
Looks like you'll have to wait to furiously click through photos of your ex and her new, stupid boyfriend frolicking in Cabo: Facebook is down for many users.
JohnServer Updates?

You eventually tune it out, but the constant whir of a desktop computer's cooling fans can take a toll on your psyche. It's like a buzzing mosquito that never strikes, and never stops. So the folks at a German company called Silent Power have created a compact desktop PC that trades noisy fans for a block of exposed copper foam that dissipates heat so effectively no fans are required.
Michael Stevens explains why darkness moves faster than light in this new episode of Vsauce. I usually find these explainers interesting because they delve not only into multiple science disciplines but often they touch philosophical questions too. This one really blew my mind.

A team of security researchers has discovered a security flaw in Google's mobile OS which affects handsets running versions up to and including 4.4—leaving a potential 82 percent of Android users at risk.
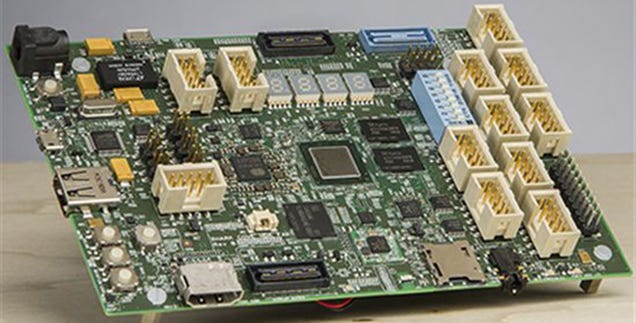
The Raspberry Pi has proved a massive success with developers and students alike—and now Microsoft has decided to get in on the act with an Atom-powered Windows board. But it fails to compete on one of the most important features: price.
JohnI still prefer to stand most of the day.
JohnMaybe this is where the missing flight went.

Russian newswire service Interfax is reporting that a Malaysian passenger plane carrying 295 people was shot down with a Buk ground-to-air missile over Ukraine near the Russian border, according to an advisor to Ukraine's Interior Minister. The advisor, Anton Gerashchenko, posted more accusations on Facebook, saying that the strike was carried out by Ukrainian rebels. He also posted a minute-long video of what supposedly is the smoking wreckage of the plane. A Reuters correspondent on the scene has confirmed the "burning wreckage of airplane, bodies on ground." A Ukrainian separatist leader, meanwhile, has blamed the crash on the Ukrainian military. President Petro Poroshenko, meanwhile, has stated that the "armed forces of Ukraine did...
JohnThey really want this to take off, don't they...

