
View Comic!
Codsmackwow that is georgious
CodsmackI need to see some of these!

Enlarge / From A to Z, as it were. This was fun. I liked making this. (credit: 20th Century Fox)
Here at Ars, we're always making lists (just like Liam Neeson). Lists of science fiction movies are a common item for discussion on the Ars staff Slack channel—particularly short lists of the best science fiction movies ever made. But "best" is an impossible word to quantify in any broadly applicable way—one person's "best ever" might be another person's worst, especially in a genre of movies as rich and varied as science fiction.
While the Ars staff has some bitter disagreements on which movies are better than others, it's undeniable that some science fiction movies are mandatory viewing for the modern geek. To that end, rather than try to pull together another tired "top ten sci-fi movies" listicle, we've instead polled the Ars staff to try to come up with a definitive "science fiction bucket list"—that is, a list of sci-fi movies that you should absolutely see at least once before you die. They aren't necessarily the "best" movies by any specific set of criteria, but every film on this list is outstanding in some particular way. Some were groundbreaking in their stories or subject matter, some were controversial, and some contained a character or plot twist that went on to become an archetype, referenced in and reused by countless other films. Some films on the list, like Fritz Lang's Metropolis, are pure cinematic poetry; others, like Pacific Rim, are pure popcorn fun. And, as a bonus, we even included a bonus list of a few absolutely terrible stinkers at the very bottom.
Strap in, dear reader, and pick through the Ars Technica sci-fi bucket list. Each staffer contributed a movie or two to the list, so we've captured a pretty broad range of must-see films. We're sure many folks are going to disagree over our choices—this is the Internet, after all, and arguments on the Internet about science fiction have been going on since the 1970s!—so you're welcome to tell us all of the movies we should have included but didn't down in the comments.

(credit: Rashmi Gupta)
As electronics have become increasingly ubiquitous, the never-ending upgrade churn fills an ever-larger e-graveyard. If that’s where the story ends, we’re in real trouble. The several years of use a typical device sees effectively become a short conveyor belt between mines around the world and the local landfill. The only sensible and sustainable thing to do is to recycle the materials in our devices—ideally right into the next generation of tech.
Responsible recycling operations (that don’t simply dump e-waste in developing countries) have an interesting set of challenges to work on. Recycling is always trying to catch up to—and is limited by—what manufacturers are doing. But opportunities are there for those willing to make it a priority.
To learn a little about the kinds of things that can be done now and what stands in the way of doing more, Ars talked to Dell about its recycling efforts. Dell runs a take-back program for old devices in partnership with Goodwill, which sells anything worth selling and sends the rest on.

Enlarge (credit: Getty | Dmitry Rogulin )
Routine hormone injections into the buttocks of 320 men dramatically shrunk their sperm counts and prevented pregnancies during a year-long, early-phase trial, researchers reported Thursday.
The findings suggest that a future hormonal male contraceptive may one day be possible. However, the data also revealed high rates of side effects, such as acne and mood swings, suggesting much more work is needed before such a birth control method is realized.
"A male hormonal contraceptive is possible," lead author Mario Festin, a medical officer with the department of reproductive health and research at the World Health Organization, told the Chicago Tribune. "We have to continue searching for or investigating the right drugs, and their combinations, with the highest efficacy and safety, and acceptability, with the least side effects."

UNIVERSAL STUDIOS, Calif.—On Friday evening Tesla officially announced an integrated solar roof and Powerwall product for individual use. When or if the roof and the Powerwall become available to consumers is most likely contingent on Tesla and SolarCity investors voting to approve Tesla's offer to buy SolarCity in a $2.6 billion (£2.1 billion) all-stock deal on November 17.
Tesla set up an elaborate "neighborhood" display on the Universal Studios lot in Los Angeles. The company unveiled several model homes with Tesla Powerwalls mounted on the side and a variety of custom roofs with photovoltaic cells disguised as tiles.
"You really need to make solar panels as appealing as electric cars have become," Tesla CEO Elon Musk told a crowd of several hundred people as the sun set on the artificial neighborhood. "The goal is to have a roof that's less than the installed cost of a roof plus electricity."

Design website Core77 says, "Industrial designers: Do you find it stings when non-designers invent a successful product that you should have thought of?" The product is called the TubShroom, and it's a silicone ribber gadget that fits into drains to trap hair.
What's interesting is that [inventors Serge and Elena Karnegie] sought funding on both Kickstarter and IndieGogo — and smashed it on both. They gathered $59,267 on the former and about $120,000 on the latter.
That was last year. This year they've returned to Kickstarter with a smaller version called, unsurprisingly, the SinkShroom. The $12 device has already been 400% funded, and there's 18 days left to pledge if you want one.

