The post ELDEN RING Colosseum-Razor1911 appeared first on SceneSource.
Ronald.phillips
Shared posts
What's better: Quake 2's railgun or the currency 'Gold'?

Last time, you decided that elaborate corridor architecture is better than funicular fights. I wholeheartedly agree with you, but needed to check because the number of video game funicular fights compared to real-world funicular fights did suggest they might be wildly popular. Now we know. As we continue the mission, this week I ask you to choose between the evils of violence and money. What's better: Quake 2's railgun or the currency 'Gold'?
China Says EU TikTok Ban Will Harm Business Confidence
Read more of this story at Slashdot.
Dish Network Confirms Network Outage Was a Cybersecurity Breach
Read more of this story at Slashdot.
Hackers Claim They Breached T-Mobile More Than 100 Times In 2022
Read more of this story at Slashdot.
Skyrim’s headless horseman is doomed to explode, because of Bethesda

Venture into the plains outside Whiterun or Solitude, and you’re likely to encounter one of the Elder Scrolls series’ most memorable NPCs. Any time after 10pm, the ghostly Skyrim headless horseman will come trotting by, blazing a trail of intrigue and eeriness as he leads you towards Hamvir’s Rest. It’s a wonderful homage to the tropes of fantasy and RPG games, skillfully woven into Skyrim by Fallout and Starfield creator Bethesda. But the headless horseman is hiding a horrifying secret - his programming and scripting mean he’s doomed to suffer, again and again, every time he spawns into your Skyrim save.
Three Seasons Into The Mandalorian, And Yep: Grogu Is Still The Cutest Thing Ever

The following article contains spoilers for "The Book of Boba Fett," and "The Mandalorian" season 2.
He's got tiny three-digit hands, glistening eyes, peach fuzz hair, and the cutest, babbly voice you've ever heard. He's green, mischievous, and more powerful than he looks. He's a foundling, capable of warming any heart, no matter how much Beskar it hides behind. He's basically Din Djarin's son and together they are a clan of two. Title aside, he's the true star of "The Mandalorian." He's Grogu, the most adorable addition to the "Star Wars" canon ever — and he's soon to finally be back on our screens!
The second most important reunion in "The Mandalorian" season 3 will be Din Djarin (Pedro Pascal) and Grogu, but nothing tops the fact that the entire viewing audience will soon bask in the glory of our favorite frog-slurping toddler. Ever since Din first stared into that floating baby basket to find huge, trusting eyes staring back, nothing has been the same. Grogu (aka Baby Yoda) has effectively altered our brain chemistry and if you thought his impact might finally wear off by the time the third season rolled around, then you're dead wrong.
All Hail Baby Yoda, Who Keeps Getting Cuter

Somehow, Grogu returned even cuter than before. How is that even possible?! It might have something to do with his force powers. Though he didn't stick around the Luke Skywalker Academy long enough to become a Jedi, Grogu is a lot more comfortable with his abilities. He can now wield the force to do very important things, like spin really fast in a desk chair and protect his vulnerable papa. Thankfully, that doesn't mean his days of hanging out in a satchel or floaty crib cocoon are over (which is great news, because those accessories infinitely add to his cuteness). But it might mean more toddling around and less keeping out of the way, which is even better news because as far as I'm concerned, the more Grogu we get, the better the show becomes!
I get it, Baby Yoda naysayers — it's pretty damn irritating when the Big Bad Corporations genetically engineer adorable creatures for the sake of selling some toys. But that's not quite the case with Grogu (who I admittedly own multiple plushies of) because his importance extends far beyond his cuddly nature. The fact that his huge eyes can melt hearts is no mere coincidence — it's kinda the whole point. As soon as he sets those eyes on Din and their fingers touch, their lives are irrevocably changed for the better.
Cuteness is subjective, except when Grogu is involved. The impulse to protect this 50-year-old toddler is a scientific inevitability. And instead of canceling out his narrative weight, that cuteness — aka his natural ability to turn out brains to goo — amplifies it. That's why our tender hearts ache when his muppet hand touches Din's face, the first being to do so affectionately since Mando was a child. It's why we cringe when "The Mandalorian" dares to show us the toddler in the crosshairs, or whenever he's captured by relentless force of evil, Moff Gideon.
Loving Grogu Is The Way

Foolish Grogu dissenters will argue that he's nothing more than a glorified merch opportunity, but that couldn't be further from the truth. Little Baby Yoda is one-half of the emotional core of the show. He's the reason for this entire chain of events, which have profoundly changed our beloved Mando. In more than one way, Grogu being supernaturally adorable is the secret sauce of "The Mandalorian." His curiosity never fails to lighten the mood (see: Grogu chomping down on space M&M's) and he has an uncanny ability to bring people together. But most important is his attachment to Mando, which pushes Din down an entirely new path, widening the world for the once solitary Mandalorian.
Their tale is a classic lone wolf and cub story, not unlike the other currently airing TV series where Pedro Pascal reluctantly dedicates his life to protecting a small child. And much like "The Last of Us," the cub in question is more than a Macguffin in need of protection. This pint-sized force user is trying to find his place in the world, just like Mando — and it just so happens that wherever they go, they also belong with each other.
Yes, Grogu's out there promoting corporate synergy by frolicking with the dust bunnies and getting his bug eyes plastered on shirts, mugs, blankets, and more. But nothing is more important than what he's doing over on "The Mandalorian": adorably reaching out for the shiny control knob of the Razor Crest, convincing strangers to trust an armored stranger, and giving Mando a very good reason to lift his helmet and open his heart.
"The Mandalorian" season 3 (and Grogu!) return to Disney+ on March 1, 2023.
Read this next: 12 Star Wars Moments That Haven't Aged Well
The post Three Seasons Into The Mandalorian, and Yep: Grogu is Still the Cutest Thing Ever appeared first on /Film.
Three Seasons Into The Mandalorian, And Let's Be Honest: Grogu Sucks

