Ronald.phillips
Shared posts
Linux 6.7 Will Let You Enable/Disable 32-bit Programs Support At Boot-Time
Ten Days Before The Twilight Zone Premiered, Mike Wallace Asked Rod Serling A Question That Aged Badly

The Invincible Review – Exploring the Unknown
What makes us ourselves? What awaits us in the vast confines of space? Are the hidden mysteries meant for us to be found? These questions are all tackled by the game The Invincible (not to be mistaken with the series of the same name). This game, based on a popular Polish sci-fi novel written by Stanisław Lem, puts us in the role of a space traveler who discovers a secret that probably shouldn't have been discovered to begin with. The game is essentially a walking simulator. As such, you are going to have to keep that in mind when unpacking […]
Read full article at https://wccftech.com/review/the-invincible-exploring-the-unknown/
From classroom to cyberfront: Unlocking the potential of the next generation of cyber defenders
In a world where the digital frontier is expanding and cyberattacks are becoming more sophisticated with speed and scale, the guardians of our virtual realms have never been in greater demand.1 It’s important to leverage this year’s Cybersecurity Awareness Month to celebrate the people who keep us safe and to raise visibility on the need for education and awareness—for everyone. With a staggering 3.4 million unfilled cybersecurity jobs, almost 70 percent of organizations report not having enough cybersecurity staff to be effective.2
And security leaders are sounding the alarm as they want to keep cybersecurity professionals equipped with the right resources to avoid burn out. Yet, this isn’t merely about technical prowess. The ideal cybersecurity workforce harmoniously merges technical expertise with invaluable soft skills. While cutting-edge technology offers part of the remedy, the heart of our defense lies in human expertise—the minds that craft strategies, wielding these tools to ward off potential cyberthreats. The gap in cybersecurity talent is a collective concern, and Microsoft is eager to support the mission to bridge this gap through educational programs that include diversity, providing guidance to security professionals and their organizations on how to be cybersmart and generative AI technology to augment the talent that prevails.

Be Cybersmart
Help educate everyone in your organization with cybersecurity awareness resources and training curated by the security experts at Microsoft.
Debunking myths about cybersecurity careers
There are still a lot of misconceptions about what is required to be a successful professional in this industry.
Common fallacies that may hold people back from exploring cybersecurity careers include that only science, technology, engineering, and mathematics graduates—or college graduates in general—can get cybersecurity jobs. The industry is growing more inclusively and attracting a broader range of people, including professionals outside IT. In fact, half of employees younger than 30 join the industry with a non-IT background.3 To take on cybersecurity challenges, security teams must be as diverse as attackers in terms of background, race, and gender. As we like to say, the door is open for anyone to become a cyber defender.
“Almost everything needs cybersecurity. It’s just going to keep growing and it will never go away, so we need more people in it. To get people into cybersecurity we need to break that stigma of what the industry is about. Cybersecurity is not just coding, and we legitimately need all types of people, like psychology majors, English majors, business majors, besides computer science, because there are so many different areas you can get into” says Caitlin Sarian, also known as Cybersecurity Girl, a prominent digital influencer that joined an episode of our Secure the Job Podcast and whose main goal is to help more people understand cybersecurity and consider joining the industry.
“We need to change the security narrative from fear-filled dark tones to hope-filled, optimistic, innovative tones for several reasons. First and foremost, security is a prime driver for innovation, and it needs to inspire and empower people. If we don’t involve everyone, if we continue to think of security as exclusive and fear-filled, then we are creating barriers to entry for defenders to participate,” says Vasu Jakkal, Corporate Vice President, Security, Compliance, Identity, and Management, Microsoft.
Creating real impact in a new and more diverse generation of cybersecurity experts
We take the cybersecurity talent gap seriously and are committed to doing our part to help close it. In 2021, we launched a national campaign with United States community colleges to skill and recruit 250,000 people into the cybersecurity workforce by 2025 and in summer 2023 we made this mission global by expanding this program to 28 countries. Furthermore, the school 42 initiative provides Microsoft Cybersecurity Curriculum and facilitates the completion of Microsoft Certification (SC900) in campuses worldwide. Additionally, with programs like Technology Education and Learning Support (TEALS) and the Last Mile Microsoft Scholarship, and partnerships with organizations such as Codepath, we’re not only taking computer science and cybersecurity learning to students, but we’re also going the full circle in providing the financial support many families need to enable students to continue their educational pathway.
However, there is still a long way to go, and we know that one way to reduce the skills gap is to bring more underrepresented groups into the workforce. One important effort we’ve been focusing on is attracting more women to the industry. Women offer diverse points of view, deep analytics and risk assessment skills, and emotional intelligence that are hallmarks for a successful cyber defender, but they represent around only 25 percent of the cybersecurity workforce today.4 In a Microsoft-commissioned survey, we learned that the reasons for this underrepresentation include gender bias, not enough female mentors and role models, insufficient education opportunities, and uncertainty about cybersecurity career pathways.5 That’s why we partner globally with projects that practice similar values and have the same commitment to diversity in cybersecurity, such as Minorities in Cybersecurity, Executive Women’s Forum, and WOMCY. In the United States, two of our main education partners, Women in Cybersecurity (WiCyS) and Girl Security, have been recently recognized by the White House’s National Cyber Workforce and Education Strategy as key players in changing the diversity landscape of the cybersecurity workforce.
“Part of the challenge is driving the message that diversity is not just about numbers. It’s about innovating security solutions that we can’t possibly conceive right now because we don’t have diverse voices in the room to yield those outcomes. When we bring first-generation college and immigrant students to the table, the effects are remarkable.”
—Lauren Buitta, Chief Executive Officer and Founder, Girl Security
At Microsoft we’ve also been using technology innovation to spread interest in cybersecurity while doing it earlier in the process, as early exposure strongly impacts career choices in the future. To help with that and to enable kids from all ages to behave safer online, we’ve developed the Minecraft Education Cybersecurity Collection, with levels that go from kindergarten to college and focus on teaching cyberskills at every level with fun, accessible lessons for the modern digital citizen, followed by learning resources.