Enlarge (credit: Jim Watson / Getty Images News)
On Thursday morning, federal authorities in Texas unsealed criminal charges against dozens of people who are accused of being part of a “transnational criminal organization” that allegedly victimized tens of thousands of people and yielded hundreds of millions of dollars in losses.
The indictment was filed against 61 people and includes charges of conspiracy to commit identity theft, impersonation of an officer of the United States, wire fraud, and money laundering. Of those people, 20 were arrested Thursday in the US.
The suspects are believed to have orchestrated an incredibly large series of phone-based scams that lasted for years. According to prosecutors, the suspects would call victims, impersonating Internal Revenue Service and United States Citizenship and Immigration Services officials, and would then demand payment through debit cards or wire transfers. If victims didn’t pay up, the callers threatened them with arrest, deportation, or heavier fines. There were also related scams involving fake payday loans and bogus US government grants, according to the criminal complaint.
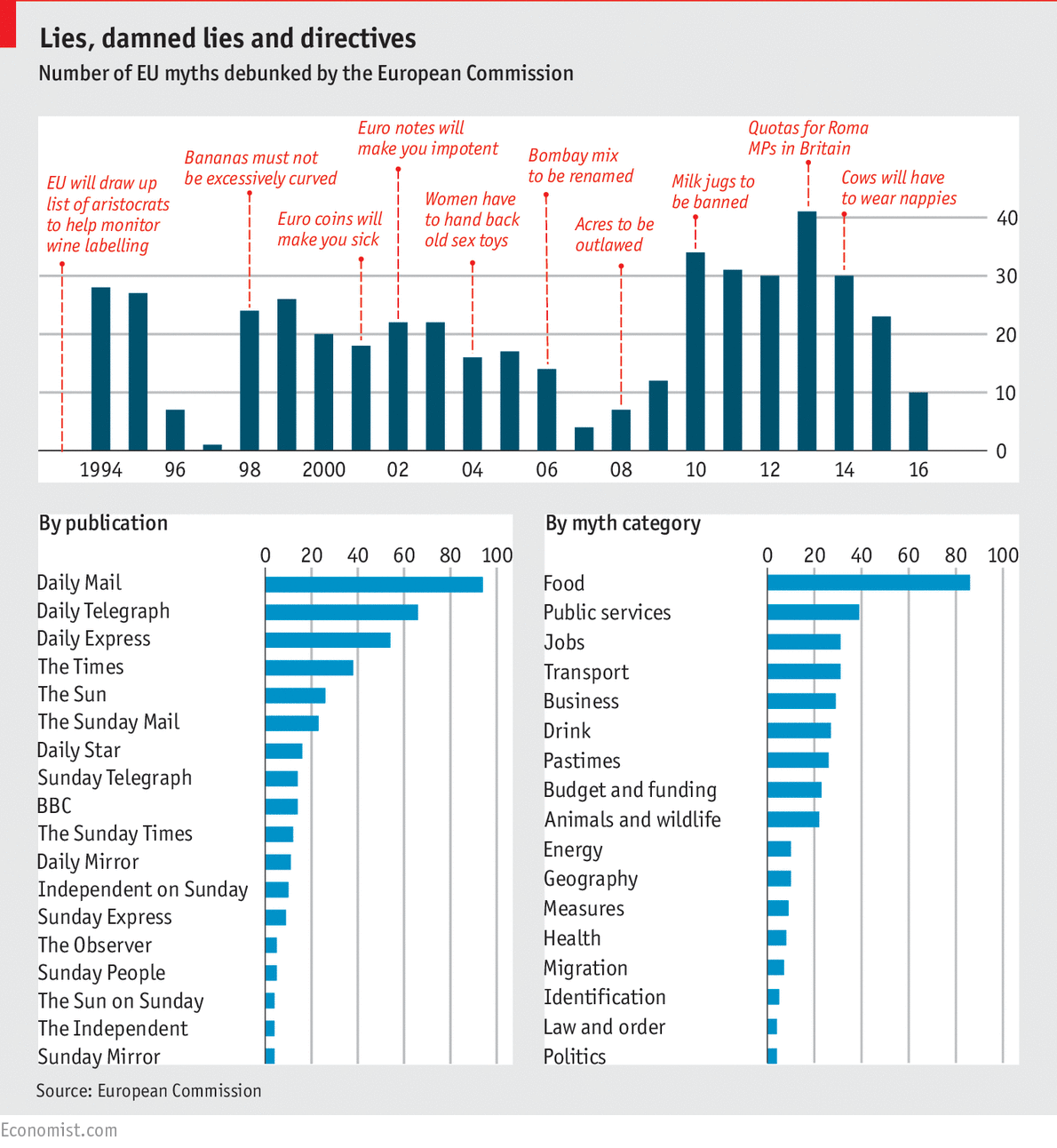
Last June, the Economist ran this chart: "Lies, Damned Lies, and Directives," which documents decades of flat-out lies about EU regulations that were published in the tabloid press (many invented by the UK's post-Brexit foreign minister and Trumpian hairclown Boris Johnson, whose press colleagues considered him most reckless confabulist on European matters in their ranks). (more…)

Dominic Patten reports that Donald Trump’s Hollywood Walk of Fame star was destroyed early Wednesday morning by a man dressed as a city construction worker.
I am in the middle of doing some real estate related research, and I came across an old favorite set of charts: These two Case-Shiller charts (via Bespoke, updated October 25th) shows the changes in current RRE prices from both the boom top and the crash bottom, by metro regions. They are still astonishing: Source: Bespoke…
The post Housing Relative to Bubble Highs & Post Crash Lows appeared first on The Big Picture.
Trend Job Growth: Where’s Normal? Rhys Bidder, Tim Mahedy, and Rob Valletta FRBSF Economic Letter 2016-32 | October 24, 2016 With the U.S. labor market at or near maximum employment, assessing trend job growth has become increasingly important. This “breakeven” rate, which is the pace of job growth needed to maintain…
The post Trend Job Growth: Where’s Normal? appeared first on The Big Picture.

Andrew Lekashman offers a brief pictorial a history of mechanical keyboards, from adding machines to dumb terminals to Symbolics monstrosities to modern blank-key hacker totems. There was a lot of ingenious tech left by the wayside on the way to finding the perfect click.
Pictured above is one not included in the roundup, a particularly beautiful Raytheon(!) model that can be bought on eBay for $300, then sent to me.
Lekashman's tastes are grittier:
Ultrasonic I Plus
This keyboard is acoustic and operates entirely by vibration. This makes it more like a musical instrument than a workplace device. This is something that hasn’t been replicated in the keyboard market since 1982. The specific principle that allows it to work is called Time Difference Of Arrival (TDOA). This is like a form of echo-location to measure which key hits the acoustic transfer bar. Whenever a switch is pressed, a metal “slapper” strikes the bar, and transducers measure the sound wave produced, which differs based on the distance of the slapper from the transducer. Typing on the keyboard is delightfully clicky and pleasantly tactile.