Folks, search your feelings and you'll know it to be true: The reign of Grogu simply must come to a close. For over three years now, "The Mandalorian" has subjected us to the endless coos and inane babbling of the most shameless marketing tool that this franchise has ever seen -- no small feat for the property responsible for Ewoks, Wookiees, BB-8, and the similarly reprehensible affront to all good taste known as Babu Frik. But unlike those side characters and thinly-veiled toys, "Star Wars" has seen fit to bend the entire arc of the series (along with a multi-episode stretch of a completely unrelated spin-off show, "The Book of Boba Fett") around the gravitational pull of this Yoda-shaped black hole. And as "The Mandalorian" approaches its upcoming third season, well, I've had enough.
Okay, with that said, let's get one thing straight right off the bat: "Star Wars" is for kids and that's okay! George Lucas hasn't been shy about the ultimate target demographic he had in mind from the start (12-year-olds, as he put it himself), and so it shouldn't come as much of a surprise that the kid-friendly franchise now under the ownership of, uh, Walt Disney Studios would keep that tradition going. Honestly, the bigger twist would've been if "The Mandalorian" didn't have some sort of blatant marketing hook to keep children and parents alike invested. But just because it's the obvious move doesn't necessarily make it the right move.
With every bit of season 3 footage that continues to throw that annoying, bald-headed furball in our faces, I can feel my disdain for this discount Muppet growing more and more by the day. Say it with me, everyone! It's time for Baby Yoda to end.
This Is Not The Way

Let me put my cards on the table -- I'm not anti-cute by any stretch of the imagination! The Marvel Cinematic Universe equivalent of Grogu, Baby Groot, continues to be one of the best and funniest and most poignant additions that writer/director James Gunn brought to "Guardians of the Galaxy: Volume 2" and beyond. The Mogwais from Joe Dante's "Gremlins" live rent-free in every film fan's head, especially as the mascots of the Letterboxd social media website (and rightfully so). And while some "Star Wars" fans may have forgotten this in the aftermath of his lightsaber-wielding antics in the prequel trilogy, Yoda's first appearance in "The Empire Strikes Back" set the franchise precedent for weirdo, goofy characters who mostly exist to annoy our heroes and make life harder for them. This is all good!
But what do each and every one of those examples have in common? For one thing, they were more than mere excuses to have audiences squeal at their screens in unison and post viral-ready clips and screenshots online, essentially doing the show's marketing on behalf of Disney and entirely for free. Ever since that cliffhanger ending back in the season 1 premiere, Grogu couldn't help but feel like a cynical business calculation by creator Jon Favreau and those higher up the food chain in Lucasfilm. How best to mitigate the risks of launching a brand-new streaming service led by a "Star Wars" series featuring a new and unknown character who (mostly) never takes off his helmet? Easy! Pair Din Djarin (Pedro Pascal) up with an impossibly cute Yoda lookalike who'll get even the most casual fan to subscribe to Disney+ and tune in every week.
Needless to say, it worked like a charm and now here we are.
I Wouldn't Like To See The Baby

Even the idea of a "Star Wars" character existing solely for cuteness' sake wouldn't be a total deal-breaker, however, if only the first two seasons hadn't bent over backwards to treat Grogu as precious as possible, like a meme-factory just waiting to happen. Images like the Child sipping tea, hopping after frogs, or playing with the controls on Mando's spaceship practically feel reverse-engineered to get the intended reactions from viewers on social media. (Note how the one time Grogu diverged even slightly from audience expectations, viewers melted down en masse over something as meaningless as him eating unfertilized eggs.)
Meanwhile, it's no coincidence that the few times Grogu has been placed in genuine peril -- think of the Stormtroopers punching their captive in the Taika Waititi-directed season 1 finale, or Moff Gideon (Giancarlo Esposito) threatening him with the Darksaber in season 2, or even having a deepfake Luke Skywalker suddenly ferry him away from his Mandalorian guardian for Force-training -- have also been the few times that the show has ever seemed to have any real stakes. There's a certain narrative logic to resorting to the classic Western pairing of a grizzled old warrior with a young innocent in his charge, but the show hasn't bothered to actually mine any genuine drama or conflict out of that pairing ... which is probably because they decided to write Grogu as a literal baby with no agency of his own.
But once the creators decided to take their boldest choice yet -- separating Grogu from Mando -- and undercut it by having them reunite in no time at all in "The Book of Boba Fett," any hope of getting even the tiniest break from Grogu's antics sputtered out alongside Lucasfilm's understanding of self-contained narratives.
Sticking Out Like A Green Thumb

Should you be under the impression that I only have the most serious and analytical of complaints regarding Grogu, allow me to dissuade you of that notion altogether.
For better or worse, I have a laundry list of gripes that are much larger than the little tyke himself. For example, I have yet to understand why the creative team behind "The Mandalorian" decided to use distractingly human infant sound effects that sound like they originated from a computer file named StockBabySoundEffects.wav. Every alien species in "Star Wars" (the real Yoda included!) have come with all kinds of distinct idiosyncrasies, voices, and behavior that separate them entirely from our own human mannerisms, while Baby Yoda just sounds like ... a human baby. And that awful name! Let me assure you, "The Book of Boba Fett," that hanging a lampshade on how bad the name "Grogu" is does nothing to absolve the name from being bad in the first place. And as much as I appreciated his single best moment in the entire series -- Force-choking Gina Carano's Cara Dune in a rare moment where I actually cheered the little guy on -- the aftermath of the brilliant "Andor" has made my tolerance for cutesy and zero-calorie storytelling from this franchise at an all-time low.
There's every chance that season 3 of "The Mandalorian" does the unthinkable and actually turns Grogu into a halfway decent character. Maybe he'll even be tolerable, with all his most cloying tendencies dialed back just a smidge. Or Disney and Lucasfilm can just keep trucking along, drowning out the minority voices of cynics beneath the oohs and ahs of Baby Yoda doin' his thing. But whether we all admit it or not, we know the truth. Grogu is just the worst.
Read this next: 11 Villain Origin Stories We Want Next From The Star Wars Universe
The post Three Seasons Into The Mandalorian, And Let's Be Honest: Grogu Sucks appeared first on /Film.
Hackers Claim They Breached T-Mobile More Than 100 Times in 2022