How AI is empowering a stronger workforce
The latest generative AI revolution has gotten plenty of people excited because of its potential to advance business initiatives, but there’s also a great potential impact of AI adoption in cybersecurity talent. Vasu Jakkal recently shared how AI can improve cybersecurity by harnessing diversity and offered other suggestions for how to encourage cybersecurity interest.6 Human ingenuity and expertise will always be a precious and irreplaceable component of security, and AI has the power to tip the scales in favor of cyber defenders by augmenting human capabilities, enabling machine speed cyberthreat detection, and fostering a stronger collective skillset of diverse backgrounds and points of view.
Among other things, generative AI also has the potential to expand the number of cybersecurity professionals and help them refine and strengthen their skills. Using AI tools in recruiting can also help “transcend biases, optimize talent acquisition, promote inclusive training and education,” and lead to more hiring of diverse candidates.7
Recognizing the increasing importance of AI skills in the global workforce, Microsoft has launched the AI Skills Initiative to enhance AI education and address emerging skills gaps. In partnership with LinkedIn, the initiative offers a Professional Certificate on Generative AI and the Generative AI Skills Grant Challenge, a collaboration with other organizations that focus on underserved communities.
Champion the advocacy to propel cybersecurity education and careers forward
There is a lot we all can do to support cybersecurity education and help narrow the skills gap. If you’re a security professional, consider being a sponsor for someone or supporting one of these many mentoring programs mentioned in this blog.
Many remain unaware of the vast opportunities awaiting them in cybersecurity, so we invite you to amplify these prospects to a broader audience. Check with your local area school if they have a TEALS program and let them know about the career path the Last Mile Education Fund offers. Amplify free cybersecurity content, training, and learning opportunities by earning a Microsoft and LinkedIn’s Career Essentials Certificate and show the wonders the Minecraft Cybersecurity education game can provide to the younger generation.
In the spirit of security being a team sport, explore our Cybersecurity Awareness Website to continue your education and to help educate your organization and community. It takes a village to make a difference in the lives of others and to support our cybersecurity professionals who tirelessly keep us safe. It is vital that no matter what role we play in our workplace, family or community, we all become a cyber defender.
Learn more
To learn more about cybersecurity best practices and educational opportunities, visit our Cybersecurity Awareness Website.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and Twitter (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Microsoft Digital Defense Report 2023, Microsoft.
2Cybersecurity Workforce Study, ISC2. 2022.
3Attracting Young Talent to the Growing Cybersecurity Industry, JonesPR. May 13, 2020.
4Empowering Women to Work in Cybersecurity Is a Win-Win, BCG. September 7, 2022.
5Results based on March 2022 IWD Survey commissioned by Microsoft in partnership with WE Communications.
6How AI can improve cybersecurity by harnessing diversity, according to Microsoft Security’s Vasu Jakkal, Dan Patterson. August 25, 2023.
7The Power of AI to Enhance Diversity in Security: Strengthening Defences through Inclusion, LinkedIn. July 2, 2023.
The post From classroom to cyberfront: Unlocking the potential of the next generation of cyber defenders appeared first on Microsoft Security Blog.
M3, M3 Pro, Criticized In New Report, Base Apple Silicon ‘Doesn’t Move The Needle Considerably’ But M3 Max ‘Is Quite A Feat’
Apple’s latest 3nm family of Mac chipsets include the M3, M3 Pro, and the M3 Max, and based on various performance tests and leaks, two of them are considered iterative updates over their direct predecessors, while one of them is viewed as a worthy upgrade. In a new report, the base SoC and the M3 Pro are largely criticized as they do not bring anything noteworthy. M3 Max performance compared to desktop chips like the M2 Ultra that power the Mac Studio and Mac Pro In the latest edition of Mark Gurman’s ‘Power On’ newsletter, the Bloomberg reporter provided his […]
Read full article at https://wccftech.com/m3-and-m3-pro-criticized-in-new-report-but-m3-max-gets-praise/
Distribute Cybersecurity Tasks with Diffusion of Responsibility in Mind

The notion that security is everyone’s responsibility in computer systems dates back to at least the early 1980s when it was included in a US Navy training manual and hearings in the US House of Representatives. Behind the pithy slogan is the idea that every person in the organization contributes to its security program. Even if the company has employees with “security” in their title, they cannot safeguard information assets on their own. After all, people outside the security team are the ones who deliver services, build products, or otherwise engage in business activities that require making security-related decisions.
Can Everyone be Responsible?
How might we distribute cybersecurity tasks and operationalize the perhaps utopian idea that "security is everyone's responsibility"? After all, the diffusion of responsibility principle suggests that people feel less responsible when they are part of a group, possibly because they think someone else will take action.
Saying that security is “everyone’s responsibility” might lead to it being “nobody’s responsibility.” To distribute security responsibilities among the stakeholders, we need to counteract the diffusion of responsibility. We should clarify expectations, hold people accountable, and establish a personal connection between the stakeholders and the affected items.
Clarify Expectations
Cybersecurity leaders generally design and manage the security program, which is the structure within which the organization can achieve its security objectives. Within that program, teams with “security” in their name have responsibilities such as:
- Identifying and tracking the remediation of security vulnerabilities
- Engineering systems for enforcing security measures
- Monitoring and investigating security events
- Documenting secure configuration guidelines, templates, and practices
- Providing security guidance to business stakeholders
- Noticing when security expectations aren't followed
Who should be fixing vulnerabilities, incorporating security principles into projects, and deploying technology in a security-appropriate way? In most cases, these tasks are distributed throughout the organization.
Members of specific teams are typically assigned security responsibilities in the company’s security policies and procedures, which communicate expectations such as:
- DevOps or IT teams patch systems according to risk-based, agreed-upon timelines.
- Procurement or Legal teams incorporate security reviews of vendors according to a defined process and include necessary security requirements in contracts.
- People or HR teams screen new hires according to specific background check requirements.
For capturing expectations in great detail, we can use some form of a responsibility matrix, such as RACI, to capture who should be responsible, accountable, consulted, and informed for specific security-related activities. In addition to documenting expectations, the discussions that lead to creating a responsibility matrix can surface disagreements or coverage gaps so the organization has the opportunity to address them.
More broadly, organizations typically rely on the security awareness program to clarify which security responsibilities apply to all personnel, including items such as:
- Handling information according to the company’s guidelines and the organization’s approach to data classification
- Watching out for suspicious activities that might indicate a cybersecurity event or a scam and reporting them for investigation
- Using established templates, libraries, and standards that incorporate security requirements or guardrails when engaging in business activities
- Reaching out to the security team for guidance as appropriate, such as when launching new projects that require security or privacy considerations
Having clarified what members of the company’s cybersecurity program should do, we need to consider how to track whether these responsibilities are followed and, where practical, enforce the expectations.
Enforce Accountability
Even with the best intentions, those whose primary job isn’t cybersecurity will sometimes forget or not follow through on their security-related responsibilities. To increase the chances that the distributed security measures will be in effect, we can use a combination of three approaches:
- Enforce security expectations using technology to prevent insecure choices or actions. For example, security teams can configure user authentication to require two-factor authentication (2FA) instead of merely reminding employees to enable 2FA. In another example, software development tools can be set up to block code commits that include secrets or vulnerable dependencies. Such measures eliminate the opportunity for non-compliance; however, direct enforcement doesn’t work for all security controls and situations. For instance, some applications don’t allow the organization to centrally control 2FA settings.
- Implement guardrails against severe risks when people take actions or make decisions outside the boundaries the organization considers reasonable. For example, infrastructure-as-code tooling, such as Terraform, allows the creation of preapproved modules with minimum security requirements while letting engineers control other aspects of the infrastructure. Similarly, software developers might need to follow strict change control practices in production while having more leeway in dev environments. Another example of guardrails is the use of network security measures, such as DNS filtering, to restrict access to dangerous website categories.
- Monitor for gaps and take action when the right security steps aren’t taken. Observing security-related activities through log aggregation is a part of this. Another is continuous compliance monitoring, which aims to automate the tracking of security controls. For instance, to confirm that background checks occur, we can query HR and background-checking systems to detect missed employee screenings. Also, modern asset management approaches involve gathering data from multiple sources to identify gaps; for example, organizations can correlate data from systems management and endpoint security tools to identify systems with missing security agents.
Of the many security controls, ensuring accountability for patch management is particularly challenging because this practice often distributes responsibilities across multiple teams. The software might be patched by DevOps, IT, developers, external vendors, and so on. It’s even possible to assign some patching responsibilities to end users as long as accountability is tracked. For example, people might be allowed to install approved applications that are not centrally managed by the IT team. In that case, the individuals should be keeping the apps up-to-date. Organizations can use automated tools to track when the apps are not maintained and contact end-users reminding them to take action (see a real-world example of this).
Make It Personal
We’ve been exploring ways of counteracting the diffusion of responsibility principle as we distribute security tasks. Communicating expectations and enforcing accountability is a part of the effort to ensure that people don’t ignore their responsibilities. Another way to fight the diffusion of responsibility is to establish a personal connection between the person and the task at hand. What does this mean in the context of cybersecurity?
People get accustomed to the systems they use at work. Many start to think of the company-supplied laptop as “their” laptop. To some extent, they consider the folders where they keep work documents as “their” folders and the applications they’ve customized as “their” apps. The security team can point to this attachment to highlight the person’s connection to such assets, so they’re more likely to remember their related security responsibilities. For example:
- When end users have patching responsibilities for their laptops, for instance, if they need to reboot the system or allow an update to be applied, remind people that these are their systems. Keeping the laptop in top shape allows them to do their best work.
- When people need to remember to include security in projects or design discussions, highlight the benefits of keeping their data secure, which they’re more likely to achieve when considering a security expert’s advice. Addressing security risks upfront will minimize the chances of a disruption to their project.
- When highlighting the need for colleagues to safeguard data shared with third parties, point out that their interactions might be compromised if they don’t follow the necessary security measures. Not only will the company look bad if the data is mishandled or misused, but so will they.
When sharing security responsibilities across stakeholders, also point to the shared business objectives that the organization’s personnel are looking to achieve. To be successful, colleagues should understand the organization’s business goals and how their security responsibilities can enable or hinder the company from reaching them. By framing security tasks in that context, you’re more likely to establish a security program that scales in a way that security will truly be everyone’s responsibility.
Power Up Anywhere With Up to 48% Off Anker Power Stations - CNET
Meta Fights Sprawling Chinese ‘Spamouflage’ Operation
Meta has purged thousands of Facebook accounts that were part of a widespread online Chinese spam operation trying to covertly boost China and criticize the West.
The post Meta Fights Sprawling Chinese ‘Spamouflage’ Operation appeared first on SecurityWeek.
Disney Spent $100 Million Making Willow, Then Threw It In The Bin

