Shared posts
Your login form posts to HTTPS, but you blew it when you loaded it over HTTP
Here’s an often held conversation between concerned website user and site owner:
User: “Hey mate, your website isn’t using SSL when I enter my password, what gives?!”
Owner: “Ah, but it posts to HTTPS so your password is secure! We take security seriously. Our measures are robust.” (and other random, unquantifiable claims)
Loading login forms over HTTP renders any downstream transport layer security almost entirely useless. Rather than just tell you what’s wrong with this, let me show precisely why this is with a site that implements this pattern:
How’s that for simple?! What people forget about SSL is that it’s not about encryption. Well that’s one feature of secure sockets, another really essential one is integrity insofar as it gives us confidence that the website content hasn’t been manipulated. Anything you load over an HTTP connection can be easily changed by a man in the middle which is why it’s absolutely essential to load those login forms over a secure connection. OWASP is very specific about this in part 9 of their Top 10 web application security risks and summarise it well in the transport layer protection cheat sheet:
The initial login page, referred to as the "login landing page", must be served over TLS. Failure to utilize TLS for the login landing page allows an attacker to modify the login form action, causing the user's credentials to be posted to an arbitrary location.
It’s not just Woolworths doing this, in fact it’s extremely common and you’ll see it on GoDaddy:

On Pandora:

And even on the Financial Times:
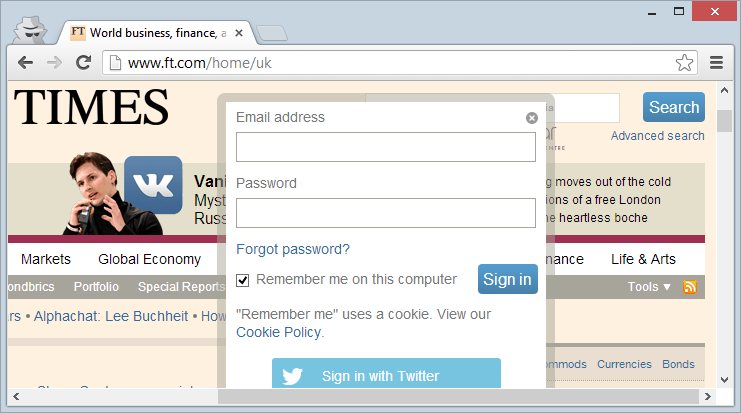
I’m calling out these simply because they’re high-profile sites yet they all load the login forms over HTTP and post to HTTPS. Why aren’t they implementing SSL correctly? Most likely convenience; customers can login direct from the homepage and they can have it delivered over HTTP. Mind you Pandora links off to a login page so why they couldn’t just serve that securely to begin with is a bit of a mystery.
So how should it be done? Load the login form over HTTPS, either by linking to a dedicated login page or popping it up in a separate window (although there’s a UX argument against this). Even better, just load the whole site over HTTPS! Yes, there are some barriers to HTTPS across the board (managing certs in web farms, dependencies on assets from third parties, impact on CDNs, etc) but it sure solves the login form issue. Check out Netflix’s approach – straight into HTTPS, job done!
The other issue with the examples above is that potential manipulation of the content aside, missing HTTPS on the login form leads to exactly the discussion this post opened with – users not believing their credentials are protected. All the messaging we’ve been delivering to website users since the early days of the web about checking for the padlock in the browser address bar goes down the drain because it’s simply not there! There’s no assurance that their credentials will be protected and it’s a real shame to dilute such an important security message.
As for how the exploit in the video works, it’s just a simple Fiddler script to inject the keylogger before the body tag closes off. The keylogger itself is over on Google Code, the only code I wrote to incorporate it was the script tags you saw at the end of the video and the “Hack Yourself” website which receives the logged keys. It really is that simple.
Whilst Fiddler is good for demonstration purposes, clearly an actual weaponised attack would work differently but the principle is the same: When unencrypted traffic passes through a node on the network – NIC, ethernet cable, router, proxy, ISP, etc. – it may be observed or manipulated by an attacker. This isn’t theoretical, there are many precedents such as the Tunisian government harvesting Facebook credentials en mass.
This is all a bit odd really, I mean these sites have gone to the effort of implementing some SSL but then blown it by loading those login forms over HTTP. As we saw with Woolworths, posting over a secure connection is completely useless if there’s no integrity in the login form itself, an attacker may already have the credentials by then if the connection is compromised which is the very risk they all implemented SSL to protect from in the first place!
Will Smith, DJ Jazzy Jeff, Alfonso Ribeiro Reunite, Sing "Fresh Prince" Theme Song
Jaden Smith and Graham Norton were there, too — but mostly OMG Fresh Prince reunion!! (It’s also the return of the Carlton Dance.)


Of course there was a Carlton dance.

'Arrested Development' Chicken Dance Compilation
That Racist Ice Cream Truck Song
Here’s a random creepy fact: one of the tunes that float out of ice cream trucks all summer is a racist song called “Nigger Love a Watermelon Ha! Ha! Ha!,” first recorded 1916 or before. Have a listen.
During slavery, the African population’s supposed taste for watermelon was used to suggest that they were stupid. As I wrote in an earlier post:
…defenders of slavery used the watermelon as a symbol of simplicity. African Americans, the argument went, were happy as slaves. They didn’t need the complicated responsibilities of freedom; they just needed some shade and a cool, delicious treat.