Image: Shutterstock.com
Three different cybercriminal groups claimed access to internal networks at communications giant T-Mobile in more than 100 separate incidents throughout 2022, new data suggests. In each case, the goal of the attackers was the same: Phish T-Mobile employees for access to internal company tools, and then convert that access into a cybercrime service that could be hired to divert any T-Mobile user’s text messages and phone calls to another device.
The conclusions above are based on an extensive analysis of Telegram chat logs from three distinct cybercrime groups or actors that have been identified by security researchers as particularly active in and effective at “SIM-swapping,” which involves temporarily seizing control over a target’s mobile phone number.
Countless websites and online services use SMS text messages for both password resets and multi-factor authentication. This means that stealing someone’s phone number often can let cybercriminals hijack the target’s entire digital life in short order — including access to any financial, email and social media accounts tied to that phone number.
All three SIM-swapping entities that were tracked for this story remain active in 2023, and they all conduct business in open channels on the instant messaging platform Telegram. KrebsOnSecurity is not naming those channels or groups here because they will simply migrate to more private servers if exposed publicly, and for now those servers remain a useful source of intelligence about their activities.
Each advertises their claimed access to T-Mobile systems in a similar way. At a minimum, every SIM-swapping opportunity is announced with a brief “Tmobile up!” or “Tmo up!” message to channel participants. Other information in the announcements includes the price for a single SIM-swap request, and the handle of the person who takes the payment and information about the targeted subscriber.
The information required from the customer of the SIM-swapping service includes the target’s phone number, and the serial number tied to the new SIM card that will be used to receive text messages and phone calls from the hijacked phone number.
Initially, the goal of this project was to count how many times each entity claimed access to T-Mobile throughout 2022, by cataloging the various “Tmo up!” posts from each day and working backwards from Dec. 31, 2022.
But by the time we got to claims made in the middle of May 2022, completing the rest of the year’s timeline seemed unnecessary. The tally shows that in the last seven-and-a-half months of 2022, these groups collectively made SIM-swapping claims against T-Mobile on 104 separate days — often with multiple groups claiming access on the same days.
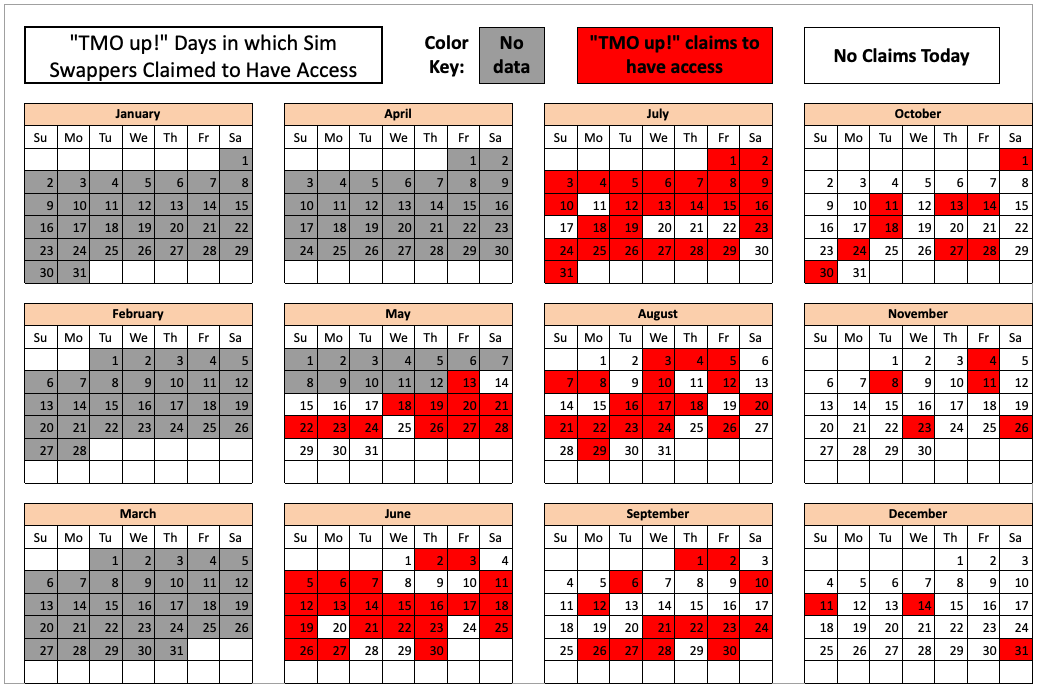
The 104 days in the latter half of 2022 in which different known SIM-swapping groups claimed access to T-Mobile employee tools.
KrebsOnSecurity shared a large amount of data gathered for this story with T-Mobile. The company declined to confirm or deny any of these claimed intrusions. But in a written statement, T-Mobile said this type of activity affects the entire wireless industry.
“And we are constantly working to fight against it,” the statement reads. “We have continued to drive enhancements that further protect against unauthorized access, including enhancing multi-factor authentication controls, hardening environments, limiting access to data, apps or services, and more. We are also focused on gathering threat intelligence data, like what you have shared, to help further strengthen these ongoing efforts.”
TMO UP!
While it is true that each of these cybercriminal actors periodically offer SIM-swapping services for other mobile phone providers — including AT&T, Verizon and smaller carriers — those solicitations appear far less frequently in these group chats than T-Mobile swap offers. And when those offers do materialize, they are considerably more expensive.
The prices advertised for a SIM-swap against T-Mobile customers in the latter half of 2022 ranged between USD $1,000 and $1,500, while SIM-swaps offered against AT&T and Verizon customers often cost well more than twice that amount.
To be clear, KrebsOnSecurity is not aware of specific SIM-swapping incidents tied to any of these breach claims. However, the vast majority of advertisements for SIM-swapping claims against T-Mobile tracked in this story had two things in common that set them apart from random SIM-swapping ads on Telegram.
First, they included an offer to use a mutually trusted “middleman” or escrow provider for the transaction (to protect either party from getting scammed). More importantly, the cybercriminal handles that were posting ads for SIM-swapping opportunities from these groups generally did so on a daily or near-daily basis — often teasing their upcoming swap events in the hours before posting a “Tmo up!” message announcement.
In other words, if the crooks offering these SIM-swapping services were ripping off their customers or claiming to have access that they didn’t, this would be almost immediately obvious from the responses of the more seasoned and serious cybercriminals in the same chat channel.
There are plenty of people on Telegram claiming to have SIM-swap access at major telecommunications firms, but a great many such offers are simply four-figure scams, and any pretenders on this front are soon identified and banned (if not worse).
One of the groups that reliably posted “Tmo up!” messages to announce SIM-swap availability against T-Mobile customers also reliably posted “Tmo down!” follow-up messages announcing exactly when their claimed access to T-Mobile employee tools was discovered and revoked by the mobile giant.
A review of the timestamps associated with this group’s incessant “Tmo up” and “Tmo down” posts indicates that while their claimed access to employee tools usually lasted less than an hour, in some cases that access apparently went undiscovered for several hours or even days.
TMO TOOLS
How could these SIM-swapping groups be gaining access to T-Mobile’s network as frequently as they claim? Peppered throughout the daily chit-chat on their Telegram channels are solicitations for people urgently needed to serve as “callers,” or those who can be hired to social engineer employees over the phone into navigating to a phishing website and entering their employee credentials.
Allison Nixon is chief research officer for the New York City-based cybersecurity firm Unit 221B. Nixon said these SIM-swapping groups will typically call employees on their mobile devices, pretend to be someone from the company’s IT department, and then try to get the person on the other end of the line to visit a phishing website that mimics the company’s employee login page.
Nixon argues that many people in the security community tend to discount the threat from voice phishing attacks as somehow “low tech” and “low probability” threats.
“I see it as not low-tech at all, because there are a lot of moving parts to phishing these days,” Nixon said. “You have the caller who has the employee on the line, and the person operating the phish kit who needs to spin it up and down fast enough so that it doesn’t get flagged by security companies. Then they have to get the employee on that phishing site and steal their credentials.”
In addition, she said, often there will be yet another co-conspirator whose job it is to use the stolen credentials and log into employee tools. That person may also need to figure out how to make their device pass “posture checks,” a form of device authentication that some companies use to verify that each login is coming only from employer-issued phones or laptops.
For aspiring criminals with little experience in scam calling, there are plenty of sample call transcripts available on these Telegram chat channels that walk one through how to impersonate an IT technician at the targeted company — and how to respond to pushback or skepticism from the employee. Here’s a snippet from one such tutorial that appeared recently in one of the SIM-swapping channels:
“Hello this is James calling from Metro IT department, how’s your day today?”
(yea im doing good, how r u)
i’m doing great, thank you for asking
i’m calling in regards to a ticket we got last week from you guys, saying you guys were having issues with the network connectivity which also interfered with [Microsoft] Edge, not letting you sign in or disconnecting you randomly. We haven’t received any updates to this ticket ever since it was created so that’s why I’m calling in just to see if there’s still an issue or not….”
TMO DOWN!
The TMO UP data referenced above, combined with comments from the SIM-swappers themselves, indicate that while many of their claimed accesses to T-Mobile tools in the middle of 2022 lasted hours on end, both the frequency and duration of these events began to steadily decrease as the year wore on.

