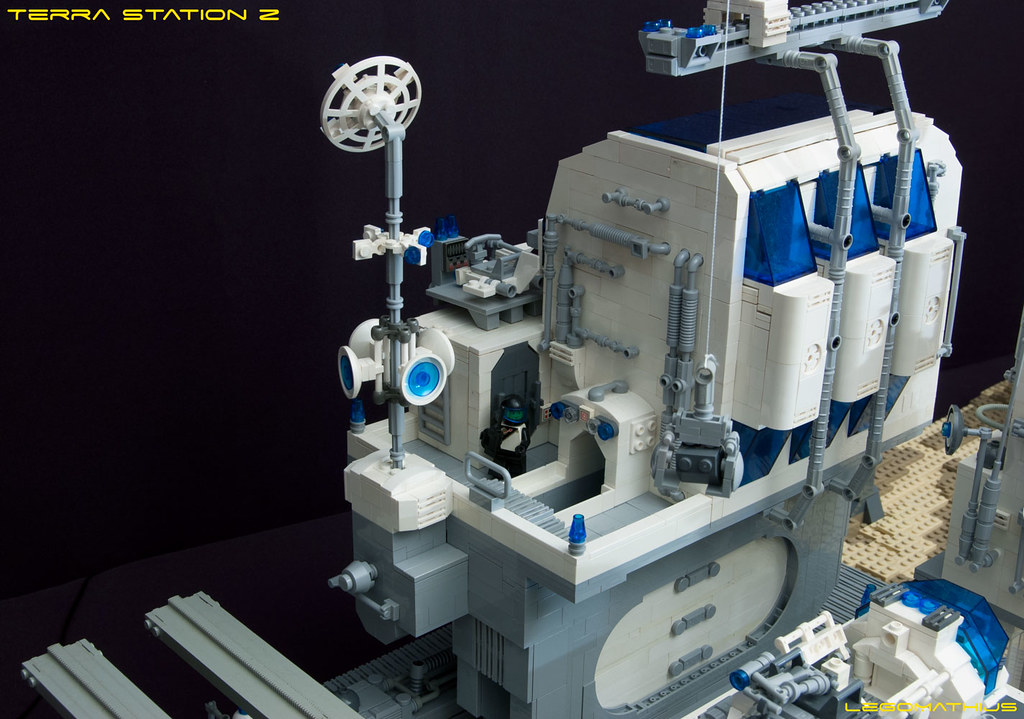
In the early 1980s, an actor named Peter Cullen told his brother Larry that he was using their shared car to go to an audition for “the voice of a hero truck.” Larry, a decorated Marine officer, gave Peter some advice on how to play an effective leader, “Be strong enough to be gentle.” Peter took Larry’s words to heart and earned the role of Optimus Prime, commander of the Autobots. The show Peter Cullen was auditioning for, The Transformers, was basically a commercial meant to sell repurposed toys from Japan to kids in America. It wasn’t supposed to create an icon. But, when Optimus Prime was killed on-screen in The Transformers: The Movie, the backlash was swift and immediate. Peter Cullen’s “strong but gentle” performance had turned Optimus Prime into something more than just an action figure in the eyes of the audience. The Transformers team quickly set to work on a series of episodes to revive Optimus Prime in Season 3 of the show, and Optimus would remain one of the few constants of the ever-evolving franchise from then on. Now, nearly forty years later, that original incarnation of Optimus Prime has been given new life once again as a fully transformable 1508-piece LEGO set. LEGO The Transformers 10302 Optimus Prime will be available June 1st, for US $169.99 | CAN $219.99 | UK £149.99

The LEGO Group provided The Brothers Brick with an early copy of this set for review. Providing TBB with products for review guarantees neither coverage nor positive reviews.
Unboxing the set and contents
Optimus Prime comes in the biggest “thumb punch” style box I’ve ever seen. The graphics follow the usual 18+ design; mostly black, with a stripe of greebling along the bottom. The LEGO and Transformers brand logos are present, but the main focal point is Optimus Prime in robot mode, wielding his Ion Blaster.