TMNT's Disastrous First Rehearsal Bled Into Raphael's Angry Persona

The US Is Turning Away From Its Biggest Scientific Partner at a Precarious Time
Read more of this story at Slashdot.
How to Make Sure Your Paint Job Doesn’t Peel, Bubble, or Discolor

It’s often said that painting is the home project that gives you the most bang for the buck. A fresh coat of paint can make a room feel brighter, bigger (or more intimate) or give your exterior an entirely different character, and you don’t need a ton of skills or special equipment to accomplish it.
GOG Interview: Read how to make an all killer, no filler shooter from the creator of Turbo Overkill
Turbo Overkill – savage, over-the-top FPS with stunning cyberpunk visuals and inspiration taken from some of the all-time greats like Doom, Duke Nukem and Quake, has just left its early access and is available on GOG in its full glory.
Anyone who already played it knows how immensely fun the title is. We, however, also had the pleasure of talking to Sam Prebble, one of the creators of Turbo Overkill, and directly asked him about the development process, how the game stands out in the genre, and what you can expect from it.
Enjoy the read of how to make an all killer, no filler shooter!
After more than a year in early access we can finally play Turbo Overkill in its full glory! Could you share some more light on the development process of the game? How much did the early access and community’s feedback impact it?
Early Access was something I feel benefited the game immensely! The community feedback has been very valuable and helped pivot the game in a direction that I feel is much better than anything I could think up on my own.
I've been very fortunate to have a community of players who care a lot about the game and contribute a lot of great ideas. Early Access is definitely a path I would recommend to other developers.
We know that Turbo Overkill takes over-the-top to never-before-reached heights. With its crazy gameplay and stunning visuals it is safe to assume that playing it will be an experience filled with fun and adrenaline. Was that “wildness” something you thought was missing from the modern FPS genre?
I wanted to make a game where I took everything I loved from the genre and mashed them together into a sandbox of chaos. A lot of my favorite first-person shooters get you into the action seconds after launching the game.
There was something in older shooters that I feel is sometimes missed in some games today. Back then, it's just the game and its core loop, no fat or filler. If a game takes 30-60 minutes of tutorials and hand-holding before letting me experience its core game loop, I tend to lose interest pretty fast. It was important for me to let players start blowing thugs to red mist within the first 30 seconds of starting the game, and from there it doesn't let up!
And what about the game’s difficulty? Should players expect a challenge while blasting through Turbo Overkill or they’ll rather not care about ever dying and just enjoy the pure rampage?
If the player wants it to be, the game can be extremely challenging at times. Turbo Overkill has 5 main difficulty settings, including Murder Machine, in which its description suggests if it should be played... 'Don't.'
On top of this, the game is highly customizable with hidden secret Tech-Chips, which can be used to add modifiers to the game experience, making it as easy or as difficult as you want (enable 3x enemy spawns? Why not! Unlimited ammo? Sure).
Another thing I felt was important was to make sure that every time the player dies, they get back into the action almost instantly. There is no loading after death; you are dropped back within seconds, and checkpoints are very frequent.
Is the story in the game an important aspect of it, or rather just a background for the gameplay experience?
In true boomer shooter fashion, the action takes the front stage. You can run through guns blazing and skip the story, but for those wanting to dig deeper into Paradise, there is a lot here to uncover.
The game shows its story through a series of short cinematics. Collectibles that expand the characters and the story can also be found.
Working with the amazing team at Apogee, I've been very fortunate to have the opportunity to work with a crew of extremely talented writers, actors, and actresses that added a layer on top of the experience that I think a lot of people are gonna love.
Finally, how long of a journey can we expect from Turbo Overkill?
The game takes roughly 9-10 hours to complete, but if you are a secret hunter, the experience can be extended vastly with secret levels and hidden collectibles. Mod support is also available, with a lot more to come on this front in the future.
Anything you’d like to say to our community before they jump into the skin of Johnny Turbo?
We have a lot of cool stuff we will be rolling out over the coming months, including extended multiplayer, an arcade mode, and even more modding support. This is just the beginning of Johnny's venture into Paradise!
We’d like to thank Sam very much for the interview and Apogee Entertainment for allowing us to have this great title DRM-free on GOG.
Now, there’s only one thing left to do – get those hidden arm rockets and a chainsaw ready and slaughter everyone who stands in your way. Turbo Overkill is OUT NOW on GOG.
Rockstar Games Acquires Modding Team That It Previously Banned
Read more of this story at Slashdot.
How to help Pandirna in Baldur’s Gate 3

