The post Aubrey Plaza 'Just Knew' Emily The Criminal Was The Role For Her: 'I Wanted To Be Her' appeared first on /Film.

For old-school Trekkies, the main selling point of "Picard" season 3 may be that it's getting the band back together for a full-fledged "Star Trek: The Next Generation" reunion. For the first time since the 2002 film "Star Trek: Nemesis," Jean-Luc Picard (Patrick Stewart) is being joined by all the principal members of his old "Next Generation" crew (or their evil android brothers), with Worf (Michael Dorn), Geordi La Forge (LeVar Burton), and Beverly Crusher (Gates McFadden) appearing on the show for the first time alongside the returning William Riker (Jonathan Frakes), Deanna Troi (Marina Sirtis), and Data Lore (Brent Spiner). However, as much as the third and final season of "Picard" might trade on our nostalgia for these characters, it's also looking to the future.
In a new SFX Magazine cover story, "Picard" showrunner Terry Matalas first discussed the lack of "Next Generation" movies or even TV specials since "Nemesis," despite the crowded slate of "Star Trek" shows that have popped up on Paramount+ in the days since producer Rick Berman was shepherding the franchise on network television. He told the magazine:
"That's the way of the world, whether that be Indiana Jones or 'Ghostbusters' or anything else, you don't always get to see more of those kinds of stories. It's hard to get everyone back together, to convince the studio and network that they should spend money and invest in it. You get everybody in a room, of course, you're gonna say, 'Let's do another movie.' I'm the first person to say these stories, in this time period, particularly this 'Picard' timeline, in a post-Berman universe, could continue. That's certainly where I'm the most passionate at the moment."

While previous trailers for "Picard" season 3 have leaned heavily on the novelty of seeing the "Next Generation" cast reunited, the final trailer also showed some new faces. Elsewhere in the interview, Terry Matalas alluded to the possibility of seeing some characters again "in a kind of Next, Next Generation story." However, in the same way that the first two seasons of "Picard" saw Patrick Stewart's character surrounded by a new, younger cast, Matalas suggested the third one may leave the door open for further adventures of that sort:
"This season is very much a passing of the torch to the next generation. So it will really be up to the fans to decide if they want to see more. 'Star Trek' has always been up to the fans. The fans brought back the original series characters into feature films and conventions and kept it alive, it will have to be the same here. So we'll see."
With the exception of Stewart, 82, most of the "Next Generation" cast are now in their 60s and 70s, roughly the same age as when the cast of "Star Trek: The Original Series" began retiring from their roles in the 1990s. It makes sense for them to pass the baton, and we know that fresh-faced Starfleet personnel like Geordie La Forge's daughter, for instance, will be ready to take the baton — and the ship's helm — in "Picard" season 3. There are also returning cast members like Seven of Nine (Jeri Ryan) who could potentially help lead the new generation.
In the meantime, at least "Next Generation" fans will be able to enjoy one last voyage with the former crew of the USS Enterprise (NCC-1701-D). "Star Trek: Picard" season 3 premieres February 16, 2023, on Paramount+.
Read this next: 14 Underrated Star Trek: The Next Generation Episodes
The post Picard Season 3 Will Leave Star Trek In The Hands Of The 'Next Next Generation' appeared first on /Film.

When Duke Nukem 3D burst onto the FPS scene in the Nineties, young CJ was a bit confused. This Duke wasn't the purple-shirted acrobat I'd known from Apogee Software's pair of platformers earlier that decade. He was brash, crude, and and didn't side-scroll anymore. It wasn't for me, so I moved on to other games. I still occasionally loaded up those earlier platformers though, wistfully remembering a time when Duke presumably used actual toilets when he needed to answer a call of nature.
Read more of this story at Slashdot.

A Control mod created by Remedy gameplay programmer Filippo Tardini was updated a few hours ago to also add native HDR display support. Since he has access to the game code, the results are superior to Microsoft's AutoHDR or SpecialK HDR.
Here's the full changelog:
This Control mod does not work with the Microsoft Store version of the game. Additionally, HDR only works when running the game in DirectX 12 mode. To activate it, you can enable it in Windows or in the game itself. Make sure to run the calibration app first since the Control mod will read the calibration results.
There are also several HDR settings added to the graphics options, such as HDR Brightness, HDR Extra Saturation, HDR Deeper Blacks, and HDR Ui Brightness. Regarding the HDR conversion, Tardini explained:
The HDR implementation skips the Reinhard tonemapper the game used in SDR. In my opinion it made the image look overly flat, which was a choice dictated by the limitations of SDR. Removing it allows to take full advantage of HDR, by outputting an image with a much greater level of contrast, and without disadvantages to visibility.
HDR support was the only missing feature in what was otherwise a fantastic graphical showcase. If you still haven't played this great game, check out this Control mod and let us know if you like it.
The post Control Mod Developed by Remedy Programmer Adds Native HDR, Full Ultrawide Support by Alessio Palumbo appeared first on Wccftech.

It’s redundant to describe a film as “a dark fairy tale.” All fairy tales are imbued with the darkness that children understand on a primal level. Folklore from every culture is filled with fear, grief, and death, because these are universal experiences. They feel especially potent for children, who sometimes lack the world-weariness that gives context to their terror, but children understand these heavy concepts just as much as adults do. Writer-director Kenneth Dagatan’s IN MY MOTHER’S SKIN is one such potent fairy tale. It turns a tale of war and colonialism into a microcosm of faith, loss, and betrayal; it is a world where fairies are not to be trusted, no matter how beautiful they may be.
Tala (Felicity Kyle Napuli) and her brother Bayani (James Mavie Estrella) live in the Philippines near the end of World War II. Their father is gone, and their mother Ligaya (Beauty Gonzalez) is ill. They’re running out of food, so when Tala finds some candy in the forest one day, she can’t resist it. The candy is a trap, though, for a Fairy (Jasmine Curtis-Smith) appears, offering her things that sound too good to be true: treats, a delicious feast out of nowhere, and most importantly, a cure for her mother. That cure sends Ligaya down a disturbing road of transformation and destruction, and Tala soon learns that not all fairy tales have happy endings.
The Fairy is a striking mix of native and invading species. She has insect wings and a voice that echoes like a cicada; indeed, she tells Tala that she gets her power from the cicadas that turn the forest into a living thing, always singing and watching. Their frenzied song is a truly effective bit of sound design, turning the cicadas’ omnipresence into a maddening reminder that the worst is yet to come. The Fairy’s elaborate, beautiful garb (courtesy of costume designer Carlo Tabije) looks just like the statue of the Virgin Mary that Ligaya prays to throughout the day. Dagatan isn’t just interested in the Japanese and American invasions of the Philippines alluded to in the adult conversations about the war. He’s also commenting on the Spanish colonialism that brought Catholicism to the islands. The Fairy is both a representation of all of Tala’s childhood hopes and fears and a complicated mix of cultures, including those that have invaded the Philippines over the centuries.
The gore and body horror in the aptly named IN MY MOTHER’S SKIN reminds the viewer of other Southeast Asian skin-crawling horror films. The contrast between the grotesque special effects and the forlorn tone makes for a remarkable horror fable. The foreboding yet mournful score highlights Tala and Bayani’s isolation and hopelessness. With no adults left to look out for them and a dwindling food supply, alone during wartime, where can they go? What can they do? Dagatan and cinematographer Russell Adam Morton weaponize slow pans that reveal disturbing shots of corpses and dense woods full of whispers. The skillful framing and patient camerawork turn beautiful golden hour shots into reminders that — like many classic fairy tales — these two young children are alone in the woods with a monster. Whether that monster is a devious Fairy or the war itself, the result is the same.
IN MY MOTHER’S SKIN is a haunting piece of Filipino folk horror that, yes, gets under the viewer’s skin. It’s a captivating and heartbreaking story that embraces the darkness at the heart of all fairy tales and finds the horror in grief, loss, and displacement. Ultimately, IN MY MOTHER’S SKIN takes the viewer on a child’s futile and terrifying journey to try to understand a world that makes no sense.
IN MY MOTHER’S SKIN had its world premiere at the 2023 Sundance Film Festival. It has been acquired by Amazon Prime Video.
The post [Sundance Review] IN MY MOTHER’S SKIN appeared first on Nightmarish Conjurings.
Shadow Warrior 3 is an insane first person slasher/shooter with a quipping hero named Lo Wang taking on hordes of different beasts and monsters. Sometimes you can slice them up with your katana. Sometimes you can shoot them with one of your special weapons. And sometime you can walk up to them, and perform a fatality-esq special kill, that will give you their powers. Larger than life bosses, hilarious banter, and off the wall weapons and arena kills are in this Devolver Digital blood fest, on the back of a story about restoring a previous foe/friend to his former demonic glory. It's a LOT, and I gave it an 8.5 in my review, because though it was hard, I was thoroughly entertained.
Now, because you need more chaos, Shadow Warrior 3 is getting that good next gen upgrade treatment. Shadow Warrior 3: Definitive Edition will be released on Xbox Series, PS5, and PC on February 16th, and if you already have a copy, you get the upgrade for the free free.
New modes include Survival Mode, which opens three battle arenas, and plenty of foul beasts for you to carve through. Enduring this will net you 3 weapon skins. Also added is a chapter select mode, so you can go back and get any missing upgrades. There's even New Game+, a hardcore difficulty, and a limited respawn mode called "Hero Mode".
Other enhancements include haptics and controller speaker support for the PS5, and your choice. 60fps mode, or 4k/30 fps, for you cinematic freaks out there. Check out the video below, and pull Wang back out on February 16th. Devolver would appreciate that last line.

