As I was looking for documentation for this post, the top result from Google was a link to “Rachel Botsman: The currency of the new economy is trust” (link) followed by an OECD forum with a highlight on “Trust is at the heart of today’s complex global economy.”
While Botsman’s lecture, punctuated with examples of the emerging collaborative economy, is worth viewing, what I challenge is the idea that trust is a new currency or that trust is more important in today’s economy than it was in previous ones. With the exception of war and predatory economies, trust has always been at the very centre of the economy. If something has changed in the economy it is how globalisation has affected trust, its currency.
Trust is at the heart of the economy — and open societies!
In Adam Smith on Trust, Faith and Free Markets (link) Jerry Evensky writes:
In a constructive society, trust and security are based on mutual respect among citizens and between the citizen and the State. It is the maturation of the citizen and of the State together that makes the emergence of a commercial free-market society possible. It is the trust engendered by this maturation of civic ethics and institutions that makes it possible for individuals to enter the market system with confidence that the competition will be a game played by just rules.
When trust is shaken, individuals pull back and the system contracts. Where trust grows, individual energy and creativity are unleashed and the system grows. In Smith’s vision of humankind’s progress, trust is the central theme.
In Top Economists: Trust is Necessary for a Stable Economy … But Trust Won’t Be Restored Until We Prosecute Wall Street Fraud, the Washington Post (link), quotes a 2001 study by Zak and Knack (link):
Our analysis shows that trust can be raised directly by increasing communication and education, and indirectly by strengthening formal institutions that enforce contracts and by reducing income inequality. Among the policies that impact these factors, only education, … and freedom satisfy the efficiency criterion which compares the cost of policies with the benefits citizens receive in terms of higher living standards. Further, our analysis suggests that good policy initiates a virtuous circle: policies that raise trust efficiently, improve living standards, raise civil liberties, enhance institutions, and reduce corruption, further raising trust. Trust, democracy, and the rule of law are thus the foundation of abiding prosperity.
As indicated in a previous post (The Deleterious Effects of Mistaking Security for Trust), there is also a vicious circle, and I am afraid that we are living it: trust in each other and authorities is depleting, creating social problems; as a response to those problems, security policies are implemented that further reduce the trust in each other and the society, leading to ever more stringent security policies. This is the story of France, where the Government with the support of the Parliament has decided to introduce into the French Constitution the state of emergency (“état d’urgence”), i.e. the ability for administrative and police power to take precedence over the judiciary! Not only the French government does not trust his citizens — not exactly fresh news! — but it does not even trust judges — not exactly fresh news either!
Far from being a characteristic of the “new economy,” trust has always been the fuel of open and democratic societies and economies. One change brought with the modern economy and its globalisation might be a greater abstraction of trust: before I could trust my butcher for offering the best meat, now I am asked to trust a label stuck on a package, based on undecipherable standards designed by an agency most likely under the influence of business lobbies complacent parliaments and the very Council of the European Union.
A Transparency International report (link) on 19 European countries and 3 EU institutions shows undue influence on politics across the region and in Brussels:
Moreover, there is a high risk that conflicts of interest can sway decision-making processes. In France, parliamentarians are permitted to carry out lobbying and consulting work while holding office – a situation that is similar in Portugal and Spain.
“Unchecked lobbying has resulted in far-reaching consequences for the economy, the environment, human rights and public safety,” said Anne Koch, Director for Europe and Central Asia, Transparency International. The research highlights problematic lobbying practices across a wide range of sectors and industries in Europe, including: Alcohol, tobacco, automobile, energy, financial and pharmaceutical.
It is interesting to note that the Council of the European Union ranks antepenultimate worst, just before Hungary and Cyprus as institution prone to corruption — for an illustration of the influence of lobbyists one can read Tobacco lobbying warped EU law, British scientists ‘prove’ or Big money and close ties behind Big Pharma’s Brussels lobby efforts.
While, according to an OECD study (link), it is difficult to establish a direct connection between corruption and GDP:
corruption affects other important indicators of economic development such as the quality of the environment, personal health and safety status, equity (income distribution), and various types of social or civic capital (“trust”) – which impact significantly on economic welfare and, in the case of trust, also a country’s development potential […] Recent empirical work by Aidt (2009) shows that the negative effect of corruption on sustainable wealth formation, which adjusts gross fixed investment for resource depletion and human capital formation, is statistically significant and robust. This research also shows that, within the context of such an enlarged definition of growth, no significant “grease effect” of corruption is discernible.
What is the state of Trust in our societies?
