The two "Exorcist" prequels, "Exorcist: The Beginning" and "Dominion: Prequel to the Exorcist," offer something that may be unique in the whole of cinema; a strange case of one actor playing the same character in two different versions of the same film shot back-to-back. Oh, and the first version was only released after the second proved a total dog. It's a story of epic studio interference that makes the tacked-on ending William Peter Blatty was forced to shoot for "The Exorcist III" seem like a minor tweak. Morgan Creek studio head James G. Robinson was the person responsible for that change, and he one-upped himself when it came to the prequel.
After two directors parted company with the project, he hired Paul Schrader. That might seem like a shrewd choice given the subject matter of doubting priests and matters of the soul, something that Schrader has wrestled with in his screenplays and directorial works throughout his career. Problems arose when Schrader went ahead and made a Paul Schrader film, which Robinson felt wasn't scary or gory enough.
Apparently deciding that his "Exorcist" prequel needed to be more like "The Mummy" movies, he fired Schrader and hired Renny Harlin to jack things up a bit. It wasn't just a case of re-jigging existing material and shooting a few new scenes: Harlin was given another hefty budget on top of the money Schrader had already spent (via Today), re-writing the script, re-casting most of the actors, and re-shooting the entire film.
The result is a hokey CGI-stuffed horror film totally at odds with the original "Exorcist" trilogy, although a side-by-side comparison of the two prequels will provide a treasure trove for film studies tutors who want to demonstrate just how much a director brings to a project. So let's get into the first one ... or should I say, the second?
The Set Up

"Exorcist: The Beginning" opens in the Middle Ages with a bloodied priest staggering through the carnage of a terrible battle. He finds the body of another priest holding the head of a Pazuzu statuette in his lifeless hand, and the camera swoops out to reveal thousands of men crucified upside down.
Next, we're in Cairo in 1949, where Father Lankester Merrin (Stellan Skarsgård) is drinking away his sorrows, having lost faith after his experiences during the Second World War. He is approached by a shady dealer in antiquities called Semelier (Ben Cross) who asks him to find a demonic artifact buried in a Byzantine Christian church in Kenya. The church shouldn't exist in that location because it dates from before Christianity reached that part of Africa.
On his arrival at the site in the Derati valley, Merrin meets loathsome head excavator, Jefferies (Alan Ford); a kindly doctor, Sarah Novak (Izabella Scorupco); Father Francis (James D'Arcy), a younger priest sent by the Vatican, and Major Granville (Julian Wadham), the British officer overseeing the dig. Merrin learns that the superstitious workmen from the local Turkana tribe won't enter for fear of evil spirits.
Gaining access to the church, Merrin and Francis discover some unsettling features. The weapons held by the statuary point downwards rather than heavenwards, and the effigy of Christ on the Cross has been vandalized and inverted. Meanwhile, sinister events unfold in the camp and nearby tribal village. The lead archaeologist Bession (Patrick O'Kane) has been carted away to a sanatorium in Nairobi after being plagued by demonic visions. When Merrin visits him, the man carves a swastika on his chest with a piece of glass and speaks in a voice that takes the former priest back to the event that caused his crisis of faith.
Father Merrin's Loss Of Faith

"Exorcist: The Beginning" gives us a series of flashbacks that gradually reveal why Father Merrin lost his faith. During the Second World War, he was the priest in a small Dutch town under Nazi occupation. When a German soldier was killed, the local SS Commander demanded a summary execution; after shooting a young girl to make Merrin and the townsfolk realize he means business, he forced the priest to pick ten people to die, otherwise, the whole town would be massacred. Merrin was left with no choice but to point out members of his flock to be shot, starting with elderly men.
"God is not here today," the SS man taunted Merrin, and these same words emerge from the lips of Bession before he slashes his own throat. Father Gionotti (David Bradley), an elderly priest who works at the sanatorium, suggests that Bession wasn't fully possessed but was "touched" by a demon, causing him to have a psychotic breakdown and take his own life. He gives Merrin a copy of the Roman Ritual, the 1614 rites that are used to perform an exorcism. Merrin vows he will never use them.
Back in the Derati valley, a young boy called Joseph (Remy Sweeney) also seems touched, falling into a catatonic state after his brother is ripped to shreds by some incredibly unconvincing CGI hyenas. In the nearby tribal village, the chief's wife gives birth to a stillborn baby covered in maggots, while Jefferies disappears after he is brutally attacked in a bar. Sarah, who has mysteriously begun hemorrhaging blood, tries convincing Merrin that it is all down to a curse. Merrin is still having none of it, stating evil comes from man and not some supernatural entity.
The Terrible History Of The Derati Valley