During the last AMD earnings call with investors and analysts, Dr. Lisa Su, AMD CEO, revealed that the company held back shipments of CPUs and GPUs over the previous two quarters. She went on further to explain that the company will continue to lessen orders for the next quarter, albeit much less.
The company feels that this next quarter will return the most diminutive sales figures due to the slow but stagnant marketplace for computers and components. NVIDIA recently admitted to similar restraint for its GPUs two months ago but has not revealed any recent details as to if they are continuing this practice. Most companies outside of computer components generally see a lack of sales during the first few months after the holiday season.
We do believe the first quarter is the bottom for our PC market — for our PC business, and we’ll see some growth in the second quarter and then a seasonally higher second half. In terms of the under shipment, I mean, I think we’re — we undershipped in Q3, we undershipped in Q4.
We will undership, to a lesser extent, in Q1. So I think you can infer that from our guidance single-digit down. And then, we’ll be back to a more normal environment. Now, just as a reminder though, the first half is not usually a — the first half is usually a seasonally weak client time anyways.
— Dr. Lisa Su, Chief Executive Officer, AMD
To stay competitive, AMD did lower the pricing on CPUs and GPUs over the last few quarters. The company's current AMD Ryzen 7000 series processors saw a dramatic twenty percent decrease in pricing since its first month of release. Intel has faced the complete opposite and continued to ship an excess of inventory into the market which is getting hard to get off the shelves due to a decline in the PC segment.

The new AMD Ryzen 7000X3D series will begin shipping during the latter half of this month, starting at $449 for the AMD Ryzen 7 7800X3D, $599 for the AMD Ryzen 9 7900X3D, and $699 for the AMD Ryzen 9 7950X3D. The Ryzen 9 7950X CPU was initially released with an MSRP of $699 but is currently selling below $600 with no sign of increasing the cost of the chip in the future.
The post AMD Admits To Overpricing & Underselling CPUs/GPUs Over Last Two Quarters, Plans To Continue Practice by Jason R. Wilson appeared first on Wccftech.
It's a bountiful harvest season in Dwarf Fortress land, and this time, the crop isn't plump helmets - it's cold, hard cash. Brothers Tarn and Zach Adams have posted their monthly earnings report for their legendary colony management game, and January's earnings - the first to include sales of the new Steam edition of Dwarf Fortress - totaled more than $7 million USD.
Read more of this story at Slashdot.
Researchers warn that many electric vehicle (EV) charging management systems are affected by vulnerabilities that could allow hackers to cause disruption, steal energy, or obtain driver information.
The vulnerabilities were discovered by researchers working for SaiFlow, an Israel-based company that specializes in protecting EV charging infrastructure and distributed energy resources.
The security holes are related to the communications between the charging system management service (CSMS) and the EV charge point (CP), specifically the use of the Open Charge Port Protocol (OCPP). The flaws have been confirmed to impact the CSMS offered by multiple vendors.
The problem is related to the use of WebSocket communications by the OCPP and how it mishandles multiple connections. The protocol does not know how to handle more than one CP connection at a time and attackers could abuse this by opening a new connection to the CSMS. Another issue is related to what SaiFlow describes as “weak OCPP authentication and chargers identities policy”.
By opening a new connection to the CSMS on behalf of a charge point, the attacker causes the original connection to be closed or to become nonfunctional.
According to SaiFlow, an attacker can exploit the weaknesses to launch a distributed denial-of-service (DDoS) attack that disrupts the electric vehicle supply equipment (EVSE) network. In addition, if an attacker can connect to the CSMS, they may be able to obtain drivers’ personal information, including payment card data, as well as other sensitive data, such as server credentials.
In certain configurations, if the charger approves unknown driver identities, an attacker may be able to charge their vehicle without paying for it, the security firm said.
“Since the CSMS platforms are publicly accessible, it is possible for an attacker to hijack the connection remotely, without needing to gain credentials, access, or perform MITM attacks,” Ron Tiberg-Shachar, co-founder and CEO of SaiFlow, told SecurityWeek.
Tiberg-Shachar believes it may be possible for a somewhat inexperienced hacker to carry out an attack, even with limited resources.
In order to conduct an attack, the hacker first needs to obtain a charger’s identity. This identity typically has a standard structure, making it easier for threat actors to enumerate the values of valid identifiers.
In the next phase, they need to obtain information on which CSMS platform the charger is connected to. The expert noted that the CSMS URL can be discovered using services such as Shodan or SecurityTrails.
SaiFlow has published a technical blog post describing the vulnerabilities and the attack scenarios. The company also provides recommendations for how these types of attacks can be mitigated.
It doesn’t seem like the vulnerabilities can be easily patched by vendors.
“We’ve approached many key players in the industry (and keep on doing so) to make them aware of our findings and how they can approach a solution,” Tiberg-Shachar said. “Additionally, we’ve made our solutions team available to support any specific technical questions, in an effort to reinforce vulnerabilities as quickly as possible. Our key goal is to support partners in scaling their charging infrastructure as quickly and safely as possible.”
Related: Unpatched Econolite Traffic Controller Vulnerabilities Allow Remote Hacking
Related: Remote ‘Brokenwire’ Hack Prevents Charging of Electric Vehicles
Related: New Flaws Expose EVlink Electric Vehicle Charging Stations to Remote Hacking
The post EV Charging Management System Vulnerabilities Allow Disruption, Energy Theft appeared first on SecurityWeek.
About SecurityWeek Cyber Insights | At the end of 2022, SecurityWeek liaised with more than 300 cybersecurity experts from over 100 different organizations to gain insight into the security issues of today – and how these issues might evolve during 2023 and beyond. The result is more than a dozen features on subjects ranging from AI, quantum encryption, and attack surface management to venture capital, regulations, and criminal gangs.

SecurityWeek Cyber Insights 2023 | Supply Chain Security – The supply chain threat is directly linked to attack surface management (it potentially represents a hidden part of the attack surface) and zero trust (100% effective zero trust would eliminate the threat). But the supply chain must be known and understood before it can be remediated.
In the meantime – and especially throughout 2023 – it will be a focus for adversaries. Why attack a single target when successful manipulation of the supply chain can get access to dozens or even hundreds of targets simultaneously.
The danger and effectiveness of such attacks is amply illustrated by the SolarWinds, log4j, Spring4Shell, Kaseya, and OpenSSL incidents.
Supply chain attacks are not new. The iconic Target breach of late 2013 was a supply chain breach. The attackers got into Target using credentials stolen from its HVAC provider, Fazio Mechanical Services – that is, via Target’s supply chain.
The 2018 breach of Ticketmaster was another supply chain breach. A Ticketmaster software supplier, Inbenta, was breached and Inbenta software was modified and weaponized. This was automatically downloaded to Ticketmaster.
Island hopping is another form of supply chain attack. In 2017, Operation Cloud Hopper was revealed. This disclosed that an advanced group, probably APT10, was compromising managed service providers to gain access to the MSP’s customers.
Despite these incidents, it has only been in the last couple of years, fueled by more extensive incidents such as SolarWinds, that industry has become cognizant of the full threat from increasingly sophisticated and wide-ranging supply chain concerns. But we should not forget that the 2017 NotPetya incident also started as a supply chain attack. Software from the Ukrainian accounting firm M.E.Doc was weaponized and automatically downloaded by the firm’s customers, before spreading around the globe. Both SolarWinds and NotPetya are believed to be the work of nation state actors.
All forms of supply chain attacks will increase in 2023, and beyond. Chad Skipper, global security technologist at VMware, specifically calls out island hopping. “In 2023, cybercriminals will continue to use island hopping, a technique that aims to hijack an organization’s infrastructure to attack its customers,” he warns. “Remote desktop protocol is regularly used by threat actors during an island-hopping campaign to disguise themselves as system administrators. As we head into the new year, it’s a threat that should be top of mind for all organizations.”
That supply chain attacks will increase in 2023 and beyond is the single most extensive prediction for 2023. “Supply chain attacks happen when hackers gain access to a company’s inner workings via a third-party partner, a method that provides them with a much greater amount of privileged information from just one breach,” explains Matt Jackson, senior director security operations at Code42. “This type of attack already rose by more than 300% in 2021, and I anticipate this trend will continue in 2023, with these attacks becoming more complicated and intricate.”