An interesting document published by Our World in Data (link) collects a number of data sources related to trust. The figure below represents the interpersonal trust levels as measured by international surveys. It shows a high level of discrepancy between countries. For example, France, the country where I live, the level of interpersonal trust is closer to what is experienced in Uganda and Nigeria than Denmark…

Interpersonal trust levels as measured by the World Values Survey and European Values Study, and the European Social Survey and Afrobarometer Survey – Inglehart & Welzel (2010)
While the difference of perception of interpersonal trust across countries can be striking, there are also differences across generations. According to an Ipsos Mori study (UK) while 73% of the prewar generation say other people can be trusted to tell the truth only 46% of generation Y agrees. While the cause for this generational disparity probably rests on a wide range of factors from massive youth unemployment (youth unemployment rate is at its worst for 20 years in the UK) to the difference in the perception of politicians impotency and wide spread corruption, notwithstanding the lack of trust society has in the younger generation (the educational system is becoming a gigantic test and accountability machine), we are far from the conditions elicited by Zak and Knack for the initiation of a “virtuous circle” developing trust.
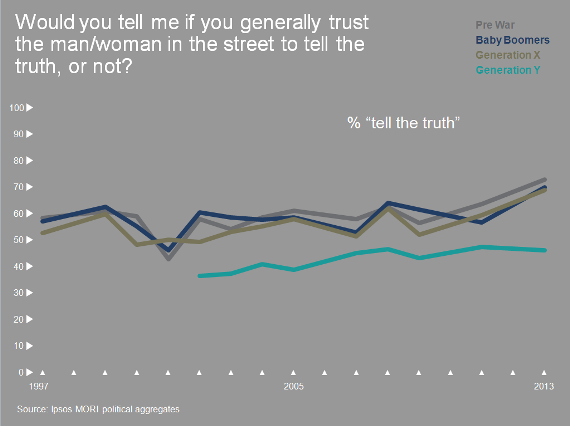
Interpersonal trust levels across generations — Ipsos Mori 2015
The distrust in each other is matched by the distrust in institutions. According to Eurobarometer, a public opinion service of the European Commission, in 2013, sixty percent of Europeans tended not to trust the European Union. That compares to the 32% level of distrust reported in early 2007 before the onset of the 2008/2009 global financial crisis and the ensuing euro zone debt crisis (source).
Intrigued by those statistics, I went to a colleague, Pierre Perot, a sociologist, who recommended reading La Société de Défiance, Comment le modèle social français s’autodétruit ( The Society of Distrust, How the French social model self-destructs), a study by Yann Algan et Pierre Cahuc (link). This book reports a number of studies, in particular the International Social Survey Program (ISSP) and the World Values Survey (WVS).
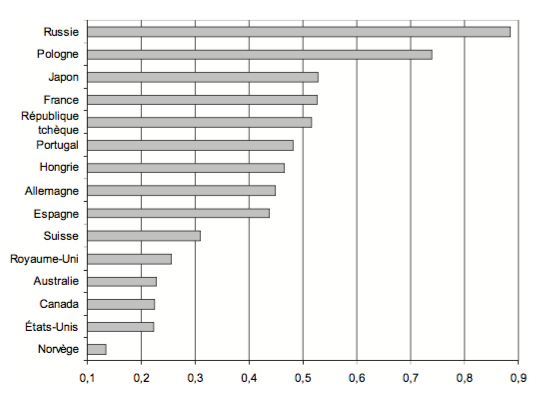
People responding to the statement “To reach the summit, you need to be corrupted” -Source: International Social Survey Program 1999.
While very few will be surprised to find Russia ranking so high in the corruption scale, I had to understand why France ranked so high. It is when I found another damming statistic: France is penultimate, just after Mexico when being asked whether it is acceptable to buy something known to have been stolen (c.f. chart below).
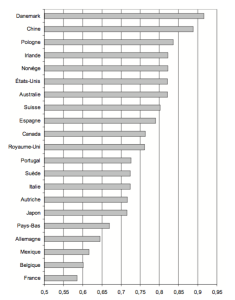
 People responding to whether “buying something you knew was stolen” cannot be justified – Source: World Values Survey, 1980-2000.
|
 People responding that “someone accepting a bribe in the course of their duties” cannot be justified – Source: World Values Survey, 1980-2000.
|
|
|
While the figures in the previous charts refer to a 1980-2000 wave of World Values Surveys, more recent data (2010, c.f. annex) confirm the gap between countries and France’s position… I have to testify that those figures confirm my own experience and reflect the level of apathy and sense of disempowerment I can observe.
How can trust be rebuilt?
If governments have demonstrated their inability, and often their unwillingness, to address the causes of increased distrust, then who should take the lead? Last week I got from Carla Casilli (@carlacasilli) the news about a meeting organised by Citizen’s Initiative Review: “Rebuilding the Public’s Trust Begins with Trusting the Public” (link). How true! How dare politicians ask for our trust when they themselves do not trust us?

While bringing “representative groups of citizens together to fairly and thoroughly evaluate ballot questions and give voters information they can trust” is certainly a worthy effort, the problem of trust goes far beyond ballot issues. Moreover, the lack of trust might be caused by the institutional framework itself, and providing information one can trust might not be enough to bring people back to the ballot stations.