Tensions are rising between the Turkana and the British; the tribe blames evil coming from the church for the death of the chief's child while the Brits suspect Jefferies was attacked in revenge.
Merrin investigates the church further and discovers a tunnel leading underground to a statue of our old pal Pazuzu, the demon that plagues the protagonists in the original "Exorcist" trilogy. He is also intrigued by a Christian graveyard nearby, supposedly the resting place of villagers who died during a plague 50 years earlier, and decides to excavate a few graves to find out for himself. Meanwhile, tribesmen take the exorcism of Joseph into their own hands and get violently attacked by a demonic force.
Merrin discovers that the graves are empty and confronts Father Francis about it, who tells him the terrible backstory of the Derati valley. 1500 years before, a vast army led by two priests arrived in the area seeking the source of a great evil. The demonic presence lurking in the valley turned the men against each other and only one priest survived. Emperor Justinian of the Byzantine empire ordered a church built over the site to contain the evil below.
All records were meant to be destroyed but, in 1873, a Vatican researcher found a letter referring to the church. Four more priests were dispatched to Kenya to investigate, enlisting the local tribe to help them. Everyone involved disappeared and the Vatican cooked up a cover story, burying empty coffins and keeping people away with rumors of the plague. Father Francis also reveals his true purpose on the dig; he is there to investigate the legend that it is the place where Lucifer fell to earth after the war in Heaven.
The Twist Ending

The animosity between the Turkana tribe and the British troops escalates. After the horribly mutilated body of Jefferies is found strung up in the church, Major Granville takes revenge by executing a tribesman. Merrin's guide, Chuma (Andrew French), tells him that the tribe believes the evil force is inside Joseph and plans to kill him.
As the British soldiers ready themselves to repel an attack from the tribe, Major Granville shoots himself in the head. Merrin wants to send Father Francis and Joseph to safety in Nairobi, but the CGI sandstorm from "The Mummy" makes an appearance to trap them. Francis suggests taking the boy to the church because the Turkana won't enter; Merrin gives him the copy of the Roman Ritual and heads off to find Sarah.
Merrin makes a shocking discovery in Sarah's room: it is swarming with flies and she has daubed demonic symbols and imagery over the walls in blood. Merrin finds the statuette head of Pazuzu above her bed, the very item he has been hired to find. When he spots a wedding photo revealing that Sarah was married to Bession, he deduces that she also entered the church and became possessed.
This realization comes too late: possessed Sarah sneaks up behind Father Francis in the church and kills him. With things looking bleak, Merrin decides to give God another shot. He enlists Joseph's help to read the rites and vanquish the demon inside Sarah, but she dies shortly afterward. Merrin and the kid emerge from the church to find it has been buried again by the sandstorm and history has repeated itself; the tribal warriors and the British troops lay dead all around.
Sometime later in Rome, Merrin is a priest again. He meets Semelier to say he was unable to find the demonic trinket and heads off toward the Vatican.
Is Exorcist: The Beginning As Bad As You've Heard?

For those who care about what Rotten Tomatoes says, "Exorcist: The Beginning" is currently tying with "Exorcist II: The Heretic" with a Tomatometer score of 10%, although the latter's audience rating is far worse. This may be because John Boorman's widely-hated film has had four decades of people dunking on it to increase its reputation as one of the worst sequels ever made. Renny Harlin's prequel certainly isn't the berserk shock to the system that Boorman's movie provides, but it is a tedious piece of hackery that suggests not a single original thought ever passed through the director's head.
It's a complete mishandling of the "Exorcist" series typified by cheap jump scares, unnecessary gore, and Alan Ford's cartoonish performance as Jefferies who, from this evidence, was asked to play his character exactly like his gangster Bricktop in "Snatch." It also isn't scary at all, beyond the jolt you get when you have a movie shouting "Boo!" in your face every few minutes. There is none of the original's pervading atmosphere of timeless evil, which was summed up by the hushed but dread-laden moment when Father Merrin faces the statue of Pazuzu across a windswept gully. Harlin quotes this moment, but there is no sense that he appreciates what it means; it feels like fan service without any comprehension of what fans of the original actually love about the first movie.
All that said, "Exorcist: The Beginning" isn't anywhere near as unwatchable as its poor reputation suggests. A large part of that comes down to Stellan Skarsgård, who pulls off the quietly extraordinary feat of carrying a movie as shallow as this with a nuanced performance that deserves far better.
Exorcist: The Beginning Ending Explained