T-Mobile declined to discuss what it may have done to combat these apparent intrusions last year. However, one of the groups began to complain loudly in late October 2022 that T-Mobile must have been doing something that was causing their phished access to employee tools to die very soon after they obtained it.
One group even remarked that they suspected T-Mobile’s security team had begun monitoring their chats.
Indeed, the timestamps associated with one group’s TMO UP/TMO DOWN notices show that their claimed access was often limited to less than 15 minutes throughout November and December of 2022.
Whatever the reason, the calendar graphic above clearly shows that the frequency of claimed access to T-Mobile decreased significantly across all three SIM-swapping groups in the waning weeks of 2022.
SECURITY KEYS
T-Mobile US reported revenues of nearly $80 billion last year. It currently employs more than 71,000 people in the United States, any one of whom can be a target for these phishers.
T-Mobile declined to answer questions about what it may be doing to beef up employee authentication. But Nicholas Weaver, a researcher and lecturer at University of California, Berkeley’s International Computer Science Institute, said T-Mobile and all the major wireless providers should be requiring employees to use physical security keys for that second factor when logging into company resources.

A U2F device made by Yubikey.
“These breaches should not happen,” Weaver said. “Because T-Mobile should have long ago issued all employees security keys and switched to security keys for the second factor. And because security keys provably block this style of attack.”
The most commonly used security keys are inexpensive USB-based devices. A security key implements a form of multi-factor authentication known as Universal 2nd Factor (U2F), which allows the user to complete the login process simply by inserting the USB key and pressing a button on the device. The key works without the need for any special software drivers.
The allure of U2F devices for multi-factor authentication is that even if an employee who has enrolled a security key for authentication tries to log in at an impostor site, the company’s systems simply refuse to request the security key if the user isn’t on their employer’s legitimate website, and the login attempt fails. Thus, the second factor cannot be phished, either over the phone or Internet.
THE ROLE OF MINORS IN SIM-SWAPPING
Nixon said one confounding aspect of SIM-swapping is that these criminal groups tend to recruit teenagers to do their dirty work.
“A huge reason this problem has been allowed to spiral out of control is because children play such a prominent role in this form of breach,” Nixon said.
Nixon said SIM-swapping groups often advertise low-level jobs on places like Roblox and Minecraft, online games that are extremely popular with young adolescent males.
“Statistically speaking, that kind of recruiting is going to produce a lot of people who are underage,” she said. “They recruit children because they’re naive, you can get more out of them, and they have legal protections that other people over 18 don’t have.”
For example, she said, even when underage SIM-swappers are arrested, the offenders tend to go right back to committing the same crimes as soon as they’re released.
In January 2023, T-Mobile disclosed that a “bad actor” stole records on roughly 37 million current customers, including their name, billing address, email, phone number, date of birth, and T-Mobile account number.
In August 2021, T-Mobile acknowledged that hackers made off with the names, dates of birth, Social Security numbers and driver’s license/ID information on more than 40 million current, former or prospective customers who applied for credit with the company. That breach came to light after a hacker began selling the records on a cybercrime forum.
In the shadow of such mega-breaches, any damage from the continuous attacks by these SIM-swapping groups can seem insignificant by comparison. But Nixon says it’s a mistake to dismiss SIM-swapping as a low volume problem.
“Logistically, you may only be able to get a few dozen or a hundred SIM-swaps in a day, but you can pick any customer you want across their entire customer base,” she said. “Just because a targeted account takeover is low volume doesn’t mean it’s low risk. These guys have crews that go and identify people who are high net worth individuals and who have a lot to lose.”
Nixon said another aspect of SIM-swapping that causes cybersecurity defenders to dismiss the threat from these groups is the perception that they are full of low-skilled “script kiddies,” a derisive term used to describe novice hackers who rely mainly on point-and-click hacking tools.
“They underestimate these actors and say this person isn’t technically sophisticated,” she said. “But if you’re rolling around in millions worth of stolen crypto currency, you can buy that sophistication. I know for a fact some of these compromises were at the hands of these ‘script kiddies,’ but they’re not ripping off other people’s scripts so much as hiring people to make scripts for them. And they don’t care what gets the job done, as long as they get to steal the money.”
Skyrim and Fallout devs talk about some fun secrets in their games