Trump hotels are slashing their rates to try and maintain occupancy, and similar stories are emerging from other corners of the Trump brand-licensing empire held to be the source of The Donald's wealth. The simple answer is that he's just ruining his brand, but it may be truer to say that his political base is becoming his clientele.
The Republican nominee for president is in danger of losing not just the election, but something dear to a man who claims the marketing value of his name alone is worth $3 billion: the many customers, mostly wealthy, who have stayed at his hotels, played a round at his golf courses or held galas at his oceanside resorts.
Experts say the Trump brand is tarnished and at a tricky crossroads as his appeal shifts from the well-heeled, high-income people he has long courted to a more middle-class base, including the fervent fans he cultivated during the campaign.
There is speculation that he could start a Trump media network as a right-wing alternative to major news outlets, drawing money from advertisers to make up for any weakness in his empire elsewhere. But he may have to pivot fast.
"The current trajectory is very harmful to his businesses," said Scott Galloway, a marketing professor at New York University. "Right now his brands cater to the affluent, who are disproportionately turned off by his activities."


Recent revised estimates upping the number of galaxies in the universe seem even more mind-boggling when contemplating this image released from Hubble this week. It shows NGC 362, one of about 150 globular clusters on the outskirts of just one galaxy, our own Milky Way. (more…)
(Here is the latest edition of the Institute for Justice’s weekly Short Circuit newsletter, written by John Ross.)
Is judicial engagement little more than a camouflaged appeal for more libertarian judicial outcomes? Not a bit of it, argues Evan Bernick of the Center for Judicial Engagement, responding to a critique of his lead essay over at Cato Unbound. Click here to read more.
The Center for Judicial Engagement just released its second installment of an annual review that probes particularly soaring examples of judicial engagement and particularly searing examples of judicial abdication. It’s a congenial read for the convivial reader. Click here to read.
And click here to give last week’s podcast a listen.
- Patent holder: You know how people go through their mail and throw out junk based on who sent it? We own the idea of doing that with a computer. Federal Circuit: That is not a patentable idea. Concurrence: And even if it were, the asserted patents would disrupt a huge amount of online communication — and are therefore barred by the First Amendment.
- Allegation: The NSA is collecting all or nearly all private messages between U.S. citizens communicated via Google, Yahoo, Microsoft, and other companies’ services. Gov’t: Not so. The program only targets specific foreigners located overseas. Third Circuit: Plaintiff has sufficiently alleged harm to his interests, which is not to say he has standing to proceed. On remand, the district court may wish to allow for some limited discovery that might shed light on the scope of the program.
- State investigator obtains indictment of nurse for neglecting patient at Frankfort, Ky. facility by testifying falsely to grand jury. (Among other things, he said she had not ordered lab tests that she had indeed ordered.) A state judge dismisses the case. Can she sue the investigator? Sixth Circuit: Absolute immunity.
- The U.S. admitted 10,000 Syrian refugees this year. Fearing terrorists might be among them, the governor of Indiana banned them from settling in the state. Seventh Circuit: There’s no evidence for the guv’s “nightmare speculation.” Indeed, Syrians admitted in 2015 have settled in Indiana (and other states) without incident. So no enforcing the ban while the suit proceeds.
- Allegation: Among other indiscretions, U.S. Fish and Wildlife researcher gave voice to prurient thoughts about student while the two were alone in Alaskan wilderness. After the trip, the student arrived in Minnesota to start Ph.D. program and discovered she’d been assigned to share an office with the researcher, where pestering persisted. Researcher: The university didn’t provide me sexual-harassment training, so she can’t sue me. Eighth Circuit: Not so. No qualified immunity.
- In which the Eighth Circuit affirms a 25-year sentence for former acting director of cybersecurity at the U.S. Dept. of Health and Human Services, who accessed child pornography on a website seized and then briefly run by the FBI.
- After it emerged that hundreds of graduates of U.S. academy for foreign military personnel committed atrocities abroad, activists began tracking graduates’ careers and Congress mandated reforms. In 2005, however, the DoD ceased its practice of releasing names of students and instructors. Ninth Circuit: Out of legitimate concern for their well-being. Dissent: The gov’t introduced no evidence to justify its concern, and now there’s no verifying officials’ assurances that the reforms are working.
- Years ago, Elbert County, Colo. officials discovered that they had lost their zoning regulations and map. Instead of re-passing a zoning code, they just had a county planner do his best to recreate the lost documents, without holding the public hearing required by Colorado law for zoning-law changes. Aggrieved property owners sued for due-process violations after discovering they’d been spending lots of money complying with a zoning code that nobody had actually adopted. Tenth Circuit: The county may well have violated something, but it wasn’t the Fourteenth Amendment.
- Owasso, Okla. officer fired for stepping on handcuffed arrestee’s head, striking arrestee in the face with his elbow — but is reinstated by state appeals court. Can the officer sue city officials for releasing video of the incident, purportedly in retaliation for his union activities? The Tenth Circuit says no. (Related: The officer will soon face trial for a separate instance of excessive force.)
- When sonography students at public college expressed misgivings about requirement that they submit to transvaginal ultrasounds, staff belittled them and threatened to have them banned from area hospitals. Eleventh Circuit: Which could have been retaliation for protected speech. Moreover, students can press Fourth Amendment claims even though the search in question was neither administrative nor investigatory.
- Back in July, the Eleventh Circuit overturned a Miami nightclub owner’s convictions on all but one count arising from scheme wherein Eastern European women lured men staying in luxury hotels to his club to buy wildly overpriced drinks. This week: No need for a panel rehearing, the owner isn’t guilty on the last wire-fraud count either. (Fourteen other defendants (probably): Man, we should not have pled guilty.)
- Financial adviser takes advantage of elderly clients to the tune of $142k. District court: I’d sentence her to time served if she could come up with the $142k, but, as she cannot, she’s going to prison instead. Eleventh Circuit: Conditioning one’s freedom on her ability to pay is probably unconstitutional, but there’s no need to reach that issue. It’s certainly not permissible under federal sentencing guidelines.
Terry and Ria Platt’s son was caught with cash and a small amount of marijuana in their car — something that does not give rise to forfeiture in Arizona. But Navajo County prosecutors, who stand to reap the proceeds, want to take the car anyway. When the Platts petitioned for their car back, prosecutors rejected their paperwork (because the words “under penalty of perjury” were not included along with their signatures) and labeled the forfeiture “uncontested,” a designation that prevents the Platts from objecting in court and allows the government to proceed with a process that the Arizona Supreme Court admits “virtually assur[es] a forfeiture.” This week, the Platts joined forces with IJ to challenge the constitutionality of Arizona’s forfeiture machine. Read more about the case here.
 The Hidden Persuaders project has interviewed neuropsychologist Tim Shallice about his opposition to the British government’s use of ‘enhanced interrogation’ in the Northern Ireland conflict of the 1970s – a practice eventually abandoned as torture.
The Hidden Persuaders project has interviewed neuropsychologist Tim Shallice about his opposition to the British government’s use of ‘enhanced interrogation’ in the Northern Ireland conflict of the 1970s – a practice eventually abandoned as torture.
Shallice is little known to the wider public but is one of the most important and influential neuropsychologists of his generation, having pioneered the systematic study of neurological problems as a window on typical cognitive function.
One of his first papers was not on brain injury, however, it was an article titled ‘Ulster depth interrogation techniques and their relation to sensory deprivation research’ where he set out a cognitive basis for why the ‘five techniques’ – wall-standing, hooding, white noise, sleep deprivation, and deprivation of food and drink – amounted to torture.
Shallice traces a link between the use of these techniques and research on sensory deprivation – which was investigated both by regular scientists for reasons of scientific curiosity, and as we learned later, by intelligence services while trying to understand ‘brain washing’.
The use of these techniques in Northern Ireland was subject to an official investigation and Shallice and other researchers testified to the Parker Committee which led Prime Minister Edward Heath to ban the practice.
If those techniques sound eerily familiar, it is because they formed the basis of interrogation practices at Guantanamo Bay and other notorious sites in the ‘war on terror’.
The Hidden Persuaders is a research project at Birkbeck, University of London, which is investigating the history of ‘brainwashing’. It traces the practice to its use by the British during the colonisation of Yemen, who seemed to have borrowed it off the KGB.
And if you want to read about the modern day effects of the abusive techniques, The New York Times has just published a disturbing feature article about the long-term consequences of being tortured in Guantanamo and other ‘black sites’ by following up many of the people subject to the brutal techniques.
Link to Hidden Persuaders interview with Tim Shallice.
Link to NYT on long-term legacy of war on terror torture.

