The post Last Light S01 1080p WEB h264-KOGi appeared first on SceneSource.
Ronald.phillips
Shared posts
Wedding Season S01 720p DSNP WEB-DL DDP5 1 H 264-KiNGS
The post Wedding Season S01 720p DSNP WEB-DL DDP5 1 H 264-KiNGS appeared first on SceneSource.
Quentin Tarantino Gave Michael Madsen An Ultimatum After His Reservoir Dogs Audition

"Reservoir Dogs," Quentin Tarantino's directorial debut, was indicative of his career to come. It has his trademark snappy dialogue, hyperviolence, and questionable utterance of racial slurs. All it needs is extensive shots of a woman's bare feet, and you'd have a good predictor of Tarantino's entire oeuvre.
Now, despite my snarky dressing-down of Tarantino's artistic stylings, I do thoroughly enjoy his movies, and "Reservoir Dogs" is one of his strongest films, despite being his earliest and cheapest to produce. It's perhaps the shoestring budget and simplicity of the film that gives it its charm, allowing the writing and directing to shine above all else.
Another of Tarantino's great strengths as a filmmaker is his casting. "Reservoir Dogs" is no different, with the film featuring incredible work from fantastic actors such as Steve Buscemi and Harvey Keitel. For Michael Madsen, who portrayed Mr. Blonde in the film, the role was his big breakout performance. After a string of bad luck and bad decisions, Tarantino's request for Madsen to act in his debut film was a golden opportunity for the actor. Of course, he had to meet the demands of the somewhat tyrannical Tarantino in order to gain the role, which was not even the role he initially wanted, according to a 2016 piece by The Independent.
Go Blonde Or Go Home

"Reservoir Dogs," which was heavily inspired by the French neo-noir "Le Doulos," focuses on the aftermath of a heist gone wrong, and the stand-off between the accomplices of the heist in their designated safehouse. Wanting to keep their true identities secret for the purpose of their criminal undertaking, none of the characters go by their true names. They all go by the names of various colors, like "Mr. Pink," "Mr. Black," and "Mr. Orange."
Madsen was always pegged by Tarantino to play Mr. Blonde, the most unhinged and murderous of the band of scoundrels, according to The Independent. But Madsen, upon reading the script, had other designs in mind. "I wanted to play Mr. Pink," Madsen said, referring to the role that was played immaculately by Steve Buscemi. "Because he had more scenes with Harvey Keitel."
Wanting to perform with the legendary Keitel is an understandable desire, but Tarantino wasn't having it. "I made my case for playing Mr Pink, and Quentin said:
"'Okay, show me what you got.' For one of the only times in my life I'd rehearsed the dialogue, so I did a couple of Mr Pink scenes. When I was done, Quentin looked at me and went: 'Is that it? Okay, good. You're not Mr Pink. You're Mr Blonde -- and if you're not Mr Blonde, then you're not in the movie.'"
The Blonded Life

"Reservoir Dogs" was a critical hit, and Madsen acted the hell out of his role. His performance in the scene where Mr. Blonde tortures a kidnapped police officer to the tune of Stealers Wheel's "Stuck In The Middle With You" is legendary, inspiring homages in shows like "The Simpsons" and "It's Always Sunny in Philadelphia." The movie received such acclaim that Tarantino at one point considered remaking it as his final film, just to "recapture the moment" of the making of the film.
Additionally, Tarantino loves to cast the same actors over and over. This hiring practice landed Michael Madsen additional roles in future Tarantino joints such as the "Kill Bill" films, "The Hateful Eight," and even a cameo in "Once Upon a Time In Hollywood".
Despite their slightly adversarial first impressions, Madsen seems to still enjoy working with Tarantino, even after all these years. "Quentin is just as excited and charged up as he was when we were doing 'Reservoir Dogs,'" said Madsen, in an interview with The National Post. "He's still like a big kid who has giant toy box and he loves it."
With Tarantino partially to thank for his long career as an actor, you have to imagine Madsen is pretty thankful for the opportunity. He surely does not regret his decision to take the role Tarantino envisioned for him. Like many performers before him, Madsen decided to go blonde. And in the long run, he probably did end up having more fun.
Read this next: The 23 Best Heist Movies Of All Time
The post Quentin Tarantino Gave Michael Madsen An Ultimatum After His Reservoir Dogs Audition appeared first on /Film.
AMD FSR 2.1 has arrived to improve graphics card upscaling
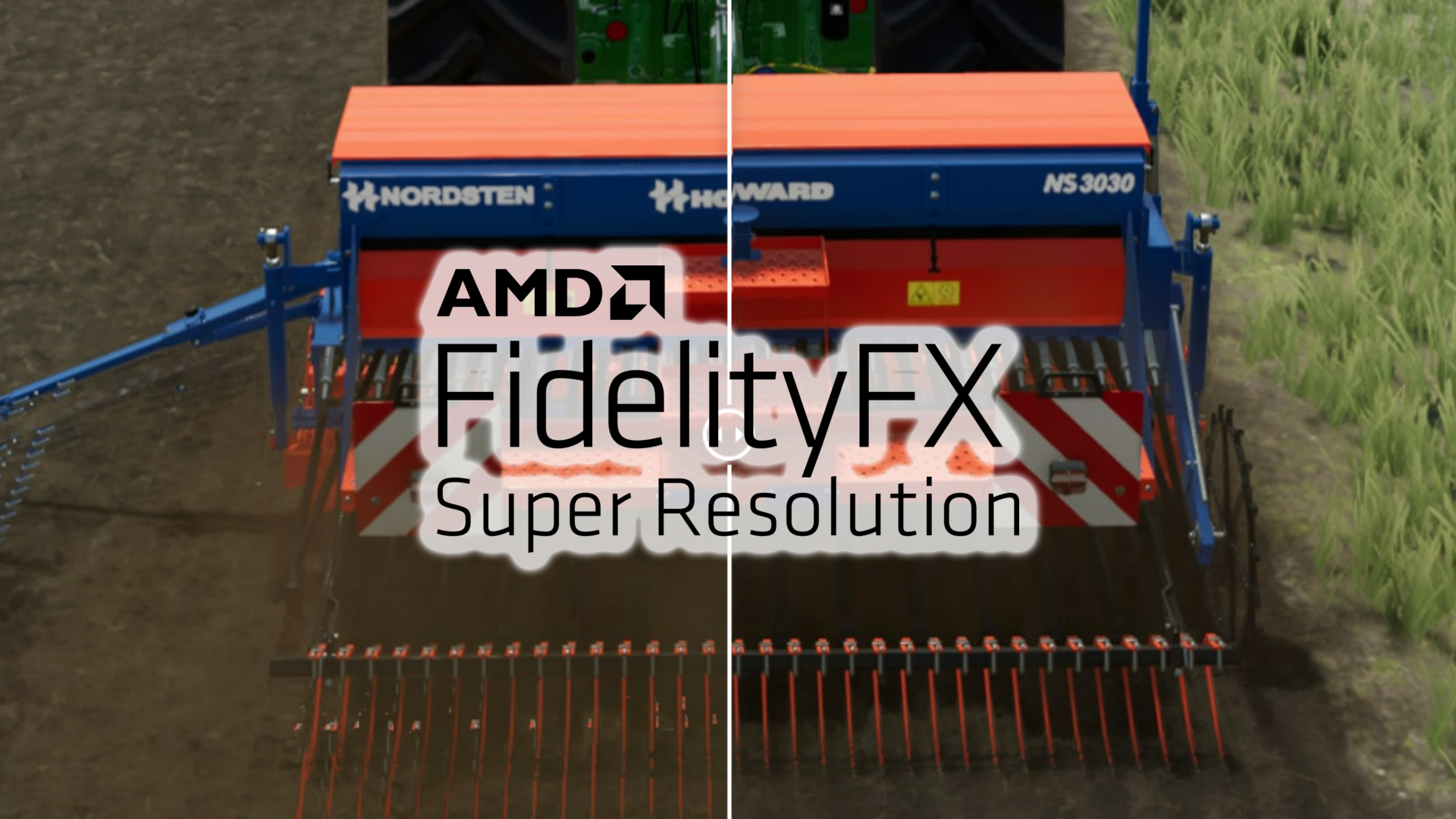
AMD just announced FSR 2.1, a major FidelityFX Super Resolution update that'll boost graphics card upscaling capabilities. The new version of the Nvidia DLSS competitor aims to refine the tool by improving temporal stability and alleviating ghosting, both of which will help games look great at higher resolutions without sacrificing frame rate.
RELATED LINKS: Ryzen 7000 CPUs - everything we know, RDNA 3 GPUs - everything we know, Best gaming CPUMicrosoft investigates Iranian attacks against the Albanian government
Shortly after the destructive cyberattacks against the Albanian government in mid-July, the Microsoft Detection and Response Team (DART) was engaged by the Albanian government to lead an investigation into the attacks. At the time of the attacks and our engagement by the Albanian government, Microsoft publicly stated that “Microsoft is committed to helping our customers be secure while achieving more. During this event, we quickly mobilized our Detection and Response Team (DART) to help the Albanian government rapidly recover from this cyber-attack. Microsoft will continue to partner with Albania to manage cybersecurity risks while continuing to enhance protections from malicious attackers.” This blog showcases the investigation, Microsoft’s process in attributing the related actors and the observed tactics and techniques observed by DART and the Microsoft Threat Intelligence Center (MSTIC) to help customers and the security ecosystem defend from similar attacks in the future.
Microsoft assessed with high confidence that on July 15, 2022, actors sponsored by the Iranian government conducted a destructive cyberattack against the Albanian government, disrupting government websites and public services. At the same time, and in addition to the destructive cyberattack, MSTIC assesses that a separate Iranian state-sponsored actor leaked sensitive information that had been exfiltrated months earlier. Various websites and social media outlets were used to leak this information.
There were multiple stages identified in this campaign:
- Initial intrusion
- Data exfiltration
- Data encryption and destruction
- Information operations
Microsoft assessed with high confidence that multiple Iranian actors participated in this attack—with different actors responsible for distinct phases:
- DEV-0842 deployed the ransomware and wiper malware
- DEV-0861 gained initial access and exfiltrated data
- DEV-0166 exfiltrated data
- DEV-0133 probed victim infrastructure
Microsoft uses DEV-#### designations as a temporary name given to an unknown, emerging, or a developing cluster of threat activity, allowing MSTIC to track it as a unique set of information until we reach a high confidence about the origin or identity of the actor behind the activity. Once it meets the criteria, the DEV reference is converted to a named actor:
Microsoft assessed with moderate confidence that the actors involved in gaining initial access and exfiltrating data in the attack are linked to EUROPIUM, which has been publicly linked to Iran’s Ministry of Intelligence and Security (MOIS) and was detected using three unique clusters of activity. We track them separately based on unique sets of tools and/or TTPs; however, some of them may work for the same unit.
Information specific to Albania is shared with permission from the Albanian government.

Forensic analysis
Evidence gathered during the forensic response indicated that Iran-affiliated actors conducted the attack. This evidence includes, but is not limited to:
- The attackers were observed operating out of Iran
- The attackers responsible for the intrusion and exfiltration of data used tools previously used by other known Iranian attackers
- The attackers responsible for the intrusion and exfiltration of data targeted other sectors and countries that are consistent with Iranian interests
- The wiper code was previously used by a known Iranian actor
- The ransomware was signed by the same digital certificate used to sign other tools used by Iranian actors
Intrusion and exfiltration
A group that we assess is affiliated with the Iranian government, DEV-0861, likely gained access to the network of an Albanian government victim in May 2021 by exploiting the CVE-2019-0604 vulnerability on an unpatched SharePoint Server, administrata.al (Collab-Web2.*.*), and fortified access by July 2021 using a misconfigured service account that was a member of the local administrative group. Analysis of Exchange logs suggests that DEV-0861 later exfiltrated mail from the victim’s network between October 2021 and January 2022.
DEV-0861 was observed operating from the following IPs to exfiltrate mail:
- 144[.]76[.]6[.]34
- 176[.]9[.]18[.]143
- 148[.]251[.]232[.]252
Analysis of the signals from these IPs, and other sources, indicated that DEV-0861 has been actively exfiltrating mail from different organizations in the following countries since April 2020:

The geographic profile of these victims—Israel, Jordan, Kuwait, Saudi Arabia, Turkey, and the UAE—aligns with Iranian interests and have historically been targeted by Iranian state actors, particularly MOIS-linked actors.
DEV-0166 was observed exfiltrating mail from the victim between November 2021 and May 2022. DEV-0166 likely used the tool Jason.exe to access compromised mailboxes. A public analysis of Jason.exe can be found here. Note that this tool was reportedly used by actors affiliated with MOIS.

Ransomware and wiper
The cyberattack on the Albanian government used a common tactic of Iranian state sponsored actors by deploying ransomware first, followed by deployment of the wiper malware. The wiper and ransomware both had forensic links to Iranian state and Iran-affiliated groups. The wiper that DEV-0842 deployed in this attack used the same license key and EldoS RawDisk driver as ZeroCleare, a wiper that Iranian state actors used in an attack on a Middle East energy company in mid-2019. In that case, IBM X-Force assessed that actors affiliated with EUROPIUM gained initial access nearly a year ahead of the wiper attack. The wiper attack was subsequently performed by a separate and unknown Iranian actor. This is similar to the chain of events Microsoft detected against the Albanian government.
The code used in this attack had the following properties:
| Filename | SHA-256 |
| cl.exe | e1204ebbd8f15dbf5f2e41dddc5337e3182fc4daf75b05acc948b8b965480ca0 |
| rwdsk.sys | 3c9dc8ada56adf9cebfc501a2d3946680dcb0534a137e2e27a7fcb5994cd9de6 |
Embedded in the cl.exe wiper was the hex-string ‘B4B615C28CCD059CF8ED1ABF1C71FE03C0354522990AF63ADF3C911E2287A4B906D47D,’ which was the same license key used for the EldoS RawDisk driver of the ZeroCleare wiper documented by IBM X-Force in 2019. The Eldos driver is a legitimate tool that was also abused by the ZeroCleare wiper and was used to delete files, disks, and partitions on the target systems. While ZeroCleare is not widely used, this tool is being shared amongst a smaller number of affiliated actors including actors in Iran with links to MOIS.
The ransomware payload used in this attack by the DEV-0842 operator had the following properties:
| Filename | SHA-256 |
| GoXml.exe | f116acc6508843f59e59fb5a8d643370dce82f492a217764521f46a856cc4cb5 |
This tool was signed with an invalid digital certificate from Kuwait Telecommunications Company KSC. This certificate had a SHA-1 thumbprint of 55d90ec44b97b64b6dd4e3aee4d1585d6b14b26f.
Microsoft telemetry indicates this certificate was only used to sign 15 other files—a very small footprint, suggesting the certificate was not widely shared amongst unrelated actor groups. Multiple other binaries with this same digital certificate were previously seen on files with links to Iran, including a known DEV-0861 victim in Saudi Arabia in June 2021:
| Filename | SHA-256 |
| Read.exe | ea7316bbb65d3ba4efc7f6b488e35db26d3107c917b665dc7a81e327470cb0c1 |
It’s not clear if Read.exe was dropped by DEV-0861 on this Saudi victim or if DEV-0861 also handed off access to the Saudi victim to DEV-0842.
Additional indications of Iranian state sponsorship
The messaging, timing, and target selection of the cyberattacks bolstered our confidence that the attackers were acting on behalf of the Iranian government. The messaging and target selection indicate Tehran likely used the attacks as retaliation for cyberattacks Iran perceives were carried out by Israel and the Mujahedin-e Khalq (MEK), an Iranian dissident group largely based in Albania that seeks to overthrow the Islamic Republic of Iran.
Messaging
The attacker’s logo is an eagle preying on the symbol of the hacking group ‘Predatory Sparrow’ inside the Star of David (Figure 4). This signals the attack on Albania was retaliation for Predatory Sparrow’s operations against Iran, which Tehran perceives involved Israel. Predatory Sparrow has claimed responsibility for several high-profile and highly sophisticated cyberattacks against Iran state-linked entities since July 2021. This included a cyberattack that disrupted television programming of the Islamic Republic of Iran Broadcasting (IRIB) with images saluting MEK leaders in late January. Predatory Sparrow forewarned about the attack hours ahead of time and claimed they supported and paid for it, indicating others were involved. Iranian officials blamed this cyberattack on the MEK and additionally blamed the MEK and Israel for a cyberattack that used the same images and messaging against the Tehran municipality in June.
The message in the ransom image indicates that the MEK, a long-standing adversary of the Iranian regime, was the primary target behind their attack on the Albanian government. The ransom image, like several posts by Homeland Justice, the group overtly pushing messages and leaking data linked to the attack, asked “why should our taxes be spent on terrorists of Durres.” This is a reference to the MEK, who Tehran considers terrorists, who have a large refugee camp in Durrës County in Albania.