How do you help Pandirna in Baldur's Gate 3? You will come across a locked storehouse as you explore Emerald Grove. Inside are all sorts of nicknacks, but also a Tiefling named Pandirna. Unfortunately for her, she seems to be in quite a predicament: she can't use her legs. After drinking a potion to become stronger, she seems to be paralyzed from the waist down.
This is just one of many puzzles and riddles that, according to our Baldur's Gate 3 review, make this RPG "beautifully complex." Luckily, you can help Pandirna in Baldur's Gate 3 by using one of your many spells. If your main character's selection of spells can't help her, then one of your many potential BG3 companions, the Half-Elf Cleric Shadowheart, can help her out instead.
NVIDIA’s GeForce RTX 4090 Is 4 Times More Popular Than AMD’s Radeon RX 7900 XTX According To Steam

Steam has just released its latest hardware survey and it looks like NVIDIA's flagship RTX 4090 is far more popular than AMD's RX 7900 XTX.
NVIDIA GPUs Remain King of The Hill On Steam, AMD Still In 2nd Place But Picking Up Share In CPUs Against Intel
According to the latest figures, NVIDIA GPUs amount for 74.69% of the share across Steam's entire userbase who participated in the survey while AMD accounts for 15.93% and Intel for 9.02%. When looking at the top five most popular GPUs, the GeForce GTX 1650 remains in the top 5.3% share & that is followed by the RTX 3060 which sits at 4.88% share. The GTX 1060 is in third place with 4.6% share while the RTX 2060 sits at 4.10% share. We lastly have the RTX 3060 Laptop GPU which sits at fifth place with a share of 3.76%.

From what you can see, the NVIDIA 60 and 50-class GPUs remain the most popular amongst the gaming community due to their price-to-performance ratio. Meanwhile, AMD's Radeon RX 6600 & 6500 series graphics cards make up for a combined share of 1.29%.
Looking at the higher-end spectrum, the NVIDIA GeForce RTX 4090 itself holds a respectable 0.72% share which is more than the share of its predecessor, the RTX 3090 (0.66%). The RTX 4080 sits at a share of 0.47% versus the 2.46% & 0.85% shares of its predecessors, the RTX 3080 & RTX 3080 Ti. A similar example is the RTX 4070 series which has a combined share of 1.23% versus the RTX 3070 series which has a combined share of 2.52%.

Finally, we have the RTX 4060 Ti which has a share of just 0.23% which is quite low versus the 3060 Ti which sits at 3.43% and the Non-Ti RTX 4060 is nowhere to be seen.
Steam Hardware Survey (July 2023) Current-Gen GPU Market Share
| GPU Name | Steam Share |
|---|---|
| RTX 4070 Ti | 0.68% |
| RTX 4090 | 0.65% |
| RTX 4070 | 0.55% |
| RTX 4080 | 0.47% |
| RTX 4060 Ti | 0.23% |
| 7900 XTX | 0.17% |
What's impressive is that the NVIDIA GeForce RTX 4090 GPU is almost 4 times more popular than the AMD Radeon RX 7900 XTX which only recently showed up in the Steam database. The GPU has a share of 0.17%. The RTX 4090 and RX 7900 XTX launched just a few months apart but feature a big price difference. The RTX 4090 retails for $1599 US (MSRP) while the RX 7900 XTX has an MSRP of $999 US. Even the RTX 4080 which launched closer to the 7900 XTX is 2.7 times more popular on Steam despite the Radeon offering a better price-to-performance proposition to gamers. The RTX 4080 however is overshadowed by the RTX 4090 which is often seen as a better value.

Moving over to the CPU side, here we see AMD gaining a share each month over Intel. AMD CPUs account for 33.19% of the share across Steam's userbase while Intel declined to 66.76%. We can expect a 50/50 percentile split between the two chipmakers in the coming months.

For some very odd reason, the quad-core CPUs saw the biggest rise along with dual-core while 10-core & 12-core chips saw a 0.20%+ increase compared to last month. In terms of OS, Windows remains the most popular choice amongst Steam gamers with Windows 11 gaining share and now sitting at 38.11% while Windows 10 leads the overall share but declining rapidly with a current share of 60.15%.
Disclaimer: These results are only applicable to Steam & not representative of global market share. Steam has a large user base, measuring hundreds of millions of gamers and several million active gamers who participate in such surveys each month to get an idea of what kind of hardware is popular amongst the PC gaming community.
- Intel
- AMD
- AMD
- NVIDIA
- Intel
The Accessories That'll Make You Actually Use Your Water Bottle

Somewhere there’s a student of human behavior who can explain why, for so long, I have surrounded myself with water bottles, yet still remained dehydrated. I had several good reasons for this—which I will get to—but whatever the cause, I was determined to fix it. Fortunately for me, the solutions were only a few…
Apple SVP Of Hardware Engineering Hints That iPhones Won’t Have Removable Batteries Despite EU’s New Rules; Says It Will Reduce Durability

An earlier EU ruling will require companies like Apple to offer devices to customers that feature ‘easy to replace’ batteries. However, despite the enforcement of these rules, the Cupertino firm’s Senior Vice President of hardware engineering hints that such a change will not be arriving to the company’s devices as it can compromise the internal integrity, reducing the overall durability.
Assuming new EU rules are stringent, Apple may be forced to exit several markets entirely
Apple executive John Ternus spoke in an interview with the YouTube channel ORBIT that was spotted by Supercharged regarding the possibility of bringing removable batteries to future iPhones. Though most of the interview focused on Apple’s environmental efforts that Lisa Jackson led, Ternus believes that if consumers truly want a battery replacement for their devices, there needs to be a safer way to make that happen.
In other words, the company’s SVP of hardware engineering believes that iPhone owners would inadvertently harm themselves when performing a battery replacement procedure. While the executive may have said this out of concern for the people’s well-being, it is likely that this statement was made to ensure that one of Apple’s revenue streams is not severed.
Despite the technology giant shipping millions of iPhones in a calendar year, it stands to make a ton of money through battery replacements alone, with U.S. customers needing to pay $99 for a battery replacement for the base iPhone 14 if they have not opted for AppleCare+. Ternus states that making an internal component more repairable can also add a potential failure point in that area, making devices less durable.
He also mentions that making batteries easily replaceable would make incorporating water and dust-resistant seals on iPhones difficult. Ternus also says that Apple wants to build products that last while also pointing out that iPhones have held their resale value quite well over the years thanks to their improved durability.
At the end of the day, despite offering customers a premium experience when they purchase their first iPhone, Apple is a company focused on generating profits, so assuming that EU’s rules do not allow for any ‘bending of the rules,’ the iPhone maker would exit the markets that fall under the European Union rather than be forced to change the design. Even if Ternus did not explicitly admit this in the interview, most of us knew where his mind was at.
Fortunately, even if Apple does not offer customers an easy solution to replace the batteries in the future, it does not mean the company will make the iPhone 15 family difficult to take apart, as the upcoming lineup is said to be easily repairable.
How Information Disclosure Vulnerabilities Can Wreck Your Organization’s Security
Your organization's security is a vital part of your business. Think about the data you store on your servers. Is it safe from unauthorized users? Are bits of private information like source codes and API keys inadvertently disclosed on your applications?
The original Resident Evil looks phenomenal in newly upscaled HD