Lucia Milică, global resident CISO at Proofpoint, worries that despite all the wake-up calls so far, “We are still a long way from having adequate tools to protect against those kinds of digital supply chain vulnerabilities. We predict these concerns will mount in 2023, with our trust in third-party partners and suppliers becoming one of the primary attack channels.”
The result, she added, is, “We expect more tension in supply chain relationships overall, as organizations try to escalate their vendors’ due diligence processes for better understanding the risks, while suppliers scramble to manage the overwhelming focus on their processes.”
Jackson added, “Because many third-party partners are now privy to more sensitive data than ever before, companies can no longer rely on their own cybersecurity prowess to keep information safe,” he said.
“Supply chain attacks purposefully target the smaller organizations first because they’re less likely to have a robust cybersecurity setup, and they can use those companies to get to the bigger fish,” he continued. “In the next year, companies will become even more diligent when deciding on an outside organization to work with, creating an increase in compliance verifications to vet the cyber tools used by these prospective partners.”
Anand Raghavan, co-founder and CPO at Armorblox, expands on this theme. “This becomes particularly relevant,” he said, “for the Fortune 500 or Global 2000 companies that have a large ecosystem of suppliers, vendors, and distributors whose security stacks are nowhere as mature as those of large organizations. Large organizations might consider requiring all vendors to follow certain security best practices, including modernizing their email security stack if they want to continue being a vendor in good standing.”
Interestingly, despite all the warnings of an escalating threat, Christopher Budd, senior manager of threat research at Sophos, notes, “Unlike two years ago when the SolarWinds attack put supply chain attacks high on people’s radar, supply chain attacks have faded from prominence.” This may be a misleading premise. The discovery of a vulnerability in a widely used piece of software, such as the log4j vulnerability, will be used by individual cybercriminals and nation state actors alike.
However, targeted attacks such as that against SolarWinds requires resources and skill. These attributes are more usually found only in the more advanced gangs and nation state actors. Such adversaries have another attribute: patience. “Today’s and undoubtedly tomorrow’s threat actors have shown they can play the long game,” warns Pieter Arntz, senior intelligence reporter at Malwarebytes.
Budd also warns that despite their immediate lack of prominence (at the time of writing, but anything could happen tomorrow), “Supply chain may be something that continues to not gather news, similar to 2022. But it will remain a real threat and one that organizations should be prioritizing across the board, in part because effectively countering this threat requires a comprehensive, careful, methodical approach.”
The primary growth area in supply chain attacks will likely be the software supply chain. “Over the past few years,” explains Eilon Elhadad, senior director of supply chain security at Aqua, “increasing pressure to deliver software faster has widened attack surfaces and introduced severe vulnerabilities.”
New tools, languages and frameworks that support rapid development at scale are being targeted by malicious actors, who understand the widespread impact that results from attacks to the software supply chain.
“In 2023,” Elhadad continued, “software supply chain threats will continue to be a significant area of concern. These attacks have a larger potential blast radius to allow hackers to impact entire markets and wreak havoc for organizations.”
Eric Byres, founder and CTO at aDolus, agrees. “Software supply chain attacks will continue to increase exponentially in 2023,” he said; “the ROI on these attacks is just too sweet for professional adversaries to resist.” He notes that supply chain attacks have increased by 742% over the last three years.
Much of the software supply chain threat comes from the growing reliance on open source software libraries as part of the ‘increasing pressure to deliver software faster’. Zack Zornstain, head of supply chain security at Checkmarx, believes the software threat will particularly affect the open source supply.
“We believe that this threat of compromising open source packages will increase as malicious code can endanger the safety of our systems, ranging from ransomware attacks to the exposure of sensitive information, and more. We expect to see this as a general attack vector used both by cyber firms and nation-state actors. SBOM adaptation will help clarify which packages we’re using in applications, but we will need to invest in more controls to ensure the safety of those packages,” he said.
“Organizations should be on high alert for supply chain attacks if they use open-source software,” warns Kevin Kirkwood, deputy CISO at LogRhythm. “Bad actors examine the code and its components to obtain a thorough understanding of its flaws and the most effective ways to exploit them.”
If the source code of an open source software library either has – or can be engineered by bad actors to have – a vulnerability, then every company that downloads and uses that code becomes vulnerable.
“In 2023,” continues Kirkwood, “we’ll see bad actors attack vulnerabilities in low-hanging open-source vendors with the intention of compromising the global supply chain that uses third-party code. Attackers will infect the open-source repositories and chromium stores with malicious code and will wait for developers and other end users to come along and pick up the new sources and plugins.”
Venafi’s Matt Barker, president of cloud native solutions, adds, “We’re seeing many instances of vulnerable code brought inside their firewall by developers trying to go fast using unverified code from GitHub, or copypasta from Stack Overflow.”
He continues, “Thankfully, we’ve reached a collective sense of focus on this area and are seeing tremendous developments in how we tackle it. This is only going to increase through 2023 as we see more start-ups popping up and open source tools like cosign and sigstore designed to help it. Biden’s SBOM initiative has helped bring attention to the requirement, and The OpenSSF is leading in this charge.”
Mark Lambert, VP of products at ArmorCode, expands on this. “As the software supply chain continues to get more complicated, it is vital to know what open source you are indirectly using as part of third-party libraries, services (APIs) or tools. This is where SBOM comes in,” he said. “By requiring a disclosure of all embedded technologies from your vendors, you can perform analysis of those libraries to further assess your risk and react appropriately.”
Biden’s May 2021 Executive Order on Improving the Nation’s Cybersecurity introduced the concept of a software bill of materials (SBOM), effectively if not actually mandating that software bought (or supplied) by government agencies be accompanied with a bill of materials. It described the SBOM as “a formal record containing the details and supply chain relationships of various components used in building software,” and analogous to a list of ingredients on food packaging.
While the advantages of the SBOM may appear obvious in helping software developers understand precisely what is included in the open source libraries they use, it must be said that not everyone is immediately enthusiastic. In December 2022, it emerged that a lobbying group representing major tech firms such as Amazon, Microsoft, Apple, Intel, AMD, Lenovo, IBM, Cisco, Samsung, TSMC, Qualcomm, Zoom and Palo Alto Networks was urging the OMB to ‘discourage agencies’ from requiring SBOMs. The group argued that the requirement is premature and of limited value — but it didn’t ask for the concept to be abandoned.
It is the complexity and difficulty in both compiling and using an SBOM that is the problem — and it is these concerns that will drive a lot of activity through 2023. The value of the concept outlined in the executive order remains undiminished.
“Incidents such as Log4shell [log4j] and the most recent SpookySSL vulnerabilities [CVE-2022-3602 and CVE-2022-3786] will push the adoption of a software bill of materials as a core component of achieving effective incident response, while efforts will continue in maturing the SBOM ecosystem (adoption across sectors, tooling, standardization around sharing and exchanging of SBOMs and more),” explains Yotam Perkal, director of vulnerability research at Rezilion.
“One of the big challenges I see in the year ahead is that this is more data for the development teams to manage as they deliver software,” notes Lambert. “In 2023, organizations are going to need ways to automate generating, publishing and ingesting SBOMs – they will need ways to bring the remediation of the associated vulnerabilities into their current application security programs without having to adopt whole new workflows.”
As part of this process, Michael Assraf, CEO and co-founder at Vicarius, said, “We predict that a new market will evolve called binary software composition analysis, which will look for software files that are different from what was pre-packaged and shipped. Automated techniques can utilize machine learning that will find this discrepancy, which will be vital in knowing where your risk lies and how large your attack surface can potentially be.”

Thomas Pace, CEO at NetRise, suggests, “SBOM is going to continue to garner mainstream adoption, not just from software/firmware suppliers that are building products they are selling, but also for internal development teams that are building applications and systems for internal use.”
He adds, “The need to be able to rapidly understand the provenance of software components is becoming increasingly critical. Without this visibility, the window for attackers to exploit these vulnerabilities is much too big and puts cyber defenders at a significant disadvantage.” But he also notes, “strong efforts from organizations like Google have moved the ball forward in a positive way. Efforts such as open-source insights provide a lot of visibility for end users and vendors alike to scale out the analysis of these components.”
The problems involved with SBOM generation and use have not yet been solved, but enthusiasm remains. We can expect considerable effort into automating these processes to continue throughout 2023.
Nevertheless, Kurt Baumgartner, principal security researcher at Kaspersky, warns, “Open source projects continue to be polluted with malicious code. Awareness of these issues and challenges increase, but the attacks continue to be effective on a large scale. Despite the best efforts of software bill of materials, complex dependency chains help ensure that malicious code is uncontrolled for a time in some projects.”
Despite all companies’ need to be wary of potential software supply chain attacks via the code they develop for their own use, we should not forget that there is a potentially more catastrophic physical supply chain threat. We need only consider the effect the prevention of grain supplies leaving Ukraine (because of the Russia/Ukraine conflict) had on global food supplies to see the potential. Covid-19 also affected many different global supply chains, causing panic buying and popular distress in its early days.
These were not the result of cyberattacks – but many of those physical supply chains could be disrupted by cyberattacks. The Colonial Pipeline incident, although a financially motivated attack, had an immediate effect on the supply of oil to eastern USA. The longer the Ukraine/Russia conflict continues, and the greater that east/west tensions increase, the possibility of physical supply chain cyber disruption will equally increase through 2023, and possibly beyond.
SecurityWeek discussed one such possibility in May 2022: The Vulnerable Maritime Supply Chain – a Threat to the Global Economy here.
Lorri Janssen-Anessi, director of external cyber assessments at BlueVoyant notes that in the utilities and energy sector, “99% of energy companies say they have been negatively impacted by at least one supply chain breach in the past year, representing the highest rate of overall impact in any other industry. Because it remains one of the most frequently attacked verticals, it is especially crucial that it rises to the challenge of supply chain defense in 2023.”
Taylor Gulley, senior application security consultant at nVisium, comments, “The past few years have shown that both the digital supply chain, as well as the physical world supply chain, are very fragile. This fragility is due to a lack of redundancy and resources due to economic constraints or skill gaps. For 2023, this situation will still stand true. Supply chain security is a weak link that needs to be strengthened.”