As an educator, my first reflex when defining an objective, here rebuilding trust, is the definition of success indicators: how shall we know when trust is being rebuilt? What are the criteria? How shall we proceed to collect the data? The way trust has been measured until now is through polls and surveys based on a small sample of the population. Is there a means to involve 100% of the population, to obtain a rate of participation even greater than the percentage of the population going to the polling stations?
While the measure of the absolute value of social capital is probably a very complex if not an impossible task, one might be able to measure its relative value, whether it increases or decreases in its different constituents. For example, the trust in political parties could decrease while the trust in fellow citizens increase,s the trust in industrial food decreases while that in local food and fair trade increases.
The power to trust!
And if the solution to re-building trust was to provide every citizen with the means to express their trust, giving citizens the power to trust? Until now, we used ballot papers to invest our trust in representatives, money to express our trust in goods and services. While this might be sufficient in an open society and an open market, we have to recognise that both political life and the market are rigged. If people do not go to polling stations, it is not unreasonable to imagine that this might be connected with a feeling of disempowerment, a disability acquired through repeated experience…
The recent history of the Open Badges is an iconic illustration of how rigged the system is: while Open Badges are trust tokens, the infrastructure has been designed in such a way that it is almost impossible for ‘normal’ individuals to issue Open Badges — unless one is a geek or ready to pay for access to an issuing platform. Of course, it is clear that at no point in time the designers of the Open Badge infrastructure stopped their work and asked: “how shall we make it as difficult as possible for the average punter to create Open Badges, so that only institutions will find the will and strength to issue them.” They probably did not say either “and to make it even easier for the institutions, they will not to have to prove their credentials, therefore institutions will not need to have a Backpack.”
If the infrastructure is designed that way, it is not because of a faulty design nor the will of wicked designers. It is simply the manifestation of the power of the superstructure, the pressure of institutional frameworks and mind-frame. The current Open Badge Infrastructure was designed competently to instantiate in a piece of software the asymmetry between authorities that have the right to trust and the vulgum pecus who has the right to beg to be trusted. This superstructure is also reflected in the numerous narratives where institutions are glorified as the natural credentialing authorities and individuals as those in need of being guided through pre-digested pathways to reach the Valhalla of formal recognition!
It is a fallacy to pretend that individuals are “empowered” with Open Badges when it is the institutions that are in control and are the main beneficiaries. That does not imply that individuals are “loosers”, and do not gain any benefit, but that individual benefits are ancillary to institutional benefits. The brilliant presentation of David Leaser during last week’s community call (c.f. etherpad, recording and the picture below) is an impressive illustration of the beneficial impact of Open Badges have had on IBM and its employees. One of the main benefits is probably the creation of a level playing field by making visible information that would have been previously kept hidden within human resource information systems silos. By making it public, new processes have emerged to plan and recognise development and organise teamwork.
Yet, the Open Badge system presented during the call is clearly asymmetrical with the organisation defining and issuing the badges while employees collect and exploit them. It partially reflects how businesses operate and how employees’ interests are subordinate to those of the organisations paying their salaries. Employees might not have (yet) the power to trust by issuing and endorsing their own badges, but a community has many means to establish trust networks — trust networks existed long before the invention of Open Badges! And the power to trust using digital technology might come sooner than expected, starting with the endorsement of Open Badges then with the adoption of the personal ledgers, a means to record and value even more granular data to create an intelligible life log, a path pioneered by Steve Mann.

Impact of Open Badges at IBM — source
The BoT economy
In previous posts I introduced the Bit of Trust (BoT) a “currency” representing an elementary trust bond between two nodes in a Web of Trust (WoT). Imagine a network where every entity (person, organisation, product, service, etc.) is represented by a node and each node has a public distributed ledger recording the BoTs received and issued, we would have:
-
BoTs I have issued: my trust capital investment — a credit lent to those I trust
-
BoTs I have received: the trust invested in me — a debt owed to those trusting me
We could define the individual’s trust capital as the sum of the trust received and trust issued and the social capital as the sum of the investments in others.
-
Individual (Trust) Capital = debts + credits
-
Social (Trust) Capital = ∑debts = ∑credits
Contrary to currencies, there is no need for a “central bank of trust” to control the number of BoTs issued, as every node in the network should have the ability to trust and therefore to produce BoTs. While increasing the number of banknotes leads to inflation and sometimes to the collapse of an economy, trust works the other way around!
NB: The time is long gone where money was created by central banks. 97% of the money in today’s economy is created by banks (through loans), whilst just 3% is created by governments (link). The Web of Trust just pushes the logic one step further: every node is its own trust bank and produces as many BoTs as required!