I’m a sucker for well-hidden video game easter eggs, from Psychonauts 2’s strange mpreg cutscene to the ability to play as a baby in Mount & Blade 2, they're all great they’re great. But it’s all too easy to walk past easter eggs without knowing they were even there. I’ve probably waved off multiple fun secrets, mistaking them for lore I didn’t understand or a questline I haven’t gotten to. So, my pea-sized brain enjoyed this video of game designer Steve Lee interviewing the devs behind Skyrim and Fallout as they reveal some dev secrets behind those games - including a cool egg.
Resident Evil 5 for Steam updated with split-screen co-op

I really, really miss Sheva
Here's an odd but not unwelcome occurrence, Capcom has quietly updated the Steam/PC edition of its survival horror sequel Resident Evil 5. The new patch, now available to download on the Steam platform, adds split-screen local co-op, removes Games for Windows Live, and stomps a few bugs.
Originally released in 2009, Resident Evil 5 saw former S.T.A.R.S. operative Chris Redfield head out to West Africa, investigating a potential Bio-Organic weapon sale, led by terrorist Ricard Irving. Teamed with BSAA operative Sheva Alomar, the duo soon find that this case goes far deeper than mere weapons sales, and will bring Chris face-to-face with some welcome, and very unwelcome, faces from the past.
He also punches a boulder to death.
This Steam update is a long, long time coming, and the removal of Games for Windows Live support eliminates a frustrating hurdle in playing the game. Of course, the Resident Evil series has long moved forward from its heady, tank-controlled, RE5 days, but for those who still enjoy running through the entire franchise with pals, then this new update contemporizes the release for future efforts.
Now, if we can just see to giving Sheva her grand franchise return, that'd be just peachy.
The post Resident Evil 5 for Steam updated with split-screen co-op appeared first on Destructoid.
The real Cocaine Bear taxidermy statue is in Kentucky
If you found it hard to believe that the film, Cocaine Bear, was in theatres, just wait until you find out about the real-life taxidermy statue. We also highlight where to watch the movie.
Keri Russell is joined in the cast list by Alden Ehrenreich, Margo Martindale, Kristofer Hivju, Hannah Hoekstra, and Jesse Tyler Ferguson.
Directed and co-produced by Elizabeth Banks and written by Jimmy Warden, the horror comedy, Cocaine Bear, is inspired by the true story of an American black bear that consumed a whole bag of the titular drug in 1985.
Cocaine Bear’s real-life taxidermy statue
The Kentucky for Kentucky Fun Mall, located in Lexington, Kentucky, is the proud owner of the real-life Cocaine Bear taxidermy statue.
For those who don’t know, the real bear died after ingesting a large amount of the substance and was found in Chattahoochee National Forest, Georgia in 1985.
After the bear had died, the examiner declared it would be a shame to burn the body since it was in good shape.
The body of the Cocaine Bear was then stuffed and gifted to the Chattahoochee River National Recreation Area. Later, it was moved into storage because of an approaching wildfire and was subsequently stolen.
This bizarre story led the search for the bear to Anonymous Outlaw Country Musical, Waylon Jennings, who had apparently bought the stuffed bear at a pawn shop and gifted it to his friend, Ron Thompson.
After Thompson died, much of his estate was put up for auction, which is when the owners of the Kentucky mall stepped in to see if they could get it – and it’s been there ever since.
just found out that not only is the cocaine bear story real, but it happened in Tennessee AND the cocaine bear is supposedly on display at a mall in Kentucky pic.twitter.com/dRD7pFEIoJ
— em (@neuroticgemini) February 24, 2023
Where to watch Cocaine Bear right now
Cocaine Bear was released on Friday, February 24, 2023, and the only place you can currently watch the movie during its premiere will be in your local theatre.
Cinema exclusive releases can stay in theatres anywhere between 14-90 days, depending on their popularity.
Universal Pictures is distributing Cocaine Bear, therefore, the dark comedy will follow the pattern of past Universal releases and come to streaming service Peacock approximately eight weeks after its cinema debut, estimating its streaming date to be somewhere in mid-to-late April.
The movie will then arrive on Amazon Prime Video sometime in August 2023, four months after its Peacock release.
Unfortunately, Cocaine Bear will not be available to stream on Netflix, Disney Plus, or HBO Max at any point.
By Jo Craig – jo.craig@grv.media
Cocaine Bear is now in theatres worldwide.
The post The real Cocaine Bear taxidermy statue is in Kentucky appeared first on ForeverGeek.
CISO’s Guide to Ransomware