(credit: Jürgen Telkmann)
Update (12:04p ET): A second wave of DDoS attacks against Dyn is underway, as of noon Eastern Time today. Dyn is continuing to work on the issue. Our original story follows below; further updates will be added as information becomes available.
A distributed denial of service attack against Dyn, the dynamic DNS service, affected the availability of dozens of major websites and Internet services this morning, including Twitter and Reddit. The attack, which began this morning at 7:10am Eastern Time (12:10pm UK), is apparently focused on Dyn’s US East Coast name servers.
“This morning, Dyn received a global DDoS attack on our Managed DNS infrastructure in the east coast of the United States,” Doug Madory, Director of Internet Analysis at Dyn, said in an e-mail sent to Ars this morning. “DNS traffic resolved from east coast name server locations are experiencing a service interruption during this time.” By 9:20am ET this morning, Dyn had mitigated the attack and services returned to normal.
Interesting side effect of the #DynDNS #DDOS SPF checks fail, so @twitter emails were put in my spam folder. pic.twitter.com/POHpHTQEJ6— Rik van Duijn RCX (@rikvduijn) October 21, 2016
OpenDNS retains cached DNS records during NS failures, no problems on Internet for me. Here's their servers.— SwiftOnSecurity (@SwiftOnSecurity) October 21, 2016
208.67.222.222
208.67.220.220
Criminals this morning massively attacked Dyn, a company that provides core Internet services for Twitter, SoundCloud, Spotify, Reddit and a host of other sites, causing outages and slowness for many of Dyn’s customers.
Twitter is experiencing problems, as seen through the social media platform Hootsuite.
In a statement, Dyn said that this morning, October 21, Dyn received a global distributed denial of service (DDoS) attack on its DNS infrastructure on the east coast starting at around 7:10 a.m. ET (11:10 UTC).
“DNS traffic resolved from east coast name server locations are experiencing a service interruption during this time. Updates will be posted as information becomes available,” the company wrote.
DYN encouraged customers with concerns to check the company’s status page for updates and to reach out to its technical support team.
A DDoS is when crooks use a large number of hacked or ill-configured systems to flood a target site with so much junk traffic that it can no longer serve legitimate visitors.
DNS refers to Domain Name System services. DNS is an essential component of all Web sites, responsible for translating human-friendly Web site names like “example.com” into numeric, machine-readable Internet addresses. Anytime you send an e-mail or browse a Web site, your machine is sending a DNS look-up request to your Internet service provider to help route the traffic.
The attack on DYN comes just hours after DYN researcher Doug Madory presented a talk on DDoS attacks in Dallas, Texas at a meeting of the North American Network Operators Group (NANOG). Madory’s talk — available here on Youtube.com — delved deeper into research that he and I teamed up on to produce the data behind the story DDoS Mitigation Firm Has History of Hijacks.
That story (as well as one published earlier this week, Spreading the DDoS Disease and Selling the Cure) examined the sometimes blurry lines between certain DDoS mitigation firms and the cybercriminals apparently involved in launching some of the largest DDoS attacks the Internet has ever seen. Indeed, the record 620 Gbps DDoS against KrebsOnSecurity.com came just hours after I published the story on which Madory and I collaborated.
The record-sized attack that hit my site last month was quickly superseded by a DDoS against OVH, a French hosting firm that reported being targeted by a DDoS that was roughly twice the size of the assault on KrebsOnSecurity. As I noted in The Democratization of Censorship — the first story published after bringing my site back up under the protection of Google’s Project Shield — DDoS mitigation firms simply did not count on the size of these attacks increasing so quickly overnight, and are now scrambling to secure far greater capacity to handle much larger attacks concurrently.
The size of these DDoS attacks has increased so much lately thanks largely to the broad availability of tools for compromising and leveraging the collective firepower of so-called Internet of Things devices — poorly secured Internet-based security cameras, digital video recorders (DVRs) and Internet routers. Last month, a hacker by the name of Anna_Senpai released the source code for Mirai, a crime machine that enslaves IoT devices for use in large DDoS attacks. The 620 Gbps attack that hit my site last month was launched by a botnet built on Mirai, for example.
Interestingly, someone is now targeting infrastructure providers with extortion attacks and invoking the name Anna_senpai. According to a discussion thread started Wednesday on Web Hosting Talk, criminals are now invoking the Mirai author’s nickname in a bid to extort Bitcoins from targeted hosting providers.
“If you will not pay in time, DDoS attack will start, your web-services will
go down permanently. After that, price to stop will be increased to 5 BTC
with further increment of 5 BTC for every day of attack.NOTE, i?m not joking.
My attack are extremely powerful now – now average 700-800Gbps, sometimes over 1 Tbps per second. It will pass any remote protections, no current protection systems can help.”
Let me be clear: I have no data to indicate that the attack on Dyn is related to extortion, to Mirai or to any of the companies or individuals Madory referenced in his talk this week in Dallas. But Dyn is known for publishing detailed writeups on outages at other major Internet service providers. Here’s hoping the company does not deviate from that practice and soon publishes a postmortem on its own attack.
Update, 3:50 p.m. ET: Security firm Flashpoint is now reporting that they have seen indications that a Mirai-based botnet is indeed involved in the attack on Dyn today. Separately, I have heard from a trusted source who’s been tracking this activity and saw chatter in the cybercrime underground yesterday discussing a plan to attack Dyn.
Update, 10:22 a.m. ET: Dyn’s status page reports that all services are back to normal as of 13:20 UTC (9:20 a.m. ET). Fixed the link to Doug Madory’s talk on Youtube, to remove the URL shortener (which isn’t working because of this attack).
Update, 1:01 p.m. ET: Looks like the attacks on Dyn have resumed and this event is ongoing. This, from the Dyn status page:
This DDoS attack may also be impacting Dyn Managed DNS advanced services with possible delays in monitoring. Our Engineers are continuing to work on mitigating this issue.
Oct 21, 16:48 UTCAs of 15:52 UTC, we have begun monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Our Engineers are continuing to work on mitigating this issue.
Oct 21, 16:06 UTC
Earlier this month a hacker released the source code for Mirai, a malware strain that was used to launch a historically large 620 Gbps denial-of-service attack against this site in September. That attack came in apparent retribution for a story here which directly preceded the arrest of two Israeli men for allegedly running an online attack for hire service called vDOS. Turns out, the site where the Mirai source code was leaked had some very interesting things in common with the place vDOS called home.
The domain name where the Mirai source code was originally placed for download — santasbigcandycane[dot]cx — is registered at the same domain name registrar that was used to register the now-defunct DDoS-for-hire service vdos-s[dot]com.
Normally, this would not be remarkable, since most domain registrars have thousands or millions of domains in their stable. But in this case it is interesting mainly because the registrar used by both domains — a company called namecentral.com — has apparently been used to register just 38 domains since its inception by its current owner in 2012, according to a historic WHOIS records gathered by domaintools.com (for the full list see this PDF).