The messaging linked to the attack closely mirrored the messaging used in cyberattacks against Iran, a common tactic of Iranian foreign policy suggesting an intent to signal the attack as a form of retaliation. The level of detail mirrored in the messaging also reduces the likelihood that the attack was a false flag operation by a country other than Iran.
- The contact numbers listed in the ransom image (Figure 4), for example, were linked to multiple senior Albanian leaders, mirroring the cyberattacks on Iran’s railways and fueling pumps, which included a contact phone number belonging to the Iranian Supreme Leader’s Office.
- The messages in the information operations also emphasized targeting of corrupt government politicians and their support for terrorists and an interest in not harming the Albanian people (Figure 5). Similarly, the attack on Iranian steel companies claimed to target the steel factories for their connections to the Islamic Revolutionary Guard Corps (IRGC) while avoiding harm to Iranians. Another cyberattack on an Iranian airline in late 2021, which was claimed by Hooshyaran-e Vatan (meaning “Observants of the Fatherland” in Farsi), emphasized Tehran’s corruption and misappropriation of money on IRGC activities abroad.

Timing
The cyberattack on July 15 occurred weeks after a string of cyberattacks on Iran, one week ahead of the MEK-sponsored Free Iran World Summit and aligned with other Iranian policy moves against the MEK, further bolstering the likelihood of Iranian involvement. On July 16, the day after the cyberattack, Iran’s Ministry of Foreign Affairs issued a statement designating current and former American politicians for supporting the MEK. The Free Iran World Summit, which the Iranian regime actively opposes, was canceled this year following warnings of possible terrorist threats to the Summit on July 21. A few days after the planned Free Iran World Summit, Iranian official press issued an editorial calling for military action against the MEK in Albania. This string of events suggests there may have been a whole-of-government Iranian effort to counter the MEK from Iran’s Ministry of Foreign Affairs, to intelligence agencies, to official press outlets.
Target selection
Some of the Albanian organizations targeted in the destructive attack were the equivalent organizations and government agencies in Iran that experienced prior cyberattacks with MEK-related messaging. This suggests the Iranian government chose those targets to signal the cyberattacks as a form of direct and proportional retaliation, a common tactic of the regime.
Parallel information operations and amplification
Before and after the Homeland Justice messaging campaign was launched, social media persona accounts and a group of real-life Iranian and Albanian nationals known for their pro-Iran, anti-MEK views, promoted the campaign’s general talking points and amplified the leaks published by the Homeland Justice accounts online. The parallel promotion of the Homeland Justice campaign and its central themes by these entities in the online space—before and after the cyberattack—suggests a broad-based information operation aimed at amplifying the impact of the attack.
Ahead of the cyberattack, on June 6, Ebrahim Khodabandeh, a disaffected former MEK member posted an open letter addressed to Albanian Prime Minister Edi Rama warning of the consequences of escalating tensions with Iran. Invoking “[h]acking of Tehran municipal systems” and “gas stations,” Khodabandeh claimed that the MEK was the source of “sabotaging acts against the interests of the Iranian people [sic]” and argued that these constituted “the hostile work of your government” and has caused “obvious enmity with the Iranian nation [sic].”
Four days later, on June 10, Khodabandeh and the Nejat Society, an anti-MEK NGO that he heads, hosted a group of Albanian nationals in Iran. The group included members of another anti-MEK organization called the Association for the Support of Iranians Living in Albania (ASILA)—Gjergji Thanasi, Dashamir Mersuli, and Vladimir Veis. Given the highly political nature of ASILA’s work on issues related to a group that Tehran considers a terrorist organization (the MEK), it is highly possible that this visit was conducted with sanction from the state. Upon their return from Iran, on July 12, Nejat Society said Albanian police raided their offices and detained some ASILA members. While Nejat Society said this raid was a result of “false and baseless accusations,” according to local media the raid stemmed from possible connections to Iranian intelligence services.

In the wake of the cyberattack, on July 23, Thanasi and Olsi Jazexhi, another Albanian national who frequently appears on Iran’s state-sponsored media outlet PressTV espousing anti-MEK positions, penned a second open letter addressed to then-Albanian President Ilir Meta, also published on Nejat Society’s website. This letter echoed Homeland Justice’s central claim—namely that Albania’s continuing to host the MEK constituted a danger to the Albanian people. Jazexhi and Thanasi called on Meta to convene Albania’s National Security Council to “consider whether Albania has entered into a cyber and military conflict with the Islamic Republic of Iran.”
In May 2021, at around the same time that Iranian actors began their intrusion into Albanian government victim systems, accounts for two anti-MEK social media personas, which do not appear to correspond to real people, were created on both Facebook and Twitter. The accounts largely post anti-MEK content and engage with the social media accounts of some of the individuals detailed above. These two accounts along with a third, older account, were among the first to promote posts from Homeland Justice accounts on Twitter, and all three dramatically increased the rate of anti-MEK posts after the mid-July 2022 cyberattack became public.
There exists some additional evidence that the role of these personas extended beyond mere social media amplification and into content production. One of the personas which repeatedly posted Homeland Justice content had previously written for the now-defunct IRGC-linked American Herald Tribune and other fringe news sites, often in negative terms about the MEK. A second persona account, meanwhile, may have attempted to contact at least one Albanian newspaper ahead of the hack-and-leak, requesting “cooperation”, and the ability to publish with the outlet.
The parallel promotion of the Homeland Justice campaign and its central themes by these individuals and personas online both before and after the cyberattack adds a compelling human dimension to the broader Homeland Justice influence effort. While there were no observed direct relationships between the threat actors responsible for the destructive attack and these messaging actors, their actions raise questions worthy of further examination.
Observed actor activity
DART and MSTIC supported the post ransom and wiper attack analysis leveraging Microsoft 365 Defender and collection of additional forensic artifacts. Analysis identified the use of vulnerabilities to implant web shells for persistence, reconnaissance actions, common credential harvesting techniques, defense evasion methods to disable security products, and a final attempt of actions on objective deploying encryption and wiping binaries. The Iranian sponsored attempt at destruction had less than a 10% total impact on the customer environment.
Access and implant
Based on investigative analysis, starting in May 2021, actors exploited vulnerabilities of a public-facing endpoint to execute arbitrary code that implanted web shells on the unpatched SharePoint server (Collab-Web2.*.*), as stated previously. These generic web shells provided the ability to upload files, download files, delete files, rename, execute commands with an option to run as specific user.

Web shells were placed in the following directories:
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\evaluatesiteupgrade.cs.aspx
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\Pickers.aspx
- C:\ProgramData\COM1\frontend\Error4.aspx
Lateral movement and execution
Following initial access and implant, the threat actor was observed using Mimikatz for credential harvesting and a combination of Impacket and Remote Desktop Clients for lateral movement efforts using the built-in administrator account. Unrecoverable tooling was identified, which highly suggests that reconnaissance efforts were present in the form of file names of executables, resident mailbox data, database, and user details. Similar actions by the threat actors observed by MSTIC and DART detail both custom and open-source tooling utilized for these efforts. Artifacts of tooling identified:
- IPGeter.exe
- FindUser.exe
- recdisc.exe
- NetE.exe
- advanced_port_scanner.exe
- mimikatz.exe
- shared.exe
- Stored CSV and TXT files
Data collection
During the period of October 2021 – January 2022, the threat actors used a unique email exfiltration tool which interacted with the Exchange web services APIs to collect email in a manner that masked the actions. The threat actors accomplished these actions by creating an identity named “HealthMailbox55x2yq” to mimic a Microsoft Exchange Health Manager Service account using Exchange PowerShell commands on the Exchange Servers. The threat actors then added the account to the highly privileged exchange built-in role group “Organization Management” to later add the role of “Application Impersonation”. The ApplicationImpersonation management role enables applications to impersonate users in an organization to perform tasks on behalf of the user, providing the ability for the application to act as the owner of a mailbox.
Defense evasion
Prior to launching the final stage of the attack, the threat actors gained administrative access to a deployed endpoint detection and response (EDR) solution to make modifications, removing libraries that affected the agents across the enterprise. In addition, a binary to disable components of Microsoft Defender Antivirus was propagated using custom tooling. The distributed binary named disable-defender.exe queries for TokenElevation using the GetTokenInformation API and checks if the process is running with elevated privileges. If the token is not running with elevated privilege, the binary prints “Must run as admin!\n”. If the token is elevated, it queries TokenUser and checks if the SID is “S-1-5-18”. If the current process doesn’t run under system context, it prints “Restarting with privileges\n” and attempts to elevate the privilege.
To elevate the privilege, the binary checks if the TrustedInstaller service is enabled. To do this, it starts the service “SeDebugPrivilege” and “SeImpersonatePrivilege” to assign privileges to itself. It then looks for winlogon.exe process, acquires its token, and impersonates calling thread using ImpersonateLoggedOnUser/SetThreadToken. After impersonating as winlogon.exe, it opens TrustedInstaller process, acquires its token for impersonation and creates a new process with elevated privileges using CreateProcessWithTokenW.

Once it successfully creates its own process with TrustedInstaller privilege, it proceeds to disable Defender components.
- Terminates smartscreen.exe
- Modifies WinDefend service to DemandLoad.
- Modifies “TamperProtection” value to 0
- Queries WMI “Root\Microsoft\Windows\Defender” Namespace “MSFT_MpPreference” class for “DisableRealtimeMonitoring”
- Sets “DisableAntiSpyware” value to 1
- Sets “SecurityHealth” value to 3
- Sets “DisableAntiSpyware” value to 0
- Sets “SYSTEM\CurrentControlSet\Services\WinDefend” service “Start” value to 3
- Sets “DisableRealtimeMonitoring” value to 1
- Modifies further settings using WMI “Root\Microsoft\Windows\Defender” Namespace “MSFT_MpPreference” class values,
- “EnableControlledFolderAccess”
- “PUAProtection”
- “DisableRealtimeMonitoring”
- “DisableBehaviorMonitoring”
- “DisableBlockAtFirstSeen”
- “DisablePrivacyMode”
- “SignatureDisableUpdateOnStartupWithoutEngine”
- “DisableArchiveScanning”
- “DisableIntrusionPreventionSystem”
- “DisableScriptScanning”
- “DisableAntiSpyware”
- “DisableAntiVirus”
- “SubmitSamplesConsent”
- “MAPSReporting”
- “HighThreatDefaultAction”
- “ModerateThreatDefaultAction”
- “LowThreatDefaultAction”
- “SevereThreatDefaultAction”
- “ScanScheduleDay”
Additional evasion techniques included the deletion of tooling, Windows events, and application logs.
Actions on objective
Distribution of the encryption and wiping binaries was accomplished with two methods via a custom SMB remote file copy tool Mellona.exe, originally named MassExecuter.exe. The first method remote file copied the ransom binary GoXml.exe and a bat file that triggers the execution of the ransom or wiper on a user login. The second method was by remotely invoking the ransom binary with the Mellona.exe tool, post SMB remote file copy.

win.bat – Batch file for ransom execution – Trojan:Win32/BatRunGoXml
- Executes the ransom binary from the All Users starts up folder and will be executed on the trigger of a user login.

GoXml.exe – ransomware binary – Ransom:Win32/Eagle!MSR
- Takes >= 5 arguments, and the arguments can be anything, as it looks for argument count only. If the number of the command line arguments is less than 5, it will error and create an Open dialog box via GetOpenFileNameA that lets the user open a *.xml file
- If 5 or more command line arguments were provided, it will firstly check the running instances by opening the Mutex below via OpenMutexA:
“Global\\abcdefghijklmnoklmnopqrstuvwxyz01234567890abcdefghijklmnopqrstuvwxyz01234567890”
- If there are no other running instances, it will create the Mutex above via CreateMutexA.
- Attempts to mount all the volumes:
- Finds available volumes via FindFirstVolumeW and FindNextVolumeW.
- Retrieves the mounted folders of the volume via GetVolumePathNamesForVolumeNameW.
- If there is no mounted point for the volume, creates a new directory named c:\\HD%c (%c is A, B, C, …) via CreateDirectoryW.
- Mounts the volume to the newly create directory via SetVolumeMountPointW.
- Launches cmd.exe and runs the following batch script through anonymous pipe:

- Strings are encrypted with RC4 Algorithm with key “8ce4b16b22b58894aa86c421e8759df3”.
- Generates Key using rand() function and uses that to derive RC4 key to encrypt files. The derived key is then encrypted with Public key hardcoded in the file.
- This encrypted key is then encoded with customized Base64 characters and appended to the ransom note.
- Renames the file as [original file name].lck, and then encrypts the renamed file.
- Drops a ransom notes file named How_To_Unlock_MyFiles.txt in each folder before encrypting the files, the ransom notes are written in Albanian.

- Performs a self-delete by launching cmd.exe and executes a batch script though anonymous pipe to perform deletion.

cl.exe – wiper – Dos:Win64/WprJooblash
-
cl.exe takes the following parameters
- cl.exe in – Installs the driver rwdsk.sys and its service
- cl.exe un – Uninstalls the driver rwdsk.sys and its service
- cl.exe wp <PATH> – Wipes the give path leveraging rwdsk.sys driver

- Service created: HKLM\SYSTEM\CurrentControlSet\Services\RawDisk3
- Installed driver should be located in C:\Windows\System32\drivers\rwdsk.sys or the same directory cl.exe is staged.