The job of a Chief Information Security Officer (CISO) is never truly done. Just as soon as one threat is neutralized and mitigating controls have been put in place, some industrious cybercriminal finds a new way to make life miserable.
Even those of us working in information technology aren’t immune to these attacks. For example, Coinbase recently shared lessons learned from a phishing attempt on one of their employees. No customer account information was compromised, but the incident goes to show that “anyone can be social engineered.”
Coinbase took the right approach by assuming they’d be attacked and understanding that humans make mistakes, even the most diligent among us. In sharing what they learned, they make the whole community more aware. A rising tide lifts all boats, as they say. In that spirit, I’m sharing some of the lessons I’ve learned over the course of my career as a CISO that might help you be better prepared for the inevitable cyberattack.
Read on for best practices you can follow to mitigate your ransomware risk.
- Ransomware: How to Prevent or Recover From an Attack
- Introducing the Ransomware Economy
- Object Lock 101: Protecting Data From Ransomware
- The True Cost of Ransomware
- 2021 Ransomware Takeaways: Q1, Q2, Q3, Q4
- 2022 Ransomware Takeaways: Q1, Q2, Q3
And, don’t forget that we offer a thorough walkthrough of ways to prepare yourself and your business for ransomware attacks—free to download below.
Ransomware Prevention, Detection, Mitigation, and Recovery Best Practices
The best way to address the threat of ransomware is to reduce the likelihood of a successful attack. First, help your employees through training and mitigating controls:
- User Training: Making sure end users are savvy enough to spot a malicious email will ensure that you get fewer well-intentioned folks clicking on links. Things like phishing simulations can train users not to click on suspicious links or download unexpected attachments. While training is the first line of defense, you can’t rely on it alone. Even gold standard security training companies have been hit with successful phishing attacks.
- Endpoint Detection and Response: An endpoint detection and response (EDR) tool can provide additional guardrails. Backblaze leverages EDR to help block and quarantine malicious payloads as they attempt to execute on the workstation.
- Multifactor Authentication: Password strength can be weak, and people often reuse passwords across websites, so another essential component is multifactor authentication (MFA). If you click on a phishing link, or a cybercriminal gains privileged access to your system through some other means, they may be able to retrieve your account password from memory using readily available tools like Mimikatz on Windows or dscl on a Mac. MFA in the form of a logical or physical token, provides for an additional authentication credential that is random, and changes after a brief period of time.
- Limiting Applications: Only allowing authorized applications to be installed by users, either through operating system configuration or third-party software, can help limit what employees can download. Be sure that people aren’t permitted to install applications that may open up additional vulnerabilities.
In addition to helping end users from falling for phishing, there are some best practices you can implement on your systems, network, and backend to reduce vulnerabilities as well.
- Implement a Strong Vulnerability Management Program: A robust program can help you reduce your overall risk by being proactive in identifying and remediating your vulnerabilities.
- Conduct Static Analysis Security Tests: These focus on looking for vulnerabilities in source code.
- Perform Dynamic Application Security Tests: These look for vulnerabilities in running applications.
- Execute Software Composition Analysis Security Tests: These can focus on enumerating and identifying vulnerabilities in versions of the third-party libraries and frameworks leveraged by your application.
- Engage Third Parties to Conduct Penetration Testing: Third parties can discover weaknesses in your systems that your own team may miss.
- Implement a Bug Bounty Program: Security researchers are incentivized to find security vulnerabilities in your application through bug bounty program rewards.
- Stay on Top of Your Patching Cadence: Test and deploy system and application updates as soon as possible, but also have a rollback strategy in the event of a bad patch.
- Implement Least Privilege: Users and programs/processes should only have the privileges they need to accomplish their tasks.
- Use Standard User Accounts for Non-Admin Tasks: Admins can fall for the same types of phishing attacks as any other user. Using a regular non-admin account to read email, browse the web, etc., can help protect the admin from drive-by downloads, phishing, ransomware, and other forms of attack.
- Segment Your Network: Implement physical separation, virtual local area networks (VLAN), and/or microsegmentation to limit what a server or device is able to communicate with.
Finally, stay up to date on guidance from sources such as the White House, the National Institute of Standards and Technology (NIST), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA). The FBI and CISA also issued holiday and weekend ransomware advisories after a pattern of increased attacks was observed during those periods.
Responding If an Attack Slips Through
Realistically, attacks may slip through, and smart CISOs work from that assumption (and assume breach mindset).
Limiting the Blast Radius
As I mentioned during a 2021 SpiceWorld presentation, limiting the blast radius is key. When you’re experiencing a ransomware attack, you also want to isolate the infected system before the ransomware can attempt to access and encrypt other files on network shares. Once it has been isolated, you can investigate whether or not the ransomware has spread to other systems, collect digital forensics, wipe the system, reimage the system, restore the data from backup, and block the command and control IP addresses while monitoring the network to see if other systems attempt to communicate with those IP addresses.
Restoring Your Data
Once you have identified and remediated the root cause of the compromise, you can restore the data from backup after making sure that the backup doesn’t contain the malware you just cleaned up.
Of course, you can only back up if you’ve planned ahead. If you haven’t, you now have a difficult choice.
Should I Pay?
That really depends on what you have done to prepare for a ransomware attack. If you have backups that are disconnected, there’s a high likelihood you will be able to successfully recover to a known good state. It’s in everybody’s best interest not to pay the ransom, because it continues to fuel this type of criminal activity, and there’s no guarantee that any decrypter or key that a cybercriminal gives you is going to unlock your files. Ransomware, like any other code, can contain bugs, which may add to the recovery challenges.
There is, of course, cyber insurance, but you should know that organizations that have been hit are likely to pay higher premiums or have a more difficult time securing cyber insurance that covers ransomware.
Planning for a Fast Recovery
It is important to have a robust recovery plan, and to practice executing the plan. Some elements of a strong recovery plan include:
- Train and Test Your Team: Regularly test your plan and train those with incident response and recovery responsibilities on what to do if and when an incident occurs. Tensions are high when an incident occurs, and regular testing and training builds muscle memory and increases familiarity so your team knows exactly what to do.
- Plan, Implement, and Test Your Backups: Ensure that you have immutable backups that cannot be compromised during an attack. Test your restore process frequently to ensure backups are working properly. Focus on your data most importantly, but also your system images and configurations. Have a solid change management process that includes updating the system images and configuration files/scripts.
- Know Who to Call: Maintain a list of internal and external contacts, so you know who to contact within your organization.
- Establish Relationships With Law Enforcement: Building relationships with your local FBI field office and local law enforcement before an attack goes a long way toward being able to take the steps required to recover quickly from a ransomware attack while also collecting legally defensible evidence. Sharing indicators of compromise with the FBI or other partner law enforcement agencies may help with attribution and (later) prosecution efforts.
Don’t Be a Soft Target
Ransomware continues to cause problems for companies large and small. It’s not going away anytime soon. Cybercriminals are also targeting backups and Windows Shadow Volumes as part of their attacks. As a backup provider, of course, we have some thoughts on tools that can help, including:
Object Lock: Object Lock provides the immutability you need to know your backups are protected from ransomware. With Object Lock, no one can modify or delete your data, including cybercriminals and even the person who set the lock.
Instant Recovery in Any Cloud: Integrated with Veeam, this solution gives you your data back with a single command.
The reality is that attacks happen all the time, but you can take steps to prepare, prevent, respond to, and then recover from them in a way that doesn’t take your business down for weeks or months.
The post CISO’s Guide to Ransomware appeared first on Backblaze Blog | Cloud Storage & Cloud Backup.
Microsoft Security Experts discuss evolving threats in roundtable chat
Get an in-depth recap of the latest Microsoft Security Experts Roundtable, featuring discussions on trends in global cybercrime, cyber-influence operations, cybersecurity for manufacturing and Internet of Things, and more.
The post Microsoft Security Experts discuss evolving threats in roundtable chat appeared first on Microsoft Security Blog.
LastPass Reveals Second Attack Resulting in Breach of Encrypted Password Vaults
AI Could Be Made Obsolete by 'Biocomputers' Running on Human Brain Cells - CNET
Huge Oblivion and Skyrim mods bring old yet new games to GOG