Sam Curry, CSO at Cybereason, believes the SBOM will be an important part of solving the software supply chain problem. “It would be naive in the extreme to think that with thousands of trusted software and service providers to choose from… that the handful of known supply chain compromises were the sum total of them. No. 2023 will show us more, and we will be lucky to learn of them because the attacker can quietly exploit these without tipping their hands.”
He added, “We need to use 2023 to be innovative and vigilant and to find new answers to the supply chain problem, to build on software bills of material, to innovate with the men and women building our software and to find the solutions to deter, to detect and to remove the vulnerabilities and exposures that enable this most insidious and trust eroding of attacks.”
Sharon Chand, Deloitte US’ cyber risk secure supply chain leader, believes that software supply chain security will require continuous realtime monitoring of third-party risks and vulnerabilities in inbound packaged software and firmware components. “For instance,” she said, “this includes implementing leading practice techniques around ingesting SBOMs and correlating the output to emerging vulnerabilities, identifying risk indicators such as geographical origin of the underlying components, and providing visibility to transitive dependencies.”
Christian Borst, EMEA CTO at Vectra AI, suggests collaboration and cooperation across the software industry will be required. “A holistic approach may help turn the tables on the matter: supply chain means partnership – partnership means collaboration and supporting each other. Only as a ‘mesh’ interconnected structure with consistent resiliency can companies thrive in the digital economy. This includes ensuring that they review the security policies of all those in the chain.”
Sounil Yu, CISO at JupiterOne, makes a fitting summary, referencing a paper written by Richard Danzig in July 2014 (Surviving on a Diet of Poisoned Fruit: Reducing the National Security Risks of America’s Cyber Dependencies). “To borrow Richard Danzig’s analogy,” says Yu, “we are on a diet of poisoned fruit with respect to our software supply chain. This poison is not going to go away, so we will need to learn how to survive and thrive under these conditions. Being aware of the risks, through efforts such as SBOM, and managing the risks through compensating controls such as egress filtering, will be a priority in 2023 and the foreseeable future.”
Related: US Gov Issues Software Supply Chain Security Guidance for Customers
Related: OpenSSF Adopts Microsoft-Built Supply Chain Security Framework
Related: Hundreds Infected With ‘Wasp’ Stealer in Ongoing Supply Chain Attack
Related: US Gov Issues Supply Chain Security Guidance for Software Suppliers
The post Cyber Insights 2023 | Supply Chain Security appeared first on SecurityWeek.
About SecurityWeek Cyber Insights | At the end of 2022, SecurityWeek liaised with more than 300 cybersecurity experts from over 100 different organizations to gain insight into the security issues of today – and how these issues might evolve during 2023 and beyond. The result is more than a dozen features on subjects ranging from AI, quantum encryption, and attack surface management to venture capital, regulations, and criminal gangs.

SecurityWeek Cyber Insights 2023 | Ransomware – The key purpose behind cybercriminality is to gain money. Extortion has always been a successful and preferred method to achieve this. Ransomware is merely a means of extortion. Its success is illustrated by the continuous growth of ransomware attacks over many years.
The evolution of ransomware has not been static. Its nature has changed as the criminals have refined the approach to improve the extortion, and the volume (generally upward) has ebbed and flowed in reaction to market conditions. The important point, however, is that criminals are not married to encryption, they are married to extortion.
The changing nature of what we still generally call ransomware will continue through 2023, driven by three primary conditions: the geopolitical influence of the Russia/Ukraine war, the improving professionalism of the criminal gangs, and more forceful attempts by governments and law enforcement agencies to counter the threat.
The Russia/Ukraine war has removed our blinkers. The world has been at covert cyberwar for many years – generally along the accepted geopolitical divide – but it is now more intense and more overt. While the major powers, so far at least, have refrained from open attacks against adversaries’ critical infrastructures, criminal gangs are less concerned.
“The rate of growth in ransomware attacks is currently slowing slightly [late 2022] – but this will prove to be a false dawn,” suggests Mark Warren, product specialist at Osirium. “Currently, the most successful teams of cybercriminals are focused on attacking Ukraine’s critical infrastructure. The second that conflict is over, all the technology, tools and resources will be redeployed back into ransomware attacks – so organizations and nation states alike must not become complacent.”
One of the most likely effects of the European conflict will be an increasingly destructive effect from ransomware. This has already begun and will increase through 2023. “We are seeing an increase in more destructive ransomware attacks at scale and across virtually all sector types, which we expect to continue into 2023,” comments Aamir Lakhani, cybersecurity researcher and practitioner for FortiGuard Labs.
“Ransomware will continue to make headlines, as attacks become more destructive, and threat actors develop new tactics, techniques, and procedures to try and stay one step ahead of vendors,” agrees John McClurg, SVP and CISO at BlackBerry.
“We expect ransomware to continue its assault on businesses in 2023,” says Darren Williams, CEO and founder at BlackFog. “Specifically, we will see a huge shift to data deletion in order to leverage the value of extortion.”
There are two reasons for this move towards data deletion. Firstly, it is a knock-on effect of the kinetic and associated cyber destruction in Ukraine. But secondly it is the nature of ransomware. Remember that ransomware is merely a means of extortion. The criminals are finding that data extortion is more effective than system extortion via encryption. Andrew Hollister, CISO LogRhythm, explains in more detail:
“In 2023, we’ll see ransomware attacks focusing on corrupting data rather than encrypting it. Data corruption is faster than full encryption and the code is immensely easier to write since you don’t need to deal with complex public-private key handling as well as delivering complex decryption code to reverse the damage once the victim pays up,” he said.
“Since almost all ransomware operators already engage in double extortion, meaning they exfiltrate the data before encrypting it, the option of corrupting the data rather than going to the effort of encryption has many attractions. If the data is corrupted and the organization has no backup, it puts the ransomware operators in a stronger position because then the organization must either pay up or lose the data.”