What’s more, a cursory look at the other domains registered via namecentral.com since then reveals a number of other DDoS-for-hire services, also known as “booter” or “stresser” services.
It’s extremely odd that someone would take on the considerable cost and trouble of creating a domain name registrar just to register a few dozen domains. It costs $3,500 to apply to the Internet Corporation for Assigned Names and Numbers (ICANN) for a new registrar authority. The annual fee for being an ICANN-approved registrar is $4,000, and then there’s a $800 quarterly fee for smaller registrars. In short, domain name registrars generally need to register many thousands of new domains each year just to turn a profit.
Many of the remaining three dozen or so domains registered via Namecentral over the past few years are tied to vDOS. Before vDOS was taken offline it was massively hacked, and a copy of the user and attack database was shared with KrebsOnSecurity. From those records it was easy to tell which third-party booter services were using vDOS’s application programming interface (API), a software function that allowed them to essentially resell access to vDOS with their own white-labeled stresser.
And a number of those vDOS resellers were registered through Namecentral, including 83144692[dot].com — a DDoS-for-hire service marketed at Chinese customers. Another Namecentral domain — vstress.net — also was a vDOS reseller.
Other DDoS-for-hire domains registered through Namecentral include xboot[dot]net, xr8edstresser[dot]com, snowstresser[dot]com, ezstress[dot]com, exilestress[dot]com, diamondstresser[dot]net, dd0s[dot]pw, rebelsecurity[dot]net, and beststressers[dot]com.
Namecentral’s current owner is a 19-year-old California man by the name of Jesse Wu. Responding to questions emailed from KrebsOnSecurity, Wu said Namecentral’s policy on abuse was inspired by Cloudflare, the DDoS protection company that guards Namecentral and most of the above-mentioned DDoS-for-hire sites from attacks of the very kind they sell.
“I’m not sure (since registrations are automated) but I’m going to guess that the reason you’re interested in us is because some stories you’ve written in the past had domains registered on our service or otherwise used one of our services,” Wu wrote.
“We have a policy inspired by Cloudflare’s similar policy that we ourselves will remain content-neutral and in the support of an open Internet, we will almost never remove a registration or stop providing services, and furthermore we’ll take any effort to ensure that registrations cannot be influenced by anyone besides the actual registrant making a change themselves – even if such website makes us uncomfortable,” Wu said. “However, as a US based company, we are held to US laws, and so if we receive a valid court issued order to stop providing services to a client, or to turn over/disable a domain, we would happily comply with such order.”
Wu’s message continued:
“As of this email, we have never received such an order, we have never been contacted by any law enforcement agency, and we have never even received a legitimate, credible abuse report. We realize this policy might make us popular with ‘dangerous’ websites but even then, if we denied them services, simply not providing them services would not make such website stop existing, they would just have to find some other service provider/registrar or change domains more often. Our services themselves cannot be used for anything harmful – a domain is just a string of letters, and the rest of our services involve website/ddos protection/ecommerce security services designed to protect websites.”
Taking a page from Cloudflare, indeed. I’ve long taken Cloudflare to task for granting DDoS protection for countless DDoS-for-hire services, to no avail. I’ve maintained that Cloudflare has a blatant conflict of interest here, and that the DDoS-for-hire industry would quickly blast itself into oblivion because the proprietors of these attack services like nothing more than to turn their attack cannons on each other. Cloudflare has steadfastly maintained that picking and choosing who gets to use their network is a slippery slope that it will not venture toward.
Although Mr. Wu says he had nothing to do with the domains registered through Namecentral, public records filed elsewhere raise serious unanswered questions about that claim.
In my Sept. 8 story, Israeli Online Attack Service Earned $600,000 in Two Years, I explained that the hacked vDOS database indicated the service was run by two 18-year-old Israeli men. At some point, vDOS decided to protect all customer logins to the service with an extended validation (EV) SSL certificate. And for that, it needed to show it was tied to an actual corporate entity.
My investigation into those responsible for supporting vDOS began after I took a closer look at the SSL certificate that vDOS-S[dot]com used to encrypt customer logins. On May 12, 2015, Digicert.com issued an EV SSL certificate for vDOS, according to this record.
As we can see, whoever registered that EV cert did so using the business name VS NETWORK SERVICES LTD, and giving an address in the United Kingdom of 217 Blossomfield Rd., Solihull, West Midlands.
Who owns VS NETWORK SERVICES LTD? According this record from Companies House UK — an official ledger of corporations located in the United Kingdom — the director of the company was listed as one Thomas McGonagall.
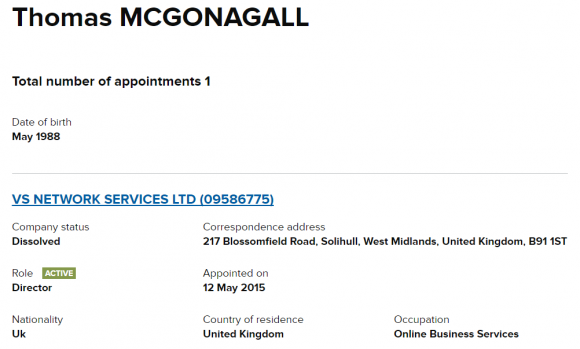
Records from Companies House UK on the firm responsible for registering vDOS’s SSL certificate.
This individual gave the same West Midlands address, stating that he was appointed to VS Network Services on May 12, 2015, and that his birthday was in May 1988. A search in Companies House for Thomas McGonagall shows that a person by that same name and address also was listed that very same day as a director for a company called REBELSECURITY LTD.
If we go back even further into the corporate history of this mysterious Mr. McGonagall we find that he was appointed director of NAMECENTRAL LTD on August 18, 2014. Mr. McGonagall’s birthday is listed as December 1995 in this record, and his address is given as 29 Wigorn Road, 29 Wigorn Road, Smethwick, West Midlands, United Kingdom, B67 5HL. Also on that same day, he was appointed to run EZSTRESS LTD, a company at the same Smethwick, West Midlands address.
Strangely enough, those company names correspond to other domains registered through Namecentral around the same time the companies were created, including rebelsecurity[dot]net, ezstress[dot]net.
Asked to explain the odd apparent corporate connections between Namecentral, vDOS, EZStress and Rebelsecurity, Wu chalked that up to an imposter or potential phishing attack.
“I’m not sure who that is, and we are not affiliated with Namecentral Ltd.,” he wrote. “I looked it up though and it seems like it is either closed or has never been active. From what you described it could be possible someone set up shell companies to try and get/resell EV certs (and someone’s failed attempt to set up a phishing site for us – thanks for the heads up).”
Interestingly, among the three dozen or so domains registered through Namecentral.com is “certificateavenue.com,” a site that until recently included nearly identical content as Namecentral’s home page and appears to be aimed at selling EV certs. Certificateavenue.com was responding as of early-October, but it is no longer online.
I also asked Wu why he chose to become a domain registrar when it appeared he had very few domains to justify the substantial annual costs of maintaining a registrar business.