The original Resident Evil has been given the HD upscaling treatment, and it gives Capcom's classic horror game a whole new look. While the 1996 game springboarded a whole videogame series alongside the survival horror genre, its visuals haven't aged the best. It still has great artistic direction and brilliant ideas that haven't aged a day, but now a group of players has used modern technology to make the Resident Evil Spencer Mansion feel as sleek as ever, and you can see it below.
No Apologies As Reddit Halfheartedly Tries To Repair Ties With Moderators
Read more of this story at Slashdot.
Dolphin Emulator Abandons Steam Release Plans After Nintendo Legal Threat
Read more of this story at Slashdot.
Portal Prelude: RTX Is Out Today and We’ve Got the Scoop on RTX IO, RTX Remix, and Much More from NVIDIA

Today, NVIDIA has readied a big surprise called Portal: Prelude RTX for PC gamers. Designed as the latest showcase title for RTX Remix, Portal: Prelude RTX will be available on Steam starting at 12 PM PT as a free download to all owners of the original game.
It is a community remaster of Portal: Prelude, the fan-favorite award-winning mod for Valve's game. It's the first game made by modders who had early access to the RTX Remix creator toolkit, and it was designed to leverage all of NVIDIA's cutting-edge technologies: path tracing, NVIDIA DLSS 2 and 3 (which boost performance by 5X at 4K and max settings, according to NVIDIA, allowing 80+FPS on RTX 4080 and 4090 GPUs), NVIDIA Reflex, and NVIDIA RTX IO. The long-awaited suite of GPU-based loading and decompression technologies debuts here, delivering 5X faster texture load times in Portal: Prelude RTX and reducing occupied disk space by 44%.

On top of that, the remaster packs a challenging 8-10 hour campaign composed of 19 new test chambers, new advanced gameplay mechanics, and a fully voiced story with NPCs.
Wccftech has the scoop on Portal: Prelude RTX and all its features, thanks to a chat with Nyle Usmani, Product Manager for RTX Remix at NVIDIA. As a side note, there's a new Game Ready driver available for download today, optimized for this RTX remaster.
What was involved in adding RTX to Portal: Prelude RTX?
We developed RTX Remix to make it easy to turn RTX On in classic games. Using RTX Remix, all of the geometry, textures, and lights from Portal Prelude were converted to USD (the universal scene descriptor file format) and then imported into the application to be further modified. Every asset in the game was either ported into Portal: Prelude RTX from Portal With RTX or remade by the mod team by hand via Omniverse connected applications like Blender. In total, the mod team made hundreds of new props and textures for this remaster, all gorgeously rendered with physically accurate materials and immense detail for 4K gaming.
RTX Remix includes a custom D3D9 runtime that can act in place of the D3D9 runtime that the game ships with–this allows us to replace the old rendering APIs and systems with RTX Remix’s 64-bit Vulkan ray traced renderer. This enables the addition of path tracing to classic games and it all updates in real-time as lights and objects move. Light can be cast from behind the player or from another room, and in Portal: Prelude RTX, light even travels through portals. Glass refracts light, surfaces reflect detail based on their glossiness, objects can self-reflect, and indirect light from off-screen illuminates and affects everything you see. DLSS 3 allows us to target an incredibly accurate simulation of light while keeping the experience smooth and FPS high.
On top of the graphical changes, Portal: Prelude RTX also includes updated gameplay and fully voice acted dialogue, making this the definitive way to play the game.
How many people worked on this project?
It was a surprisingly small team. We actually reached out to the original creator of the Portal Prelude mod, Nicolas “Nyko18” Grevet and talked him into coming out of modder retirement and spearheading the project. He partnered with well-known modder David “Kralich” Driver-Gomm. The mod team behind the remaster was five people in total, including two voice actors from the mod community.
How much time did it take from start to finish?
The team of five people had Portal: Prelude RTX completely remastered in less than eight months.
Does Portal: Prelude RTX support Ada Lovelace's hardware path tracing optimizations, like Shader Execution Reordering (SER), Displaced Micro-Mesh (DMM), and Opacity Micro-Maps (OMM)?
Portal: Prelude RTX uses the newest version of the RTX Remix runtime, which includes superior denoisers and improvements to CPU and GPU performance for existing path tracing techniques.
For Portal: Prelude RTX and future NVIDIA RTX Remix mods, the NVIDIA RTX Path Tracing SDK has been enhanced, improving denoiser performance and quality. This is particularly beneficial at lower resolutions, where gamers with older GeForce RTX GPUs can have a better experience.
Portal: Prelude RTX supports Shader Execution Reordering (SER). SER dynamically reorganizes inefficient ray tracing workloads into considerably more efficient ones, further accelerating GeForce RTX 40 Series performance. This leads to better efficiency and eventually better performance.
Opacity Micro Meshes (OMM) increase real-time performance and memory compression for complex geometry, further accelerating GeForce RTX 40 Series ray tracing performance, and with new CPU optimizations debuting in Portal: Prelude RTX, players receive even faster performance.
NVIDIA DLSS 3 and NVIDIA Reflex also make an appearance in Portal: Prelude RTX but have both been upgraded to their newest versions for improved performance, even better image quality, and more responsive gameplay. The game also features NVIDIA RTX IO, enabling incredibly fast loading.
The rest of the tech is pretty consistent with Portal With RTX.
Portal: Prelude RTX is the first game to feature RTX IO. What is RTX IO exactly?
RTX IO is a suite of technologies that enables rapid GPU-based loading and asset decompression with optimizations through our Game Ready Driver for both the DirectX and Vulkan APIs. RTX IO is based on GDeflate, an open GPU compression standard contributed by NVIDIA, which is utilized by both Microsoft’s DirectStorage and new Vulkan Extensions. Portal: Prelude RTX leverages the new Vulkan Extensions.
NVIDIA RTX IO delivers up to 5X faster texture load times in Portal: Prelude RTX and utilizes 44% less disk space! This is a huge boon to modders as they can design their assets in the highest fidelity while taking up a smaller footprint on people’s hard drives.
Does Portal: Prelude RTX only work on NVIDIA GPUs?
Portal: Prelude RTX uses Vulkan ray tracing and should run on any Vulkan RT-capable graphics card. We’ve optimized the game to ensure a good experience on all RTX GPUs, but Portal: Prelude RTX is best experienced on RTX 40 Series GPUs with DLSS 3 due to how intensive and cutting edge path tracing is.
So NVIDIA RTX IO works on AMD and Intel GPUs, correct?
Yes. If a developer implements RTX IO, they get cross-platform support for DirectStorage and Vulkan.
Does RTX IO use tensor cores?
No. RTX IO leverages the open standard GDeflate, which is designed to run on as many parallel cores in the GPU as possible. GDeflate is an open GPU compression standard contributed by NVIDIA.
Is RTX IO compression lossy or lossless?
GDeflate is lossless.