It should also be noted that the more destruction the criminal gangs deliver after exfiltrating the data, the more completely they will cover their tracks. This becomes more important in an era of increasing law enforcement focus on disrupting the criminal gangs.
But there is an additional danger that might escape from the current geopolitical situation. Vitaly Kamluk, head of the Asia-Pacific research and analysis team at Kaspersky explains: “Statistically, some of the largest and most impactful cyber epidemics occur every six to seven years. The last such incident was the infamous WannaCry ransomware-worm, leveraging the extremely potent EternalBlue vulnerability to automatically spread to vulnerable machines.”
Kaspersky researchers believe the likelihood of the next WannaCry happening in 2023 is high. “One potential reason for an event like this occurring,” continued Kamluk, “is that the most sophisticated threat actors in the world are likely to possess at least one suitable exploit, and current global tensions greatly increase the chance that a ShadowBrokers-style hack-and-leak could take place.”
Finally, it is worth mentioning an unexpected effect of the geopolitical situation: splintering and rebranding among the ransomware groups. Most of the larger groups are multi-national – so it should be no surprise that different members might have different geopolitical affiliations. Conti is perhaps the biggest example to date.
“In 2022, many large groups collapsed, including the largest, Conti,” comments Vincent D’Agostino, head of digital forensics and incident response at BlueVoyant. “This group collapsed under the weight of its own public relations nightmare, which sparked internal strife after Conti’s leadership pledged allegiance to Russia following the invasion of Ukraine. Conti was forced to shut down and rebrand as a result.” Ukrainian members objected and effectively broke away, leaking internal Conti documents at the same time.
But this doesn’t mean that the ransomware threat will diminish. “After the collapses, new and rebranded groups emerged. This is expected to continue as leadership and senior affiliates strike out on their own, retire, or seek to distance themselves from prior reputations,” continued D’Agostino.
The fracturing of Conti and multiple rebrandings of Darkside into their current incarnations has demonstrated the effectiveness of regular rebranding in shedding unwanted attention. “Should this approach continue to gain popularity, the apparent number of new groups announcing themselves will increase dramatically when in fact many are fragments or composites of old groups.”
The increasing sophistication, or professionalism, of the criminal gangs is discussed in Cyber Insights 2023: Criminal Gangs. Here we will focus on how this affects ransomware.
The most obvious is the emergence of ransomware-as-a-service. The elite gangs are finding increased profits and reduced personal exposure by developing the malware and then leasing its use to third-party affiliates for a fee or percentage of returns. Their success has been so great that more, lesser skilled gangs will follow the same path.
“It initially started as an annoyance,” explains Matthew Fulmer, manager of cyber intelligence engineering at Deep Instinct, “but now after years of successful evolution, these gangs operate with more efficiency than many Fortune 500 companies. They’re leaner, meaner, more agile, and we’re going to see even more jump on this bandwagon even if they’re not as advanced as their partners-in-crime.”
The less advanced groups, and all affiliates of RaaS, are likely to suffer at the hands of law enforcement. “It is likely that there will be a constant battle between law enforcement agencies and ransomware affiliates. This will either be veteran/more established ransomware affiliates or new ransomware groups with novel ideas,” comments Beth Allen, senior threat intelligence analyst at Intel 471.
“Much like whack-a-mole, RaaS groups will surface, conduct attacks, be taken down or have their operations impacted by LEAs – and then go quiet only to resurface in the future. The instability within criminal organizations that we have observed will also be a contributing factor to groups fading and others surfacing to fill the void.”
As defenders get better at defending against ransomware, the attackers will simply change their tactics. John Pescatore, director of emerging security trends at SANS, gives one example: “Many attackers will choose an easier and less obtrusive path to gain the same critical data. We will see more attacks target backups that are less frequently monitored, can provide ongoing access to data, and may be less secure or from forgotten older files.”
Drew Schmitt, lead analyst at GuidePoint, sees increased use of the methodologies that already work, combined with greater attempts to avoid law enforcement. “Ransomware groups will likely continue to evolve their operations leveraging critical vulnerabilities in commonly used applications, such as Microsoft Exchange, firewall appliances, and other widely used applications,” he suggested.
“The use of legitimate remote management tools such as Atera, Splashtop, and Syncro is likely to continue to be a viable source of flying under the radar while providing persistent access to threat actors,” he added.
But, he continued, “ransomware ‘rebranding’ is likely to increase exponentially to obfuscate ransomware operations and make it harder for security researchers and defenders to keep up with a blend of tactics.”
Warren expects to see criminal ransomware attacks focusing on smaller, less well-defended organizations. “State actors will still go after large institutions like the NHS, which implement robust defenses; but there are many small to mid-size companies that invest less in protection, have limited technical skills, and find cyberinsurance expensive – all of which makes them easy targets.”
This will partly be an effect of better defenses in larger organizations, and partly because of the influx of less sophisticated ransomware affiliates. “We can expect smaller scale attacks, for lower amounts of money, but which target a much broader base. The trend will probably hit education providers hard: education is already the sector most likely to be targeted,” he continued.
He gives a specific example from the UK. “Every school in the UK is being asked to join a multi-academy trust, where groups of schools will be responsible for themselves. With that change comes great vulnerability. This ‘network’ of schools would be a prime target for ransomware attacks; they are connected, and they’re unlikely to have the resilience or capabilities to protect against attacks. They may have no choice but to reallocate their limited funds to pay ransom demands.”
But it won’t just be more of the same. More professionalized attackers will lead to new attack techniques. Konstantin Zykov, senior security researcher at Kaspersky, gives an example: the use of drones. “Next year, we may see bold attackers become adept at mixing physical and cyber intrusions, employing drones for proximity hacking.”
He described some of the possible attack scenarios, such as, “Mounting drones with sufficient tooling to allow the collection of WPA handshakes used for offline cracking of Wi-Fi passwords or even dropping malicious USB keys in restricted areas in hope that a passerby would pick them up and plug them into a machine.”
Marcus Fowler, CEO of Darktrace Federal, believes the existing ransomware playbook will lead to increased cloud targeting. “Part of this playbook is following the data to maximize RoI. Therefore, as cloud adoption and reliance continue to surge, we are likely to see an increase in cloud-enabled data exfiltration in ransomware scenarios in lieu of encryption,” he said. “Third-party supply chains offer those with criminal intent more places to hide, and targeting cloud providers instead of a single organization gives attackers more bang for their buck.”
Evasion and persistence are other traits that will expand through 2023. “We continue to see an emergence in techniques that can evade typical security stacks, like HEAT (Highly Evasive Adaptive Threats) attacks,” says Mark Guntrip, senior director of cybersecurity strategy at Menlo. “These tactics are not only are tricking traditional corporate security measures but they’re also becoming more successful in luring employees into their traps as they identify ways to appear more legitimate by delivering ransomware via less suspecting ways – like through browsers.”
Persistence, that is, a lengthy dwell time, will also increase in 2023. “Rather than blatantly threatening organizations, threat actors will begin leveraging more discreet techniques to make a profit,” comments JP Perez-Etchegoyen, CTO at Onapsis. “Threat groups like Elephant Beetle have proven that cybercriminals can enter business-critical applications and remain undetected for months, even years, while silently siphoning off tens of millions of dollars.”
David Anteliz, senior technical director at Skybox, makes a specific persistence prediction for 2023: “In 2023, we predict a major threat group will be discovered to have been dwelling in the network of a Fortune 500 company for months, if not years, siphoning emails and accessing critical data without a trace. The organizations will only discover their data has been accessed when threat groups threaten to take sensitive information to the dark web.”
The effect of ransomware and its derivatives will continue to get worse before it gets better. Apart from the increasing sophistication of existing gangs, there is a new major threat – the worsening economic conditions that will have a global impact in 2023.
Firstly, a high number of cyber competent people will be laid off as organizations seek to reduce their staffing costs. These people will still need to make a living for themselves and their families – and from this larger pool, a higher than usual number of otherwise law-abiding people may be tempted by the easy route offered by RaaS. This alone could lead to increased levels of ransomware attacks by new wannabe criminals.
Secondly, companies will be tempted to reduce their security budgets on top of the reduced staffing levels. “Once rumblings of economic uncertainty begin, wary CFOs will begin searching for areas of superfluous spending to cut in order to keep their company ahead of the game,” warns Jadee Hanson, CIO and CISO at Code42. “For the uninformed C-suite, cybersecurity spend is sometimes seen as an added expense rather than an essential business function that helps protect the company’s reputation and bottom line.”
She is concerned that this could happen during a period of increasing ransomware attacks. “These organizations may try to cut spending by decreasing their investment in cybersecurity tools or talent – effectively lowering their company’s ability to properly detect or prevent data breaches and opening them up to potentially disastrous outcomes.”
One approach, advocated by Bec McKeown, director of human science at Immersive Labs, is to treat remaining staff as human firewalls. “I believe that 2023 will be the year when enterprises recognize that they are only as secure and resilient as their people – not their technologies,” she says. “Only by supporting initiatives that prioritize well-being, learning and development, and regular crisis exercising can organizations better prepare for the future.”
Done correctly, she believes this can be achieved in a resource- and cost-effective manner. “Adopting a psychological approach to human-driven responses during a crisis – like a cybersecurity breach – will ensure that organizations fare far better in the long run.”
But perhaps the most dramatic response to ransomware will need to come from governments, although law enforcement agencies alone won’t cut it. LEAs may know the perpetrators but will not be able to prosecute criminals ‘protected’ by adversary nations. LEAs may be able to take down criminal infrastructures, but the gangs will simply move to new infrastructures. The effectively bullet-proof hosting provided by the Interplanetary File System (IPFS), for example, will increasingly be abused by cybercriminals.
The only thing that will stop ransomware/extortion will be the prevention of its profitability – if the criminals don’t make a profit, they’ll stop doing it and try something different. But it’s not that easy. At the close of 2022, following major incidents at Optus and Medibank, Australia is considering making ransom payments illegal – but the difficulties are already apparent.
As ransomware becomes more destructive, paying or not paying may become existential. This will encourage companies to deny attacks, which will leave the victims of stolen PII unknowingly at risk. And any sectors exempted from a ban will have a large target on their back.
While many foreign governments are known to be, or have been, considering a ban on ransom payments, this is unlikely to happen in the US. In a very partisan political era, the strength of the Republican party – with its philosophy of minimal government interference in business – will make it impossible.
Ultimately, beating ransomware will be down to individual organizations’ own cyber defenses – and this will be harder than ever in 2023. “There’s no letup in sight,” comments Sam Curry, CSO at Cybereason. “Ransomware continues to target all verticals and geographies, and new ransomware cartels are popping up all the time. The biggest frustration is that it is a soluble problem.”
He believes there are ways to stop the delivery of the malware, and there are ways to prevent its execution. “There are ways to prepare in peacetime and not panic in the moment, but most companies aren’t doing this. Saddest of all is the lack of preparation at the bottom of the pyramid in smaller businesses and below the security poverty line. Victims can’t pay to make the problem go away. When they do, they get hit repeatedly for having done so. The attackers know that the risk equation hasn’t changed between one attack and the next, nor have the defenses.”
Related: It Doesn’t Pay to Pay: Study Finds 80% of Ransomware Victims Attacked Again
Related: New Zealand Government Hit by Ransomware Attack on IT Provider
Related: Ransomware, Malware-as-a-Service Dominate Threat Landscape
The post Cyber Insights 2023: Ransomware appeared first on SecurityWeek.
About SecurityWeek Cyber Insights | At the end of 2022, SecurityWeek liaised with more than 300 cybersecurity experts from over 100 different organizations to gain insight into the security issues of today – and how these issues might evolve during 2023 and beyond. The result is more than a dozen features on subjects ranging from AI, quantum encryption, and attack surface management to venture capital, regulations, and criminal gangs.