The finale of "Exorcist: The Beginning" perhaps doesn't need much explaining. It's pretty much all there on the screen, a story of a doubting priest who rediscovers his faith just in time to perform the requisite exorcism that the brand demands. It is perhaps more interesting to discuss how it plays out in the context of the original trilogy, particularly William Friedkin's first film.
Renny Harlin's hack job broadly hits the main beats, especially the theme of recurrent age-old evil. You also have Father Merrin's crisis of faith which somewhat mirrors that of Father Karras (Jason Miller) in the original. Unfortunately, Harlin only pays lip service to these ideas while ladling on the cheap scares and nasty gore, resulting in a film that is almost totally devoid of the philosophical and theological underpinnings that made "The Exorcist" so powerful. For all the original film's show-stopping scenes of demonic possession, screenwriter William Peter Blatty was very serious about exploring a battle between good and evil, and Friedkin's quasi-documentary approach added to its chilling believability.
Paul Schrader's prequel (which I'll cover in greater detail in the next explainer article) also treats the nature of evil with the utmost sincerity, but only the barest vestige of his efforts remains in the Renny Harlin version. The jarring disconnect is further tainted by making the possessed person in need of an exorcism Merrin's tacked-on love interest; he and Sarah have a kiss and cuddle earlier in the movie. This stands at odds with the selfless love and integrity of Merrin and Karras in the first film, who sacrifice themselves to save an innocent from evil without any reassurance that God has their backs. This fundamental misunderstanding, or sheer lack of interest, in what made the first film so captivating reduces "Exorcist: The Beginning" to a strictly by-the-numbers origin story for Father Merrin.
Read this next: 14 Horror Movie Flops That Became Cult Classics
The post Exorcist: The Beginning Ending Explained: The Spot Where Lucifer Fell appeared first on /Film.





