Whether it's a matter of price or functionality, robotic assistants have never really caught on. The Roomba is a genuine cultural movement, but no such luck for little bots with serious brains, the kind that sit on your desk, patiently waiting for you to come home, and ask about your day when you stroll through the door. Jibo could finally change that.
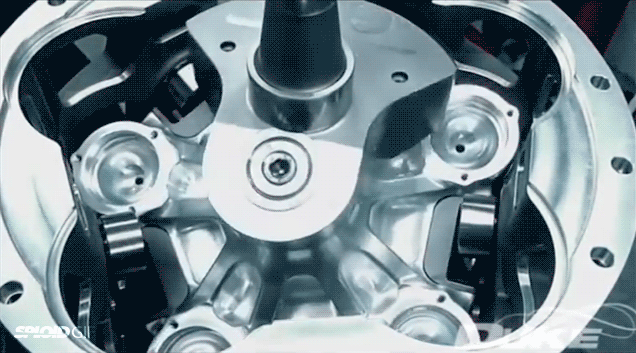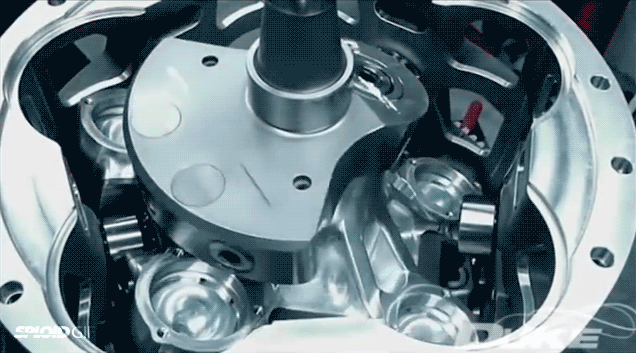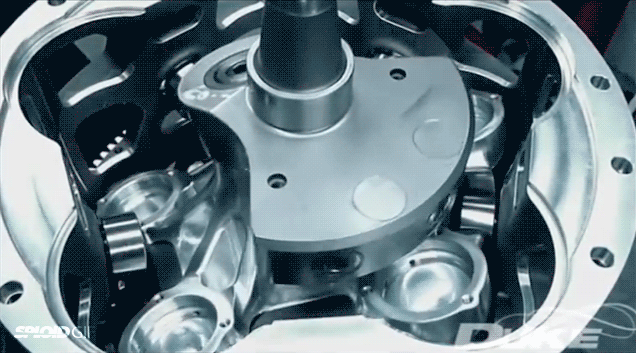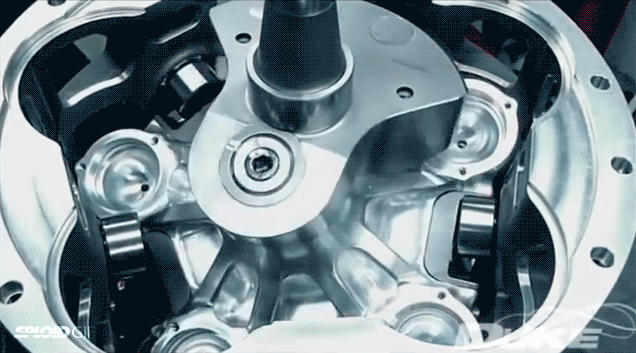
According to Duke Engineering, their axial engine is the most efficient and lightest engine you can put in boats, light aircrafts, and generators—the mechanical engine of the (near) future! Maybe. I don't know if their claims are true and I don't really care. I just love watching it in action in this eternal gif.
Today, the Raspberry Pi foundation have announced the release of an updated version of the Raspberry Pi model B, known as the B+ (the official announcement is here). There have been a couple of tweaks to the design over the past couple of years, but this is the first major revision. The big news is that it still has the same CPU, SoC and memory (which means that it should run exactly the same software as the previous version). However, there have been a number of important improvements across various parts of the board.