SecurityWeek Cyber Insights 2023 | Regulations – In this world, nothing is certain but death, taxes, and cyber regulations. The first is static, the second goes up and down, but the third seems only to increase. The three primary drivers for cyber regulations are voter privacy, the economy, and national security – with the complication that the first is often in conflict with the second and third.
Privacy is the headline battleground going forward, and amply illustrates the conflict between voter demands and national economies. This can be seen in the unsettled but multi-year attempt to find a legal solution to the transfer of personal user data from Europe to the US. Economics demands it, but European law (GDPR) and swathes of European public opinion deny it.
At the time of writing, it is almost certainly illegal to transfer PII from Europe to the US. The Privacy Shield – the second attempt at finding a workaround to GDPR – was declared illegal in what is known as the Schrems II court ruling. The wording of that ruling almost certainly eliminates an alternative approach known as ‘standard contractual clauses’.
During 2022, the European Commission (EC) and the US Biden administration have worked on developing a replacement for Privacy Shield. The ball was obviously in the US court, and on October 7, 2022, Biden issued an Executive Order to implement the EU-US Data Privacy Framework agreement – sometimes known as Privacy Shield 2.0.
This was enthusiastically greeted by US business. IBM, for example, issued a statement, “These steps will restore certainty to the thousands of companies already self-certified under Privacy Shield. Providing predictable, free flows of data between the US and the EU will secure the mutual benefits of continued business cooperation and will create a foundation for future economic growth.”
Our first prediction for 2023 is that the EC will approve Biden’s Executive Order and allow ‘free flows of data between the US and the EU’. This approval is in process. The EC issued a draft adequacy determination for the EU-US data privacy framework on December 12, 2022.
“As expected,” comments Caitlin Fennessy, VP and chief knowledge officer at the International Association of Privacy Professionals (IAPP), “the draft outlines the Commission’s reasoning in finding the framework adequate, with a focus on the new necessity and proportionality requirements for US signals intelligence and the Data Protection Review Court outlined in the recent Executive Order and Department of Justice regulations.”
But that will be just the beginning. European activists, such as Max Schrems, are likely to challenge the EC ruling in the European Court.
The basic problem remains the NSA’s requirement to only surveil non-Americans (such as Europeans) for national security purposes. Schrems’ website, noyb, has already indicated a dissatisfaction. “So-called ‘bulk surveillance’ will continue under the new Executive Order (see Section 2 (c)(ii)) and any data sent to US providers will still end up in programs like PRISM or Upstream, despite of the CJEU declaring US surveillance laws and practices as not ‘proportionate’ (under the European understanding of the word) twice.”
So, during 2023, transatlantic PII data flows will become legal under the new framework, but that framework will be challenged as unconstitutional in the European Court. The court case will take several years to come to a conclusion, but it will probably declare the data privacy framework (or whatever it becomes known as) to be illegal. The basic problem is that GDPR and NSA surveillance are incompatible, and neither is likely to change.
The US government has been seeking a federal privacy law for around a decade but is probably no closer to achieving one. Progress was made during 2022, but the midterms kicked the bill into the long grass while the lawmakers concentrated on more pressing career issues. The question is whether it can be retrieved during 2023.
Mitzi Hill, a partner at the Taylor English Duma law firm, thinks it is unlikely. “I remain doubtful,” she said. “It is a complex topic both technically and legally. It is made more complicated with every new state law, because that is a new set of factors to consider in drafting any federal legislation.”
She also notes the outcome of the 2022 midterms. “Traditionally, we would expect that a Republican House majority [as we will have in 2023] will favor marketplace (as opposed to regulatory) solutions, making it tough to get anything passed in both houses of Congress. My own view is that the states will continue to lead in this area.”
Gopi Ramamoorthy, senior director of security and GRC at Symmetry Systems points out that “Five states have already enacted privacy acts, and more are expected to follow. The increased focus on privacy has stemmed from the introduction of GDPR and Schrems II decision from the EU.”
The California Privacy Rights Act (CPRA) comes into effect on January 1, 2023, with enforcement beginning on July 1, 2023. It is an extension of the existing CCPA, which is already possibly the strongest privacy act in the US (and largely modeled on GDPR). While it is somewhat more friendly to small businesses, it gives consumers more rights, places more requirements on organizations, and establishes an enforcement agency.
The consumer demand for privacy is strong, but not absolute – and often depends on what is received in return for giving up personal information. Consider Google, widely acknowledged as one of the primary collectors and users of PII. Despite this, consumers continue to consume Google because of the ‘free’ services the company offers in exchange. The result is that it is difficult for lawmakers to know exactly what their voters really want.
“Privacy laws and regulations will continue to swing widely between completely useless – even harmful – and amazing wins for consumers. This is due to corporation lobbying and consumer [voter] demands,” comments Taylor Gulley, senior application security consultant at nVisium. “Though most consumers desire complete privacy, the growing demand for personalized content and services requires providing ever more information to companies. This increase of valuable, marketable, information gives corporations a reason to continue to lobby for their benefit.”
One area worth watching in 2023 is whether the FTC picks up the mantle of a ‘federal’ privacy regulator. Noticeably, the FTC includes failures in consumer privacy to be a potential deceptive practice – and deceptive practices are firmly within the FTC bailiwick.
“The FTC may become even bolder about privacy matters in the next couple of years,” suggests Hill. “It recently adopted an enforcement action that is targeted to a particular CEO and any future business he may join.”
She explained that his current company has multiple privacy violations and may have misstated the degree to which it addressed security issues following the first set of violations. His future companies or employers will be required to release detailed security plans. “This is unprecedented as far as I know,” she added.
Although Biden does not believe in trickle-down economics, he nevertheless makes use of trickle-down cybersecurity. He cannot pass federal laws for private industry without the support of Congress – but he can (and does) issue executive orders that become mandatory instructions for federal agencies and strong trickle-down recommendations for private industry.
If security vendors must conform to certain requirements before they can sell into the government, the size of the government market makes it a commercial if not legal requirement to conform. Furthermore, if federal agencies are required to apply certain cybersecurity methodologies, much of private industry will also take heed.
Both conditions were introduced in May 2021 with Executive Order 14208, spurring activity in zero trust, and introducing the software bill of materials (SBOM). Both are intended to counter the growing supply chain threat, and both will remain top of mind for companies during 2023.
“SBOM is going to continue to garner mainstream adoption, not just from software/firmware suppliers that are building products they are selling, but also for internal development teams that are building applications and systems for internal use,” comments Tom Pace, CEO at NetRise.
The federal government described the requirements for SBOMs in an OMB memorandum published on September 14, 2022. “This is going to cause a cascading effect in the private sector,” continued Pace, “since obviously the federal government does not manufacture all its own software and firmware – in fact very little is manufactured in house.”
There will be a bedding-in period before SBOMs achieve their end – and attackers are likely to increase their own efforts in the meantime. “Highly visible attacks on the software supply chain start with access to the weakest link. As we head into 2023, it will be important for businesses of all sizes to be engaged as new secure software development practices are defined,” warns John McClurg, SVP and CISO at BlackBerry.
Executive Orders are not the only tools the federal government can use – it also has NIST (a standards body) and CISA (a DHS agency responsible for strengthening security and infrastructure across all levels of government). While they primarily provide recommendations, this may not always be the case.
“The combined efforts of CISA and NIST in recent years,” comments Eric Hart, manager of subscription services at LogRhythm, “have led to a series of new cross-sector cybersecurity performance goals (CPGs) that organizations have already begun to implement.”
CISA’s CPGs are designed to provide an easier route towards conforming to NIST for organizations that may not have the resources to go straight to the complexities of the NIST CSF. “While these standards are designed to strengthen organizations,” continued Hart, “the process of reaching full regulatory compliance can be tricky. The complexity, along with the growing push for federally enforced compliance, suggests we could see a flurry of activity in 2023 as more organizations seek to adopt these new security standards.”
Noticeably, CISA describes the CPGs as ‘voluntary’ and ‘not comprehensive’, adding, “The CPGs are intended to supplement the [NIST] Cybersecurity Framework (CSF) for organizations seeking assistance in prioritizing investment toward a limited number of high-impact security outcomes, whether due to gaps in expertise, resources, or capabilities or to enable focused improvements across suppliers, vendors, business partners, or customers.”
But it is also worth considering a comment from Grant Geyer, CPO at Claroty, who blogged that they may prove a jumping off point for upcoming regulations coming from the White House. “Regulators now have a CISA-approved, pre-built checklist of critical areas to focus on that address key practices such as account security, data and device integrity, supply chain and third-party risk, and response and recovery.” We may yet see CISA’s CPGs become mandated for federal agencies and join the trickle-down process of federal regulations.
Ben Johnson, CTO and co-founder of Obsidian Security, sees a great future for CISA. “CISA came into its own in 2022. This next year, we’ll see CISA drive better, more resilient security, especially in critical infrastructure — increasing the sector’s maturity as a whole.”
The trajectory for regulations is to increase, and they are increasing rapidly. These include state-level, federal level, and overseas national level that may impact US companies with operations in those countries. An example of the last could be Australia’s current plans for a new more aggressive attitude toward cybercriminals. Part of this will be to make ransom payments illegal in Australia.
One question to be decided is how that might impact American companies with an Australian operation that gets ransomed. Will the American parent, where ransom payments are not illegal, be able to pay the ransom on behalf of the Australian operation?
Such complexities will require expert input by companies to match their infrastructure and processes against a huge number of regulations simply to understand where their compliance requirements are effectively mandatory.
Another new law, passed by Congress but targeted at federal agencies, may be introduced early in 2023: the Strengthening Agency Management and Oversight of Software Assets Act. MeriTalk reported on November 17, 2022, “The legislation would order Federal government agencies to undertake an inventory of all software used by the government – with a view toward eventually creating strategies to consolidate government software contracts, create governmentwide software licenses, and move toward adopting open-source software.”
This is not directly a cybersecurity regulation and will not be enforced on private industry. Nevertheless, if its precepts are adopted by industry, it could benefit industry groupings and separately lead to a beneficial reduction of security tool sprawl within companies.
The totality of regulations is beyond the scope of this peek into regulations in 2023. However, there is one we should consider that won’t come into effect until 2024.: PCI DSS 4.0. This will impact all organizations that store, transmit or process cardholder data and sensitive authentication data. The new standard allows organizations to customize their approach to proving compliance with each PCI DSS security requirement.
“If organizations take this direction,” warns Terry Olaes, senior technical director at Skybox Security, “there are growing opportunities for threat actors to exploit retailers who may have taken non-standard routes to achieve compliance. Additionally, the long lead time to implement these regulations gives attackers more opportunity to use those requirements as a blueprint to breach retailers before they have time to implement changes to their cybersecurity strategy.”
It is also worth noting that while regulations are becoming more numerous, they are also becoming more difficult to satisfy. “We’ll see more failed audits in regulated companies as multi-cloud, multi-cluster grows as a strategy in 2023,” warns Sitaram Iyer, senior director of cloud native solutions at Venafi. This strategy is increasingly popular among smaller but regulated organizations because it spreads risk, increases performance, and offers the control and visibility they need for compliance.
“However,” adds Iyer, “it also increases complexity because these environments are fragmented and require a huge number of machines which all need an authenticated identity to communicate securely. Due to this increased volume of machine identities in cloud native environments, compliance with regulations on machine identity management is a real challenge.”
Elon Musk has completed his takeover of Twitter, and his swashbuckling management style has caused ructions even before the end of 2022. These are not relevant to us. What may be relevant, however, is his adherence to the constitutionally protected concept of free speech; and the potential for Musk’s new Twitter to operate at a lower level of moderation than the old Twitter. Noticeably, in late November 2022, Musk reinstated almost all the accounts that had previously been suspended for spreading misinformation.
As a quick aside, on November 17, 2022, a group of Democrat senators asked the FTC to investigate any possible violations by the platform of consumer-protection laws or of its data-security commitments. The FTC had already said it is “tracking recent developments at Twitter with deep concern”.
Of more direct relevance, many governments have already expressed concern over the practice of bad actors spreading misinformation, malinformation and disinformation – and giving extremist viewpoints a loudspeaker – via social media platforms such as Twitter. This is a direct challenge to democratic government, and some governments have suggested countering it by making websites legally responsible for the user-generated content they publish. There is a possibility that such suggestions will increase during 2023.
Mitzi Hill does not think this is likely in the US. Although lower moderation might lead to howls of protest, “I never bet against the First Amendment,” she said. “‘Congress shall make no law… abridging the freedom of speech’ is one of the most important tenets in American legal thinking.”
Europe, however, thinks differently. The EU already has a new Digital Services Act that will kick in from January 2024. It doesn’t make platforms directly responsible for any unknown illegal content, but does require them to remove it once they are informed that it is illegal. It will also impose greater transparency on how algorithms work and are used. It is aimed at platforms that reach more than 10% of the EU population; that is, have at least 45 million EU users – that includes US big tech companies such as Twitter and Facebook. Non-compliance could lead to fines of up to 10% of annual turnover.
Martin Zinaich, CISO at the City of Tampa, once suggested to SecurityWeek, “If it ain’t required, it ain’t gonna happen.” We may have reached the point, with better organized cybercriminals and more aggressive nation states, where it must happen and therefore must be required.
Ron Kuriscak, MD at NetSPI, certainly believes so. “Regulations need to become much more mature, stringent, and punitive. We must hold organizations more accountable for their inaction in the area of cybersecurity… Organizations will be held accountable for basic cybersecurity hygiene. If they are unable to meet the most basic standards a regulator will require a third party to take over cybersecurity program execution (they will be mandated to cover the associated costs). Similar to the FDA, we will start seeing industry-aligned compliance regulations with real penalties that will force real compliance and organizational change. The key will be enforcement and penalties.”
But don’t expect much from the federal government in 2023. “On federal government cybersecurity issues,” explains Robert DuPree, manager of government affairs at Telos Corporation, “Congress has been more active and effective but further progress in 2023 will be hampered by the fact that some longtime cyber policy advocates and experts from both parties – including Sen. Rob Portman (R-OH), Rep. Jim Langevin (D-RI) and Rep. John Katko (R-NY) – are retiring and won’t be around in 2023. Their absence will leave a tremendous void when it comes to pushing ‘good government’ cybersecurity issues through Congress.”
Related: Do Privacy and Data Protection Regulations Create as Many Problems as They Solve?
Related: Robinhood Crypto Penalized $30M for Violating Cybersecurity Regulations
Related: Hack Prompts New Security Regulations for US Pipelines
Related: New York Imposes New Cybersecurity Regulation for Financial Services
The post Cyber Insights 2023 | Regulations appeared first on SecurityWeek.
Recently, a friend brought up the term “carcinization” and I must admit, I had to look it up! Turns out the term was coined more than 100 years ago to describe the phenomenon of crustaceans evolving into crab-shaped forms. Today, there are even memes for it. So, what does this example of convergent evolution have to do with security? It’s an apt description of how the security industry has evolved and why security leaders often struggle to determine the right security investments for their organization.
The security industry started out with a series of point products to solve very specific challenges. Organizations used endpoint antivirus, firewalls, IPS/IDS, and routers to protect themselves. Email and web security tools were soon added, along with SIEMs and other tools like ticketing systems, log management repositories and case management systems to house internal threat and event data. Endpoint detection and response (EDR) tools then came into the mix and a few years later served as the jumping off point for the next phase in the industry’s evolution. That’s when the traditional walls between endpoint and network security technologies began to crumble and product categories were no longer clearly defined.
Everything starts to look alike
When the concept of extended detection and response (XDR) was introduced a couple of years ago, industry analysts each seemed to have slightly different, but colliding, definitions of it. Some said XDR is EDR+ (with different opinions as to what the + consisted of) while others said XDR isn’t a solution at all, but an approach or an architecture. Those conversations continue today.
Now the industry is talking about threat detection, investigation and response (TDIR) platforms and depending on who you ask about the difference with XDR, you’ll get a different answer. Some say XDR is an overarching architecture and TDIR is the platform that integrates all the capabilities required for XDR. Others say TDIR is a process. And another contingent says they are one and the same.
The varied viewpoints as related security concepts take on similar traits create substantial confusion among security teams trying to evaluate and purchase security technologies to strengthen their organization’s security posture. At a time when the market should be maturing and moving security to a better place, these discrepancies prevent that from happening.
Use cases, not labels
So, how can security teams cut through the noise and confusion? In the carcinization of security, where everything starts to look and sound alike, it’s critical to focus first on use cases. To do this, start with what you are trying to accomplish, the associated workflows, and the people, processes, and technology required. From there, you can look at where the gaps exist and where to invest to achieve your goals.
Sometimes you may need a specific technology for a specific use case. Or, ideally, you find a platform that can handle multiple use cases security professionals are focused on today as security operations centers (SOCs) mature. These include spear phishing, threat hunting, alert triage, vulnerability prioritization and incident response.
For each of these use cases, context is critical to understand the who, what, where, when, why and how of an attack. With a security operations platform that can aggregate and correlate internal threat and event data with external data on indicators, adversaries and their methods, you can analyze multisource data and understand relevance to your environment based on parameters you set. Once you have the right data and context, you can pivot around a specific piece of data to understand and act. You can parse and analyze spear phish emails for prevention and response, prioritize alerts for triage, identify vulnerabilities to patch first, and accelerate threat hunting. Integration with the right tools allows you to send data back out across your defense grid to accelerate incident response, including blocking threats, updating policies and arming the organization against the next wave of attacks.
The truth is, the walls established to separate product categories should have been challenged sooner for the benefit of security. Organizations considering the latest acronym or spurred by the latest attack may have selected a different, more effective tool or platform depending on their goals, internal resources and capabilities. When everything starts to look like a crab and walk like a crab, we can’t rely on labels. We need to look at use cases, desired outcomes and the best path to get us there.
The post Dealing With the Carcinization of Security appeared first on SecurityWeek.
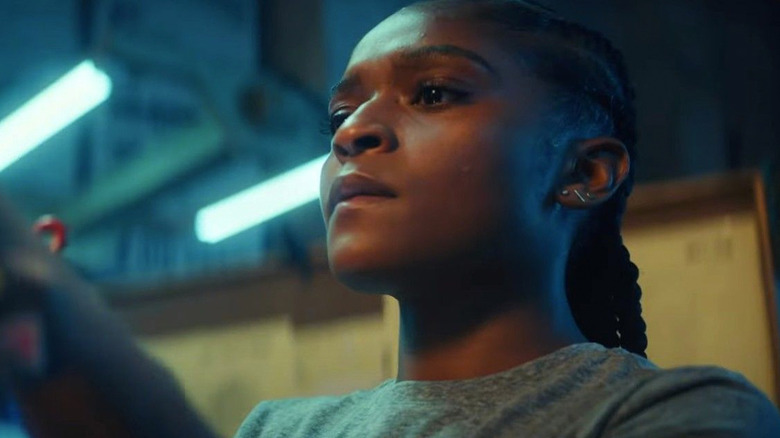
One of the bigger missed opportunities within Marvel's Cinematic Universe might lie in its introduction of Riri Williams, aka Ironheart. Riri was folded into the Marvel Comics canon in 2016 as Iron Man's legacy counterpart. As Riri grew on the pages of the comics, she amassed quite the following, validating Black female comic lovers -- and aspiring Black women in STEM -- with each new adventure. She was a fascinating foil to Tony Stark's privilege and snark, and a lot of fans hoped to see their dynamic eventually play out on the big screen. But the MCU went a different way, with Robert Downey Jr.'s Iron Man mentoring an all-new Spider-Man (played by Tom Holland) before ultimately meeting his demise in "Avengers: Endgame."
By the time Riri was finally introduced in "Black Panther: Wakanda Forever," Iron Man was long gone. His legacy still lives on in Riri — after all, his Stark Industries tech does power her own familiar armor. And there's a chance that his influence will bleed into Riri's upcoming solo series. But even if we never get to see these two characters sharing a screen, it's comforting to know that Dominique Thorne — who plays Riri in "Wakanda Forever" and will soon continue the role in "Ironheart" — has actually gotten some roundabout wisdom from Iron Man himself.