How is the work on the RTX Remix creator toolkit coming along? Do you have an ETA to share on when it might enter early access?
Nicolas Grevet and David Driver-Gomm are the first modders to receive the RTX Remix creator toolkit. We will be expanding the group of modders with early access soon.
What do you think about the community's creations since you released the RTX Remix runtime?
We love it. There is a community-run Discord group where 5,000 modders are utilizing the RTX Remix runtime to remaster over 80 games. The degree of passion we’ve already seen is mindblowing, and I’m struggling to grasp what they’ll produce when we finally put the creator toolkit in their hands. We encourage anyone interested in RTX Remix mods to join the “RTX Remix Showcase” Discord group and take a look.
Can creators expect increased stability for mesh hashes in future versions of RTX Remix?
One of the earliest changes we implemented with the runtime was improving our mesh hashing system to increase stability–it is something we are always keeping our eye on. RTX Remix is groundbreaking tech in that visuals and assets are being replaced on the fly at playback but it's always unfortunate when something breaks and a new asset fails to render at full fidelity or as a replaced asset.
We can confirm our new runtime allows for much more stable meshes in Portal: Prelude RTX than was present in Portal with RTX and due to the speedup in asset streaming with RTX IO, assets load in at full quality at lightning-fast speeds.
Will there be any way to improve particle physics and/or smoke, for instance, at some point?
We had predicted when we open sourced the RTX Remix runtime that modders might contribute code to the runtime that could modernize fluid simulation for smoke and fire. So far, there hasn’t been a community effort on this front. We do find this space interesting but have nothing to announce today.
What about a potential scripting language to add new functionality to games?
It would be cool to enable scripting for dynamic conditional replacements. For example, make the lights turn off when a user enters a room or add fog in a room when a certain asset flies in.
As of now, we have nothing to announce, but it’s the kind of addition we predicted could happen when we open sourced the RTX Remix runtime.
Do you plan to improve the accessibility of using RTX Remix?
The RTX Remix runtime is open source and available for anyone to dig into. We are always working to make the tool as easy to use as we can. And for those who want to dive deep, we are very active in the aforementioned community run Discord and are always keeping an eye on projects that are evolving quickly.
Again, we encourage anyone interested in RTX Remix mods to join the Discord group.
Is there anything else you wish to add about what's next for this tool?
We are hyper focused on getting the RTX Remix creator toolkit available to more people as soon as we can, and we can’t wait to see what modders do when they get their hands on it. We hope everyone enjoys playing Portal: Prelude RTX, the first mod made by the community with early access to the RTX Remix creator toolkit. It’s a sign of what’s to come with respect to RTX Mods that push the graphical horizon.
Thank you for your time.
Manage security settings for Windows, macOS, and Linux natively in Defender for Endpoint
As advanced threats such as ransomware continue to increase in velocity, and sophistication, organizations are evolving their endpoint security strategies away from point solutions to a more holistic security approach focused on vendor consolidation. At the same time, we continue to see a gap between security and IT teams to achieve a seamless and effective operating model for effective endpoint security.
While many endpoint security solutions now provide some level of endpoint management experience that include capabilities such as device inventory and policy authoring, they are often disconnected from the tools IT teams use to do many of the same things. This combination leads to a lack of visibility and coordination among these two groups, leaving too much room for security gaps to grow.
Microsoft believes organizations can protect their endpoints more effectively by bringing their security and IT teams closer together. Today we are excited to announce the public preview of a unified security settings management experience that offers a consistent, single source of truth for managing endpoint security settings across Windows, macOS, and Linux. It is built into the Microsoft 365 Defender portal, and therefore easily accessible for security teams, but built on the powerful capabilities of Microsoft Intune.
Starting today, customers will benefit from a host of new capabilities:
- Native security settings management capabilities in Defender for Endpoint that support Windows, macOS, and Linux
- Existing endpoint security policies are automatically ingested in the Microsoft 365 Defender portal
- Create and edit AV policies directly from the Microsoft 365 Defender portal
- Policies are automatically synced with Microsoft Intune to ensure coordination between IT and Security teams for organizations who use Intune as a full management suite.
- A new list on the device page, that shows all security policies and their settings
- Simplified device onboarding: Removal of Azure Active Directory hybrid join as a management prerequisite
Cross-platform support
Security administrators can now use the security settings management capabilities in Defender for Endpoint to manage their security configuration settings across Windows, macOS and Linux devices without the need for separate management tools, or updates to IT resources.
Managing security policies in the Microsoft 365 Defender portal
Up until today, security administrators were required to use additional tools to manage their endpoint security settings, which can slow down response. The new integration of Microsoft Intune’s endpoint security experience into the Microsoft Defender for Endpoint bridges this gap to help organizations better protect themselves by operating from a single portal.
While Microsoft Intune is not a requirement, the seamless sync offers additional benefits for organizations using both products. All data is shared, always in sync and therefore ensures that IT and security teams share single source of truth for both IT administrators using Microsoft Intune and Security administrators – thanks to this integration, both administrators will see the same data between their portals, preventing confusion, misconfigurations and potential security gaps.
Simplified device onboarding
For organizations that wanted to use security settings management capabilities in the past, Defender for Endpoint required all devices to fully register with Azure AD. This required fixing of pre-existing misconfigurations that prevented devices from successfully joining their identity inventory. Starting today, devices no longer need to be joined to the organizations Azure AD and can instantly be managed with Defender for Endpoint. This significantly simplifies the onboarding process and security settings can be deployed to all in-scope devices immediately.
Let’s take a look at the new, integrated experience.
Manage your security policies
View all your Intune security policies directly in the Microsoft 365 Defender portal by going to Configuration Management > Endpoint Security Policies. You can filter the list as well as search for specific policies using the built-in ‘filter’ and ‘search’ capabilities.
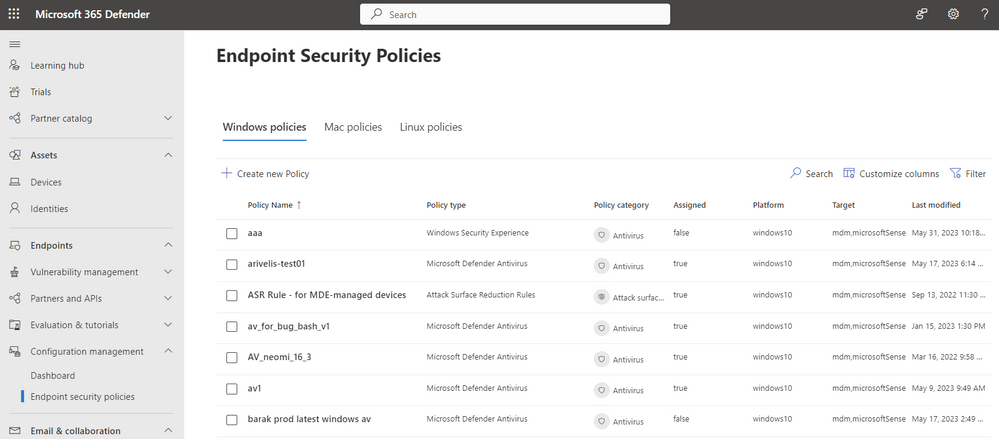
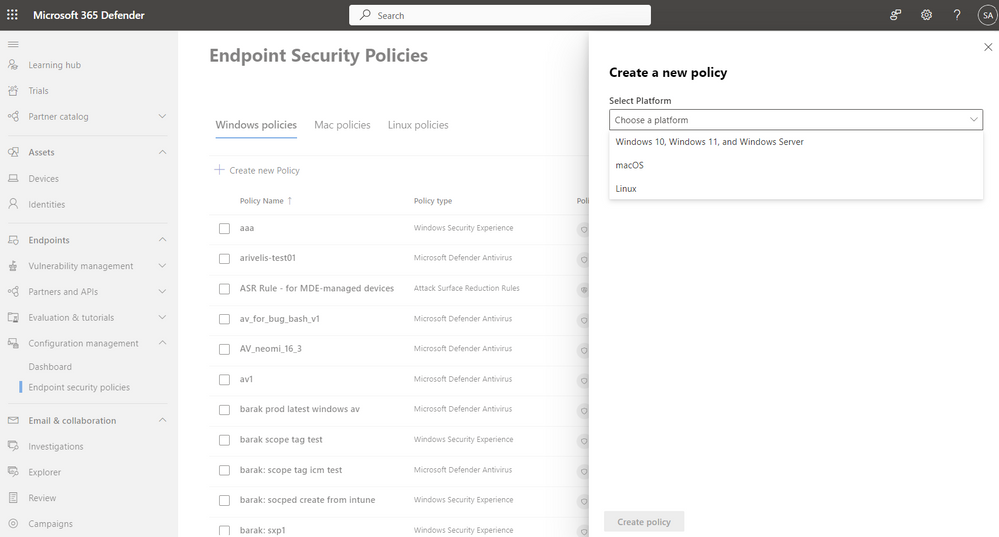
AV policies for Windows, Linux and MacOS can be created from the portal.
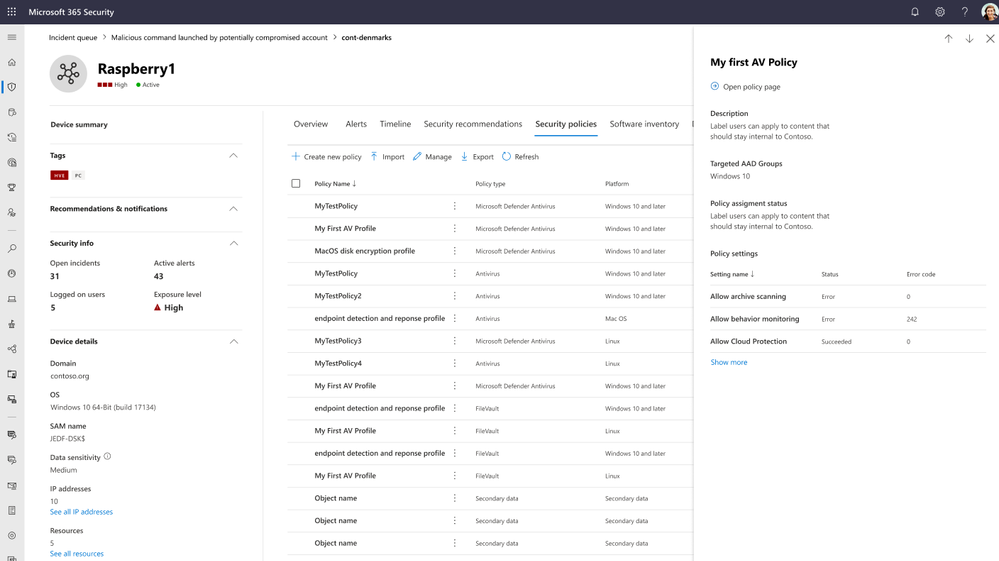
The device page includes a list of received policies, as well as their respective settings and status:
With this update we want to make sure that the transition is seamless for all existing customers. Here is how the transition will work:
- All Windows devices that previously used this management feature, will seamlessly transition to use the new, lightweight mechanism.
- Devices that were previously managed by Defender for Endpoint but had enrollment errors will now seamlessly be enrolled.
- Devices that are already fully registered with Azure AD and are receiving policies, will remain registered to Azure AD and continue to receive policies.
Get started today!
While this change doesn’t require any immediate administrative action, you can take the following actions to prepare for this upgrade:
Step 1: Turn on preview features
Make sure you have preview features enabled in order to use Native Security Settings Management for Microsoft Defender for Endpoint
- In the Microsoft 365 Defender portal navigation pane, select Settings > Endpoints > Advanced features > Preview features.
- Toggle the setting On and select Save preferences.
Step 2: Review how Settings Management for Microsoft Defender for Endpoint is configured
We recommend navigating to the Microsoft 365 Defender portal and reviewing which devices you intend to manage using by Defender for Endpoint at Settings > Endpoints > Configuration management > Enforcement scope. Make sure the feature is turned on, and that for each Operating System, your management preferences have been configured accurately. Advanced configuration options which were available until today remain effective and are outlined in our main documentation.