Googling around, I learned almost nothing about the song. It seems clear that it’s not an inside joke between Black people, making fun of the stereotype. Instead, it’s an earnest, intended-to-be-humorous song meant to make fun of Black people. But I could find little contextualizing information. I also don’t know if the tune was also set to other lyrics that were or weren’t racist.
Still, the fact that the tune is an ice cream truck classic reveals how our racist history is still part and parcel of our everyday lives.
Hat tip to Theodore Johnson.
Lisa Wade is a professor of sociology at Occidental College. You can follow her on Twitter and Facebook.(View original at http://thesocietypages.org/socimages)
Photo Series Visits Abandoned Star Wars Film Sets in the Tunisian Desert
![]()
In September 2010, visual artist and filmmaker Rä di Martino set out on a quest to photograph and document old abandoned film sets in the North African deserts. The project had started when she discovered that it was common practice to abandon these sets without tearing them down, leaving them fully intact and crumbling over time, like archeological ruins.
Martino spent that month traveling around Chott el Djerid in Tunisia, finding and photographing three Star Wars sets in all for her photo series No More Stars and Every World’s a Stage.
Actually finding the sets wasn’t as easy as you might think. At first, Martino had only Google Maps as her guide, and when you’re in the desert, that just won’t do. It was only after a chance encounter with a driver who knew the desert well and a detour to ask directions at a police station that she finally stumbled upon her subject.
After finally reaching the so-called “ruins” of Luke Skywalker’s childhood, Martino spent the morning shooting on both digital and film, surprisingly moved by the memories of her own childhood that the set brought to the surface:
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Interestingly enough, after the photos were published, Star Wars fans annoyed with the disheveled state of Skywalker’s fictional home spent $11,000 and worked with locals to restore the old set. Now tourists who are brave enough to explore the Tunisian desert may find themselves in a pristine slice of Tatooine history if they’re lucky.
To see more from Martino, including more photos from other well-known and abandoned film sets, check out her website here.
(via Laughing Squid)
Image credits: Photographs by Rä di Martino and used with permission.
What Do Medieval Nuns and Bo Jackson Have in Common? Full Transcript
[MUSIC: Artist Name, “Song Title” (from Album Title)]
Lisi OLIVER: It probably was pretty darn painful because you’re not living in a world with good razors. The chances are what they’re using is kitchen cutlery I would imagine. And that is not necessarily all that sharp. I can’t imagine how painful it was.
[MUSIC: Jaquemin de Senleches, “En attendant esperance conforte, ballade” (from Ce Diabolic Chant)]
Stephen DUBNER: That’s Lisi Oliver. She studies medieval law at Louisiana State University. What do you think she’s talking about that was so “darn painful”?
OLIVER: Between the 5th and the 12th century in Early Modern Europe, barbarity swept through the continent and also the island of England. And often the targets of these attacks were monasteries and nunneries. But nunneries you had the added incentive of rape to add to sort of pillage and destruction.
DUBNER: For a nun, rape was especially problematic, aside from the obvious reasons. Rape violated a nun’s chastity — which meant that, as a bride of Christ, she might be forbidden entry into Heaven. So what do you do if you’re a nun and there are barbarians at the gate? In the ninth-century, one nun, an abbess who came to be known as St. Ebba, came up with a plan. Here is Lisi Oliver reading from a history by Roger of Wendover.
[MUSIC: Michael and Spider / Smoke and Mirrors, “Indra the Rainmaker”]
OLIVER: “The abbess with an heroic spirit took a razor and with it cut off her nose together with her upper lip up unto the teeth, presenting herself a horrible spectacle to those who stood by. Filled with admiration at this admirable deed, the whole assembly followed her maternal example and severally did the like to themselves. When this was done, together with the morrow’s dawn, the pagan attackers came. On beholding the abbess and the sister so outrageously mutilated and stained with their own blood from the sole of their foot unto their head, they retired in haste from the place. Their leaders ordered their wicked followers to set fire and burn the monastery with all its buildings and its holy inmates. Which being done by these workers of iniquity, the holy abbess and all the most holy virgins with her attained the glory of martyrdom.” There’s a very graphic picture of St. Ebba cutting her nose and lip off, and all the women around her looking thrilled at the concept. In terms of pain it must have been dreadful to cut your nose off at night and then wait until the morning with that pain racking your body. But, that is the pain of martyrdom; it is the crown of thorns.
[MUSIC: Moruza, “Garden In The Sand” (from Moruza)]
DUBNER: I know it’s hard to transpose oneself to a different time and place, but if you could put yourself back in a nunnery, do you think that you would have followed suit and gone ahead and cut off your own nose to spite your face?
OLIVER: Probably.
DUBNER: Why?
OLIVER: I think there is a wave of hysteria that follows that kind of action where I don’t think I would have been number two but I probably would have been number 20. I mean, it’s the happening thing man, we’re all cutting our noses off, right?
DUBNER: Now, why are we telling you this grisly tale? Because the theme of today’s show is spite. As in “cutting off your nose to spite your face.” Scholars aren’t certain, but this phrase quite likely originates with the practice of medieval nuns like St. Ebba. Women who mutilated themselves in an attempt to preserve their chastity. Now, economics is all about tradeoffs — everything has a cost and a benefit. What do you make of the nuns’ tradeoff? Was it worth it?