“Like most other registrars, we register domains only as a value added service,” he replied via email. “We have more domains than that (not willing to say exactly how many) but primarily we make our money on our website/ddos protection/ecommerce protection.”
Now we were getting somewhere. Turns out, Wu isn’t really in the domain registrar business — not for the money, anyway. The real money, as his response suggests, is in selling DDoS protection against the very DDoS-for-hire services he is courting with his domain registration service.
Asked to reconcile his claim for having a 100 percent hands-off, automated domain registration system with the fact that Namecentral’s home page says the company doesn’t actually have a way to accept automated domain name registrations (like most normal domain registrars), Wu again had an answer.
“Our site says we only take referred registrations, meaning that at the moment we’re asking that another prior customer referred you to open a new account for our services, including if you’d like a reseller account,” he wrote.
I was willing to entertain the notion that perhaps Mr. Wu was in fact the target of a rather elaborate scam of some sort. That is, until I stumbled upon another company that was registered in the U.K. to Mr. McGonagall.
That other company —SIMPLIFYNT LTD — was registered by Mr. McGonagall on October 29, 2014. Turns out, almost the exact same information included in the original Web site registration records for Jesse Wu’s purchase of Namecentral.com was used for the domain simplifynt.com, which also was registered on Oct. 29, 2014. I initially missed this domain because it was not registered through Namecentral. If someone had phished Mr. Wu in this case, they had been very quick to the punch indeed.
In the simplyfynt.com domain registration records, Jesse Wu gave his email address as jesse@jjdev.ru. That domain is no longer online, but a cached copy of it at archive.org shows that it was once a Web development business. That cached page lists yet another contact email address: sales@jjdevelopments.org.
I ordered a reverse WHOIS lookup from domaintools.com on all historic Web site registration records that included the domain “jjdevelopments.org” anywhere in the records. The search returned 15 other domains, including several more apparent DDoS-for-hire domains such as twbooter69.com, twbooter3.com, ratemyddos.com and desoboot.com.
Among the oldest and most innocuous of those 15 domains was maplemystery.com, a fan site for a massively multiplayer online role-playing game (MMORPG) called Maple Story. Another historic record lookup ordered from domaintools.com shows that maplemystery.com was originally registered in 2009 to a “Denny Ng.” As it happens, Denny Ng is listed as the co-owner of the $1.6 million Walnut, Calif. home where Jesse until very recently lived with his mom Cindy Wu (Jesse is now a student at the University of California, San Diego).
Another domain of interest that was secured via Namecentral is datawagon.net. Registered by 19-year-old Christopher J. “CJ” Sculti Jr., Datawagon also bills itself as a DDoS mitigation firm. It appears Mr. Sculti built his DDoS protection empire out of his parents’ $2.6 million home in Rye, NY. He’s now a student at Clemson University, according to his Facebook page.
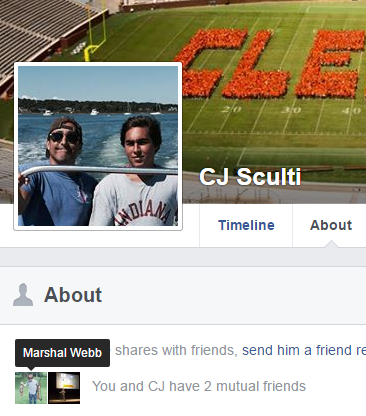
CJ Sculti Jr.’s Facebook profile photo. Sculti is on pictured on the right.
As I noted in my story DDoS Mitigation Firm Has a History of Hijacks, Sculti earned his 15 minutes of fame in 2015 when he lost a cybersquatting suit with Dominos Pizza after registering the domain dominos.pizza (another domain registered via Namecentral).
Around that time, Sculti contacted KrebsOnSecurity via Skype, asking if I’d be interested in writing about this cybersquatting dispute with Dominos. In that conversation, Sculti — apropos of nothing — admits to having just scanned the Internet for routers that were known to be protected by little more than the factory-default usernames and passwords.
Sculti goes on to brag that his scan revealed a quarter-million routers that were vulnerable, and that he then proceeded to upload some kind software to each vulnerable system. Here’s a snippet of that chat conversation, which is virtually one-sided.
July 7, 2015:
21:37 CJ http://krebsonsecurity.com/
21:37 CJ
vulnerable routers are a HUGE issue
21:37 CJ
a few months ago
21:37 CJ
I scanned the internet with a few sets of defualt logins
21:37 CJ
for telnet
21:37 CJ
and I was able to upload and execute a binary
21:38 CJ
on 250k devices
21:38 CJ
most of which were routers
21:38 Brian Krebs
o_0
21:38 CJ
yea
21:38 CJ
i’m surprised no one has looked into that yet
21:38 CJ
but
21:39 CJ
it’s a huge issue lol
21:39 CJ
that’s tons of bandwidth
21:39 CJ
that could be potentially used
21:39 CJ
in the wrong way
21:39 CJ
lol
—
Tons of bandwidth, indeed. The very next time I heard from Sculti was the same day I published the above-mentioned story about Datawagon’s relationship to BackConnect Inc., a company that admitted to hijacking 256 Internet addresses from vDOS’s hosting provider in Bulgaria — allegedly to defend itself against a monster attack allegedly launched by vDOS’s proprietors.
Sculti took issue with how he was portrayed in that report, and after a few terse words were exchanged, I blocked his Skype account from further communicating with mine. Less than an hour after that exchange, my Skype inbox was flooded with thousands of bogus contact requests from hacked or auto-created Skype accounts.
Less than six hours after that conversation, my site came under the biggest DDoS attack the Internet had ever witnessed at the time, an attack that experts have since traced back to a large botnet of IoT devices infected with Mirai.
As I wrote in the story that apparently incurred Sculti’s ire, Datawagon — like BackConnect — also has a history of hijacking broad swaths of Internet address space that do not belong to it. That listing came not long after Datawagon announced that it was the rightful owner of some 256 Internet addresses (1.3.3.0/24) that had long been dormant.
The Web address 1.3.3.7 currently does not respond to browser requests, but it previously routed to a page listing the core members of a hacker group calling itself the Money Team. Other sites also previously tied to that Internet address include numerous DDoS-for-hire services, such as nazistresser[dot]biz, exostress[dot]in, scriptkiddie[dot]eu, packeting[dot]eu, leet[dot]hu, booter[dot]in, vivostresser[dot]com, shockingbooter[dot]com and xboot[dot]info, among others.
Datawagon has earned a reputation on hacker forums as a “bulletproof” hosting provider — one that will essentially ignore abuse complaints from other providers and turn a blind eye to malicious activity perpetrated by its customers. In the screenshot below — taken from a thread on Hackforums where Datawagon was suggested as a reliable bulletproof hoster — the company is mentioned in the same vein as HostSailor, another bulletproof provider that has been the source of much badness (as well as legal threats against this author).
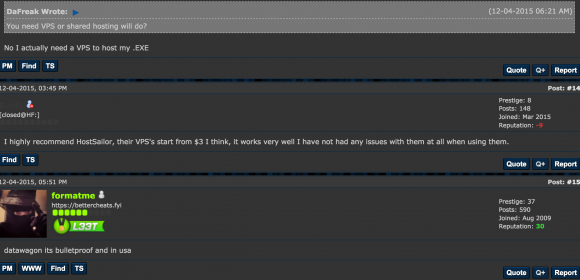
In yet another Hackforums discussion thread from June 2016 titled “VPS [virtual private servers] that allow DDoS scripts,” one user recommends Datawagon. “I use datawagon.net. They allow anything.”
Last year, Sculti formed a company in Florida along with a self-avowed spammer. Perhaps unsurprisingly, anti-spam group Spamhaus soon listed virtually all of Datawagon’s Internet address space as sources of spam.
Are either Mr. Wu or Mr. Sculti behind the Mirai botnet attacks? I cannot say. But I’d be willing to bet money that one or both of them knows who is. In any case, it would appear that both men may have hit upon a very lucrative business model. More to come.
Since Death Valley is below sea level could we dig a hole to the ocean and fill it up with water?
—Nick Traeden
Yes! We can do anything we want. We shouldn't do this, though, because it would be gross.