The back of the box demonstrates Optimus Prime’s transformation and shows off his various accessories: An info placard, the Autobot Matrix of Leadership, an Energon Cube, a spare bumper tile, his Energon Axe and Ion Blaster weapons, and the jetpack he borrowed from Sideswipe in that one episode.

Inside the box are a perfect bound instruction booklet, a small set of stickers, an unnumbered bag of tires, and eleven numbered bags of parts (the numbers only go up to 10, there are two bag 5s).




The instructions include notes about the franchise and some thoughts from the set designer, Joseph Patrick Kyde (who actually used to work for Hasbro on The Transformers brand before joining LEGO). There are also some facts about Optimus Prime, and The Transformers in general sprinkled throughout the building process.




There are numerous parts of interest in this set. The new 1x2x1&1/3 click socket bricks show up in red, after debuting in light-bluish gray in the Horizon Zero Dawn Tallneck set.

Also, the Technic 2×2 joint brick makes a reappearance in red after a long out-of-production stint.

The newer Technic rotation joints show up here, partnered with a brand-new joint disk that features two Technic pins protruding from the reverse side. These are used to construct Optimus’s hips.

There are also a number of bricks in metallic silver, some for the first time, to emulate the chrome parts on the original Optimus toy.

The most notable of these is a new 2×2 slope, which tapers to a point on one end, perfectly recreating the shape of Optimus Prime’s faceplate. This piece was actually designed specifically for this set, even though it first debuted in bright light orange in the Botanicals Succulents set.

The build
Usually, with sets of this size, the first several bags are devoted to laying down a sturdy frame, often in colors unrepresentative of the final model. It can take some time before the look of the model you’re building comes into focus. Not with this set. By the time you’re done with Bag 1, you’ve very clearly built Optimus Prime’s trademark truck window chest, and the functionality of his shoulder transformation is even apparent.

This pattern will continue through the building process. While there’s a lot of building to do overall, individual sections (like an upper leg for example) don’t take very long to build, which makes for lots of moments of gratification throughout the build process. Because of this, the build feels like it goes faster than it probably actually does.



This isn’t to say that it isn’t a complicated build or that there aren’t any clever techniques to be found. For instance, a set of stacked plates with free end bars peg into a pair of studs not on top bricks housed within the chest to help keep the shoulders in place during robot mode.

Prime’s lower legs make nice use of jumpers to offset a clip/bar system that keeps the legs locked together in truck mode.

And Prime’s feet make use of Technic slopes in dark blue to create a joint midfoot, so they can collapse in on themselves for truck mode.


The final steps of the main model involve creating Prime’s head, which is perfectly brought to life with plenty of dark blue pieces (including the bar holder with handle in that color for the first time). A printed tile represents Prime’s forehead crest, and his eyes are printed on the edge of a 1×2 plate.

The final model – robot mode
The resulting model is instantly recognizable as the Generation One (G1) iteration of Optimus Prime, although he’s not a dead ringer for any specific version of the character. See, back in the 1980s, what Optimus Prime (or, truly, almost any Transformer) looked like could vary wildly depending on whether you were playing with the toys, watching the TV show, or reading the Marvel comic. Heck, even some of the toy commercials featured animated designs of some characters that are unique to those 30 seconds of broadcast. All that said, this Optimus Prime splits the difference between the TV show animation model and the original toy pretty perfectly. Details like the arrows printed on 2×2 tiles at his wrists and most of the included accessories are straight from the show. Other details, like the gray stripes above his elbows and the visible wheels on his legs, are toy-specific. His shoulders feature Autobot symbols printed on 4×4 tiles with a row of studs on the edge. The exposed studs work to great effect here, reminding me of the rivets molded into the arms of the original toy.

Optimus is highly posable, as LEGO mechs go. His arms have a wide range of motion, due in large part to the needs of their transformation. His legs are less functional. While his hip joints can move forward, they’re hampered from doing so in robot mode by the truck bumper at his waist. And his legs can’t bend at the knee, likely for stability reasons. But the combination of an outward swing at his hips and an ankle tilt still allows for enough dynamic posing in the legs that he’ll look great standing on your shelf.