[THEME]
[MUSIC: Teddy Pressberg, “My Bird Can Fly” (from Blueprint of Soul)]
ANNOUNCER: From WNYC and APM, American Public Media, this is Freakonomics Radio, the podcast that explores the hidden side of everything. Here’s your host, Stephen Dubner.
DUBNER: Today’s show is about spite. We’re going to look at why people sometimes try to hurt others even when it’s very costly to themselves. It struck me that spite is, in some ways, an economic concept. So I called up an economist I know, Steve Levitt. He’s my Freakonomics friend and co-author, teaches at the University of Chicago.
Steve LEVITT: So when I think about spite as an economist, the way I would think of spite is that it is the response of an individual who has been wronged in some way by another who then is willing in the future to pay a large cost in order to punish the person who wronged him in the first place. So in a strange sense it’s not a very economic concept because in general we don’t think that people are going to be overly willing to pay a lot of costs themselves to punish other people.
DUBNER: Yeah, I think what you described is more revenge than spite though.
LEVITT: So maybe I don’t even know what spite is. What is spite?
Benedikt HERRMANN: Excellent question. Well it’s not so easy indeed to define spite.
DUBNER: That’s Benedikt Herrmann. He’s also an economist, originally from Germany. Now he works as policy officer for the European Commission. He’s done a lot of research on anti-social behavior. You might in fact call him a scholar of spite.
HERRMANN: Let’s have an easy start here and define spite as a behavior where an individual is ready to harm him or herself at own cost to harm somebody else without creating anything good for a third party for anyone outside, because you could sometimes be nasty to somebody just because he or she has misbehaved and you would like to do it in a kind of educational way, which then I would not call spite.
DUBNER: Because it’s not costing you anything?
HERRMANN: No, if I’m punishing somebody who has misbehaved to the community, to our group, if I punish him or her at own cost it could look like spite, but it’s not spite because it’s an educational momentum. You’re trying to get somebody who’s done something bad to behave better in the future. So it’s a kind of moralistic way of punishing, a moralistic way of being aggressive. And so it’s not a kind of spite I’m after. I’m after the kind of behavior where somebody would harm others with for no reason, for no moral reason, apart from something that might satisfy him or herself only.
[MUSIC: Vagabond Opera, “Ganef” (from The Zeitgeist Beckons)]
DUBNER: Traditional economics argues that most people try to satisfy their self-interest, to maximize their profits and opportunities. Economists have a name for this model of self-interest: Homo economicus. But within that framework, spite is a bit puzzling. Why would someone pay outsized costs for no benefit other than to hurt someone else? Well, Benedikt Herrmann thinks that the idea of Homo economicus is a bit archaic. He prefers a different term:
HERRMANN: Homo rivalis, yes indeed.
DUBNER: Homo rivalis. Meaning that humans are driven, at our core, by competition rather than simple self-interest. Homo economicus wants to get as much as possible for himself; Homo rivalis just wants to make sure he gets more than the other guy. In other words, as much as we like to think that we are absolute animals, we are in fact relative animals. Now, we know this in part through the experimental games that economists like to play. One of the classics is called the Ultimatum game. Here’s Steve Levitt again.
LEVITT: So the ultimatum game is a little experimental game that the behavioral economists have developed in which two players come into the lab and they’re completely anonymous. They’ll never meet each other. It’s a one-shot game. And one player is given, say, $10 and they’re allowed to divide that $10 however they’d like between themselves and the other player. That other player is then informed about the way in which the division has occurred and is given a choice. They can either accept the division—say, $7 for the person who’s splitting the pot and $3 for me. Or I have another option, say no I prefer both of us to get zero. So what you always face a choice between as the recipient of this ultimatum is I can accept what the person offered me or I can have us both get zero. And empirically what we see is that rarely will anyone accept an offer that’s less than 20 percent. So if the person who splits the pot divides it more unevenly than 75-25, you’re almost guaranteed to have it rejected, even though the rejecter is giving up the 25 or the 20 percent of their own money in order to take the 75 or 80 percent away from you.
DUBNER: Now to an economist this might seem perplexing. Why am I willing to throw away 2 or 3 of my dollars just to make sure that you don’t get 7 or 8? Well, maybe it’s because I feel you’ve wronged me by splitting the pot so unevenly. But remember what Benedikt Herrmann said earlier about spite. True spite, as he sees it, is not motivated by a desire to punish someone’s bad behavior. So he wanted to see how people behave absent such a moral incentive. He and a colleague came up with an experiment.
[MUSIC: Donvision, “Waiting For You”]
HERRMANN: So let me quickly try to explain here on the radio how this experiment works. So you would be invited to our experiment like many other students. You don’t know each other. You come to our lab inside, you have to sit behind computers, you’re requested not to talk with anyone during the whole experiment.
DUBNER: So you’re paired with another player but you don’t see that person. You each get $10 and then you’re given an option—if you surrender $1 of your money, you can destroy $5 of the other person’s wealth. Now, there’s no revenge going on here; there wouldn’t seem to be anything for you to gain by destroying the other person’s money. But as Benedikt Herrmann found, about 10 percent of the players did take that option. Hermann calls such a player a “difference maximizer.”
HERRMANN: That means that we want to maximize the payoff differential between the opponent and us. So maybe in a more picturesque way…being aware that we are losing our trousers for the sake and for the hope that the opponent will lose both the shirt and trousers.
DUBNER: In other words, some people were always willing to cut off their noses to spite the other player. Herrmann was perplexed by this finding, and he tried the experiment in a variety of versions, a variety of settings, different parts of the world, different kinds of societies. But in each case, he found that a surprising number of people would give up some of what was theirs for the sole purpose of taking something away from someone else.