Two colossal total conversions for Elder Scrolls games Oblivion and Skyrim are now available on GOG for free, as the classic Bethesda RPG games never seem to go out of style. While both mods are free, they do require that you own Skyrim and Oblivion respectively, and each is a brilliant way to shake up the games if you missed them the first time around.
‘Hackers’ Behind Air Raid Alerts Across Russia: Official
Russian authorities said that several television and radio stations that have recently broadcast air raid alerts had been breached by hackers.
The post ‘Hackers’ Behind Air Raid Alerts Across Russia: Official appeared first on SecurityWeek.
11 Ways to Make a Frozen Pizza Less Sad

Eating a frozen pizza for supper can feel a little like giving up, but you can’t deny the convenience factor, nor the nostalgic, juvenile appeal. It is, after all, still pizza.
I would never judge or belittle someone for enjoying their freezer pizza au naturel, but a little adornment can do wonders for them. Here are…
Vulnerabilities Being Exploited Faster Than Ever: Analysis
The time from vulnerability disclosure to exploitation is decreasing, according to a new intelligence report from Rapid7.
The post Vulnerabilities Being Exploited Faster Than Ever: Analysis appeared first on SecurityWeek.
Deus Ex Community Update Version 2.4.2
Deus Ex Community Update 2.4.2 - 7Zip SFX to Winzip SFX Change
Resident Evil 5 February 28th Update completely removes GFWL, adds support for local co-op
Now here is something unexpected. After almost eight years, Capcom released a new patch for Resident Evil 5 that removes its Games for Windows Live support. Furthermore, this latest update adds support for local split-screen co-op. Now in case you weren’t aware, the Steam version of Resident Evil 5 did not utilize GFWL. However, Capcom … Continue reading Resident Evil 5 February 28th Update completely removes GFWL, adds support for local co-op →
The post Resident Evil 5 February 28th Update completely removes GFWL, adds support for local co-op appeared first on DSOGaming.
US Marshals Service Suffers 'Major' Security Breach That Compromises Sensitive Information
Read more of this story at Slashdot.
Release: Enderal: Forgotten Stories and Nehrim: At Fate's Edge alongside their soundtracks and Mad Restaurant People from SureAI
Do you love TES IV: Oblivion and TES V: Skyrim? Now that’s an obvious question. And how about their standalone, total conversion mods created by SureAI and available to claim for free for every owner of the respective TES titles?
We’re incredibly happy to announce that both Enderal: Forgotten Stories and Nehrim: At Fate's Edge, alongside their soundtracks and another awesome title from SureAI – Mad Restaurant People, are now all available on GOG!
But let’s unpack all of this awesome news one by one!
Enderal: Forgotten Stories and Nehrim: At Fate's Edge are gems both created non-commercially by SureAI studio. These standalone mods are available to claim for free for every owner of respective TES titles on GOG – TES V: Skyrim for Enderal: Forgotten Stories and TES IV: Oblivion for Nehrim: At Fate's Edge (no DLCs are necessary in both cases). But if you’d like to support awesome developers of SureAI, you can do so by purchasing Enderal and Nehrim’s soundtracks or their Mad Restaurant People title, which we will cover in just a second.
Enderal: Forgotten Stories is a total conversion mod for TES V: Skyrim that is set in its own world with its own lore and story. It offers an immersive open world, all for the player to explore, overhauled skill systems and gameplay mechanics and a dark, psychological storyline with believable characters.
Since its release Enderal gathered extremely positive reviews from both players and critics. The game takes place in the world of the titular Enderal, a land beset by conflict and turmoil. The player takes on the role of a protagonist who is plagued by recurring nightmares and visions, and must embark on a journey to uncover the truth behind their mysterious affliction.
It offers deep and immersive storytelling with a rich and complex narrative that explores themes of loss, identity, and redemption. It is full of memorable characters, unexpected twists, and emotional moments. Unique and challenging gameplay with a revamped leveling system, new combat mechanics, and a variety of quests and side missions that offer a high degree of choice and consequence, as well as stunning visuals and a hauntingly beautiful soundtrack that help to create a truly atmospheric experience is all that we can expect in this outstanding modification.
In addition, its two amazing soundtracks: Enderal: The Bard Songs and Enderal: The Shards of Order Soundtrack are also available to claim for free on GOG!
Nehrim: At Fate's Edge is the predecessor of Enderal: Forgotten Stories, being a total conversion mod for TES IV: Oblivion, featuring its own unique story, world, characters, and gameplay mechanics. The game takes place in the world of Nehrim, a land on the brink of destruction. The player takes on the role of a protagonist who is thrust into a world of political intrigue, ancient prophecies, and supernatural threats, and must navigate through a complex web of alliances and betrayals to uncover the truth behind their own destiny.
It provides a complex and well-written narrative that explores themes of power, religion, and morality, and just as Enderal, it is filled with memorable characters, plot twists, moral dilemmas and challenging gameplay. Gorgeous audiovisuals, unique leveling system, new combat mechanics, and a variety of quests all add up to an incredible gaming experience.
As mentioned before, you can support SureAI’s developers by purchasing Enderal: Forgotten Stories Soundtrack and Nehrim: At Fate's Edge Soundtrack. They are both now available on GOG and discounted -20% until March 13th, 2 PM UTC. And if you’d like to grab both of them together, you can do so with The Music of Vyn (with -25% discount until March 13th, 2 PM UTC). 
Moreover, Mad Restaurant People – SureAI’s awesome time management memory game full of fun and chaos is now also available on GOG with a -20% launch discount which lasts until March 13th, 2 PM UTC.
In this title you’ll progress your career as a server by using your keen perception, your short-term memory and your ability to decide quickly. Fancy and unique places will hire you as you master challenges, unlock perks and stay calm even in the weirdest situations.
You’ll start in an ordinary diner with a small number of tables, dishes and drinks. Customers will appreciate your swiftness with happiness and tips. Each time you unlock a new level, you’ll be able to prove your skills in a more exciting new location, until your reputation as a perfect server will spread into space.
So there you have it! We’re super glad that SureAI’s amazing work has joined our catalog. Make sure to check Enderal and Nehrim out and see for yourself why they are so highly-praised. And don’t worry if you do not own TES IV: Oblivion or TES V: Skyrim yet – there’s a Bethesda’s Publisher Sale up and running right now, meaning you can get Oblivion on a -75% discount and Skyrim Anniversary Edition on a -60% discount. The sale lasts until March 6th, 11 PM UTC, so grab your favorite Bethesda’s titles now!
Metal Gear Solid 2 HD Remaster is already available on PC via emulation
A lot of rumors have surfaced these past few months, suggesting that Konami may be working on a Metal Gear Solid Collection. However, PC gamers can already experience an HD Remaster of Metal Gear Solid 2: Substance thanks to the Playstation 2 emulator, PCSX2. A few days ago, ‘NoBigDeal La’ shared the following video, showcasing … Continue reading Metal Gear Solid 2 HD Remaster is already available on PC via emulation →
The post Metal Gear Solid 2 HD Remaster is already available on PC via emulation appeared first on DSOGaming.
Amazon Removes Books From Kindle Unlimited After They Appear On Pirate Sites
Read more of this story at Slashdot.
LastPass Says DevOps Engineer Home Computer Hacked
LastPass DevOp engineer's home computer hacked and implanted with keylogging malware as part of a sustained cyberattack that exfiltrated corporate data from the cloud storage resources.
The post LastPass Says DevOps Engineer Home Computer Hacked appeared first on SecurityWeek.
But Have You Read The Book? Review: TCM Presents An Insightful Look At 52 Great Movie Adaptations
Few pop culture conversations feel more uninspired to me than those that start with the assertion that "the book is always better." Despite the fact that this platitude about the shortcomings of on-screen adaptations is ubiquitous, adorning countless Instagram posts and Etsy T-shirts, it's frankly not true. Film is a different medium than literature, and visual stories can often expand upon and even interrogate the texts on which they're based. The well-curated, richly researched new book "But Have You Read The Book?" from TCM and The Wrap's film editor Kristen Lopez recognizes this, and in turn starts a series of much more inspired and nuanced conversations. Sometimes, Lopez communicates through the text's 52 examples, the book and the film are both excellent, and their differences are complementary and intriguing.
In keeping with the tradition of other Turner Classic Movies-branded books like Jeremy Arnold's "The Essentials," "But Have You Read The Book?" divides its 239 pages into 52 neat sections, with exactly enough titles to fuel a year-long weekly watchlist. The book is a brisk read thanks to its short essay structure, plus Lopez's accessible but efficient and fact-packed prose. "But Have You Read The Book?" isn't a spoiler-free primer on some of Hollywood's most indelible adaptations, but a wide-ranging survey that digs surprisingly deep into the themes, performances, and even historical context surrounding movies like Alfred Hitchcock's "Rebecca" and Francis Ford Coppola's "The Godfather."
A Richly Researched Survey Of Page And Screen