The back of the robot mode looks quite a bit like the original toy, with hollow space in the torso to allow for things to fold away in vehicle mode. If that’s not to your liking, this empty and undetailed space gets hidden nicely with the addition of the jetpack, which we’ll cover in a bit.

Optimus Prime’s G1 animation model kept the truck grill as his abdomen, like the original toy, but made it slope upward in robot mode. Modern Optimus toys often try to give the robot a slopped grill and the truck a flat grill by molding two different pieces and asking you to basically turn the toy inside out to hide or reveal the appropriate grill depending on which mode he’s in. This set simply puts the grill on a hinge that allows it to slope or hang flat. It’s an elegant solution that I’m surprised we haven’t seen on more Optimus toys. The truck headlights remain visible on panels that angle into the abdomen. His headlights weren’t visible in robot mode in either the cartoon or the original toy, so leaving them here is probably the most inaccurate thing this model does. But their inclusion isn’t too distracting, and the angle they’re at keeps them from interrupting the flow of Prime’s familiar torso.

Interestingly, while the upper leg detail copies the design of the animation model almost perfectly, the box images and instructions both have it upside-down. The longer rectangle should extend down from the waist, while the smaller trio of trapezoids should be just above the knee. This is easily remedied by popping off the stickered 2×6 tile from each leg and reattaching them in the correct orientation, and I’ll be doing that as soon as I’m done with this review. But for now, let’s keep the set construction “official.”

This is the largest Optimus Prime toy I own, and it might be the tallest G1 Optimus Prime figure on record. As you can see, he towers pretty easily over the first and second “Masterpiece” molds.

But he’s still second tallest when it comes to LEGO 80s robots, as Voltron stands head and shoulders over him.

Transformation
Prime’s transformation is both simple and satisfying. If you ever played with the original Optimus Prime toy, you know the basics – swing the legs back, flip the head down, swing his shoulders back, and tuck the forearms into the torso. Boom. It’s a truck. It can take a little bit of time to get everything aligned and tucked into truck mode just right, but it isn’t a terribly laborious process. And unfolding him back into robot mode is super easy. I can convert him from truck to robot mode in just a few seconds.

One of the big selling points of this model is that Prime can transform without needing any disassembly, unlike other building block attempts at the character. And while that is technically true, there is one piece that some collectors may find themselves wanting to parts-swap each time they transform Optimus. In the original cartoon, Optimus had a bright orange square in the middle of his waist. That square became gray detail on the front bumper in truck mode. To account for this magic color change, LEGO has included two 2×6 tiles stickered with the appropriate detail for each mode. Swapping them is an official step in the transformation but, if you’d prefer to ignore that step, Prime looks good sporting either tile in either mode.

Truck mode
Optimus Prime’s truck is an excellent representation of his original alternate mode. But it isn’t flawless. There are gaps in the main cab that exist to allow the arms clearance to shift in and out of position. Parts of his head are visible in the back of the cab. The headlight panels and windows don’t square up with the gray stripe to create an even plane. These sorts of imperfections are par for the course for Transformers fans, who are used to unsightly seems or visible hinges marring the look of a vehicle mode. Viewed through that lens, this is a remarkably effective alt. mode for a transforming LEGO creation. The original Optimus Prime toy towed a trailer (which tended to disappear when he turned into a robot on the TV show), and it is a touch disappointing that this Optimus is riding around without one. But his Ion Blaster does attach to the rear of the truck mode to create a trailer hitch, which opens the door for plenty of custom trailer builds.



The accessories
Speaking of Prime’s Ion Blaster, it’s time to take a look at all of this set’s accessories.

First on the agenda is probably the most important – The Autobot Matrix of Leadership. This powerful artifact is handed down from one Autobot commander to the next, and Prime carries it in a compartment in his chest, awaiting any potential deathbed bequeathing.

The Matrix is a simple, but interesting build. The main handle is a 1x6x3 rectangular bar in metallic silver, which gets sandwiched between a boat tile and some round tiles with pin holders to keep it in place. The colors aren’t entirely accurate. While the silver handle is correct, the body of the Matrix should be mostly gold or orange, with a blue center.