- By providing path (Example: \??\PHYSICALDRIVE0) with the ‘wp’ parameter, passes it to the below function including GENERIC_READ | GENERIC_WRITE access value and a hexadecimal value “B4B615C28CCD059CF8ED1ABF1C71FE03C0354522990AF63ADF3C911E2287A4B906D47D”. Based on the reference below, the same hex value is used in ZeroCleare Wiper in 2020. IBM confirms this value is the license key for RawDisk

Recommended customer actions
The techniques used by the actor and described in the Observed actor activity section can be mitigated by adopting the security considerations provided below:
- Use the included indicators of compromise to investigate whether they exist in your environment and assess for potential intrusion
- Block inbound traffic from IPs specified in the Indicators of compromise table
- Review all authentication activity for remote access infrastructure, with a particular focus on accounts configured with single factor authentication, to confirm authenticity and investigate any anomalous activity
- Enable multifactor authentication (MFA) to mitigate potentially compromised credentials and ensure that MFA is enforced for all remote connectivity
NOTE: Microsoft strongly encourages all customers download and use password-less solutions like Microsoft Authenticator to secure your accounts - Enable Microsoft Defender Antivirus tamper protection to prevent unwanted malicious apps disabling components of Microsoft Defender Antivirus
- Understand and assess your cyber exposure with advanced vulnerability and configuration assessment tools
Indicators of compromise (IOCs)
The table below shows IOCs observed during our investigation. We encourage our customers to investigate these indicators in their environments and implement detections and protections to identify past related activity and prevent future attacks against their systems.
| Indicator | Type | Description |
| GoXml.exe | SHA-256 | f116acc6508843f59e59fb5a8d643370dce82f492a217764521f46a856cc4cb5 |
| “w.zip”, “cl.exe” “cls5.exe” |
SHA-256 | e1204ebbd8f15dbf5f2e41dddc5337e3182fc4daf75b05acc948b8b965480ca0 |
| Win.bat | SHA-256 | bad65769c0b416bb16a82b5be11f1d4788239f8b2ba77ae57948b53a69e230a6 |
| ADExplorer.exe | SHA-256 | bb45d8ffe245c361c04cca44d0df6e6bd7596cabd70070ffe0d9f519e3b620ea |
| Ldd.2.exe | SHA-256 | e67c7dbd51ba94ac4549cc9bcaabb97276e55aa20be9fae909f947b5b7691e6b |
| Mellona.exe | SHA-256 | ac4809764857a44b269b549f82d8d04c1294c420baa6b53e2f6b6cb4a3f7e9bd |
| Sl.exe | SHA-256 | d1bec48c2a6a014d3708d210d48b68c545ac086f103016a20e862ac4a189279e |
| HxD.exe (Hex Editor) | SHA-256 | d145058398705d8e20468332162964dce5d9e2ad419f03b61adf64c7e6d26de5 |
| Lsdsk.exe | SHA-256 | 1c926d4bf1a99b59391649f56abf9cd59548f5fcf6a0d923188e7e3cab1c95d0 |
| NTDSAudit.exe | SHA-256 | fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b |
| Disable-defender.exe | SHA-256 | 45bf0057b3121c6e444b316afafdd802d16083282d1cbfde3cdbf2a9d0915ace |
| Rognar.exe | SHA-256 | dfd631e4d1f94f7573861cf438f5a33fe8633238d8d51759d88658e4fbac160a |
| Ipgeter.exe | SHA-256 | 734b4c06a283982c6c3d2952df53e0b21e55f3805e55a6ace8379119d7ec1b1d |
| evaluatesiteupgrade.aspx | SHA-256 | f8db380cc495e98c38a9fb505acba6574cbb18cfe5d7a2bb6807ad1633bf2df8 |
| Pickers.aspx | SHA-256 | 0b647d07bba697644e8a00cdcc8668bb83da656f3dee10c852eb11effe414a7e |
| ClientBin.aspx | SHA-256 | 7AD64B64E0A4E510BE42BA631868BBDA8779139DC0DAAD9395AB048306CC83C5 |
| App_Web_bckwssht.dll | SHA-256 | CAD2BC224108142B5AA19D787C19DF236B0D12C779273D05F9B0298A63DC1FE5 |
| C:\Users\<User name>\Desktop\ | Staging directory | |
| C:\ProgramData\ | Staging directory | |
| C:\Users\<User name>\Desktop\a | Staging directory | |
| C:\ProgramData\1\ | Staging directory | |
| C:\ProgramData\2\ | Staging directory | |
| 144[.]76[.]6[.]34 | IP address | Accessed web shell |
| 148[.]251[.]232[.]252 | IP address | Accessed web shell |
| 148[.]251[.]233[.]231 | IP address | Accessed web shell |
| 176[.]9[.]18[.]143 | IP address | Accessed web shell |
| 185[.]82[.]72[.]111 | IP address | Accessed web shell |
| 216[.]24[.]219[.]65 | IP address | Accessed web shell |
| 216[.]24[.]219[.]64 | IP address | Accessed web shell |
| 46[.]30[.]189[.]66 | IP address | Accessed web shell |
NOTE: These indicators should not be considered exhaustive for this observed activity.
Microsoft Defender Threat Intelligence Community members and customers can find summary information and all IOCs from this blog post in the linked Microsoft Defender Threat Intelligence article.
Detections
Microsoft 365 Defender
Microsoft Defender Antivirus
- TrojanDropper:ASP/WebShell!MSR (web shell)
- Trojan:Win32/BatRunGoXml (malicious BAT file)
- DoS:Win64/WprJooblash (wiper)
- Ransom:Win32/Eagle!MSR (ransomware)
- Trojan:Win32/Debitom.A (disable-defender.exe)
Microsoft Defender for Endpoint EDR
Microsoft Defender for Endpoint customers should watch for these alerts that can detect behavior observed in this campaign. Note however that these alerts are not indicative of threats unique to the campaign or actor groups described in this report.
- Suspicious behavior by Web server process
- Mimikatz credential theft tool
- Ongoing hands-on-keyboard attack via Impacket toolkit
- Suspicious RDP connection observed
- Addition to Exchange Organization Management role group
- TrustedInstaller hijack attempt
- Microsoft Defender Antivirus tampering
- Process removed a security product
- Tamper protection bypass
- Suspicious file in startup folder
- Ransomware behavior detected in the file system
- Ransomware behavior by remote device
- Emerging threat activity group
Microsoft Defender Vulnerability Management
Microsoft Defender Vulnerability Management surfaces impacted devices that may be affected by the Exchange (ProxyLogon) and SharePoint vulnerabilities used in the attack:
Advanced hunting queries
Microsoft Sentinel
To locate possible threat actor activity mentioned in this blog post, Microsoft Sentinel customers can use the queries detailed below:
Identify threat actor IOCs
This query identifies a match based on IOCs related to EUROPIUM across various Microsoft Sentinel data feeds:
Identify Microsoft Defender Antivirus detection related to EUROPIUM
This query looks for Microsoft Defender AV detections related to EUROPIUM actor and joins the alert with other data sources to surface additional information such as device, IP, signed-in users, etc.
Identify creation of unusual identity
The query below identifies creation of unusual identity by the Europium actor to mimic Microsoft Exchange Health Manager Service account using Exchange PowerShell commands.
Microsoft 365 Defender
To locate possible threat actor activity mentioned in this blog post, Microsoft 365 Defender customers can use the queries detailed below:
Identify EUROPIUM IOCs
The following query can locate activity possibly associated with the EUROPIUM threat actor. Github link
DeviceFileEvents | where SHA256 in ("f116acc6508843f59e59fb5a8d643370dce82f492a217764521f46a856cc4cb5","e1204ebbd8f15dbf5f2e41dddc5337e3182fc4daf75b05acc948b8b965480ca0","bad65769c0b416bb16a82b5be11f1d4788239f8b2ba77ae57948b53a69e230a6","bb45d8ffe245c361c04cca44d0df6e6bd7596cabd70070ffe0d9f519e3b620ea","d1bec48c2a6a014d3708d210d48b68c545ac086f103016a20e862ac4a189279e","fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b","45bf0057b3121c6e444b316afafdd802d16083282d1cbfde3cdbf2a9d0915ace","f8db380cc495e98c38a9fb505acba6574cbb18cfe5d7a2bb6807ad1633bf2df8","7ad64b64e0a4e510be42ba631868bbda8779139dc0daad9395ab048306cc83c5","cad2bc224108142b5aa19d787c19df236b0d12c779273d05f9b0298a63dc1fe5","84be43f5830707cd421979f6775e9edde242bab98003644b3b491dbc08cc7c3e")
Identify Microsoft Defender Antivirus detection related to EUROPIUM
This query looks for Microsoft Defender Antivirus detections related to EUROPIUM actor. Github link
let europium_sigs = dynamic(["BatRunGoXml", "WprJooblash", "Win32/Eagle!MSR", "Win32/Debitom.A"]); AlertEvidence | where ThreatFamily in~ (europium_sigs) | join AlertInfo on AlertId | project ThreatFamily, AlertId
Identify unusual identity additions related to EUROPIUM
This query looks for identity additions through exchange PowerShell. Github link
DeviceProcessEvents
| where ProcessCommandLine has_any ("New-Mailbox","Update-RoleGroupMember") and ProcessCommandLine has "HealthMailbox55x2yq"
The post Microsoft investigates Iranian attacks against the Albanian government appeared first on Microsoft Security Blog.
The art and science behind Microsoft threat hunting: Part 1
At Microsoft, we define threat hunting as the practice of actively looking for cyberthreats that have covertly (or not so covertly) penetrated an environment. This involves looking beyond the known alerts or malicious threats to discover new potential threats and vulnerabilities.
Why do incident responders hunt?
The Microsoft Detection and Response Team (DART) mission is to respond to security incidents and help our customers become cyber-resilient. This involves incorporating threat hunting as part of our proactive and reactive investigative service offerings to determine the following:
- Whether systems are under targeted exploitation through investigation for signs of advanced implants and anomalous behavior.
- Identifying groundwork for the recovery process of evicting the attacker from the environment.
- Strategic recommendations for protecting against sophisticated threat actors.
In reactive incident response investigations, threat hunting helps determine the full scope of the incident and informs an effective recovery and remediation strategy. In proactive investigations, a threat hunt can discover latent threats or existing compromises as well as demonstrate the effectiveness of current security controls and their security operations processes. By uncovering novel attacker campaigns and previously undetected threats, DART provides valuable feedback to improve product detections, both for Microsoft security products and for the entire security ecosystem.
How do we approach threat hunting?
The canonical definition of threat hunting involves three interrelated things:
- Targeted threat hunting—We define targeted hunting as actively looking for and rooting out cyberthreats that have penetrated an environment, and looking beyond the known alerts or malicious threats to discover new potential threats and vulnerabilities. Targeted threat hunting has a scope where we are looking for specific classes of indicators. For example, given a recently revealed attack, an organization may want to assess its environment to see if it, too, has been affected.
- Security monitoring—Process of continuously monitoring the state of an environment to detect unusual or unauthorized activities. This involves a network operations center (NOC) and an SOC to ensure that networks are protected against disruptions and threats.
- Incident response investigation—An investigation to identify the root cause and develop a remediation plan to regain and retain positive control over the environment following the detection of unauthorized access or suspicious activity.
Each organization approaches threat hunting differently. Sometimes, the customer will have specific outcomes in mind that align with the known techniques. We center on a general approach based on anomaly detection and pivoting combined with a knowledge of the overall environment. This allows us to accomplish multiple goals, versus employing an approach solely focused on a targeted threat hunt where additional threats and risks may be overlooked.
We will go into more detail about hunting for anomalies later in this blog.
Threat hunting principles
Our forensic investigators at DART lean on the Alexiou Principle, which states four key questions for our investigators to answer:
1. What question are you trying to answer?
Threat hunting varies depending on the main objectives or questions that need to be answered. This involves trying to understand a threat actor’s main objective, the cyber terrain in which they operate, and understanding how you can get closer to those objectives. Framing the question clearly helps us define the scope of every threat hunt.
2. What data do you need to answer that question?
To answer the previous question would involve a two-pronged approach with a focus on determining what data is required, and how to obtain that data. During DART investigations, we often get a variety of datasets while entering a customer investigation, such as live feeds and telemetry. We want to pick up everything that is currently in the environment, enumerate directories that we know bad actors like to live in, collect event logs that will potentially show us evidence of historical or current badness, registry keys that we see bad actors like to tamper with, and many more.
We use a tiered data collection model and start by collecting a snapshot of the densest, most indicator-rich data we can from every object and endpoint we can reach. This data is intended to provide information about any known threats, known attack patterns, and many (but not all) indicators of suspicious or anomalous activity. Where systems of interest are identified, we return and collect a larger, more complete dataset of logs and forensic artifacts.
3. How do you extract that data?
Now that you’ve identified the data, you’ll need to capture it using various toolsets, such as a point-in-time snapshot tool or, if the customer doesn’t have one deployed already, an endpoint detection and response tool, such as Microsoft Defender for Endpoint, to obtain the data. From the analytics captured, we can see things that are potentially good, bad, or interesting. Part of this phase also takes data ingestion into account. We consider how the collected data is consumed and how to efficiently separate threats from the background noise of a complex global enterprise.
4. What does the data tell you?
Looking at the collected data now becomes an exercise in data analytics. It’s a question of evaluating prevalence and frequency by taking everything that occurs within an environment and trying to figure out what belongs and what doesn’t belong. This train of thought can take a handful of different forms, that can be something as simple as “How often does this secure hashing algorithm show up across the entire environment?” to a more nuanced and precise way, such as asking “How often does it show up only on domain controllers? On devices in this organizational unit? How about when it’s seen with this other user account?”
As it turns out, there are a lot of different ways for us to do this counting game. Our role as threat hunters is to figure out the most relevant, high-priority way to account for these interesting findings and see if patterns revealed themselves. We’re looking for indicators of attack or compromise that maybe others haven’t found. It all depends on what data is available to us and understanding it.
Understanding the data
We approach understanding the data by looking for anomalies, the current state, and the absence of data.
Where the rubber meets the road: forming the attack narrative
We believe there’s a clear art and science to threat hunting, but at the end of the day, we seek to understand the anomalies in the acquired evidence. One way we do this is by using the knowledge of what is typical in an environment to identify what isn’t. Understanding the typical scenario and marrying that with the knowledge of threat actor tools, techniques, and processes allows us to gain a deep understanding of the data and the systems we’re looking at. Stringing these anomalies together can then create a pattern of anomalies, helping us form a story using analytical opinions based on facts, also known as the attack narrative.
The ability to identify anomalies makes for an important skill set for an analyst, but understanding the current state is just as crucial. Anomaly-based hunting will be discussed in more detail in the second part of this series when we go into general hunting strategies.
Looking at the current state
If an investigator is lucky enough, they might be dealing with forensic data for the anomaly hunt. But often, there will be times when our observations are limited to the current state of the environment. Even if we don’t have the luxury of historical artifacts, looking at the current state can provide valuable information.
Our proactive Cybersecurity Operations Services prior to an incident allow organizations to gain better knowledge of their current security posture and risk exposure before an incident even occurs.
By understanding the current state and its configurations, you can determine where the potentially malicious or anomalous activity lies as an initial starting point.
Asking questions like “How did it get into that state? Was that it in that state intentionally or was that the result of somebody doing something malicious?” allows our investigators to build from something of interest, look a little bit closer, and then pivot from there until we find true signs of malicious activity.
Looking at the absence of data
The absence of data is just as important as understanding the presence of it. Often, we are provided with data that is lacking or missing, and so the questions gleaned from these observations become: “Why don’t I have that artifact(s)? What didn’t happen? Was it because this data wasn’t recorded? Was the data removed?”
In the absence of data, we also try to determine what could have happened at a given stage of a compromise and what normally happens at that stage. With that information, we try and form our hypothesis about the stages of compromise, if it occurs in an environment. For instance, a customer during an incident response engagement might halt further investigation or response simply because they’re not seeing data exfiltration activity on their sensors and logs.
The approach to understanding the data varies depending on the analyst, but the goal is to answer a series of questions and turn those questions into more questions, and then stop at some point so you can paint the most complete picture possible.
Knowing when to stop
Following an investigative trail results in some form of data aggregation. Knowing when to stop this trail can often be challenging. An indication of knowing when to stop is when the picture doesn’t change even after pulling in more information, leaving you with a nexus of truth about that event or indicator. A comparison to this is the computer science algorithm of depth-first search versus breadth-first search, where investigators can potentially chase one single trail too far, investing too much time on one possible indicator of an attack, and running out of time to investigate other possible indicators. One approach we take to avoid the pitfalls of digging for data is to consult with fellow analysts to get a different perspective to ensure that you are looking at everything from every possible angle. Weighted risk analysis also helps us narrow down what leads to follow. We ask ourselves “what is the probability that a lead I’m investigating will turn out to be malicious?” Multiply that by the potential impact that malicious activity would have. Using that value to rank which leads are most important to follow first helps find higher-risk threats (ransomware, full-domain compromises) faster than low-risk threats (adware, coin miners).
We’ve just described DART’s threat hunting principles and the art form that is understanding the data we’re dealing with when it comes to our incident response work, combing through the data, and creating patterns of suspicious activity by applying critical thinking. In our follow-up post, we will talk about general strategies behind threat hunting and how we work with threat intelligence. Stay tuned.
Learn more
Go to our DART blog series to learn more about the Microsoft Detection and Response Team.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
The post The art and science behind Microsoft threat hunting: Part 1 appeared first on Microsoft Security Blog.
The General Relativity Rabbit Hole: Unraveling Space, Time and the Fourth Dimension - CNET
Darren Aronofsky Fought The Studio To Keep Mickey Rourke In The Wrestler