The author's close comparison between page and screen offers up plenty of insights about each individual adaptation, but the book shines in large part due to Lopez's extensive incorporation of Hollywood history. As the book works its way through time, patterns emerge, with the self-imposed censorship guidelines known as the Hays Code and studios' stubborn interest in marketability popping up as two recurring factors that often lead to major shifts from page to script. Fascinating fun facts abound, often shared in sidebar blurbs, and a series of striking blue illustrations from Jyotirmayee Patra — a bowler hat here for "A Clockwork Orange," a mosquito trapped in amber there for "Jurassic Park" — decorate many entries.
The book's greatest strength is its curation. Its 52 titles include expected favorites, like "Frankenstein" and "The Hunger Games," but the book also takes care to touch upon many stories that center women, people of color, and queer characters, casually canonizing films that are all too often left out of the coffee table film book syllabus. Books built around pop culture lists are often mind-numbingly homogenized, but Lopez and TCM seem to care much less about whether an adaptation is popular (there's no "Harry Potter" or "Twilight" to be found here) than about whether it's actually significant or interesting. To that end, the book includes several surprising but delightful additions, like modern Jane Austen riff "Clueless" and Rebecca Hall's excellent adaptation of Nella Larsen's "Passing."
Exceptional Curation Sets The Book Apart

All in all, it's a satisfying cross-section of genres and time periods, one that gives equal space to noir films, rom-coms, horror movies, dramas, and more. The book also side-steps these types of tomes' frequent penchant for recency bias in order to spend nearly half its time exploring pre-'80s films, and makes the early days of Hollywood come alive on the page through brief-but-lively behind-the-scenes anecdotes about the production of several classic films. Lopez and TCM's compelling programming lineup does leave something to be desired, though, when it comes to international film and literature. "But Have You Read The Book?" is centered squarely on American and British films, and suffers a bit for the glaring omission of great works outside the Western canon. Some entries about milestone movies that come with complex cultural discourses, like "The Color Purple" and "The Joy Luck Club," also seem too nuanced to effectively pare down into just a few hundred words.
Despite these few shortcomings, "But Have You Read The Book?" is a great read, one that takes a basic listicle-like format and turns it into an impressively entertaining and erudite collection of essays. The book's subtitle is "52 Literary Gems That Inspired Our Favorite Films," but Lopez is frank about which books do and don't hold up, pointing out the "unrepentant and prominent" racism on display in Ernest Hemingway's "To Have and To Have Not" while heralding Michael Crichton's "Jurassic Park" as a masterpiece. In the end, "But Have You Read The Book?" does its job well: it's the kind of read that'll leave you running to both your reading list and your watchlist to add several titles to the top.
Read this next: The Best Movies Of 2022
The post But Have You Read the Book? Review: TCM Presents An Insightful Look At 52 Great Movie Adaptations appeared first on /Film.
Building a Retro Linux Gaming Computer - Part 27: Lost Souls
The Outer Worlds: Spacer's Choice Edition brings moving foliage and 4K 60fps to space next week

Late last year game voted Most Likely To Make Me Accidentally Say The Name Of A Different Game and neo-old-school space RPG The Outer Worlds was rated for a mysterious Spacer's Choice Edition. Obsidian are now ready to officially reveal said wash and brush up, which is coming next week on March 7th, and bundles both DLCs for the game with remaster-y improvements to AI, VFX and technical art. To mark the occasion I got to chat with co-directors Leonard Boyarsky and Tim Cain, and producer Eric DeMilt, all of whom who made games that are stastistically likely to number among your favourites - especially if you like RPGs.