The value of the BoT will be relative to a context of interpretation. It is the glasses through which the reader visualises a collection of BoTs across multiple ledgers that a value can be assigned. While a BoT is a generic construct, it is the account where it is invested that transforms a general meaning (trust) into something more specific such as “I trust that you are a competent cook.” This is done by “investing” the BoT in the “competent cook” entry of the personal ledger. But that information is of little value if there is no contextual information, such as recent endorsements by other members of the Web of Trust, collection of recent evidence of cooking-related activities. It is an opportunity to explore the potential of moving from an analytical approach (against a competency framework) to an analogical approach (against the position of a subject in relation to other subjects in a domain or community of practice.)
Conclusion (provisional)
With distributed ledgers and BoTs we would have the means to establish a new kind of generalised trust index, based not just on a sample of individuals but on all the participants in the Web of Trust. This index could be exploited through different contexts providing different communities with a mirror to reflect and improve their trustworthiness. Just like the Bitcoin did not wait for the approval of monetary and regulatory authorities, there is no reason to wait for the approval of policy authorities to implement the means to rebuild trust, bottom-up, bit by bit, using the Bit of Trust as the 21st century’s ballot e-paper for building an open society!
This post has hardly scratched the surface of the potential benefits of BoTs as the translation of Open Badges and open credentials with the distributed ledger technology. In a next post, I will explore trust from a micro, meso and macro perspective challenging the value of the dominating interpretation of micro-credentials to advocate the value of “microlevel-trust.”
NB: Salava, the Open Badge Passport Community Edition will soon provide the sandbox to explore new approaches to issuing and exploiting Open Badges for building bottom-up trust networks. We will do so by exploiting the current Open Badge Infrastructure and as soon as possible develop a distributed ledger extension (c.f. #badgechain!).
Stay tuned!
Previously published in HASTAC
Annex
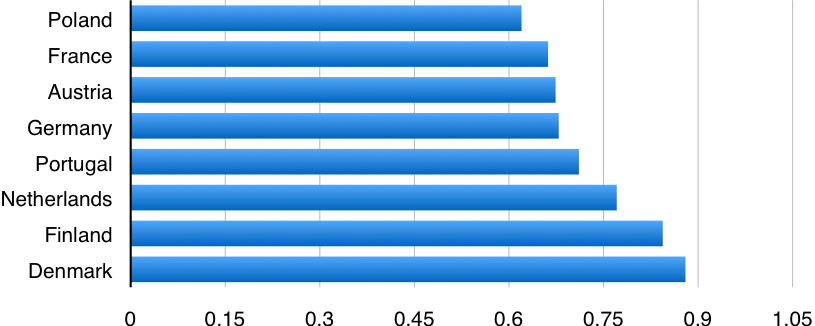
People responding that “accepting a bribe in the course of their duties” cannot be justified – Source: World Values Survey 2010.
Data is available through the European Values Study (EVS 2010) accessible at the Leibniz Institute for the Social Science (link).
To the question “Please tell me whether you think that claiming state benefits which you are not entitled to can always be justified, never be justified, or something in between,” only 30.2% of French respondents replied “Never” (they were 40.8% in 1999!) against 62.8% in Finland and 79.8% in the Netherlands and 67.9% in Italy —so much for the French citizens who tend to justify their shortcomings for being a “Latin country” — what could be more “Latin” than… Latins!
The fact that the number of French respondents that would never claim an undue state benefit decreased from 40.8% to 30.2% in 10 years time might be the price to pay for the toll of the economic crisis and the inability of the governments to take adequate measures to resorb massive unemployment and rampant corruption.

























 The name Rapier is an acronym for “REST APIs from entities and relationships.” With Rapier, you specify an API in YAML by specifying the entities and relationships of the data model that underlies the API, along with query paths traversing the relationships.
The name Rapier is an acronym for “REST APIs from entities and relationships.” With Rapier, you specify an API in YAML by specifying the entities and relationships of the data model that underlies the API, along with query paths traversing the relationships.


 After being on the verge of extinction, microSD card slots are now once again making a return in flagship Android smartphone this year. To make things better, Google has also added an option in Marshmallow that makes it possible to use a microSD card as an internal storage disk.
After being on the verge of extinction, microSD card slots are now once again making a return in flagship Android smartphone this year. To make things better, Google has also added an option in Marshmallow that makes it possible to use a microSD card as an internal storage disk.
 MediaTek has announced its new mid-range chipset at the Mobile World Congress, the Helio P20. Successor to the Helio P10, the P20 is an octa-core chip that features higher clocked Cortex-A53 cores and is based on the 16nm fabrication process.
MediaTek has announced its new mid-range chipset at the Mobile World Congress, the Helio P20. Successor to the Helio P10, the P20 is an octa-core chip that features higher clocked Cortex-A53 cores and is based on the 16nm fabrication process.