Darren Aronofsky is a director known for his ambition. Starting with his incredibly risky debut film, "Pi," he's known for going all-out in telling layered and metaphysical stories such as "Black Swan" and "Mother!" But following "The Fountain," one of his more shakily reviewed films, Aronofsky decided to scale back his storytelling for his next project.
He decided upon the topic of an aging professional wrestler, whose obsession with his craft severely damages not only his personal life, but his health and well-being. "The Wrestler," which starred Mickey Rourke in one of his greatest roles, is my personal favorite of Aronofsky's movies because it's such a departure from his other films. Compared to the grand ambition of some of his other work, "The Wrestler" is a small-scale piece that uses the showmanship and cheaply produced flash of the wrestling industry as a replacement for his usual upscale ideas. The world of independent pro wrestling is grimy, and so is the movie. The movie's representation of the seedy underbelly of the wrestling business has been praised by real life wrestlers and fans alike, and even been reflected recently by the 73-year-old Ric Flair insisting on wrestling one last match.
Despite Aronofsky scaling back his ambition, he maintained his refusal to compromise on his vision. When the studio wanted to fire Rourke from the film, Aronofsky pushed to keep the actor, according to an interview with Rourke (via Collider).
The Man For The Job

Mickey Rourke's performance in the movie is a standout, with him managing to embody the character both emotionally and physically, gaining an impressive 27 pounds of muscle for the film. Rourke's portrayal of the emotionally stunted former wrestling star Randy "The Ram" Robinson is nuanced and dark, while still managing to play humorously in multiple scenes.
According to Rourke, working with Aronofsky in itself was a dream of his. "I think the main thing that attracted me to the piece was the fact that I had an opportunity to work with a really special director," said Rourke in his Collider interview. "In the years I've been working, I can count them on maybe four or five fingers, and I could put him right there right at the top of the list with Coppola and the rest of them, Cimino, Adrian Lyne."
Including Aronofsky in the same list as those legendary directors is high praise, but not a ridiculous take whatsoever. The respect Rourke had for Aronofsky was returned by the director during the filming process, when Aronofsky fought for Rourke to remain in the film. "He's very uncompromising. He has a lot of integrity, and he's smarter than the rest of us. I knew why he wanted me to do this part. I mean, it didn't take a rocket scientist to figure that out," said Rourke, himself a former boxer. "But he really fought for me to do this role when he had a lot of resistance, and he kept fighting for me to do it. And then finally, I lost the part, and I guess even when I lost it, he kept fighting for me to do it. And it worked out."
Revitalization

It did indeed work out, as "The Wrestler" was a huge critical success for Aronofsky, getting his filmography back on track following a the box office misfire of "The Fountain." The film netted Aronofsky the Golden Lion award at the Venice Film Festival, the award given to the festival's best director. It solidified Aronofsky's place in the upper echelon of modern directors, and allowed him to go back to creating his weirdo movies again (ahem, "Mother!").
It was a triumph for Mickey Rourke as well, who won multiple awards for his acting in the movie. His performance was seen as the beginning of his "acting comeback" by some, though the momentum wasn't followed through. To give the laziest performance in "The Expendables," a film full of old men sleepwalking through flashbacks of their youth, is an impressive feat in a very negative sense.
Aronofsky saw Rourke, who hadn't had much work of late at the time, and knew he was the man to be in his movie. In doing so, he resurrected Rourke's career and bolstered his own. Aronofsky continues to use his uncompromising vision to produce great films to this day, with his most recent effort "The Whale" acting as the reclamation project for Brendan Frasier. That surely took some courage as well, and a stern rebuff of likely hesitant movie producers, but when an artist as singular like Aronofsky has demands, you can bet on his taste.
Read this next: The Coen Brothers Movies Ranked Worst To Best
The post Darren Aronofsky Fought The Studio To Keep Mickey Rourke In The Wrestler appeared first on /Film.
William Gibson Adaptation THE PERIPHERAL Finally Gets a Trailer!
 we FINALLY get a trailer for Amazon Prime's adaptation of William Gibson's epic cyberpunk novel THE PERIPHERAL. The series includes episodes directed by Vincenzo Natali (of Cube, Cypher, Splice, Haunter) as well as Alrick Riley and is executive produced by Jonathan Nolan, Lisa Joy, Scott Smith, Athena Wickham, Steve Hoban, Vincenzo Natali, and Greg Plageman.
we FINALLY get a trailer for Amazon Prime's adaptation of William Gibson's epic cyberpunk novel THE PERIPHERAL. The series includes episodes directed by Vincenzo Natali (of Cube, Cypher, Splice, Haunter) as well as Alrick Riley and is executive produced by Jonathan Nolan, Lisa Joy, Scott Smith, Athena Wickham, Steve Hoban, Vincenzo Natali, and Greg Plageman. Amazon releases The Peripheral streaming on Prime Video starting October 21st, 2022.
Synopsis:
Flynne Fisher (Chloë Grace Moretz) lives in the rural American South, working at the local 3D printing shop, while earning much needed extra money playing VR games for rich people. One night she dons a headset and finds herself in futuristic London—a sleek and mysterious [Continued ...]
[News] Rejoice! INTERVIEW WITH A VAMPIRE Trailer Has Risen!
![[News] Rejoice! INTERVIEW WITH A VAMPIRE Trailer Has Risen!](https://i0.wp.com/www.nightmarishconjurings.com/wp-content/uploads/2022/09/IWTV_1920x1080_PR15-1.jpg?resize=640%2C360&ssl=1)
A sensuous, contemporary reinvention of Anne Rice’s revolutionary gothic novel, Anne Rice’s Interview with the Vampire follows Louis de Pointe du Lac (Jacob Anderson), Lestat de Lioncourt (Sam Reid) and Claudia’s (Bailey Bass) epic story of love, blood, and the perils of immortality, as told to journalist Daniel Molloy (Eric Bogosian).
Chafing at the limitations of life as a Black man in 1900s New Orleans, Louis finds it impossible to resist the rakish Lestat de Lioncourt’s offer of the ultimate escape: joining him as his vampire companion. But Louis’s intoxicating new powers come with a violent price, and the introduction of Lestat’s newest fledgling, the child vampire Claudia, soon sets them on a decades-long path of revenge and atonement.
Executive produced by award-winning producer Mark Johnson (“Breaking Bad”, “Better Call Saul”, “Halt and Catch Fire”, “Rectify”), creator and showrunner Rolin Jones (“Perry Mason”, “Friday Night Lights”), along with Christopher Rice and the late Anne Rice, the series’ first season consists of seven episodes. Acclaimed director Alan Taylor directs the first two episodes and is also an executive producer.
The post [News] Rejoice! INTERVIEW WITH A VAMPIRE Trailer Has Risen! appeared first on Nightmarish Conjurings.
Blonde Review: Ana De Armas' Powerhouse Performance Tries Hard To Save An Ambitious Mess [Venice]

Revisionist history can, in the right context, be quite fun. Movies like "Inglorious Basterds" come to mind: exciting, surprising, and bold works that expand on — and in some cases, make better — the reality of our world and history. As for Andrew Dominik's latest feature, "Blonde," it could've been a masterpiece in the same vein, but the film (adapted from Joyce Carol Oates' 2000 novel of the same name) comes off as a half-baked fever dream that asserts a lot of good ideas and solid performances without the strength of the cinematic flair it needs behind it. Ana de Armas is a marvel as Marilyn Monroe, embodying her mind, body, and soul — but it's not enough to pull this film out of the mess it makes of itself. It's one of those movies that has a decent amount of great elements, but when they're smashed together, it becomes more of a car crash than an expressionist work of art.
"Blonde" follows the somewhat fictionalized story of one of America's greatest stars of the screen, Marilyn Monroe. The film explores her early life, when she was simply Norma Jean Baker, through her well-known shot to stardom — and the subsequent downfall she faced throughout several relationships, marriages, movies, and attempts to have a child.
An Audacious Biopic Attempt

Let's start with this: The film is undoubtedly audacious, but not necessarily in a good way. Dominik's direction plays out quite disjointed on screen, and it becomes obvious that he has a lot of interesting ideas, but his execution leaves something to be desired most of the time. I love a bold, unapologetic film, but in order for that boldness to hit home, the movie needs to not only achieve a sophistication that removes any cheapness — it also has to be saying something it hasn't already said. "Blonde" certainly doesn't tell us anything we don't know about Monroe, and it doesn't — at least not consistently throughout the film — give her story the carefully crafted treatment it deserves. It feels as though Dominik had a lot of ideas, and wasn't exactly willing to kill any of his darlings. It's not easy to do, but it would have served the story, and shortened an unnecessarily long film.
The first 20 minutes of the film, during which we meet young Norma and delve into her fraught relationship with her disturbed mother (Julianne Nicholson), aren't well acted or written, which sort of sets the audience up with a sour taste in their mouths from the beginning. I'm quick to give actors the benefit of the doubt; most times, they're doing the best with the tools they're given, but I was disappointed with the way the film tried to raise tensions through the subpar performance of Norma's mother. After the film segues into the actress' 20s, it bleeds into something a lot more fun, and naturally, de Armas' performance seems to bring out the best in everyone. In fact, during a scene where the now-semi famous Norma visits her mother in a hospital after 10 years, Nicholson does some of her best acting in the film — and de Armas gives that level of performance quality right back to her. It's a heartbreaking scene, and it leaves you wondering why everything in the film's opening scenes had to be so heightened when Nicholson, and by extension de Armas, are so good at small, powerful gestures and glances.
The Film's Visual Strengths And Weaknesses

One of the film's greatest strengths were its striking visual flairs. I deeply enjoyed some of the metaphors being presented via images, one of my favorites being a scene where Monroe walks a red carpet for one of her film premieres. As she walks toward the theater, the camera pans along the crowd of men waiting and cheering for her, but something feels off. It takes a few seconds to realize that their mouths are enlarged, comically long and wide in a way that is deeply unsettling. It's a beautiful yet nasty nod to how Monroe has been devoured by men in all aspects of her life — the theme of her absent father, whose identity she does not know, is a constant throughout the film — and career for as long as she can remember.
Later, there is a scene in which Monroe is in and out of a catatonic, potentially drug-induced state on a flight. As she weaves in and out of the seats, stumbling on other passengers and their beverages, the film pulls us from the plane to the movie theater and back again, making a comment about how Monroe's profession is haunting her, and despite loving the craft, the business element of the job — which, to her, is the most distasteful part — is always lurking around every corner.
A Lack Of Nuance

I wanted more of these layered, nuanced moments, but was met instead with hollow visual gimmicks. For example, Dominik used POV shots several times in the film, focusing the camera on his actor's faces and letting their movements dictate how the background image would be presented on screen. During one such shot with Bobby Cannavale, who plays Monroe's short-lived husband and retired baseball player Joe DiMaggio, the erratic camera movements — which could be very telling in regards to his character's abusive tendencies — come off very amateur and out of place in the rest of the film. Dominik focused more on making this film a hodgepodge of ideas and visual representations rather than building something cohesive; the only thing that is cohesive is the throughline of Monroe's story — despite the fact that we as audience members can't really tell exactly what is truth and what is fiction.
De Armas was incredible in the role, there's absolutely no denying that fact. But neither the direction nor the script actually served her performance. It was an impression of Monroe, which in and of itself was the real Norma Jean Baker's impression of what she thought a bombshell movie star was. Paired with the film's incredible costuming, make-up, and de Armas' — let's be real — nearly identical face, de Armas' dazzling screen presence is inarguable. But with a disjointed directorial eye and a messy script, de Armas is simply doing the best she can within the chaotic world of Monroe's life, but also the chaotic world the film itself forces her to be a part of.
/Film Rating: 5.5 out of 10
Read this next: The 14 Greatest Biopics Of The 21st Century
The post Blonde Review: Ana De Armas' Powerhouse Performance Tries Hard To Save An Ambitious Mess [Venice] appeared first on /Film.
Clerks III Review: Kevin Smith's Deeply Personal Goodbye To The Past

Twenty-eight years after Kevin Smith made his film debut with the foul-mouthed low-budget comedy "Clerks" and 16 years after the sweet and silly sequel, "Clerks II," the director returns to the Quick Stop to bring the story full circle in "Clerks III." Clerks Dante Hicks (Brian O'Halloran) and Randal Graves (Jeff Anderson) own the convenience store that brought them together, but they aren't sure if they've achieved their dreams or just fallen into their same old routines. Then Randal has a heart attack and realizes life is too short to waste, so he wants to make a movie.
This is Smith at his most deeply personal: Randal's heart attack is clearly based on Smith's own, and the creation of his film at the Quick Stop is a metacommentary on the making of the first "Clerks." Fans in search of the mile-a-minute crass comedy of some of his earlier work, including the first "Clerks" and "Jay and Silent Bob Strike Back," might be disappointed by this deeply heartfelt dramedy that deals with some tough topics, but "Clerks III" is one of the best things Smith has ever made.
Taking Stock Of Life

"Clerks III" is about moments when we're forced to take stock of our lives, and I would be remiss if I didn't mention my life-long appreciation of Smith and his work. "Clerks" was the movie that made me want to make movies when I was a young teen, the movie that made me think it was even within the realm of possibility. It's vulgar and it's messy, but it's a pure slice of life from an incredible storyteller. Smith himself was inspired by another director in much the same way. In his book "Tough Sh*t: Life Advice From a Fat Lazy Slob Who Did Good," Smith revealed that on the night before his 21st birthday, he and a friend went and saw Richard Linklater's "Slacker" and it changed his life. "Slacker" made him want to make his own movie, and put him on the road to making "Clerks."
If "Clerks" was Smith's "Slacker," "Clerks III" is his "Before Midnight." It's self-reflective and a little melancholy, and focuses heavily on the relationships these characters have forged over the years. Just as "Before Midnight" goes back to "Before Sunrise" and "Before Sunset," "Clerks III" returns to both of the earlier "Clerks" films with not only bright-eyed nostalgia, but the hard-earned wisdom of time.
Fewer Funnies But As Heartfelt As Ever

Don't get me wrong — there are some great laughs to be had in "Clerks III." Just about everything in the hospital surrounding Randal's heart attack is hilarious, from the sassy surgeon played by Amy Sedaris teasing Randal about "The Mandalorian" during surgery to a pretty great prayer to Crom (the god of Conan the barbarian) from Randal on the operating table. Funny moments are peppered throughout, but mostly only to relieve some of the heaviness of the situations involved. After all, this is a story about two men facing mortality in very different ways, and it's no laughing matter. Dante's relationship with his wife Becky (Rosario Dawson) isn't what it once was, and he longs for their happy times together long before, while Randal feels like he's wasted his life and longs for a future where he feels fulfilled.
In order to make Randal's movie, the duo has to dig into the past, and that means reuniting Dante with former loves Veronica (Marilyn Ghigliotti) and Emma (Jennifer Schwalbach Smith) as well. Dante must reconcile his feelings about these relationships in order to help Randal, which is the relationship he clearly treasures most. Both "Clerks" movies were about Dante and Randal's deep friendship, and the other friendships they made with the weirdos they worked with. "Clerks III" lets go of the laughs and lets us see the duo as real people instead of potential punchlines.
Growing Up Is Hard To Do