DUBNER: And what are you as the researcher thinking? Are you thinking this is remarkably surprising, sad, strange, irrational? What is your…I mean, on the one hand you must be excited because for the sake of a paper it’s a fascinating finding.
HERRMANN: That’s exactly…These are the two souls of a researcher. Of course on the one side, you said it very nicely, you are very excited. But on the other side of course you start thinking oh my God, who the heck are we, we the humans? For me the outcome of all this research is definitely a kind of sadness and also worry that we can be too fast, we humans, we can get too fast into intergroup conflicts, which don’t make any sense to anyone, that we start to harm each other, that we start innocent people to kill each other for something that at the end of the day could have been decided in a much more reasonable way.
[MUSIC: The Jaguars; “Snake Charmer” (fromThe Jaguars)]
DUBNER: Now, as interesting as this may be—as believable as it may be—Steve Levitt warns us not to make too much of lab experiments like these. It’s hard to extrapolate from a lab setting to the hurly-burly of the real world.
LEVITT: When people are in the lab, they’re completely anonymous, it’s the only time we’ll ever play. But the real world isn’t usually like that.
DUBNER: Indeed. So, after the break, we’ll get back to the real world, see if we can find a story where someone willingly gives up money, and not just a few bucks, like in these lab games, but lots and lots of bucks, in order to prove a point.
Dave O’CONNOR: Well, the contract he was offered was five years, $7.66 million.
DUBNER: That’s coming up, on Freakonomics Radio.
[UNDERWRITING]
[MUSIC: Nicholas Tremulis, “Just Drive” (from Chicago Rapid Transit)]
ANNOUNCER: From WNYC and APM, American Public Media, this is Freakonomics Radio. Here’s your host, Stephen Dubner.
DUBNER: We are talking today about spite. About actions that hurt someone else but are especially costly to ourselves. Dave O’Connor is a filmmaker with Radical Media in New York. He was the executive producer of a documentary film made for ESPN called “You Don’t Know Bo”. The Bo in question is Bo Jackson.
[BO JACKSON SPORTS CALLS]
O’CONNOR: Bo was probably the single greatest athlete of his generation. Two-sport star, football and baseball, and was just a transformative athlete. He just physically, there’s something about his presence that feels different than normal human beings.
[SUPER BO]
[MUSIC: Melani L Skybell, “Days Like This” (from Just A Chase Away)]
DUBNER: In the spring of 1986, Bo Jackson was playing his senior year of college baseball, at Auburn.
O’CONNOR: He showed signs of being a very highly valued Major League Baseball player.
Bo JACKSON: I’m tearing the cover off the ball. I’m batting over 400, I don’t know how many home runs I was sitting on then.
DUBNER: That’s Jackson himself, from the film. Now, he had just completed his senior season of college football, which had gone even better. Dave O’Connor again:
O’CONNOR: Football, his senior year is one of the all-time great seasons of a running back in college football. He rushes for nearly 1,800 yards. He wins the Heisman Trophy and basically enshrines himself as a legend of college football. Sort of the common wisdom was that Bo will be the No. 1 draft pick in football, he will probably not play baseball at all, and if he does, somebody should pick him in the 20th round or 30th round on a flyer just in case.
DUBNER: Right, you don’t want to waste a pick on a guy who’s going to be playing football.
O’CONNOR: Right.
DUBNER: So while finishing up his college baseball career, Jackson starts getting courted by NFL teams. The football draft happens before the baseball draft. The No. 1 overall NFL pick is held by the Tampa Bay Buccaneers, who are owned by a man named Hugh Culverhouse. The Bucs have made it clear that they want Bo Jackson.
BO JACKSON: I was all gung-ho, and I had taken a few trips to visit some teams my senior year. I got the okay to go visit Tampa Bay. Hugh Culverhouse sent his jet to Columbus airport, drove over, got on the jet went to Tampa Bay for my visit. It was almost like a college visit when you’re a high school senior and you’re going to visit the college and they get some of the players to show you around town, to show you the night spots, take you to a nice restaurant, and entertain you. About four or five days later, I’m back at Auburn, getting ready for my baseball game. And I walked out on the field, I had to walk from the athletic department across the parking lot, across the street to the baseball field. And as I get to the gate to come around the dugout, Coach Baird approaches me. He said Bo, can I talk to you for a second? I said, “Sure, coach.” He said let’s go behind the dugout, let’s go sit and talk. I said, alright. So we go behind the dugout, and I’m thinking that he’s gonna tell me hey some big league team wants to sign me. And he said, did you take a trip last week on Hugh Culverhouse’s jet to go down and visit Tampa? I said yes and the folks checked and said it was okay they checked with the NCAA and said that it was okay to do that. He said well Bo, somebody didn’t check and the NCAA has declared you ineligible for any more college sports, so you can’t play baseball no more. And I sat there on that ground and I cried like a baby. I cried like a baby.
[MUSIC: Laura Ault, “Right It In a Song” (from The Greatest Thing)]
DUBNER: Bo Jackson immediately felt that he’d been wronged. He loved baseball, and even though it looked like he was going to play football professionally, he was distraught about being barred from finishing out his college baseball career. And what’s more, he became convinced that Hugh Culverhouse, the Tampa Bay owner, had done this to Bo on purpose.