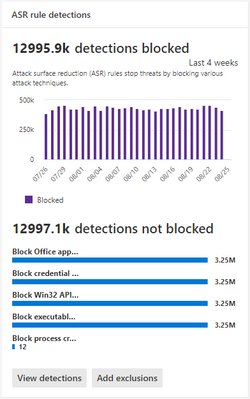
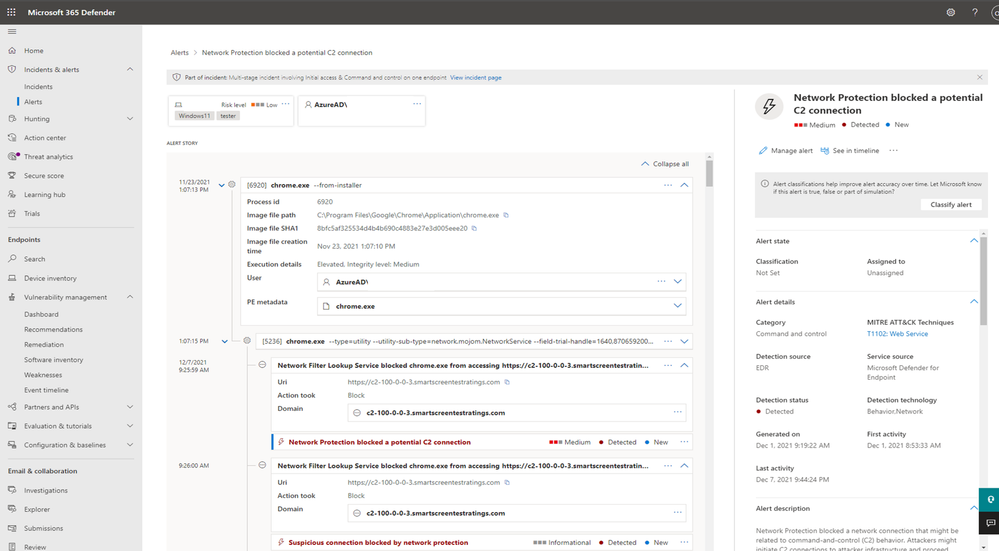
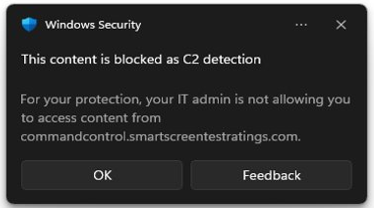
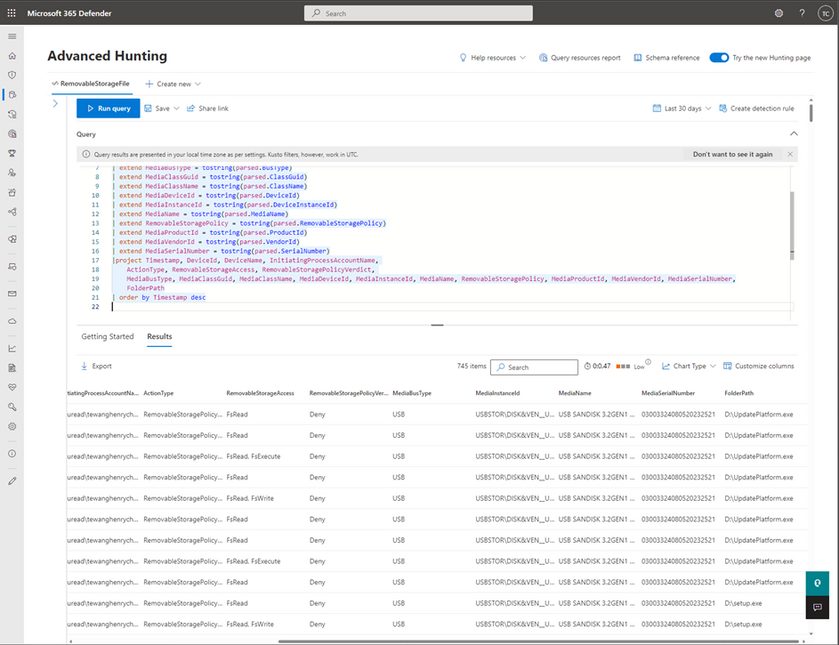
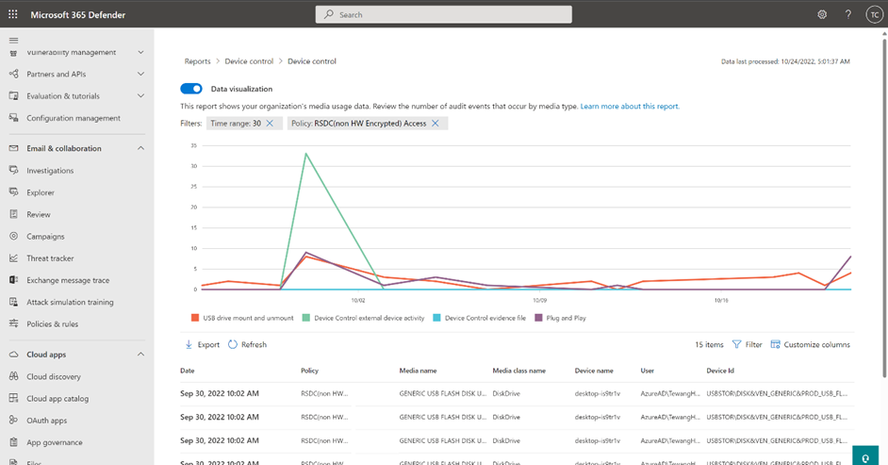
 Figure 1: The following screenshot demonstrates querying for Tampering events via advanced hunting
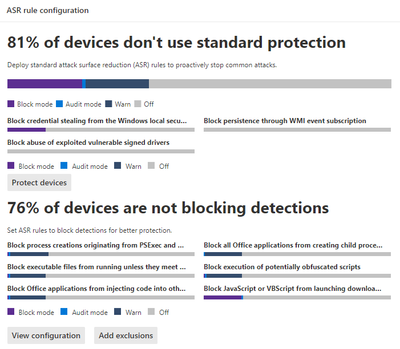
Figure 1: The following screenshot demonstrates querying for Tampering events via advanced hunting