"Clerks III" is sneaky. It's been marketed as a straightforward comedy, but audiences should be prepared to bring a box of tissues with them to the theater. All of Smith's flicks, save for maybe "Jay and Silent Bob's Super Groovy Cartoon Movie" and "Red State," have some kind of heartfelt message at their core, so the sentimentality and seriousness of "Clerks III" didn't come completely out of nowhere.
Just as the first "Clerks" inspired me as a young creative to let my freak flag fly, and the second "Clerks" taught me about how we make our own family after we've outgrown the one of our childhood, "Clerks III" reminded me that while the past shapes us, we should never let it overshadow the present. The movie begins with My Chemical Romance's "Welcome to the Black Parade," and the lyrics are practically the film's thesis statement. Life is hard, but we "carry on."
Smith's latest isn't an easy watch, but neither is growing older. "Clerks III" is the director at his most mature and emotionally resonant. It would have been easy to make "Clerks III" an easy nostalgia-fest with lots of throwbacks, but instead Smith opted for something more. It's a big swing that might not work for frat boys looking to laugh at dick and fart jokes, but that's what "Jay and Silent Bob Strikes Back" is for, after all. "Clerks III" brings things full circle at the Quick Stop in many ways, and it feels like a definitive ending to the saga he started.
/Film Rating: 8 out of 10
Read this next: The 15 Best '90s Comedies Ranked
The post Clerks III Review: Kevin Smith's Deeply Personal Goodbye to the Past appeared first on /Film.
The Boys Showrunner Eric Kripke Pulls No Punches Over The Series' Misogynist Critics

You know, I thought that media literacy and basic decency regarding "The Boys" had hit an all-time low when season 3 was hit with an onslaught of 1-star reviews because certain fans finally realized that they were the punchline, but apparently the toxic dorks can go even lower. Not content to simply complain about the show going "woke" any longer, a certain contingent of fans have taken their ire out on Erin Moriarty, the actor who portrays Annie January, A.K.A. Starlight.
Taking a page from her character's playbook, Moriarty took to Instagram to share her experiences being harassed and belittled by misogynistic fans. While misogynistic backlash against a strong female character is nothing new (Skyler White, anyone?), it feels especially insidious when the character in question has been abused, shamed, and suffered from intense misogyny within the show itself. Annie January is fictional and can handle it, but Moriarty is a human being, and deserves to be treated better.
In response to Moriarty's post, some of the other members of "The Boys" cast and crew reached out to offer their support, but no one did it with as much fight or fury as showrunner Eric Kripke, who unleashed a Twitter post telling misogynists exactly where they can shove their hateful opinions.
No Time For Trolls

After Variety reported on Moriarty's mistreatment at the hands of misogynistic fans, showrunner Eric Kripke hopped on over to Twitter and really let the losers have it:
"Hi trolls! One, this is literally the opposite of the show's f****** message. Two, you're causing pain to real people with real feelings. Be kind. If you can't be kind, then eat a bag of d***s, f*** off to the sun & don't watch #TheBoys, we don't want you. #TheBoysTV"
Kripke's on the money with this one, because these "fans" are missing the message of "The Boys" completely if they think it's acceptable to obsessively critique an actor's appearance and harass them. Moriarty shouldn't have to experience the same kind of hate that Annie does, but unfortunately there are quite a few viewers out there who still think Homelander (Antony Starr) is some kind of hero. There are just way too many Todds still watching the series and not learning anything, and that's sorely disappointing.
Hopefully they will either get the message and learn to escape their boneheaded brainwashing and treat other people with common decency, or they'll follow Kripke's instructions and take a vacation to Earth's nearest star.
"The Boys" season 3 was brilliantly sharp satire, and it's truly a shame that so many fans were too dull to understand.
Read this next: The 14 Best Sci-Fi Shows On Amazon Prime
The post The Boys Showrunner Eric Kripke Pulls no Punches Over the Series' Misogynist Critics appeared first on /Film.
Why Tom Hanks Never Appeared On Doctor Who, Despite Peter Capaldi's Best Efforts

The great thing about the Doctor on "Doctor Who" is the wayward Time Lord's ability to re-generate gives the long-running TV series a canon excuse to recast its titular role and soft-reboot every few years. That also means the possibilities are limitless when it comes to the Doctor's race and gender, which is why of the 13 iterations so far we've... only had one who wasn't played by a cis-male white actor and none played by a person of color.
Yeah, okay, I'm probably not blowing anyone's minds by pointing out a sci-fi TV show that aired from 1963 to 1989 and was later revived in 2005 has a long way to go to being more inclusive (though it is taking steps to get there). But aside from the racists and sexists of the world, "Doctor Who" fans seem to agree the Doctor can and should be brought to life by a far more diverse group of actors going forward. Far more controversial, however, is the matter of whether they can also be portrayed by an American.
America's Dad himself, Tom Hanks, is all-too-aware of this issue, which he discussed in an interview on the Happy Sad Confused podcast (via ScreenRant). According to Hanks, Peter Capaldi pushed for the "Doctor Who" producers to cast him as one of the Doctor's previous incarnations back when Capaldi was starring on the show from 2014 to 2017. Hanks indicated it was ultimately a scheduling conflict that prevented this from happening, but admitted that might've been for the best.
'Can You Imagine The Outrage?'

"Doctor Who" could be described as a lot of things, but "American" most certainly isn't one of them. My friends and I have long joked the show's writers seem to think most of the U.S. is a place we've dubbed "Texas Land," a vaguely Western-y setting of empty roads and retro-style diners. Even when it visits specific locations, like the White House or New York City, the series tends to paint a portrait of these places in amusingly broad strokes.
In perhaps an example of turnabout being fair play, here's Hanks getting some basic "Doctor Who" details blatantly wrong while describing his near-miss casting on the show:
"That would've been a blast, but that's all, that's all scheduling I guess. Can't do every job. And honestly, me as Doctor Who — can you imagine? Can you imagine the outrage? I'm an American, and I'm gonna go over, and I'm gonna jump in that you know, red telephone box, and you know, and either wear a scarf and whatever it is."
None of this is to suggest American actors are banned from joining the Doctor's adventures. In fact, no less than Doctor Horrible himself, Neil Patrick Harris, will be suiting up for a role in the "Doctor Who" 60th anniversary celebration. Perhaps there's also room for Hanks to lend his voice to one of the Doctor's greatest enemies: the Daleks? He's open to the idea, anyway:
"I would've played one of the Daleks, maybe. I would've been inside one of those big salt and pepper shakers talking in that automated voice — with an English accent, by the way."
The "Doctor Who" 60th anniversary festivities will begin in 2023. Meanwhile, you can catch Hanks as Geppetto in the live-action "Pinocchio" remake now streaming on Disney+ (if you dare).
Read this next: The Most Controversial Scenes In Sci-Fi Movies
The post Why Tom Hanks Never Appeared on Doctor Who, Despite Peter Capaldi's Best Efforts appeared first on /Film.
Wolfenstein multiplayer from 2003 comes back online via id Software

Wolfenstein has a new, or at least, relaunched multiplayer mode thanks to id Software and Bethesda, which have introduced official servers for the Return to Castle Wolfenstein spin-off Enemy Territory, the online FPS that was added to Steam back in April.
The Lord Of The Rings' Valinor Explained: How The Blessed Realm Differs In The Books, Peter Jackson's Films, And The Rings Of Power

The lore of J.R.R. Tolkien's Middle-earth is vast and sometimes confusing. There's over 9,000 years worth of intricate history that film and television has not even touched on. For those who have been watching Amazon's "The Lord of the Rings: The Rings of Power," it's been exciting to explore new corners of Middle-earth and the early lives of beloved characters like Galadriel (Morfydd Clark). One of the key places that we are introduced to in the first episodes of the series is Valinor, also known as the Undying Lands. It is a tranquil, sprawling land where Galadriel grew up that she describes as a "winterless spring."
In "The Return of the King" novel, Tolkien depicts Frodo's experience in Valinor:
"Frodo smelled a sweet fragrance on the air and heard the sound of singing that came over the water ... the grey rain-curtain turned all to silver glass and was rolled back, and he beheld white shores and beyond them a far green country under a swift sunrise."
This language is eventually used in Peter Jackson's film version during the song "Into the West." Both Peter Jackson in "The Lord of the Rings" trilogy and the "The Rings of Power" creators reflect Valinor's immaculate beauty in their cinematography of shining, golden hues. Valinor is a mix between Mount Olympus and the Garden of Eden, the home of Middle-earth's godlike beings and the immortal elves. The common misconception is that Valinor is a kind of heaven for everyone in Middle-earth but only elves and a select few are permitted to spend the rest of their lives there. It is a paradise with no pain or suffering. Galadriel has a different relationship with Valinor in all versions of Middle-earth tales.
The History Of Tolkien's Valinor

In the books, Valinor exists on the continent of Aman, west of Middle-earth across the great ocean known as the Sundering Seas. Before, the ocean was a bridge of ice called the Helcaraxë which Galadriel walked across during the Exile of the Noldor in the First Age, when a group of elves went to defeat Morgoth in Middle-earth after he destroyed the Two Trees of Valinor. We see these trees in "The Rings of Power," beautiful sources of light created by the Valar in ancient times. Their last flower and fruit was transformed into the sun and the moon. The rebellious Noldor are banned from returning to Valinor by the Valar.
In the Second Age, the Valar destroy passage to Aman after the men of Numenor attempt to invade Valinor to achieve immortality for the human race. The Valar take Valinor out of Aman and place it above the surface of the earth where you must follow The Straight Path "into the realm of hidden things, a mighty bridge invisible that passed through the air of breath and of flight (which were bent now as the world was bent)," Tolkien writes in "The Silmarillion."
After the War of Wrath ends, the Valar pardon Galadriel and the other elves and allow them to return to Valinor but Galadriel refuses because she has a fierce desire to rule over her own kingdom. That is what motivated her to travel to Middle-earth more than overthrowing Morgoth. She remains in Middle-earth for two more ages to satisfy her craving for power.
Valinor In Peter Jackson's Films

Our main glimpse of Valinor in Peter Jackson's "The Lord of the Rings" trilogy is during the deeply emotional ending of "The Return of the King." Frodo travels to the Undying Lands with Bilbo, Gandalf, Elrond, Galadriel, and Celeborn. In the books, Sam, Legolas, and Gimli eventually go as well.
While the Undying Lands are for the elves, Frodo is invited so that he can heal from the immense damage the Ring did to his soul. Middle-earth could not save him from Sauron's corruption and his painful suffering. He and Bilbo are rewarded for keeping the ring safe and are able to live the remainder of their days in serenity. Peter Jackson masterfully crafts this scene as a combination of heart-wrenching melancholy (I sob every time he says goodbye to the hobbits) and happiness that Frodo will finally be at peace.
The trilogy also references Galadriel's complicated relationship with Valinor. She has clusters of star-like lights in her deep blue eyes because she is the last to have seen the light of the Two Trees. After she resists taking the One Ring when Frodo offers it to her, she references passing a "test" and is now able to "diminish and go into the West." In other words, the Valar will let her return to the Undying Lands. Tolkien explains why Galadriel's ban is lifted in the book "The Letters of J.R.R. Tolkien":
"She was pardoned because of her resistance to the final and overwhelming temptation to take the ring for herself."
We see Galadriel at the end of "The Lord of the Rings: The Return of the King" at the ship heading to Valinor because she has given up her lust for power for the greater good.
What The Rings Of Power Changes About Valinor

In the climactic moments of the first episode of "The Rings of Power," Galadriel must choose between joining the other elves in Valinor, her beloved former home, or pursue Sauron in Middle-earth. In a heroic and lengthy sequence during the second episode, Galadriel turns back to complete her mission.
One of the biggest departures from Tolkien's writing is that Galadriel is not banned from Valinor by the Valar. Instead, the High King of the elves Gil-galad allows Galadriel and her fellow warriors to travel to the Undying Lands. He doles out Valinor like a prize, not a deeply personal decision and something each elf can choose for themselves. The show treats Valinor like something that can be handed out by a ruler based on his own whims, completely erasing the will of the supreme Valar.
This completely changes the structure of leadership in Tolkien's world, but perhaps "The Rings of Power" thought it was easier to depict it this way rather than delve even more into the dense mythology. By removing the Valar's ban, Galadriel is torn between two separate worlds that she cares about deeply due to her need to avenge her brother Finrod. This makes for higher stakes, more dramatic tension, and an exciting narrative.
What "The Rings of Power" does get across, like Peter Jackson's films, is that Valinor is a special, even holy place that promises comfort for characters, but only when they are truly ready to go there.
Read this next: Sci-Fi Masterpieces With Endings We Love To Complain About
The post The Lord of the Rings' Valinor Explained: How The Blessed Realm Differs in the Books, Peter Jackson's Films, and The Rings of Power appeared first on /Film.
Wolfenstein: Enemy Territory gets some official dedicated servers

Id Software is making sure you can play the classics
Yes, Wolfenstein: Enemy Territory is getting some new servers in the year 2022. As more players are hopping on thanks to its free availability, id Software has deployed dedicated servers with a classic ruleset for players to run.
Wolfenstein: Enemy Territory was made available on Steam earlier this year, as part of the Bethesda launcher going away. And it's also free on the Microsoft Store, too.
With the new platform and popularity likely comes players wanting to either experience the game properly, or rekindle their old memories. And so id Software has announced that it's deployed some official dedicated servers for Wolfenstein: Enemy Territory, to facilitate all the nostalgic carnage.

These servers are running the vanilla Enemy Territory Campaign ruleset, with all six original maps and no mods. While id says there are servers with a variety of mods and custom maps that it highly recommends, some folks want to play the classics.
The classic, vanilla dedicated servers are set up across multiple regions, so players around the world can hop in. Four official servers have been deployed: Texas, the Netherlands, Canberra, and London.
All servers will even have a message of the day, saying the following:
"Official & Vanilla Servers hosted by id Software. Enjoy! These servers are unmoderated. For issues, help.bethesda.net"
Back to the past
It's really cool to see id Software supporting renewed interest in an older game like this. Wolfenstein: Enemy Territory was a bit of an outlier, from what I remember of its launch. Its class system and in-match experience might not seem strange now, but it was a cool take when it launched in 2003.
Now players have an easy way to dive in and play it just like it was back then.
The post Wolfenstein: Enemy Territory gets some official dedicated servers appeared first on Destructoid.
IRS Moves Toward Free E-Filing
Read more of this story at Slashdot.
Rosie O'Donnell Defied The Director To Keep Her A League Of Their Own Character Gay

Based on the beloved 1992 film of the same name, the new Prime Video series "A League of Their Own" is an American period sports comedy drama co-created by Will Graham and series star Abbi Jacobson, about the historical formation of a World War II-era women's professional baseball league. The original film directed by Penny Marshall is viewed as a seminal, feminist classic, despite the limitations of 1990s social politics rendering it impossible for the film to have been as intersectional as the lives of the real people the film is based on.
Now, in a more progressive climate, "A League of Their Own" is able to explore how segregation impacted the Black women who wanted to play in the All-American Girls Baseball League, and finally bring the factual queer identities of the players to center field. Queer women have cited "A League of Their Own" as a source of "awakening" for generations, including Abbi Jacobson herself.
While the original "A League of Their Own" is not explicitly queer, one lesbian icon prevailed despite all odds: Rosie O'Donnell as third base player Doris Murphy. It would be another 10 years before O'Donnell herself would come out as gay, but she made sure to do her best to tell Doris' authentic story, even when Penny Marshall couldn't see what the text already knew -- that the character was gay.
Doris Was Gay Because The All-American Girls Baseball League Players Were Gay

O'Donnell made a cameo appearance in the new "A League of Their Own" series as a bartender at a local gay bar, a role that she's sure would have made Doris proud. In a recent interview with Vanity Fair, O'Donnell talked about the making of the original film, and her determination to portray Doris as gay even when no one else could see the obvious queer-coding of the character.
"When we did the movie, there was that one scene [where] I'm on the bus: 'I never felt like a real girl or even a girl, but now I see there's a lot of us, we're all okay.' To me, that was her saying she found her tribe, right? There were gay women or athletic women or women like her, and my character, I thought, was in love with Mae and didn't maybe know how to express it. But it was 1991 when we shot it, or 1990, and the times were different. You don't realize until you're sort of faced with the new show what it could have been."
The queerness of the All-American Girls Baseball League is not something Prime Video threw into the new series for "woke points" or whatever other garbage nonsense detractors are trying to claim, and O'Donnell confirmed this even when they made the film in the early 1990s. "When we met the real players, who were in their 70s—80s, some of them — they would say, 'Oh, this is my roommate, Betsy,'" said Rosie. "I'm like, 'Oh, how long have you been roommates?' [and they'd say] 'Oh, 27 years.'"
'Don't Do It So Gay.'