Many of the improvements are to an often-overlooked part of the computer, the regulator. The Raspberry Pi gets power from a micro USB port that should supply 5v. Different parts of the Pi use different voltages, so it needs some component to reduce this 5 volts down to the different levels needed. That’s the job of the regulator. The original Pi used a linear regulator. This is a simple component that reduces a voltage, and any difference between the input voltage and output voltage is converted to heat and wasted.
The model B+ uses a switching regulator. This is a slightly more complex component that converts all the input power into output power, and only wastes a small amount. In other words, the power supply on the model B was very inefficient, and this has been fixed. The difference, according to the Pi foundation is between 0.5 and 1 watt. This isn’t going to make much of a dent in your electricity bills, but it is very important.
Different USB power supplies provide different amounts of power. Usually, it’s somewhere around 5 watts. The exact power requirements of the Raspberry Pi depend on what you’re doing, but light use of the Pi is around 3.5 watts (it can be lower if you’re really trying to squeeze efficiency out of it). This increases significantly with more things plugged in, particularly USB peripherals (unless you’re using a powered hub). In practice, we’ve found that when using most power supplies, the model B becomes quite unstable if more than two USB devices are plugged in via an unpowered hub since this can result in a power draw more than the power supply can handle. With bad power supplies, even a keyboard and optical mouse are enough to trouble it. The 0.5 – 1 watt saving can be thought as extra head room for the device, and should make it far less prone to power-related crashes.
To test the model B+’s power consumption, we put it through a test. We plugged a mouse, keyboard and two USB memory sticks into an unpowered hub (although the B+ has enough USB ports for all of these, we wanted to make it a fair test with the model B which doesn’t), and tried to copy 1GB of data from one of the memory sticks to the other.
The B+ was able to do this without major problems. The model B, however, didn’t manage it at all. The power supply couldn’t handle the USB devices and they dropped in and out.
Previously, we’ve always thought of a powered USB hub as essential for everyday use of the Pi (although you can get away without it for light use, we’ve lost too much data due to power-related crashes to recommend it). With the B+, we now view the powered hub as only necessary if you’re using high-powered USB devices. Since powered hubs are often almost as expensive as the Pi itself, this knocks off a significant proportion of the total cost of a Pi setup.
A more obvious advantage of the lower power consumption is for portable devices. There are loads of battery powered applications for the Pi, but one that we come across most frequently is taking photos. We ran a simple test where we left the model B and B+ in a loop taking pictures to see which one drained the battery the quickest. We found that the B+ drained the battery about 30% slower than the B. The improvement you get will depend on exactly what your Pi is doing, but we would expect it to be around this level.

The sound output from the original model B is generally considered something of a joke. If you need reasonable quality audio, you have to use an external sound card.
The Raspberry Pi (like almost all computers) is digital. It process information in 1s and 0s, or high and low voltages. However, sound waves are analogue. That means that they vary across a whole spectrum rather than just flipping between two states. The model B had no problem processing the digital sound, however the digital-to-analogue converter (DAC) was prone to adding noise into the output that wasn’t supposed to be there.
The reason for this is that on the model B, there was a 3.3 volt supply that powered several components on the board, one of which was the DAC. If one of the other components drew current from the 3.3 volt line while sound was playing, it could cause the power supply to fluctuate slightly, and this fluctuation caused distortion to the analogue output.
On the B+, the DAC has its own power supply from the new regulator, which means there’s nothing else to make the current fluctuate and therefore the sound output is much better. There are also some other minor changes to the audio processing to make it perform better. Serious audiophiles may still want additional audio hardware, but the Pi’s sound output should now be good enough for most people.

The most obvious improvement in the B+ is the addition of two more USB 2 ports, bringing the total up to four. Without the improved regulator, these wouldn’t have been very useful since there wouldn’t have been enough power to run many peripherals. However, we found that we could run most USB peripherals. We tried to overload it with a mouse, keyboard, USB webcam and memory stick and it still worked. We even had some success with a keyboard, mouse, webcam and microphone, though we wouldn’t recommend that setup for any serious recording. For normal use of the Pi (such as with mouse, keyboard and USB memory stick), the ports should work without any problems.

After the additional USB ports, the most noticeable thing on the B+ is the additional GPIO headers. There are now 40 rather than 26 (there are actually 34 on the B, but the 8 on pad 5 don’t have headers). These provide 19 GPIOs (including pad 5) on the B and 26 on the B+. In technical terms, the whole of Bank 0 from the SoC is now exposed (and the other banks are put to work elsewhere). The first 20 of the 40 headers on the B+ are the same as the B, so some existing expansion boards should work without problems. However, because the board layout has changed, larger expansion boards that fit around the components may not fit on anymore. For example, the PiFace doesn’t. This is something that schools and workshops that already have a significant number of expansion boards may wish to consider. Since the headers just need raising to lift the expansion board above the level of the components on the board, it’s quite likely that someone will start selling adaptors for this.
The additional 7 GPIOs probably won’t have much effect on most projects since expansion boards tend to use one of the GPIO communications protocol (i2C or SPI) and these only use a few pins. If you need more GPIOs, it’s fairly trivial to use one of these protocols to drive more, and this will provide some protection for the pins on the Raspberry Pi as well. There are also no more feature pins in the GPIO, so don’t expect any more PWMs or UARTs.
One area where the extra pins could come in useful is in implementing communication protocols that need more channels. For example, the model B doesn’t have enough pins to run either DPI or SLI (protocols to communicate with displays), but the B+ does. This won’t actually be supported by the Raspberry Pi Foundation, but will, in theory, be possible should someone implement it. Hopefully we’ll see some interesting expansion boards that take advantage of the new possibilities soon.