Death Valley is an endorheic basin[1]"Big hole" in California. The floor of the valley is about 80 meters below sea level. It contains the lowest point on land in North America[2]Excluding artificial points like mines. and is the hottest place on Earth.[3]If you're about to say "Wait, what about Liby—," then don't worry, I'm with you. Just hang on and read a few more words ahead!
Now, if you're the sort of person who's into world records, you might have heard that the hottest place on Earth was Al Azizia, Libya. Al Azizia recorded a temperature of 58.0°C (136.4°F) in 1922, a mark Death Valley has never come close to. So what gives?

It turns out Al Azizia has recently been stripped of its record. In 2010, an exhaustive—and definitely a little obsessive—investigation led by Christopher C. Burt convinced the World Meteorological Organization that the Libyan measurement was probably a mistake. This left Death Valley with the record of 56.7°C (134°F), set in 1913. Case closed!

Except it's not quite settled. Burt has raised questions about the 1913 record as well, and has gone so far as to catalog a number of historical extremes along with a credibility score for each. The "real" record is probably 53.9°C (129°F). This temperature has been recorded four times, in 1960, 1998, 2005, and 2007—every time in Death Valley.
These records were recorded with modern instruments and are considered reliable. They also make sense from a theoretical point of view. Geographers have calculated[4]This Army Corps of Engineers publication cites a couple of sources for this, including a 1963 paper by G. Hoffman. Unfortunately, that paper is in German, which I can't read, so I've just decided to trust that the Army Corps of Engineers writers Dr. Paul F. Krause and Kathleen L. Flood aren't pulling a fast one on me. that the highest possible temperature in ideal spots (in desert basins like Death Valley) during the 20th century is 55°-56°C, so 54°C sounds like a reasonable world record.
Now, back to Nick's question.[5]This is nowhere NEAR the record for "most boring digression into world record trivia." That record was recently challenged by IBM computer capable of producing millions of boring pieces of trivia per second, but the machine narrowly lost to reigning human champion Ken Jennings.