JACKSON: Because the officials at Tampa Bay told me personally yes we checked and they said that it was okay, I think it was all a plot now just to get me ineligible from baseball ’cause they saw the season that I was having, and they thought that they were gonna lose me to baseball. And if we declare him ineligible, then we got him.
[MUSIC: Ruby Velle & The Soulphonics, “The Man Says” (from It’s About Time)]
DUBNER: Now, we don’t know whether the Bucs actually meant for this to happen. But it certainly did seem to work out well for them. They were in line to pick Bo Jackson No. 1 in the NFL draft and pay him so much money that he’d forget about baseball in a heartbeat. There was just one problem. Bo Jackson isn’t the forgetting type.
JACKSON: And I said there is no way I’m signing with Tampa Bay. And I told Hugh Culverhouse I said you draft me if you want, you gonna waste a draft pick, I said I promise you that. And Hugh Culverhouse well, this is what I’m gonna offer you as a signing bonus and you’re gonna take it whether you want it or not. I said alright. They didn’t think I was serious. And I sat down after baseball season was over, I talked to my baseball coach, I said coach, a lot of people don’t think I’m serious about playing baseball. I said but, if Tampa Bay drafts me, I said on my honor, and I’m looking you in your eye man to man, I’m playing baseball. So if you know any teams out there that’s interested in an outfielder, you let ‘em know.
DUBNER: In the NFL draft that April, Tampa Bay did select Bo Jackson with the No. 1 pick, which was attached to a $7.66 million, five-year contract. And then, a couple months later, Bo Jackson was selected in the baseball draft, in the fourth round, by the Kansas City Royals. They offered him three years at just $1 million. The choice would seem obvious. But Bo doesn’t know obvious. He rejects the football offer and he takes the baseball offer. How surprising is this? Here’s Dave O’Connor again.
O’CONNOR: Unprecedented. It just doesn’t happen. You can’t…I mean, money talks. You have $7.6 million sitting there and you sign a contract for 1. That’s a rare occurrence.
DUBNER: It sounds like a decision that very few people that I know at least would have made. Do you think that was an act of spite on Bo Jackson’s part?
O’CONNOR: It’s interesting because I think Bo would say that he did the honorable thing and that he has a code. But when you look at it on its surface, it is spite. There is no rational explanation for walking away from that kind of money. He’s not just hurting himself here. He’s also doing this to hurt Tampa Bay. The opportunity cost of losing a first round draft pick isn’t just that Bo Jackson isn’t playing on my team. It’s that every other player I could have selected with that pick is not playing on my team either. So, it’s a huge impact to Tampa Bay not to mention the public relations nightmare of going out on a limb and selecting somebody and not getting him.
DUBNER: So Jackson does sign with the Royals. He starts the year in the minor leagues, but by the end of the season he makes the Major League team. He’s on track for a nice baseball career. And then, the next year, he becomes eligible to reenter football. Now, will he play? Nobody knows. But the Los Angeles Raiders draft him in the seventh round. He signs and suddenly he’s playing two professional sports. At the end of the baseball season, he’d jump straight into football. And he became a star in both. He also becomes a household name in part because of his athletic feats, and in part because he was the star of one of the most beguiling ad campaigns in history, “Bo Knows,” for Nike.
[“BO KNOWS” COMMERCIAL]
O’CONNOR: Bo could surf, Bo could rollerblade, Bo could not play ice hockey, that was the one thing that they couldn’t, they couldn’t agree to let him actually be able to do. Gretzky shakes his head and says…
GRETZKY: No!
O’CONNOR: But pretty much everything else. Volleyball, tennis, running, lifting weights, aerobics, all kinds of stuff.
Bo DIDDLEY: Bo, you don’t know Diddley!
DUBNER: Alright, so we agree that Bo Jackson’s athletic career turned out pretty well, remarkable on some dimensions, but overall not one of the greatest ever because it wasn’t long enough perhaps. We agree that because he was such an unusual athlete in two sports he became this icon and the focus of a remarkable and probably quite remunerative ad campaign, right? We agree on this so far?
O’CONNOR: Yes.
DUBNER: Do we therefore agree that had this catastrophe not happened with him, with getting drafted for the NFL by a team that out of spite or something like spite he turned down, that if that had not happened that all the rest may not have happened?
O’CONNOR: Yeah, it think that’s a plausible argument to make, because he probably, had he signed that deal with Tampa Bay, if he doesn’t get injured, he probably becomes one of the best running backs in NFL history, but that’s probably it.
DUBNER: I mean honestly, my takeaway lesson here is spite pays.
O’CONNOR: Yeah, you would say…I mean, if you take a look at where he ends up, spite certainly paid in his case.
[MUSIC: Reid Willis, “Cub” (from Born of Kaleidoscope)]
DUBNER: So here’s a question worth thinking about. If spite indeed exists, is it something that we humans have always carried around in our genetic code, or did we pick it up along the way?
E.O. WILSON: We’re a very biological organism. And we’ve inherited an awful lot, in fact most of the basic emotions that guide us, from our animal and Paleolithic early human past.
Katherine WELLS: That is E.O. Wilson. He’s a renowned biologist and author.
DUBNER: And that’s Katherine Wells, she’s a producer on our show. Katherine, you had a chat with Professor Wilson, yes?