To make space on the board, the analogue video out has gone, so there’s only HDMI output. This isn’t a big loss as we’ve never heard of anyone who actually uses this output, and it frees up quite a bit of board space.
The analogue video is now combined with the audio jack into an single AV port.
There are now four mounting holes, and they’re in a rectangle which makes them a little more useful. The USB ports no longer overhang the PCB by much (it’s now the same as the Ethernet), which should make it a little easier to make cases for the board, or fit it inside embedded devices. Perhaps the biggest of the little changes is the SD card switching from full size to micro. As well as being smaller, the new card holder feels more secure. While we’ve never came across a Pi with a broken SD card slot, the old ones never felt sturdy to us.
Despite their smaller size, microSD cards come in the same capacities as full size ones (and usually for about the same prices). Other than the size, there’s no difference between them. In fact, in our testing, we used exactly the same micro SD card in the Model B as the B+, we just put it in an adaptor when using it with the B. As long as you have the latest version of Raspbian (version 1.3.9 or higher), everything should work.

The only issue we had with the new card holder is that it is now a click in – click out style. The first time we picked up our Model B+ while it was running, we placed one finger on the SD card and another on the opposite side of the Pi (we got used to picking our old Pi up in this way). Instead of securing the SD card in place like this did on the Model B, this pushed in the microSD and clicked it, and as soon as we put it down, the card popped out. This isn’t a huge problem, just something to be aware of.
The board also gets a few aesthetic improvements. It now has rounded corners, and more importantly, most of the connectors are now marked. The camera and (as yet unused) display connector are labelled. It’s a minor improvement that will make it a little easier for newcomers.
We were able to run our test Pi in the turbo overclocking setting without problems. This is something we haven’t had much luck with on Model B’s in the past (although we have heard of plenty of people whose Pis have performed well at this setting). We’ve only been sent one B+ to test, so we obviously can’t extrapolate and say that the B+ performs better in this regard. If they do, it’ll be a welcome performance improvement for many people.

We asked Eben Upton what he thought the best feature of the B+ was. He said “A lot of equal weight small changes that add up to a big one […] The extra USB and GPIO are the big win.” We respectfully disagree. While these are important, the new regulator is the most important feature for us. To be able to handle lots more input and output means this is a significantly more useful computer, and will be especially important for new users who may not have a great power supply or a powered USB hub.
For any aspiring computer designers out there, this is a real lesson in the fact that computer performance is about more than just CPU, memory and storage. The manner in which you connect them has a huge influence on the final product.
This model comes out almost two and a half years after the first Pi, yet it still uses the same CPU and memory. This obviously begs the question, will we be seeing an updated CPU and memory Pi? We put this to Eben Upton. He replied “Yes in the future – obviously – but not immediately. This is the final revision of the Pi One. It clears the decks for a notional Pi two in the future.” He also confirmed that they are looking at an improved version of the model A, but said that they hadn’t fully decided what form it would take.
If you’re set up with a model B and everything works fine for you, then there’s really no need to upgrade, unless you are particularly interested in audio or lowering your power consumption. However, if you’re getting a new Pi, the B+ really is a much better computer. Model B’s will continue to be available, but these are really only useful for people who have designed hardware that won’t fit with the new Pi.