Since Death Valley is below sea level, we could, as Nick suggests, flood it with seawater. It would take a lot of digging, since there's a lot of Earth in the way. The lowest route to Death Valley is probably by traveling up the Colorado River watershed, along the Arizona border past Quartzsite,[6]Trivia: If you want to reach Quartzsite, Arizona from my school, Christopher Newport University, you just step out onto Warwick Blvd (Rt. 60) and turn left. That's it—Route 60 runs across the country, from the CNU campus in Virginia to I-10 just outside Quartzsite. then northwest[7]Possibly following one of the routes shown on page G34 in this report. past Zzyzx, which is a real place.

If you did all that digging, you could create a channel from the Gulf of California to Death Valley, and water would flow in. We can use this handy stream-flow calculator to figure out how wide we'd need to make the channel. A channel 20 meters deep and 100 meters wide should be able to fill it in a few months. A really wide channel—like the kind carved by glacial floods—could fill it in hours.
We know it's possible to create this kind of inland sea because we've done it before—by accident. In 1905, irrigation engineers working on the Colorado River made some mistakes. During a flood, the entire Colorado river broke through into the Alamo Canal and flowed directly into the Salton basin to the north. By the time they repaired the canal, two years later, the Salton basin had become the Salton Sea—one of the larger human-caused changes to the world map.
The Salton Sea is fed mainly by agricultural runoff, so it's become saline[8]"Salty" and hypereutrophic.[9]"Gross" Large numbers of dead fish, combined with algal decay and unusual chemistry, have created a smell that the US Geological Survey describes as "objectionable," "noxious," "unique," and "pervasive." The sea is a birdwatching hot spot, but also the site of a lot of mass bird die-offs, so kind of a mixed bag if you're into birds. In recent years, the water has been evaporating quickly, leaving behind dried toxic residue which is swept up into dust storms. Work to clean up and rehabilitate the region is ongoing.
All in all, the Salton Sea is a mess—and Nick wants to make another one.

Nick's Death Valley project would start off connected to the ocean, but without a source of flowing water at the Death Valley end,[10](It's a desert.) the channel would gradually silt up. The link to the ocean would eventually be broken, the sea would start to evaporate, the water would become saline, algae would bloom, and eventually the US Geological Survey would start complaining about the smell.
There would be one more consequence to all this. Thanks to the flood of cold ocean water burying the whole region, Death Valley would stop setting temperature records, and someone else would eventually claim to have broken their 129°F record. The Death Valley records would have to be compared to the newer candidates, which would probably use slightly different methods ... and that means one thing:
A World Meteorological Organization expert panel!