WELLS: I did, it was cool. So I called him up because I wanted to know where all of this self-destructive spite comes from. You know, is this a common behavior throughout nature, or are we unusual in it? And I have to say that just assumed that we would be the meanest creatures in existence, given everything we’ve heard today, but Wilson said that wasn’t true.
WILSON: Oh no, we’re only moderately mean.
WELLS: Now, E.O. Wilson has done a lot of thinking about the origins of human behavior. And he thinks the nastiness that we see in animals might give us a clue to why we act the way we do.
WILSON: There’s a case that comes quickly to mind, for example, of a kind of spider in which the mother has a brood of spiderlings, and when they’re born she sits down and lets the little spiderlings eat her. There are a couple cases in the ants where the workers have a huge gland of poisonous material containing it. And when they get into a tough fight, they’re able to contract their abdomens and explode their abdomens so the sticky poison covers the enemy. It can disable several enemies doing that by giving its life.
WELLS: The list this kind of behavior goes on and on.
WILSON: I mean, things that you really don’t want to think about too much before you go to sleep. You might have nightmares. But here’s the story about spite. If we define spite as doing harm to someone else, at the cost of harm to yourself, and that involves a surrender of some advantage or emotional reward on your part, you’ve given up in order to hurt somebody else, that might not exist.
WELLS: In nature?
WILSON: It’s very difficult to find any case in the great encyclopedia of animal aggression where it doesn’t give some advantage to the individual doing the aggression. But it’s very rare that an animal would deliberately injure itself just in order to create injury in another individual without any further gain to itself, to deliberately do that. I think spite does not exist in the animal kingdom.
WELLS: In the way that it does in humans, is that right?
WILSON: Well, let’s take humans. When a person injures himself or herself, say in reputation, in diminishing wealth, causing their own early death, whatever it is, in order to harm another person, you would say oh that’s spite, that’s got to be spite. But, it really would be true spite in my mind as opposed to mere risk taking, or trade off for one kind of gain in exchange for one kind of loss taken if you can’t see a gain. And that’s hard to imagine. Even vengeance has its gain, has a strong emotional award. For example, if you harm yourself and your reputation by vicious gossip, by manipulation, by cheating, whatever, you accept that if the damage you can do benefits you in some other way or benefits say particularly your own offspring in a particular way. You know, like unscrupulous stage moms, murderesses of a cheerleading champion competitors. I think you get the drift. Even a mass murderer who goes out and harms a lot of people is taking some benefit, emotional benefit from that when suicide is intended, a lot of mass murderers are just a terrible form of suicide in which the person decides to get the satisfaction in advance of committing it, and maybe the satisfaction the person will get in striking out against something they imagine to have been their enemy and diminished them before. So, when you add that factor, maybe real spite doesn’t exist.
[MUSIC: Sarah Schachner, “Phone Call”
WELLS: So, I don’t know whether this is a relief or not. I mean, the idea that spite might not even exist seems good, but the fact that we get personal satisfaction out of hurting other people? I told Wilson that was kind of a bummer.
WILSON: That just shows you’re not a psychopath.
WELLS: I’m a total wuss.
WELLS: But here’s the upside. Spite is not the only motivation we have for being self-destructive. There’s actually another: altruism. When we hurt ourselves, we aren’t always doing it just to hurt someone else. Sometimes, we’re doing it to help.
WILSON: One of the things that makes us human is our internally conflicted nature, confliction, our ambivalence to our own selves. We are constantly wrestling with our own conscience and with a tendency to deviate from social norms in a risky way, and to do wrong, to be selfish. The contest within us, between doing the moral thing, even the heroic thing on one side and doing the selfish, perhaps even criminal thing on the other side, that contest is what gives us such a continuously conflicted nature. If we went and became completely altruistic then we would be like ants. If we went to the opposite extreme and had complete lack of constraint and it was complete individualism, then we would have chaos, we would not have order, the group would dissolve. So we have to be in the middle. This appears to be the human condition.
LEVITT: It’s funny listening to him talk about that.
DUBNER: That’s Steve Levitt again. He took a class with Wilson when he, Levitt, was an undergrad at Harvard; he’s very fond of the way Wilson thinks.
LEVITT: There could be no two disciplines closer than evolutionary biology and economics. They study different questions and they use different methods, but the way that evolutionary biologists think is exactly like the way that economists think. Both are very much a model of behavior, of individual behavior, and individual behavior that’s motivated by costs and benefits. The other thing is that at its heart, both economics and evolutionary biology strive for simplicity. The simplest story which can explain a set of facts is the one we gravitate to. As opposed to other disciplines. History, history is all about complexity. And you know, literature is all about complexity. Even sociology I think at heart is about complexity. But economics is about simplicity.
[MUSIC: Laura Ault, “I Wouldn’t Do This To You” (from The Greatest Thing)]
DUBNER: Like E.O. Wilson, Levitt thinks that spite, true spite, may not really exist. Because that would mean that I hurt you even though I get nothing for it—nothing. And while it may seem that I get nothing, I probably get something.
LEVITT: What I would say about spite…I would say this: To know that an act is spite, you have to be inside the head of the perpetrator. Because the idea of spite is that it’s being done without benefit. But it’s interesting because one of the first premises of economics is you can never really know what other people are thinking and why they’re doing what they’re doing. Instead we focus on what they do. And so consequently, my view is, forget about what’s going on inside of other people’s heads—you’ll probably never know what it is—and focus on what they’re actually doing.
DUBNER: Do you see altruism as sort of the flip side of the coin to spite and therefore not quite real?