Elon Musk can no longer say that no one's ever died in a Tesla automobile crash. But few people will be pointing fingers at the electric car maker for this senseless tragedy. Earlier this month, 26-year-old Joshua Slot managed to successfully ride off with a Model S he'd stolen from a Tesla service center in Los Angeles, but police quickly spotted the luxury vehicle and gave chase. According to Park Labrea News, the high-speed pursuit was eventually called off after officers were involved in a fender bender of their own, leaving the police department strained for resources and without any feasible way of catching up to Slot. Reports claim he was traveling at speeds of "nearly 100 mph," but losing the police tail apparently didn't...

Police dogs have been helping helping their human counterparts identify contraband for years — sniffing out drugs, bombs, cash, and suspects. Now they can add hard drives to the list. As reported by the Providence Journal of Rhode Island over the weekend, state police now have a dog named Thoreau capable of smelling concealed hard drives, thumb drives, memory cards, and other electronic storage media. The dog is supposed to help officers hunt for child pornography. Thoreau, a Golden Labrador, already helped arrest one suspect in June, locating a thumb drive containing child porn hidden in a tin box inside another metal cabinet. "If it has a memory card, he’ll sniff it out," Detective Adam Houston, Thoreau’s handler, told the Journal.

Chromecast's new mirroring feature lets users pull up an Android phone screen onto a TV. And why would you want to put your little screen on your bigger screen? If game maker Rolocule has its way, to play Nintendo Wii-like games without bothering with a console.
Security researchers confirmed on Monday that a vicious new cyberattack has compromised the computer systems of over 1,000 organizations in 84 countries. Dubbed "Energetic Bear," the Stuxnet-like malware is largely targeting energy and utility companies. It's almost certainly from Russia.
JohnThis is actually, really interesting.

A small software app called Onionshare offers the most secure file sharing available. So why hasn't anyone heard of it? Well, mostly because it was released with just a tweet from its creator, and you have to go to Github to download it. But don't let its underground status fool you—this is a very important app.
With online banking becoming routine for most users, it comes as no surprise that we are seeing more banking malware enter the threat landscape. In fact, 2013 saw almost a million new banking malware variants—double the volume of the previous year. The rise of banking malware continued into this year, with new malware and even new techniques.
Just weeks after we came across banking malware that abuses a Window security feature, we have also spotted yet another banking malware. What makes this malware, detected as EMOTET, highly notable is that it “sniffs” network activity to steal information.
The Spam Connection
EMOTET variants arrive via spammed messages. These messages often deal with bank transfers and shipping invoices. Users who receive these emails might be persuaded to click the provided links, considering that the emails refer to financial transactions.

Figure 1. Sample spammed message

Figure 2. Sample spammed message
The provided links ultimately lead to the downloading of EMOTET variants into the system.
Theft via Network Sniffing
Once in the system, the malware downloads its component files, including a configuration file that contains information about banks targeted by the malware. Variants analyzed by engineers show that certain banks from Germany were included in the list of monitored websites. Note, however, that the configuration file may vary. As such, information on the monitored banks may also differ depending on the configuration file.
Another downloaded file is a .DLL file that is also injected to all processes and is responsible for intercepting and logging outgoing network traffic. When injected to a browser, this malicious DLL compares the accessed site with the strings contained in the previously downloaded configuration file.
If strings match, the malware assembles the information by getting the URL accessed and the data sent. The malware saves the whole content of the website, meaning that any data can be stolen and saved.
EMOTET can even “sniff” out data sent over secured connections through its capability to hook to the following Network APIs to monitor network traffic:
Our researchers’ attempts to log in were captured by the malware, despite the site’s use of HTTPS.