Rosie O'Donnell said that after shooting the bus scene in question, Penny Marshall recognized what she was doing and told her, "Rosie, don't do it so gay." She claimed that she was performing the character as written, but something about her performance was reading "gay" to Marshall, which makes complete sense considering she was watching a closeted gay person play a closeted gay character. "I did it the same way each time, because that was the way it was real to me," Rosie said. "A League of Their Own" has been hailed for its queer portrayals, something that didn't feel possible when the film was shot in 1990/1991.
"There was no 'Will & Grace,' there was no Ellen [DeGeneres] being out," she said. "I don't think anyone thought, 'Oh, well, they're really leaving out the gay stuff.'" While the queerness was canonical to the real life players the film and series are based on, "there were lots of cultural events for the gay community that we hadn't yet lived," said Rosie. She continued by saying that she finds what Jacobson and the rest of the cast has created as "touching," and how they were able to take these very real stories of Black women and queer women in the league and open it all up to a new audience and worldview.
Read this next: 14 Remakes That Are Better Than The Original
The post Rosie O'Donnell Defied The Director To Keep Her A League Of Their Own Character Gay appeared first on /Film.
A Slap From James Woods During True Believer Taught Robert Downey Jr. A Lifelong Lesson

Hollywood legend holds that during the filming of Charles Vidor's film noir classic "Gilda," Rita Hayworth slapped co-star Glenn Ford so hard that she broke two of his teeth. This is obviously not an ideal situation. Stage and screen combat is an important discipline, one that allows actors to feign violence without actually, you know, dislodging dental work. There is another level, however, but this is typically indulged in action films. Think Sylvester Stallone getting hit so hard in the chest by Dolph Lundgren while shooting the climactic boxing match in "Rocky IV" that his heart swelled to a dangerous degree, forcing him to be flown from Vancouver at low altitude to a hospital in Santa Monica, California.
Accidents will happen. Egos, also, will run amok. Get two actors in a charged scene where they're desperate to ramp the stakes up to an Oscar-clip level, and the situation could get a tad out of hand. This is evidently what went down between James Woods and Robert Downey Jr. during the filming of Joseph Ruben's terrific legal thriller "True Believer."
Bringing Your A Game To A B Movie

Woods is at his live-wire best as a William Kuntsler-like civil rights attorney who's keeping the electricity on by negotiating plea deals for moneyed drug dealers. It's principled work in theory (these men are simply supplying a demand in a deeply corrupt system that targets people of a darker skin tone), but there are greater injustices he could be addressing. It's just that those clients don't pay as well, if they can pay at all.
Robert Downey Jr. co-stars as an idealistic clerk scrambling to convince Woods to take on the clearly crooked conviction of a young Korean man. He's both the last thing Woods' character wants to deal with, and the exact influence he needs to rekindle his righteous flame. "True Believer" is a B movie at heart, but the conflict between Woods and Downey, two of the hardest chargers that ever stepped in front of a camera, is incendiary. And it led to Woods hauling off and smacking the crap out of Downey.
Actors Like Woods And Downey Are Of A Very Different Breed

As Downey told film critic Kenneth Turan in a Q&A for Interview:
"Well, we were doing a scene together, and I was right on the edge of not acting but really making something happen, you know? It's like trying to really make something spontaneous or great happen. I was saying my lines, and he was just looking at me, kind of like, 'You're getting there. You're getting there.' And then I laughed because it was like masturbating. He got this weird look and cocked his head a little bit to the side, and he just reached over and f***ing cracked me right in the middle of the take."
Downey could've taken offense and phoned his agent, but he was in the moment, and understood what the smack was about. "He was saying, 'Here is the point where you can't let the door close,' and he put his foot in the door by slapping me, and something great happened." Is that actor BS? Absolutely. But when you're dealing with performers who operate at that dizzying frequency, you let them sort it out. They exist on a completely different intellectual/emotional plane, and their madness almost always results in on-screen gold. Give "True Believer" a spin, and you're bound to agree.
Read this next: The 16 Worst Things Actors Had To Do For Horror Movies
The post A Slap From James Woods During True Believer Taught Robert Downey Jr. A Lifelong Lesson appeared first on /Film.
I want more storytelling through hardware in video games

Freak me out like it's 1998
Not gonna lie, I’m partial to a gimmicky video game experience. Whether it’s VR, huge arcade-style cabinets, or a giant chunky plastic peripheral you have to buy for your controller, I’m fascinated by it all. I’ve even followed the niche community of streamers who make unconventional controllers, like one player who’s been grooving her way through Elden Ring on a dance pad controller.
As hardware continues to improve, it’s cool to see how we can innovate on using the physical components we interact with to further immerse us in a game’s world. Of this ninth console generation, we’ve seen PlayStation take some impressive steps forward in this regard. Putting aside what I think about the new Last of Us remake, I have to admit that using the controller’s haptic feedback to allow players to “feel” the dialogue is a genius move, especially in how it will allow disabled players to experience the game.
There are also the adaptive triggers, which I find to be more interesting in theory than in practice. It can be interesting to have certain guns feel different with the adaptive trigger, but the implementation of the feature is still young enough that I think we have more to see in how devs use it for story purposes. I’ll be keeping a watchful eye on new releases that claim to use the triggers more.
As far as what Xbox or PC modders are up to in this regard, I have no idea considering I have fostered a PlayStation household, but I’m sure someone will let me know in the comments.

Gaming hardware moments I love
Of course, this is just a modern example that comes to mind considering it’s been in the news recently. Over the years, there have been countless mechanics in games that require you to do something special with the hardware, whether it’s for story purposes or not.
The first thing I thought of in regard to my own encounters with unique hardware-centric game mechanics was that when I played Nintendogs as a kid, you could blow into the microphone to blow bubbles at your puppies. It was a small, simple mechanic within the larger scope of the game, but my little nine-year-old mind was blown nonetheless — it might as well have been magic, as far as my little brain was concerned.
Another small moment I love is the section of What Remains of Edith Finch that focuses on Lewis — particularly how he escapes into his own mind while working at the cannery. The game utilizes a simple control scheme where the use of each joystick is tied to the different realities he is torn between. To start, you use the right stick to chop fish, while the left stick starts controlling a knight character in Lewis’ imagination.
As the sequence goes on, the fantasy takes up more and more of Lewis’ attention, therefore taking up more of the screen, and players must continue the steady rhythm of chopping fish with his right hand while navigating increasingly complicated environments with the left. It’s not world-shattering use of hardware in a story moment, but using a simple, narratively-relevant control scheme to hit home the point of the vignette is something I find incredibly moving every time I play it.
https://www.youtube.com/watch?v=WQBlSnsT5bc
No one can do it like Metal Gear
The example that inspired this feature, though, is from a game I’ve never actually played before: Metal Gear Solid. I had heard whispers of players’ encounters with Psycho Mantis being some of the most chilling in games, but when I heard the whole story as to why, my mind was blown.
For those who aren’t familiar, the iconic boss fight from the first game in the series features an enemy that can read your mind, and uses some tricks that still feel innovative today, let alone when the game came out in 1998.
First Psycho Mantis “reads” the player’s memory card, making taunting comments to them about other games they’ve played. Next, he asks you to place your controller on the ground so he could show off how powerful he is before the controller starts rumbling like crazy. Apparently if you placed the controller on a table, it might also go crashing to the ground spectacularly. Finally, Psycho Mantis evades all of the player’s attacks, stating that he can read their mind, and it’s not until the player moves the controller to the second controller port that the player can land a hit on him, because he can’t “read their mind” anymore.
Metal Gear’s legacy is so multi-faceted, but this gameplay sequence has to be my favorite thing to come out of the series by far as someone on the fringes of the franchise. It’s such creative game design, and while I certainly didn’t play it when it came out considering I was two years old, the way people talk about it makes me wish I could have seen its impact back in the gaming landscape of 1998.
https://www.youtube.com/watch?v=QDJebjf_DkQ
In conclusion
I can’t imagine how unsettling that must have been at the time, and the fact that I’m still talking about it today clearly shows how influential that moment and by extension, the entire Metal Gear series, has been to games as a whole.
I’m sure there are tons of other cool examples of hardware-centric story moments in games, but that’s the only one I really know of that’s directly tied into the narrative experience — and it’s certainly done more masterfully than any other attempts at bringing hardware into a game that I’ve seen. Sound off on any other moments like that that I may have missed, but otherwise, this is my plea to game designers to implement more story moments that are told through innovative hardware mechanics. It’s creative, it’s unique, and it’s something I haven’t seen hit as hard as it did in 1998, even with all of our next-gen innovations. Make it happen, devs.
The post I want more storytelling through hardware in video games appeared first on Destructoid.
Facebook Engineers: We Have No Idea Where We Keep All Your Personal Data
Read more of this story at Slashdot.
Profiling DEV-0270: PHOSPHORUS’ ransomware operations
Microsoft threat intelligence teams have been tracking multiple ransomware campaigns and have tied these attacks to DEV-0270, also known as Nemesis Kitten, a sub-group of Iranian actor PHOSPHORUS. Microsoft assesses with moderate confidence that DEV-0270 conducts malicious network operations, including widespread vulnerability scanning, on behalf of the government of Iran. However, judging from their geographic and sectoral targeting, which often lacked a strategic value for the regime, we assess with low confidence that some of DEV-0270’s ransomware attacks are a form of moonlighting for personal or company-specific revenue generation. This blog profiles the tactics and techniques behind the DEV-0270/PHOSPHORUS ransomware campaigns. We hope this analysis, which Microsoft is using to protect customers from related attacks, further exposes and disrupts the expansion of DEV-0270’s operations.
DEV-0270 leverages exploits for high-severity vulnerabilities to gain access to devices and is known for the early adoption of newly disclosed vulnerabilities. DEV-0270 also extensively uses living-off-the-land binaries (LOLBINs) throughout the attack chain for discovery and credential access. This extends to its abuse of the built-in BitLocker tool to encrypt files on compromised devices.
In some instances where encryption was successful, the time to ransom (TTR) between initial access and the ransom note was around two days. The group has been observed demanding USD 8,000 for decryption keys. In addition, the actor has been observed pursuing other avenues to generate income through their operations. In one attack, a victim organization refused to pay the ransom, so the actor opted to post the stolen data from the organization for sale packaged in an SQL database dump.
Using these observations, this blog details the group’s tactics and techniques across its end-to-end attack chain to help defenders identify, investigate, and mitigate attacks. We also provide extensive hunting queries designed to surface stealthy attacks. This blog also includes protection and hardening guidance to help organizations increase resilience against these and similar attacks.

Who is DEV-0270?
Microsoft assesses that DEV-0270 is operated by a company that functions under two public aliases: Secnerd (secnerd[.]ir) and Lifeweb (lifeweb[.]ir). We have observed numerous infrastructure overlaps between DEV-0270 and Secnerd/Lifeweb. These organizations are also linked to Najee Technology Hooshmand (ناجی تکنولوژی هوشمند), located in Karaj, Iran.
The group is typically opportunistic in its targeting: the actor scans the internet to find vulnerable servers and devices, making organizations with vulnerable and discoverable servers and devices susceptible to these attacks.
As with any observed nation state actor activity, Microsoft directly notifies customers that have been targeted or compromised, providing them with the information they need to secure their accounts. Microsoft uses DEV-#### designations as a temporary name given to an unknown, emerging, or a developing cluster of threat activity, allowing Microsoft Threat Intelligence Center (MSTIC) to track it as a unique set of information until we reach a high confidence about the origin or identity of the actor behind the activity. Once it meets the criteria, a DEV is converted to a named actor.
Observed actor activity
Initial access
In many of the observed DEV-0270 instances, the actor gained access by exploiting known vulnerabilities in Exchange or Fortinet (CVE-2018-13379). For Exchange, the most prevalent exploit has been ProxyLogon—this highlights the need to patch high-severity vulnerabilities in internet-facing devices, as the group has continued to successfully exploit these vulnerabilities even recently, well after updates supplied the fixes. While there have been indications that DEV-0270 attempted to exploit Log4j 2 vulnerabilities, Microsoft has not observed this activity used against customers to deploy ransomware.
Discovery
Upon gaining access to an organization, DEV-0270 performs a series of discovery commands to learn more about the environment. The command wmic computersystem get domain obtains the target’s domain name. The whoami command displays user information and net user command is used to add or modify user accounts. For more information on the accounts created and common password phrases DEV-0270 used, refer to the Advanced Hunting section.
- wmic computersystem get domain
- whoami
- net user
On the compromised Exchange server, the actor used the following command to understand the target environment.
Get-Recipient | Select Name -ExpandProperty EmailAddresses -first 1 | Select SmtpAddress | ft -hidetableheaders
For discovery of domain controllers, the actor used the following PowerShell and WMI command.

Credential access
DEV-0270 often opts for a particular method using a LOLBin to conduct their credential theft, as this removes the need to drop common credential theft tools more likely to be detected and blocked by antivirus and endpoint detection and response (EDR) solutions. This process starts by enabling WDigest in the registry, which results in passwords stored in cleartext on the device and saves the actor time by not having to crack a password hash.
"reg" add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
The actor then uses rundll32.exe and comsvcs.dll with its built-in MiniDump function to dump passwords from LSASS into a dump file. The command to accomplish this often specifies the output to save the passwords from LSASS. The file name is also reversed to evade detections (ssasl.dmp):

Persistence
To maintain access in a compromised network, the DEV-0270 actor adds or creates a new user account, frequently named DefaultAccount with a password of P@ssw0rd1234, to the device using the command net user /add. The DefaultAccount account is typically a pre-existing account set up but not enabled on most Windows systems.
The attacker then modifies the registry to allow remote desktop (RDP) connections for the device, adds a rule in the firewall using netsh.exe to allow RDP connections, and adds the user to the remote desktop users group:
"reg" add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v TSEnabled /t REG_DWORD /d 1 /f
"reg" add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0
"reg" add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD
"netsh" advfirewall firewall add rule name="Terminal Server" dir=in action=allow protocol=TCP localport=3389
Scheduled tasks are one of the recurrent methods used by DEV-0270 in their attacks to maintain access to a device. Generally, the tasks load via an XML file and are configured to run on boot with the least privilege to launch a .bat via the command prompt. The batch file results in a download of a renamed dllhost.exe, a reverse proxy, for maintaining control of the device even if the organization removes the file from the device.