LEVITT: Altruism is exactly the flip side of spite in the sense that there are acts which very well could be altruistic, but equally could be done in a perfectly self-interested way. Both make you feel really good. And it feels good to help other people sometimes, and it feels so good to punish other people who have wronged you. So I think they’re both actually completely consistent with the idea of people doing the best they can.
DUBNER: And what about you personally, Levitt, do you get more satisfaction generally from helping people or punishing people?
LEVITT: I’m a lover, not a fighter. You know that, Dubner. I like to help people.
[CREDITS]
Twitter - Characters exceeding the 140 limit are highlighted in...
How to Raise Money When You’re Not in a Major VC Market
I travel the country a lot. And I am often approached by entrepreneurs in cities which don’t have a vibrant VC community. They often ask whether they have to move to SF, NY or LA to get financed.
 I have the same response always, “Where do you want to live? Where do you want to build your community, your relationships, your family?” I’m trying to get a feel for their commitment to local community versus being in a place where financing is easiest.
I have the same response always, “Where do you want to live? Where do you want to build your community, your relationships, your family?” I’m trying to get a feel for their commitment to local community versus being in a place where financing is easiest.
If their commitment to staying local is weak I normally say, “Well, it certainly would be easier on you to be in a larger community. It would be easier in terms of getting access to angels, VCs, the media, whatever. So if you’re really indifferent you might consider it.” On the other hand, if they have a strong preference to staying local I usually tell them that I believe you can build a business anywhere these days.
You can build a meaningful company just about wherever these days. Just ask the people of Portland, Seattle, Boulder, Iowa, Princeton, Dallas or countless other cities that don’t have enough venture capital.
Ask SuperCell. Or Rovio. Or UrbanAirship. NewToy, Dwolla, Pollenware or Wonga.
If you don’t live in a major VC zone, I have some tips for how to make it easier to raise Venture Capital.
Before I explain, let me give you some backgrounds why it’s harder to raise money if you live outside “the zone.”
Let’s start with “oversight.” Most VCs view it as their responsibility to mentor, debate, cajole and generally assist with investments they make. They also view it as a responsibility of the money they manage on behalf of others to provide oversight of these companies. And it is significantly easier to help when you are local.
Take me for example. This afternoon (Saturday) I have a coffee meeting with a portfolio company founder. Tomorrow I’m meeting with a senior exec who is considering joining a company in which we’ve invested. He would be a very senior hire for us and filling an urgent gap. I know local talent. I know who is perceived as good and who has a fancy resume but others think didn’t perform. That’s what local allows. I know the whole ecosystem: VCs, CEOs, tech teams, founders, angels – and I know people who have worked together for 15+ years.
Local knowledge runs deep. Thus, a desire to invest more locally where I think I have a competitive advantage. Otherwise I’m just money.
But I do invest outside of LA. Examples include DataSift (San Fran & London), MyTime (SF) and awe.sm (SF).
Every year I’m in the SF Bay Area 12-14 times. I’m in NY 6-8 times. And then there are smatterings (Dallas 2x, DC 3x, Philly 3x, Austin, Boulder, Seattle not to mention San Diego 8x, Santa Barbara 8x – where I invested in RingRevenue).
This isn’t a complaint. It’s a goal to help you understand the life of a VC. And I no longer control my calendar. When DataSift sets up a board meeting (next one in London, last was in NYC) we have investors from NYC (IA Ventures), SF (Scale Ventures) and the founding team + chairman in London. So when dates & locations are set – they’re set.
So ….
Am I looking to add 8 trips / year to [name your location not already on my annual itinerary]. Not easily. Of course if it’s a company on fire I would travel to any 2-hop city from LA.
So how do you overcome that given that all VCs must have a similar pattern to me other than super-human VCs like Brad Feld or Dave McClure who have insane travel schedules but an unbelievable ability to put in the air miles and be whenever/ whenever?
Here’s what I would do if I were you. I’ll pick a mythical company in Kansas City.
- For starters I’d try to raise my initial capital locally
- Next I’d research every VC in the country and find people who grew up in or near KC. Why? Because you know they must already come back 1-2 times / year anyways. Plus, they know the local market better and therefore don’t have the uninformed biases of those that don’t. If these people work for reputable firms and have the right industry knowledge they ought to be on your pitch list
- Importantly … I would pitch investors in SF, NY, Boston, LA, etc. and say the following
“I live and work in Kansas City. I have the tremendous advantage of access to a hard-working, loyal and technical talent pool. So I want to stay here and build my business.
That said I want the best VCs in the industry and for that I know I need to be in a major VC hub.
So here’s the deal. I will commit to traveling to NYC seven times per year for board meetings. I’ll make your life easier because I know you travel all the time anyways and KC ins’t exactly on your normal path.
Heck. I need to be in NYC a lot anyways. All I would ask is that you hold 1-2 board meetings / year in KC.
You’re going to want to do that anyways to always kick the tires of the local team. Plus, we have some rocking bbq to make it worth your time.”
I know some people will cringe at this idea, “if the VC really wanted me they would come to ME.”
Maybe. But until you’ve achieved the kind of success you know you’re capable of, it’s a harder ask. And with my strategy, you take their biggest objection off the table. By the way, no VC will ever tell you, “I don’t want to come to KC 8 times / year” because it would sound bad.