Step 3: Create a dynamic AAD group to automatically target devices with policies
To ensure that all endpoints enrolled with security settings management capabilities for Defender for Endpoint receive policies, we recommend creating a dynamic Azure AD group based on the devices’ OS Type. Note that you can now also dynamically group servers in Azure AD.
By targeting security policies to these dynamic Azure AD groups, all devices managed by Defender for Endpoint will automatically be protected - without requiring admins to perform any additional tasks like creating a new policy or fine tuning existing ones.
Important :
If until today you’ve been creating dynamic Azure AD groups based on the “MDEManaged” or "MDEJoined" system labels, these are currently not supported for new devices that enroll using Defender for Endpoint settings management. If you still intend to dynamically group devices in Azure AD based on this criterion, we recommend using the “Management Type = microsoftSense” attribute instead.
More information:
- Get started now by checking out our documentation
Hiding In The Windows Event Log
In May 2022, Kaspersky published a write-up on a newly-discovered campaign where malware authors wrote shellcode to the Windows Event Log. This was pretty interesting, and just about 4 months later, Tim Fowler published this blog post over at BlackHillsInfoSec, digging into this a bit deeper and offering several variations of the technique up to red teamers.
Now, I found this technique interesting, not because it's not really something I'd seen before, but because of how Windows Event Logs, and just "Event Logs" prior to Vista, have been used by DFIR analysts. Back in the days of WinXP and Windows 2000/2003, there were The Big Three...Security, System, and Application Event Logs. With the advent of Vista, and then Windows 7, the numbers of Windows Event Logs available to analysts exploded; on my Windows 10 system, a 'dir' of the winevt\logs folder reveals 400 files with the ".evtx" extension. However, not all logs are populated, or even enabled.
However, this doesn't mean that these logs are used during analysis; in fact, much like the Registry, the Windows Event Logs are largely misunderstood by a great many analysts, to the point where I've seen log collection processes that are still restricted to just the Security, System, and Application Event Logs. Further, there seems to be a great deal of Windows forensic analysis training that persists in identifying Windows Event Log records solely by their event ID, even when it's been stated and shown that event IDs are not unique. For example, we often refer to "event ID 4624" when identifying successful login events, but when the event source is "EventSystem", that event ID has an entirely different meaning and significance. And there's nothing the prevents someone from creating an application that writes it's logs to a current or it's own Windows Event Log, using the same event ID. In just the past year, I've seen several tools used by threat actors that create Windows Event Log records, two of which use event ID 0 (zero) for everything, literally every record written, regardless of the message, is event ID 0.
In short, using a Windows Event Log file as a persistent repository is a great idea because responders and analysts aren't likely to look there, nor consider it as a source. I found the use of the "Key Management Service" Event Log pretty interesting, because while it's enabled on the systems I have access to, it's not populated on any of them.
So, I went ahead and tried a variation of one of Tim's commands, as illustrated in figure 1.
 |
| Fig. 1 - Powershell command |
The resulting WEVT record can be seen in figure 2.
 |
| Fig. 2 - Resulting Windows Event Log record |
This is the first record written to that WEVT file on this system, and as you'd expect, the file last modification time reflects that. This illustrates why this particular Windows Event Log file serves as a pretty decent persistent repository. You could change the log file used, but you'd have to find one that either is extremely low volume, or enable one that is similarly low volume. A Windows Event Log that regularly has records written to it does not serve as a suitable persistence mechanism, unless you're able to increase the size of the file,
Tim goes on in his article to extend the technique beyond what Kaspersky discovered, and what this really demonstrates is that there's a great deal that can be done with a few simple (native) tools, some knowledge, and some imagination. And, what makes it "interesting" is that it relies on a data source not often leveraged or exploited by analysts.
Tools like Chainsaw and Events Ripper would not be effective for detecting the use of this technique, particularly if the Windows Event Log used for this technique was not included in the collection process. An Events Ripper plugin that listed all source/ID pairs and their frequency might provide a pivot point for the analyst, but a timeline of system activity would certainly show any suspicious records, again, as long as the impacted WEVTX log is included in the collection process.
This StackOverflow question resulted in several ways to create Windows Event Log records using native methods such as eventcreate.exe, Powershell, etc. Note that using eventcreate.exe is restricted to just the Application Event Log, but the availability of anything written to this (or another) Windows Event Log can be adjusted by the file size and retention settings.
Noclip saved a decade of lost video game history