Privilege escalation
DEV-0270 can usually obtain initial access with administrator or system-level privileges by injecting their web shell into a privileged process on a vulnerable web server. When the group uses Impacket’s WMIExec to move to other systems on the network laterally, they are typically already using a privileged account to run remote commands. DEV-0270 also commonly dumps LSASS, as mentioned in the credential access section, to obtain local system credentials and masquerade as other local accounts which might have extended privileges.
Another form of privilege escalation used by DEV-0270 involves the creation or activation of a user account to provide it with administrator privileges. DEV-0270 uses powershell.exe and net.exe commands to create or enable this account and add it to the administrators’ group for higher privileges.
Defense evasion
DEV-0270 uses a handful of defensive evasion techniques to avoid detection. The threat actors typically turn off Microsoft Defender Antivirus real-time protection to prevent Microsoft Defender Antivirus from blocking the execution of their custom binaries. The threat group creates or activates the DefaultAccount account to add it to the Administrators and Remote Desktop Users groups. The modification of the DefaultAccount provides the threat actor group with a legitimate pre-existing account with nonstandard, higher privileges. DEV-0270 also uses powershell.exe to load their custom root certificate to the local certificate database. This custom certificate is spoofed to appear as a legitimate Microsoft-signed certificate. However, Windows flags the spoofed certificate as invalid due to the unverified certificate signing chain. This certificate allows the group to encrypt their malicious communications to blend in with other legitimate traffic on the network.
Additionally, DEV-0270 heavily uses native LOLBins to effectively avoid detection. The threat group commonly uses native WMI, net, CMD, and PowerShell commands and registry configurations to maintain stealth and operational security. They also install and masquerade their custom binaries as legitimate processes to hide their presence. Some of the legitimate processes they masquerade their tools as include: dllhost.exe, task_update.exe, user.exe, and CacheTask. Using .bat files and powershell.exe, DEV-0270 might terminate existing legitimate processes, run their binary with the same process name, and then configure scheduled tasks to ensure the persistence of their custom binaries.
Lateral movement
DEV-0270 has been seen creating defaultaccount and adding that account to the Remote Desktop Users group. The group uses the RDP connection to move laterally, copy tools to the target device, and perform encryption.
Along with RDP, Impacket’s WMIExec is a known toolkit used by the group for lateral movement. In multiple compromises, this was the main method observed for them to pivot to additional devices in the organization, execute commands to find additional high-value targets, and dump credentials for escalating privileges.
An example of a command using Impacket’s WMIExec from a remote device:
cmd.exe /Q /c quser 1> \\127.0.0.1\ADMIN$\__1657130354.2207212 2>&1
Impact
DEV-0270 has been seen using setup.bat commands to enable BitLocker encryption, which leads to the hosts becoming inoperable. For workstations, the group uses DiskCryptor, an open-source full disk encryption system for Windows that allows for the encryption of a device’s entire hard drive. The group drops DiskCryptor from an RDP session and when it is launched, begins the encryption. This method does require a reboot to install and another reboot to lock out access to the workstation.
The following are DEV-0270’s PowerShell commands using BitLocker:

Microsoft will continue to monitor DEV-0270 and PHOSPHORUS activity and implement protections for our customers. The current detections, advanced detections, and IOCs in place across our security products are detailed below.
Recommended mitigation steps
The techniques used by DEV-0270 can be mitigated through the following actions:
- Apply the corresponding security updates for Exchange Server, including applicable fixes for CVE-2021-26855, CVE-2021-26858, CVE-2021-26857 and CVE-2021-27065. While it is important to prioritize patching of internet-facing Exchange servers to mitigate risk in an ordered manner, unpatched internal Exchange Server instances should also be addressed as soon as possible.
- For Exchange Server instances in Mainstream Support, critical product updates are released for the most recently released Cumulative Updates (CU) and for the previous CU. For Exchange Server instances in Extended Support, critical product updates are released for the most recently released CU only.
- If you don’t have a supported CU, Microsoft is producing an additional series of security updates (SUs) that can be applied to some older and unsupported CUs to help customers more quickly protect their environment. For information on these updates, see March 2021 Exchange Server Security Updates for older Cumulative Updates of Exchange Server.
- Installing the updates is the only complete mitigation for these vulnerabilities and has no impact on functionality. If the threat actor has exploited these vulnerabilities to install malware, installing the updates does not remove implanted malware or evict the actor.
- Use Microsoft Defender Firewall, intrusion prevention devices, and your network firewall to prevent RPC and SMB communication among devices whenever possible. This limits lateral movement and other attack activities.
- Check your perimeter firewall and proxy to restrict or prevent network appliances like Fortinet SSL VPN devices from making arbitrary connections to the internet to browse or download files.
- Enforce strong local administrator passwords. Use tools like LAPS.
- Ensure that Microsoft Defender Antivirus is up to date and that real-time behavior monitoring is enabled.
- Keep backups so you can recover data affected by destructive attacks. Use controlled folder access to prevent unauthorized applications from modifying protected files.
- Turn on the following attack surface reduction rules to block or audit activity associated with this threat:
- Block credential stealing from the Windows local security authority subsystem (lsass.exe)
- Block process creations originating from PsExec and WMI commands
- Block persistence through WMI event subscription. Ensure that Microsoft Defender for Endpoint is up to date and that real-time behavior monitoring is enabled
Detection details
Microsoft Defender for Endpoint
Alerts with the following titles in the security center can indicate threat activity on your network:
- Malware associated with DEV-0270 activity group detected
The following additional alerts may also indicate activity associated with this threat. These alerts, however, can be triggered by unrelated threat activity and are not monitored in the status cards provided with this report.
| A script with suspicious content was observed | Suspicious file dropped by Exchange Server process |
| A suspicious file was observed | Suspicious Modify Registry |
| Anomalous behavior by a common executable | Suspicious Permission Groups Discovery |
| Lazagne post-exploitation tool | Suspicious PowerShell command line |
| Local Emails Collected | Suspicious PowerShell download or encoded command execution |
| Mimikatz credential theft tool | Suspicious Process Discovery |
| ‘Mimilove’ high-severity malware was prevented | Suspicious process executed PowerShell command |
| New group added suspiciously | Suspicious process launched using dllhost.exe |
| Ongoing hands-on-keyboard attack via Impacket toolkit | Suspicious ‘PShellCobStager’ behavior was blocked |
| Possible Antimalware Scan Interface (AMSI) tampering | Suspicious Scheduled Task Process Launched |
| Possible attempt to discover groups and permissions | Suspicious sequence of exploration activities |
| Possible exploitation of Exchange Server vulnerabilities | Suspicious ‘SuspExchgSession’ behavior was blocked |
| Possible exploitation of ProxyShell vulnerabilities | Suspicious System Network Configuration Discovery |
| Possible web shell installation | Suspicious System Owner/User Discovery |
| Process memory dump | Suspicious Task Scheduler activity |
| Suspicious Account Discovery: Email Account | Suspicious User Account Discovery |
| Suspicious behavior by cmd.exe was observed | Suspicious user password change |
| Suspicious behavior by svchost.exe was observed | Suspicious w3wp.exe activity in Exchange System file masquerade |
| Suspicious behavior by Web server process | Tampering with the Microsoft Defender for Endpoint sensor |
| Suspicious Create Account | Unusual sequence of failed logons |
| Suspicious file dropped | WDigest configuration change |
Hunting queries
Microsoft Sentinel
Microsoft Sentinel customers can use the following queries to look for the related malicious activity in their environments.
DEV-0270 registry IOC
This query identifies modification of registry by DEV-0270 actor to disable security feature as well as to add ransom notes:
DEV-0270 malicious PowerShell usage
DEV-0270 heavily uses PowerShell to achieve their objective at various stages of their attack. This query locates PowerShell activity tied to the actor:
DEV-0270 WMIC discovery
This query identifies dllhost.exe using WMIC to discover additional hosts and associated domains in the environment:
DEV-0270 new user creation
This query tries to detect creation of a new user using a known DEV-0270 username/password schema:
Microsoft 365 Defender
To locate possible actor activity, run the following queries.
Disable services via registry
Search for processes modifying the registry to disable security features. GitHub link
DeviceProcessEvents
| where InitiatingProcessCommandLine has_all(@’”reg”’, ‘add’, @’”HKLM\SOFTWARE\Policies\’, ‘/v’,’/t’, ‘REG_DWORD’, ‘/d’, ‘/f’)
and InitiatingProcessCommandLine has_any(‘DisableRealtimeMonitoring’, ‘UseTPMKey’, ‘UseTPMKeyPIN’, ‘UseAdvancedStartup’, ‘EnableBDEWithNoTPM’, ‘RecoveryKeyMessageSource’)
Modifying the registry to add a ransom message notification
Identify registry modifications that are indicative of a ransom note tied to DEV-0270. GitHub link
DeviceProcessEvents | where InitiatingProcessCommandLine has_all(‘”reg”’, ‘add’, @’”HKLM\SOFTWARE\Policies\’, ‘/v’,’/t’, ‘REG_DWORD’, ‘/d’, ‘/f’, ‘RecoveryKeyMessage’, ‘Your drives are Encrypted!’, ‘@’)
DLLHost.exe file creation via PowerShell
Identify masqueraded DLLHost.exe file created by PowerShell. GitHub link
DeviceProcessEvents | where InitiatingProcessFileName =~ ‘powershell.exe’ | where InitiatingProcessCommandLine has_all(‘$file=’, ‘dllhost.exe’, ‘Invoke-WebRequest’, ‘-OutFile’)
Add malicious user to Admins and RDP users group via PowerShell
Look for adding a user to Administrators in remote desktop users via PowerShell. GitHub link
DeviceProcessEvents
| where InitiatingProcessFileName =~ 'powershell.exe'
| where InitiatingProcessCommandLine has_all('$admins=', 'System.Security.Principal.SecurityIdentifier', 'Translate', '-split', 'localgroup', '/add', '$rdp=')
Email data exfiltration via PowerShell
Identify email exfiltration conducted by PowerShell. GitHub link
DeviceProcessEvents
| where FileName =~ 'powershell.exe'
| where ProcessCommandLine has_all('Add-PSSnapin', 'Get-Recipient', '-ExpandProperty', 'EmailAddresses', 'SmtpAddress', '-hidetableheaders')
Create new user with known DEV-0270 username/password
Search for the creation of a new user using a known DEV-0270 username/password schema. GitHub link
DeviceProcessEvents
| where InitiatingProcessCommandLine has_all('net user', '/add')
| parse InitiatingProcessCommandLine with * "user " username " "*
| extend password = extract(@"\buser\s+[^\s]+\s+([^\s]+)", 1, InitiatingProcessCommandLine)
| where username in('DefaultAccount') or password in('P@ssw0rd1234', '_AS_@1394')
PowerShell adding exclusion path for Microsoft Defender of ProgramData
Identify PowerShell creating an exclusion path of ProgramData directory for Microsoft Defender to not monitor. GitHub link
DeviceProcessEvents
| where FileName =~ "powershell.exe" and ProcessCommandLine has_all("try", "Add-MpPreference", "-ExclusionPath", "ProgramData", "catch")
DLLHost.exe WMIC domain discovery
Identify dllhost.exe using WMIC to discover additional hosts and associated domain. GitHub link
DeviceProcessEvents | where InitiatingProcessFileName =~ "dllhost.exe" and InitiatingProcessCommandLine == "dllhost.exe" | where ProcessCommandLine has "wmic computersystem get domain"
The post Profiling DEV-0270: PHOSPHORUS’ ransomware operations appeared first on Microsoft Security Blog.
15 Movies To Watch For An At-Home Halloween Horror Nights Experience

Halloween Horror Nights time is finally here! The haunt, on both the East and West coasts at Universal Orlando Resort and Universal Studios Hollywood, is among the most popular in the world. We here at /Film know a thing or two about this annual event, but we also know that attending it could be a bit of a hassle. There's a lot of travel, planning, and strategizing that needs to happen in order for an HHN trip to come to fruition. Unless you're local to either Los Angeles or Orlando, it's not something you can just go to on a whim.
That's why we've created this handy streaming guide. Some of the movies here will be featured at either the Hollywood or Orlando events, while others are more similar to houses based on vibes and themes. No matter what, though, this guide will surely include something that will fill the HHN-sized hole in your heart.
Häxan: Witchcraft Through The Ages

House: Spirits of the Coven (Orlando)
Why it fits: Witches! They've had a major impact on horror and popular culture for as long as either concept has existed. While their history in the genre is far from incomplete, 1922's "Häxan: Witchcraft Through the Ages" tried its best to recap their supposed history, from medieval times to the early 1920s. These witches might not be flappers, per se, but they certainly are seductive and dangerous. Just how dangerous? Give this influential horror film a watch and find out.
Where to watch: The Criterion Channel, HBO Max, Kanopy, Google Play, iTunes, Prime Video, YouTube, Vudu
La Llorona/The Crying Woman

House: La Llorona: The Weeping Woman (Hollywood)
Why it fits: It's been a bit hard to nail down the legend of La Llorona on the big screen, and while Ramón Peón's film has its shortcomings, its cultural significance cannot be denied. It is largely considered to be one of the first movies to kickstart Mexico's film industry, but was unfortunately considered lost for decades. Thankfully, it has returned to the public consciousness through a rediscovered and somewhat restored reel. Take a trip through Mexico's cinematic history before experiencing Universal's return to the legend of La Llorona.
Where to watch: YouTube
House Of Dracula

House: Universal Monsters: Legends Collide
Why it fits: While this movie doesn't feature the Mummy, "House of Dracula" does mark the first time that Dracula (John Carradine) and the Wolfman (Lon Chaney Jr.) ever shared the screen. Sure, the confrontation between the two could have been more drawn out, but hey, at least we got to see these titans together during the Classic Monsters' heyday. If you're curious about whether or not these two monsters like each other, given their appearances in "Universal Monsters: Legends Collide," this film will give you the answer you're looking for.
Where to watch: Google Play, iTunes, Prime Video, YouTube, Vudu
Them!

House: Bugs: Eaten Alive (Orlando)
Why it fits: Giant bugs were kind of a big deal in 1950s horror. In fact, giant animals in general seemed to have a bit of a moment in the horror genre at the time. However, arguably no other movie sent chills down audience's spines in 1954 like "Them!" While the reason why the film's bugs are so big isn't the same as the house's version of events, it is still a hallmark of a very specific horror niche that serves as an undeniable influence on Orlando's haunt. Just make sure you don't have a massive fear of, well, massive bugs before you turn this selection on.
Where to watch: IndieFlix, Google Play, iTunes, Prime Video, YouTube, Vudu
Halloween

House: Halloween
Why it fits: Well, this one is pretty self-explanatory. Returning to the event on both coasts, we will be able to once again walk through the events of this horror classic, coming face to face with The Shape himself. We can't imagine that you've forgotten the initial story of Michael Myers, considering how his epic feud with Laurie Strode has been retold so many times. However, if you do need a refresher, or simply just want to rewatch John Carpenter's slasher (both are extremely valid answers), now is the perfect chance.
Where to watch: The Roku Channel, Shudder, Google Play, iTunes, Prime Video, YouTube, Vudu
The Fog

House: Dead Man's Pier: Winter's Wake (Orlando)
Why it fits: Don't get this mixed up with the mediocre 2005 remake. John Carpenter's supernatural horror might not be as dreary as "Dead Man's Pier" is, but it is still a perfect example of ghostly dockside horror. It's interesting that the concept of fishermen ghosts haunting piers hasn't been explored all that often, but maybe "The Fog" and "Dead Man's Pier" prove that if an idea isn't broken, don't fix it.
Where to watch: Google Play, iTunes, Prime Video, YouTube, Vudu
Killer Klowns From Outer Space

House: "Killer Klowns From Outer Space" (Hollywood)
Why it fits: Why wouldn't this be featured? If you missed the haunted houses in either Hollywood or Orlando in 2019, you probably need to get used to the bizarre klowns made famous by the Chiodo Brothers in their oddball cult classic. Without this important context, the house is going to make no sense. There are several jokes and gags that many might not be able to appreciate unless they've seen the movie. While the majority of films adapted into Horror Nights houses aren't mandatory viewing before the event, this one definitely is.
Where to watch: Tubi, Google Play, iTunes, Prime Video, YouTube, Vudu
Doomsday

House: Descendants of Destruction (Orlando)
Why it fits: This is probably a movie you forgot even existed until you saw this slide. We won't blame you if you did, but the concept of "Descendants of Destruction" should be able to make you seek it out once more. The idea of a walled-off and toxic society where people are left to their own devices is a compelling one, especially now that we have COVID-19 to worry about. If you'd like to get an idea of the depravity people can result to when isolated from the world, give this 2008 Neil Marshall flick a chance.
Where to watch: DirecTV, Starz, Google Play, iTunes, Prime Video, YouTube, Vudu
The Innkeepers