Figures 3 and 4. Login attempt captured by the malware
This method of information theft is notable as other banking malware often rely on form field insertion or phishing pages to steal information. The use of network sniffing also makes it harder to users to detect any suspicious activity as no changes are visibly seen (such as an additional form field or a phishing page). Moreover, it can bypass even a supposedly secure connection like HTTPs which poses dangers to the user’s personal identifiable information and banking credentials. Users can go about with their online banking without every realizing that information is being stolen.
The Use of Registry Entries
Registry entries play a significant role in EMOTET’s routines. The downloaded component files are placed in separate entries. The stolen information is also placed in a registry entry after being encrypted.
The decision to storing files and data in registry entries could be seen as a method of evasion. Regular users often do not check registry entries for possibly malicious or suspicious activity, compared to checking for new or unusual files. It can also serve as a countermeasure against file-based AV detection for that same reason.
We’re currently investigating how this malware family sends the gathered data it ‘sniff’ from the network.
Exercising Caution
Latest feedback from the Smart Protection Network shows that EMOTET infections are largely centered in the EMEA region, with Germany as the top affected country. This isn’t exactly a surprise considering that the targeted banks are all German. However, other regions like APAC and North America have also seen EMOTET infections, implying that this infection is not exclusive to a specific region or country.
As EMOTET arrives via spammed messages, users are advised not to click links or download files that are unverified. For matters concerning finances, it’s best to call the financial or banking institution involved to confirm the message before proceeding.
Trend Micro blocks all related threats.
With additional insights from Rhena Inocencio and Marilyn Melliang.
Update as of July 3, 2014, 2:00 A.M. PDT:
The SHA1 hash of the file with this behavior we’ve seen is:
Post from: Trendlabs Security Intelligence Blog - by Trend Micro
New Banking Malware Uses Network Sniffing for Data Theft

On July 22, 1962, at 9:20 PM, the Mariner I sat idly on its platform, ready to make history. After investing years of construction, calculation, and funding, NASA had high hopes that its rocket would successfully conduct a flyby survey of Venus, thus shifting the Space Race's momentum back to the home front. In every way, it was poised to set a space travel precedent.
In Issue 5 of Linux Voice, we take a look at the ways hackers break into websites. It’s important to understand these methods because it lets you know how to defend yourself. So, to help you understand the issues in computer security, we’re setting up a Moodle (https://moodle.org/) server that you can practice on, and we’re running a competition to try and find as many security bugs in Moodle as possible to help improve the security of this open source software.
The competition starts on 29th June 2014. We’ll update this site with more information then.

We’ve chosen Moodle because it’s a mature, secure open source product that’s already been well tested for vulnerabilites so we don’t expect there to be any easy ways in. However, even the most secure pieces of software have a few chinks in their armour. We want you to help find those chinks in the armour so that they can be fixed, and the product will be even better.
If you’re new to the world of web security, there are loads of ways to get started. Issue 5 of Linux Voice goes through some of the most common exploits and is now on sale in the UK (and soon online as well), and subscribers should have access to the digital version (the paper version is on its way). The Damn Vulnerable Web Application (http://www.dvwa.co.uk/) comes as a PHP project or a liveCD (which can run in a virtual machine), and it has loads of vulnerabilities that are easy to exploit. If you get stuck, there are loads of examples and walk throughs available in a quick web search. There is more information on the different types of attack on the Open Source Web App Security Project (OWASP) site at https://www.owasp.org/index.php/Top_10_2013-Top_10. If you want to get a head start, you could always download Moodle and start taking a look at it.
In each case, the winner will receive a Linux Voice winner’s t-shirt. These exclusive t-shirts are only available to winners of Linux Voice competitions.

Google's biggest event of the year, the I/O 2014 developers conference in San Francisco, was interrupted today by a stark reminder of the growing class divide in the city: a protester shouting about evictions allegedly caused by a Google employee. The protester, whose identity has yet to be confirmed, began shouting in the middle of Android engineering director Dave Burke's talk at San Francisco's Moscone Center. She held up a T-shirt that read "develop a conscience, stop Jack Halprin," as seen in the photo above and below.

Forget the Ouya , there's another Android game console in town, and it's coming from two of the biggest players in computing.