Video game history preservation is on a roll
It's a great time for video game history buffs. Just last week, we saw unreleased footage of the GameCube's first reveal. Today, we learned that Noclip, a Youtube channel famous for video game development documentaries, has just salvaged an entire decade of lost video game history.
https://www.youtube.com/watch?v=7KKCWGN2fBs
The findings consist of dozens of boxes filled with video tapes. Why tapes? Because the internet was very slow back in the day. Even in the early '00s, most video game reporting took place on TV, and only a select number of big tech and gaming websites ever got to do such coverage. Thus, most of the good stuff like trailers, gameplay captures, and interviews showed up on TV once and then disappeared forever. The few things that made their way onto the Internet featured absolutely abhorrent image and sound quality.
Noclip claims that this massive amount of footage was days away from getting dumped into a landfill, meaning it nearly shared the same fate as the infamous E.T. The Extraterrestrial Atari cartridges.
Their plan for video game history preservation
Noclip acquired so many tapes that they can't even pinpoint how much quality footage they now own. It's one of those rare "good" problems! The team is now going through all the tapes to find anything they deem to be of historical value, and will subsequently upload all of their findings in high resolution on a new video gaming history-dedicated Youtube channel (as well as Archive.org and some other methods). As for the already existing Noclip channel, the team is naturally planning on using the footage to create new documentaries.
Sadly, tapes degrade over time. A few of these have already sustained so much damage that either show nothing or seemingly preview an unknown video game adaptation of The Ring. There's a ticking clock hanging over the people at Noclip as they try to save as much footage as they can. They have limited resources, so they urge anyone who wants to help by subscribing to their Patreon.
Such efforts quench our nostalgia thirst, yes, but that's not the most important part. We need them especially because the preservation of video game history — and of all types of media, really— is at risk. Big streaming platforms don't seem to care about keeping anything that's not an immediate hit. Hell, even Nintendo, a company full of widely beloved games and characters, seems surprisingly adamant in eradicating even their own perfectly sustainable preservation platforms.
Here's hoping that the sheer joy so many get out of seeing these efforts come to fruition might help bring some sense into the minds of big companies.
The post Noclip saved a decade of lost video game history appeared first on Destructoid.
NBC Accused Gene Roddenberry Of Master Manipulation In Pursuit Of Star Trek Season 3

What Is ‘Roof Ponding’ (and What Can You Do About It)?

The roof is one of the most important aspects of your home. If your roof fails you, it kicks off a domino effect of water, structural, and possession damage that makes your comfortable space uncomfortable, unattractive, and potentially dangerous if mold takes root. When it’s doing its job and keeping us dry, we tend…
SNEG re-releases some classic Raven Software PC games

The late-century nightmare
SNEG, a company devoted to completing GOG’s manifesto of dredging up good old games, has dropped another three PC titles of yore. This time, it’s Take No Prisoners, Cyclones, and Necrodome. Those are some real ‘90s names!
All three games are from Raven Software, the company that brought us Hexen, Star Wars: Jedi Knight II: Jedi Outcast, and are now working in Activision Blizzard’s Call of Duty mines.
First up, we have Take No Prisoners. This is a 1997 top-down shooter set in the post-apocalypse. You play as Slade, a man tasked with finding some sort of crystal. It’s, oh gosh… You can just smell the 1990s on it.
https://youtu.be/uJv6lFX5QG8
Moving on, we’re at Cyclones. In this 1994 FPS, you play as Havoc, a man who is essentially Robo-Cop. It was a pretty ambitious first-person shooter, being an early title with mouse control for aiming. Once again, it looks dated, but I absolutely love early first-person shooters, so I absolutely love the look of Cyclones.
https://youtu.be/wGeWo1uoX9s
Finally, we have Necrodome. This one is a 1996 vehicular combat game. This one was right on the cusp of the big vehicular boom that started with 1995’s Twisted Metal. Good times.
https://youtu.be/uKwJd_-Y6f4
Keepers of the time capsule
All of these look like something I’d enjoy tinkering around with. While GOG has moved up in the world and become a more traditional storefront, I still love seeing people dredge up the forgotten PC games that may have been missed. SNEG was actually formed by the former senior vice president of business development at GOG, Oleg Klapovskiy. There doesn’t seem to be any bad blood there (SNEG publishes on GOG), but Klopovskiy’s favorite part of the job seems to have been digital excavation, so he backed Elena Roor to return to it.
The preservation of video games is something I’m extremely passionate about, so I’ll be keeping an eye on SNEG. My only regret in this line of work is that there isn’t enough time to play everything, but, dammit, I still try.
Cyclones, Necrodome, and Take No Prisoners are available right now on GOG and Steam.
The post SNEG re-releases some classic Raven Software PC games appeared first on Destructoid.