House: Universal Horror Hotel (Hollywood)
Why it fits: While the ghosts of "Horror Hotel" are definitely more on the slasher side, you can't deny that there is something extremely gothic about a centuries-old haunted hotel. Ti West's chilling film centers around a similarly haunted establishment, although the potential victims this time around are two aspiring ghost hunters. If you're looking for something atmospheric and almost beautifully horrifying, check this film out.
Where to watch: Kanopy, Peacock, The Roku Channel, Tubi, Google Play, iTunes, Prime Video, YouTube, Vudu
The Cabin In The Woods

House: Hellblock Horror (Orlando)
Why it fits: Before you say anything, yes, "The Cabin in the Woods" has already gotten a maze at Halloween Horror Nights. That being said, it obviously has the cultural staying power that allows riffs on its concept to be executed. The first half of this movie is a bit of a prototypical slasher movie with some hints of its true nature sprinkled throughout. However, the true nature of the film is a full-on assault on the senses -- one that's especially heightened when the idea of a monster prison is adapted into real life.
Where to watch: Tubi, Google Play, iTunes, Prime Video, YouTube, Vudu
Climax
House: The Weeknd: After Hours Nightmare
Why it fits: There's no real proof that Abel Tesfaye has ever directly cited filmmaker Gaspar Noe in his work, but based on vibes alone, consider "After Hours Nightmare" a mirror to this 2018 film. While none of the horrific visions the central cast of characters experience are actually seen in "Climax," we can assume they look something along the lines of the imagery seen in the maze. Disturbing, sexy, and more than a little bit deranged, prepare to dance your way into Hell with this selection.
Where to watch: DirecTV, Showtime, Google Play, iTunes, Prime Video, YouTube, Vudu
Us And Nope

House: Terror Tram (Hollywood)
Why they fit: This double feature is one that you shouldn't want to miss any time it is recommended, but it certainly shouldn't be missed now. That's because both "Us" and "Nope" are part of a Jordan Peele-centric Terror Tram, a revamped version of Universal Hollywood's Tram Tour. With "Us" already having had a maze at HHN and the permanent fixture of "Nope" locale Jupiter's Claim on the tram tour, this is sure to be a unique experience that needs some important context. Why not take the time to prepare yourself?
Where to watch "Us" and "Nope": Google Play, iTunes, Prime Video, YouTube, Vudu
Freaky And The Black Phone
House: The Horrors of Blumhouse
Why they fit: Much like how "Us" and "Nope" are two movies featured prominently throughout Hollywood's Terror Tram, these two Blumhouse releases are the centerpiece of the "Horrors of Blumhouse" maze. This time, you'll be able to walk through both movies on both coasts, so if you need a refresher on what scares will await you, now is the perfect chance. Come on, don't you want to relive that fantastic table saw kill from "Freaky?"
Where to watch "Freaky": DirecTV, HBO Max, Google Play, iTunes, Prime Video, YouTube, Vudu
Where to watch "The Black Phone": Peacock, Google Play, iTunes, Prime Video, YouTube, Vudu
Read this next: Horror Movies With Unconventional Monsters
The post 15 Movies To Watch For An At-Home Halloween Horror Nights Experience appeared first on /Film.
[Movie Review] BARBARIAN

There’s electricity in the air when people start referring to a new horror movie as extreme or labeling it as “the scariest movie” of the year. Bonus points are awarded if the film makes people walk out. For us horror fans, we see those statements far too often. What is horrific to mainstream audiences may not land the same way for die-hard horror fans. When I first started hearing about how intense Zach Cregger‘s debut film, BARBARIAN, was, it piqued my interest, but I wondered if it would live up to the reputation it was already receiving. Though BARBARIAN isn’t the most intense horror film I’ve seen this year, you better believe it’s one of the most memorable ones.
BARBARIAN is ninety minutes of unadulterated chaos and one of the biggest surprises of the year. Even after watching the trailer moments before seeing the film, there was no way I could have prepared myself for what was to come. A solid entry into the “AirBnB Horror” subgenre, BARBARIAN centers around Tess (Georgina Campbell) a young woman traveling to Detroit for a job interview. She books a rental home on the outskirts of Detroit but when she arrives late at night, she discovers that the house is double booked by a man named Keith (Bill Skarsgård). Since it’s so late and there’s a rain storm outside, Keith assures Tess that there’s nothing to worry and she begrudgingly decides to spend the evening there. However, she soon discovers that there’s a lot more to fear than just an unexpected house guest.
What I loved so much about BARBARIAN is that it’s fun and unexpected. It had jump scares, humor, misdirection, and more. It also focused on how so many of us tend to ignore red flags. We second guess ourselves when we get that tinge in our stomach that something is off. A situation where a woman finds herself alone with a strange man is scary enough, historically speaking. But what Cregger does is he pushes this concept to another level. He takes the viewer down an even darker path, one that you’ll never see coming.
Bringing this tale of horror to life is a small cast of very talented actors. Georgina Campbell (“Black Mirror”) plays Tess, a woman that I think many of us can relate to. Campbell plays her in a grounded, independent way. She’s a smart woman who has found herself in a precarious situation. This makes it all the more worse when shit begins to hit the proverbial fan. We, as the audience, may disagree with some of the decisions she makes throughout the course of the movie but let’s be real, a lot of us would probably take the same route as her if we found ourselves in a similar situation, if only out of curiosity.

Starring alongside Campbell is Bill Skarsgård (IT: Chapter 1 and 2) and Justin Long (Live Free or Die Hard) playing Keith and AJ, respectively. It would do all of you a grave disservice to reveal anything more than their surface-level aspects. Let’s just say, looks can be deceiving. And to that point, it’s another aspect of why this film is so unnerving. Both actors have a perception of them due to the roles they’ve taken on in the past. Bill Skarsgård is known for his terrifying turn as Pennywise in the updated IT films. Justin Long is known for his friendly smile and laid-back attitude. What Cregger does is he uses those aspects to his advantage. If there is one lesson to take away it would be that in this movie, men ain’t shit.
As far as the horror goes, Cregger pulls influences from horror greats such as Evil Dead, and I’d even go so far as to say The Descent mixed with REC. There’s also an element of humor that’s awkward but fits perfectly into the vibe of the film. This should come as no surprise to fans who are familiar with Cregger’s “The Whitest Kids U’Know.” I wouldn’t go so far as to say that the gore is extreme but moreso it’s comical yet disgustingly oozy. Whether it’s being forced fed from a bottle filled with the unimaginable or a head cracked open, there’s no shortage of violent acts that are bestowed upon these characters.
But in between the chaos and gore, there is a scene that brings the crux of the film to the surface. What appears to be an unassuming flashback about the origins of this house is far more than meets the eye. Drenched in pastel colors, joyful smiles, and set in the 1950s at a time when Detroit was booming, a chilling tale comes into focus. This is the strongest moment in the film – it’s subtle but we as the audience know the magnitude behind what’s going to occur. It’s here where Cregger really shines and I appreciate and respect how he was able to craft these particular moments without turning to gratuitous imagery.
BARBARIAN is an unforgettable film and, as I mentioned above, the most surprising film of the year. It has a sharp bite to it and will make the audience laugh just as much as it’ll make them shriek in disgust. The entire cast brings everything they have to their respective roles with a stand-out performance by Justin Long. Joining the ranks of other balls-to-the-wall horror films such as last year’s Malignant, BARBARIAN is set to become a cult classic within its horror subgenre. Whether you end up loving or hating the film, at the very least it’ll make you think twice about booking an AirBnB.
BARBARIAN arrives only in theaters September 9, 2022.
The post [Movie Review] BARBARIAN appeared first on Nightmarish Conjurings.
This 'Swiss Army Knife' of cables puts an end to desktop mess
The Karate Kid's Mr. Miyagi Has An Incredible Connection To Real-Life Heroes
Fans of director John G. Avildsen's "The Karate Kid" franchise will no doubt remember the emotional scene in the first film where a drunk Mr. Miyagi (Pat Morita) reflects on his early life in America. Dressed in his old army uniform, he toasts to a photograph of his late wife and shows a picture of her to Daniel (Ralph Macchio) who is just now learning of his sensei's complicated past.
Born in Okinawa, 18-year-old Miyagi immigrated to the United States after he unsuccessfully professed his love to Yukie, the woman who was arranged to marry his best friend, Sato. He met his wife in Hawaii while working in the cane fields, but their romance was quickly complicated by the United States' decision to enter World War II. When President Roosevelt ordered the incarceration of over 120,000 Japanese and Japanese American citizens in concentration camps, both Miyagi and his wife were relocated to Manzanar, a camp in California. While overseas fighting for the U.S. Army, Miyagi's wife and unborn child died during childbirth — a tragedy that would go on to haunt him for the rest of his life.
Throughout "The Karate Kid" films and "Cobra Kai," Miyagi is always referenced as having been part of the 442nd Regimental Combat Team during his time in the U.S. Army. His service in this particular regiment is even engraved on his headstone. But just what is the 442nd Infantry Regiment, and how is its history significant to "The Karate Kid's" most famous sensei?
Going For Broke

In 1942, when the United States made the heinous decision to incarcerate Japanese Americans in concentration camps, they also refused to allow any of these men to enlist in the United States Army. This decision was reversed a year later with the creation of the 442nd Regimental Combat Team (RCT). This segregated RCT was predominantly made up of Japanese American volunteers, many of which came from Hawai'i as well as the concentration camps on the mainland. During their training, the members of the 442nd excelled, foreshadowing their eventual outstanding success.
The 442nd fought the majority of its battles during World War II in Europe, and they often worked alongside the 100th battalion which was another predominantly Japanese American unit comprised of men that were already enlisted in the U.S. Army before the start of the war. They were famously known for using the phrase, "Go for broke" as their motto, and their strong determination and skill is reflected in the fact that they are, to this day, "the most decorated unit for [their] size and length of service in the history of the US military." Many of the men in the 442nd received awards for their service ("4,000 Purple Hearts, 4,000 Bronze Stars, [and] 560 Silver Star Medals") including 21 Medals of Honor which is the highest military award a person can earn.
The 442nd had a hand in many impressive operations during the war including rescuing members of the 1st battalion, 141st infantry after the group became surrounded by the German Army. Two previous attempts to rescue these men were unsuccessful, but the 442nd prevailed and got the job done. Their success as a unit is extremely impressive when you consider how despite being subject to horrific racial discrimination at the hands of their own government, the men of the 442nd made the decision to still proudly fight for their country. It's no surprise, then, that the valiant Mr. Miyagi is linked to these heroic men.
Isn't Karate For Defense Only?

Not only is Mr. Miyagi a member of the 442nd Regional Combat Team, but he is also one of the 21 men who received a Medal of Honor for his service. In "The Karate Kid," This medal is discovered by Daniel who comes upon it in a box of keepsakes after helping a drunk Miyagi to bed one night. It is a tender and revolutionary moment in the first "Karate Kid" film that quietly speaks to Miyagi's heroic nature, but some might wonder how Miyagi, a man who is so adamant that karate only be used for defense, ended up fighting in a very real, very complicated war in the first place.
It's possible that Miyagi's own sense of justice is what fueled his decision to join the 442nd RCT. When it comes to fighting, Miyagi often chooses not to, however, faced with an unending prison sentence at the hands of the United States, Miyagi may have seen his choice to enlist as a way to both prove his allegiance to his new country and fight for his freedom within it. Historically, many Japanese American men made the decision to enlist in the U.S. Army for this very reason. They believed that their choice to fight despite their incarceration would be a good way to show that they were loyal to the United States. Whatever Miyagi's reasons for enlisting, the film's decision to make him a member of the 442nd is a powerful one that is loaded with important historical significance.
Read this next: The 15 Best Netflix Original Series Of 2021 Ranked
The post The Karate Kid's Mr. Miyagi Has an Incredible Connection to Real-Life Heroes appeared first on /Film.
H. Jon Benjamin Hopes Archer Goes On Long After He Is Gone

For more than 12 years, FXX's hit spy comedy "Archer" has proven its ability to constantly reinvent itself. Since the show's fifth season, seasons of the show have taken on distinctive themes, with Sterling Archer and the rest of the show's irreverent secret agents having done everything from spending a season selling cocaine in a "Miami Vice"-inspired setting to spending multiple seasons in alternate timelines taking place entirely within the mind of the comatose Archer. Through all of these extremely different settings, the show's madcap comedic bite has remained sharp, using its constantly shifting landscape to stay funny and fresh throughout its run.
"Archer" also needed to evolve behind-the-scenes, with series creator and longtime showrunner Adam Reed departing the show for good after the tenth season. A showrunner's exit can sometimes spell doom for a series, but "Archer" managed to retain a writing staff strong enough to maintain the show's quality. Even with massive shifts in the show's talented roster of writers, the star-studded voice cast has stayed consistently strong.
As the show enters its 13th season, the production now must contend with the loss of legendary comedic actress Jessica Walters, who passed away in 2021. While the loss of Walter and her character, the overbearing mother of Sterling Archer, will surely be a tough blow to the long-running comedy, if any show has proven its ability to adapt to changes in the status quo, "Archer" certainly has. In a recent interview with ScreenRant, show star H. Jon Benjamin expressed his own optimism for the series' future, one he believes may even outlive himself.
How Long Can It Go?

Benjamin, known for his distinctive low voice, has seen voice acting success on shows like "Bob's Burgers" and "Family Guy" in addition to "Archer". When asked how long he expects "Archer" to last in the interview with ScreenRant, Benjamin responded with his signature low-key wit: "I don't want to be crass, but it's a pretty easy job, my part. So it's really up to the producers of the show, who do the bulk of the work, and the writers."
Benjamin has been consistent with his response to this line of questioning throughout the years, possibly only semi-jokingly saying in an interview with Looper in 2020 that he expects the show to last until his death. With the flexibility the show's format has shown over the years, who can question this assessment? The themed seasons that take place entirely in the dreams of a comatose Archer especially offer the show a more or less infinite amount of soft reboots to work with.
This most recent interview has him sticking with his often touted line of thinking. "I don't know, I think just based on these characters interacting, another 40 years," Benjamin casually threw out when asked to give an estimation of the show's lifespan.
The show's current showrunner, Casey Willis, has stated his own ambitions regarding how long the show will remain on the air. In an interview with Collider in 2020, Willis recalls meeting "The Simpsons" creator Matt Groening:
"I think at that time we were about to go into season 6 and he said, 'So what season are you guys going into? You're going into your sixth season?' And I was like, 'Yeah, sixth season.' And he smiled a little bit and just said, 'Well, call me when you get to 26.' In my fantasy world, I would love to get to 26 seasons and be able to call him up."
In It For The Long Haul

With both cast members and writers who seem ready to stick with the show for the long haul, maybe "Archer" will be able to join shows like "The Simpsons" and "Family Guy" in the pantheon of animated series that seem to continue putting out new episodes forever. While ideally you'd love to see a show as funny as "Archer" be able to continue ad infinitum, it's a scary prospect. Maintaining a show's quality on a run that long is difficult.
And even if the show must eventually come to an end, the show's heartfelt goodbye to the late Jessica Walter's character at the end of the twelfth season shows that the show is capable of wrapping things up neatly and in a way that honors the show and the characters, if the need arises. The show hasn't yet been renewed past its thirteenth season, but Willis seems confident that the network will do right by them. "I'm sure whatever we decide, FX is going to be with us and I think one good thing is that they'll want to give the show, when it does end, a proper ending," said Willis in his interview with Collider.
But "Archer" is here to stay, for now, with the thirteenth season currently airing on FXX. The show's future isn't exactly crystal clear at this point, but if H. Jon Benjamin has his way, maybe one day he'll be recording lines for the show's fifty-seventh season via Ouiji board. That would be pretty spooky.
Read this next: 10 Times South Park Was Ahead Of The Curve
The post H. Jon Benjamin Hopes Archer Goes On Long After He Is Gone appeared first on /Film.