Thorne spoke to The Direct about her fateful meeting with the Iron Man actor, who connected with her before she wrapped shooting on the upcoming "Ironheart" TV series:
"He and I didn't really have much chance to connect prior to, but maybe that worked out pretty well, because the first thing he said in our conversation, or toward the end of the conversation, was that he didn't have any advice for me. And he felt like I was actually pretty okay, and that I'd be all right."
Downey Jr. seemed concerned with making sure that Riri remained "her own person," especially given her connection to a hero that has already come and gone in the MCU. He and Thorne also spoke about "all of the things that I can obviously attribute to her existence, and what it means, and what it represents, and what it can offer... Really just in the vein of being authentic to that, and true to that, and nurturing that."
The "second half" of Thorne's conversation with Downey Jr. is one that the actress is keen to keep "near and dear" to her heart. "He definitely gave me a piece ... some words of encouragement ... as I continue to navigate all that this life could be, which I appreciate." Given that Iron Man was essentially the hero that started it all, there's no doubt that Downey Jr. has some great nuggets of wisdom for the young actors following in his footsteps. It's great to know that, even if he couldn't coach Thorne through her first big headliner, that she didn't really need too much help in that department.
Read this next: The Most Brutal Moments In The MCU Ranked
The post Robert Downey, Jr. Had Some Pretty Good Non-Advice for Ironheart's Dominique Thorne appeared first on /Film.