Next up is an Energon Cube, the Cybertronian way to transport energy. This is an obviously simple construct and, while it isn’t an inappropriate addition, it is the least specifically related to Optimus Prime. I wish there had been a consistency of color in this build – either all opaque pieces or all transparent. The mix doesn’t work for me. But mostly I wish there was an included minifigure of Autobot companion Spike Witwicky instead of this.

One of Optimus’s trademark weapons is one he only used once. In the second episode of the original cartoon, Optimus deploys an Energon Axe at the end of his arm to do melee battle with the evil Megatron. And then, I guess, he forgot he could do that and he never used it again. But that hasn’t stopped it from becoming a common accessory in Optimus Prime toys, including here. The axe easily plugs into an axle port buried in either of Prime’s wrists, after you remove the corresponding hand.

Next up is the aforementioned Ion Blaster. Prime’s most commonly used weapon is realized here in perfect detail. The butt of the gun attaches easily to two exposed studs on Optimus’s forearm. The gun handle lines up with Prime’s fist, and his fingers can sort of grip it, but the forearm connection is what really keeps the gun in place. Unfortunately, Optimus’s arm joints often aren’t sufficient to keep either the Energon Axe or the Ion Blaster hoisted up for very long, and both accessories tend to make his arms droop.

Optimus Prime’s jetpack is another accessory that got used once and then was kind of forgotten about. And, truth be told, it isn’t even really Optimus’s. He borrowed it from Sideswipe. And it wasn’t even supposed to be Sideswipe’s because he and his brother Sunstreaker had their tech specs swapped during production at some point and…
…sorry, I’m getting off-topic.

Regardless, Optimus Prime/Sideswipe’s jetpack is a great addition to the set that helps cover some of the unsightlier elements of the figure’s back, giving the model a more complete feel, no matter which angle you look at it from.

The final accessory is the placard, which features Prime’s name, function, and motto, along with his original tech spec stats. These placards are usually attached to some kind of stand for the final model to attach to, but in this case, it’s just a freestanding sign intended to be placed somewhere in the vicinity of Optimus Prime.

Conclusion and recommendation
I have to admit my biases here, although they might already be apparent. (I mean, come on…did you read the intro paragraph? All that stuff about the audition. What was I going on about?) I obviously loved LEGO as a kid, but I loved The Transformers even more. As I outgrew other toy lines, The Transformers franchise remained a constant hobby in my life. Then, about fifteen years ago, I started customizing LEGO minifigures specifically because they scaled well with my Transformers figures and I wanted some human characters from the franchise in my toy displays. That activity became the gateway that pulled me over into full Adult Fan of LEGO-dom. So, this is truly a full-circle moment for me. In a very real way, I probably wouldn’t be writing for this site if not for Optimus Prime. And now Optimus Prime is officially a LEGO set. So, in my estimation, this is not just the greatest LEGO set ever, but also possibly the greatest toy ever created. The question is: will you like it?
Well, it’s not without its flaws. It leans towards the higher side of the price/piece ratio for collector’s sets. Some of the pieces have a tendency to pop off if you’re not careful during transformation. In particular, there’s a turntable in the torso that often wants to pull itself apart under the weight of the robot mode. And the arms can’t always support the larger accessories. In fact, the entire robot mode can be a little too floppy in general when you try and handle it. It’s definitely not a figure for your kids to play with. But it’s a fantastic display piece that just might make you feel like a kid again.
For LEGO fans, this high-end, fully transformable mech is a worthy and relatively unique building experience with a decent selection of new parts and old parts in new colors. For Transformers fans, I don’t see how you can possibly live with yourself if you pass this up. Just remember to turn those tiles on the upper legs around.

LEGO The Transformers 10302 Optimus Prime will be available June 1st, for US $169.99 | CAN $219.99 | UK £149.99. It may also be available from third-party sellers on Amazon and eBay.
The LEGO Group provided The Brothers Brick with an early copy of this set for review. Providing TBB with products for review guarantees neither coverage nor positive reviews.








































 //embedr.flickr.com/assets/client-code.js
//embedr.flickr.com/assets/client-code.js