Welcome to The Daily Stream, an ongoing series in which the /Film team shares what they've been watching, why it's worth checking out, and where you can stream it.
The Movie: "Much Ado About Nothing" (1993)
Where You Can Stream It: HBO Max, DirecTV
The Pitch: Kenneth Branagh's film adaptation of William Shakespeare's "Henry V," the filmmaker's first feature, was a massive success when it was released in 1989. Branagh was nominated for Best Actor and Best Director, and Phyllis Dalton won the Oscar for Best Costumes. The film caused a great deal of buzz around Branagh, and audiences kept a close eye on him. In 1989, he married actress Emma Thompson (who played Katherine in "Henry V"), and the two of them would proceed to work together incredibly well on several notable films. Thompson co-starred with Branagh in the excellent reincarnation thriller "Dead Again" in 1991, and she appeared as the repressed Maggie in the thirtysomethings-reconsider-life drama "Peter's Friends."
With the release of "Much Ado About Nothing" in 1993, however, the pair reached a dizzying height. Based on Shakespeare's frothiest, most lighthearted play, "Much Ado" saw Thompson and Branagh playing the irresistible, bickersome couple of Beatrice and Benedick, and their chemistry cannot be measured by conventional instruments. It's rare that audiences are treated to such a pure distillation of randy, Shakespearean joy. "Much Ado" is a blast of relaxed, horny energy. The cast and filmmaking feel so warm, natural, and comfortable, it almost feels like audiences are watching the cast party after a typical Shakespearean production.

For those who didn't read "Much Ado About Nothing" in high school, the setup is pretty simple, as far as Shakespearean comedies go. The war has ended, and the soldiers are returning home to stay in a gorgeous countryside villa in Messina. Don Pedro (Denzel Washington) is finally relieved to be back home, the soldiers are ready to open their shirts and party, and the local villa-dwellers are only too happy to join in the celebration. The young Claudio (Robert Sean Leonard), upon seeing the equally young Hero (Kate Beckinsale), instantly falls in love and pleas with his buddies to fix them up. The return also sees the reunion of Beatrice and Benedick, a pair of ex-lovers who constantly fight and insult one another, but who are clearly in love and destined to marry.
Much of "Much Ado" is devoted to laughter and jubilance. An early montage shows people getting ready to greet the incoming soldiers, as they have pillow fights, giggle, and spray perfume down their shirts. Later, the men chuckle heartily as they undress for a communal bath. Everyone was already blissfully horny eating picnic lunches and drinking wine in the Italian sunshine. Now they get to add romantic conquest to their games. Life is good.
Lurking at the edges is the dour Don John, played by Keanu Reeves, the only actor who does not quite avail himself well in "Much Ado." Reeves is appealing as a movie star and is, by all accounts, a relentlessly decent person, but he is well out of his depths reading Shakespeare. There's a reason his acting was lampooned so often. Don John is the killjoy who resents everyone's happiness/horniness and aims to undo it all by actively ruining the potential relationship between Claudio and Hero.

Don John's plan involves making Claudio think that Hero has been unfaithful, forcing him to reject Hero in public. For a fleeting moment, everyone is unhappy. Don John flees and spends most of the film off-screen. He's also barely in the play.
In terms of traditional romantic comedy conventions, the eventual relationship and subsequent marriage of Claudio and Hero should be the very crux of the play. And while Claudio and Hero are appealing, attractive young lovers, they are not the reason we have come here. We have come to see the eventual breakdown of Beatrice and Benedick. We have come to see two very funny, very intelligent people -- so obviously perfect for each other -- swallow their pride and admit their love. An extended (hilarious) sequence sees Pedro, Claudio, and Leonato (Richard Briers) standing within earshot of Benedick, telling lies about how Beatrice is secretly in love with him. The sequence is then repeated for Beatrice. Old love letters are planted where they can be found, and Beatrice and Benedick each have to talk themselves into being the marrying type.
If that wasn't silly enough for you, Branagh also included Shakespeare's clown in the form of Dogberry, the local police officer. In a world where everyone is calm and happy, crime is sparse and Dogberry (Michael Keaton) and his deputies are ineffectual drunks. Keaton overacts with the best of them, grunting and flatulating with aplomb. The film is already joyous and funny and fun, but Dogberry tips the proceedings into outright hilarity.

There may be a temptation when staging Shakespeare to unintentionally push one's actors toward oratory and recitation. As Shakespeare's language is so poetic and gorgeous, one might want to make sure that every syllable is heard, every moment of poetic rhythm communicated. Branagh understands that the poetry will exist regardless, and -- throughout his various Shakespearean projects -- has encouraged his actors to speak in their own voices. Washington, Reeves, Keaton, and Leonard -- the film's Americans -- do not affect English accents, and speak their lines with a casual ease rarely heard with the Bard. What emerges from this approach is clarity. The characters become clearer, the relationships become clearer, the jokes become clearer, and the plot is laid bare and simple.
For any youths struggling with Shakespeare, "Much Ado" will be a salve. It reveals that Shakespeare is not only easy but natural. The dialogue in "Much Ado" feels like witty people saying scintillating things in a clever way. Every actor is comfortable with the language and seems relieved to be speaking such gorgeous lines. It is the opposite of dry recitation.
"Much Ado" was arguably the high point of the Branagh/Thompson collaborations. The two divorced in 1995, and each continued to make interesting, sometimes amazing films. Branagh would make a full-scale version of "Hamlet" in 1996, one of the best Shakespeare films ever, and Thompson would win an Academy Award for writing an adaptation of Jane Austen's "Sense and Sensibility" in 1995. They would also both eventually dip into blockbusters, and they would both appear in "Harry Potter" films. By curious coincidence, they each remarried in 2003.
Read this next: The 15 Best Historical Romance Movies Ranked
The post The Daily Stream: Kenneth Branagh's Much Ado About Nothing is Everything appeared first on /Film.