But as I always tell entrepreneurs, “Better That You Deal with The Elephant in the Room.“
Apple's nex gen iphone is said to have fingerprint recognition
The first thing that comes to mind is the ol' ‘unlock device’ scenario. That’s boring. But if the device recognizes independent fingers on the fly, then we can map individual fingers to secure data in the cloud.
eg. Using a friends phone (and your recognized finger) you can call and text using your private address book, the second we detach the data dissolves. You could pull up your favorite songs on the index finger, and store draft documents to your pinky.
Just thinking out loud. Could be cool.
Pineapple Surprise! Mixing trusting devices with sneaky Wi-Fi at #wdc13
I’m pushing the “Publish” button on this just before I go on stage at Web Directions Code because all things going well, what I’m going to talk about in this post will form part of my demo about securing web services.

I’m making some (admittedly very simple) code available and providing some resources that will hopefully help everything I talk about with regards to unprotected wireless traffic make sense. I’d like to begin by introducing you to Pineapple Surprise!
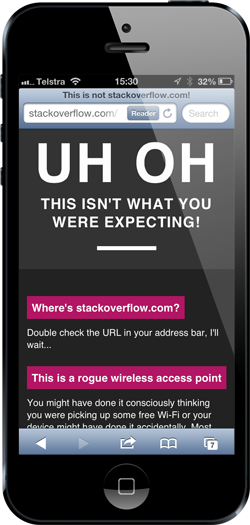
Wait – what?! Where’s my Stack Overflow?! I mean I’m seeing stackoverflow.com in the address bar, what’s going on here?! It gets worse:
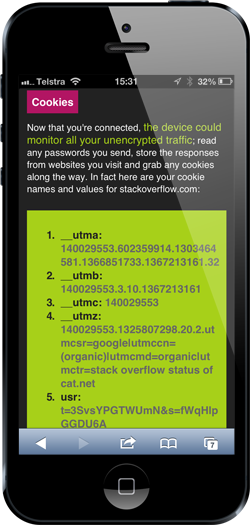
That little usr cookie down the bottom – that’s the money shot. Create a cookie in the browser with that name and value while the session is active (yes, it has expired just in case you were wondering) and wammo! You’re now me on Stack Overflow. You can go and respond to every security question about encryption and tell them to use ROT13, you can abuse Jon Skeet for not knowing his covariants from his contravariants and you can respond to any question about “How do I use ASP.NET to…” by telling them to use SharePoint. Except it’s not you saying that, it’s me and I’ll cop the abuse for it.
Let me explain what’s happening here.
All your Wi-Fis are belong to the Pineapple
This is all the work of the Wi-Fi Pineapple which I initially wrote about a couple of weeks back in The beginners guide to breaking website security with nothing more than a Pineapple and then again a few days ago in Your Mac, iPhone or iPad may have left the Apple store with a serious security risk. It’s this little guy here:

You can go and read the detail in those posts so I won’t repeat too much of it here beyond saying that this little device can trick trusting phones, tablets, laptops and anything else that can auto-connect to an open (i.e. no Wi-Fi password) known Wi-Fi access point (which is pretty much everything) into connecting to it instead. What many people don’t realise is that their wireless devices are constantly sending out “probe” requests looking for networks it has previously connected to (secured or not) and would like to connect to again. Just walking around yesterday morning with the Pineapple resulted in 315 unique SSID’s being probed for, sometimes by multiple different unique MAC addresses (the amusing ones are in bold):
#HKAirport Free WiFi, #WiFi@Changi, @yvrairport, _FREE Wi-Fi by inlink., 120wire, 14 Stewart Gibson Place, 2WIRE361, 474Labs-N, 4ten.net, ABC_PSK, ABC_WIFI, ACCESS-StarHub (2 MACs), aconex-wifi, AdshelWifi, Airport Free Wifi, ajfisher, allen, Anchors Aweigh, AndroidAP (3 MACs), AndroidAP5, AndroidHotspot1982, AnthB, ANU-Access, Apple Demo, Apple Store (3 MACs), Auckland Wi-Fi @ Tomizone, Aussieville, AUVIC-AEGIS-WIRELESS00, Axiom 5, B715 (2 MACs), BAIADAWL03, BAIADAWL04, BALoungeWiFi, BAMBI, bazillion, BBY Guest, BigPond022391, BigPond1D0761, BigPond47C6, BigPond4C0F55, BigPondD3DFA4, BigPondD7E713, BIPAC, BLERG, BlingBlingNet, Bliss, BO-AP03, Bordo, Brayza, BTHomeHub2-7J2T, BYOD, Cafe Caldera, CafeScreen_Free_WiFi, camphone, CCLA-HOTSPOT, Centre Wireless, chelagarto, ChinaNet-E3Ex, ChinaNet-Starbucks, ci+reactor, CiscoA4309 (2 MACs), CITWIRE, COKE Zero FREE WiFi, Colonial-One, Connect Free WiFi, Connect2UoM, Crush, Dan's White 64GB 4S, Darling Harbour Hotel2, db155, deblank, deblank2, deblanks, default, DEL C:, devgeeks (2 MACs), DH Studio, dh-int2, DigProd-Mixed, DigProd-N, DJ_Corp, dlink, Dodo, Dragonfly, DrayTek, DWLaptop, E583C-27a3 (2 MACs), Earth-shattering Kaboom!, Eden, Elfin, Emerald Hotspot, f9sml9fX, Fanta Wi-Fi, Finch, FinPa New Media, Flightfox.com, FLOATdroid, fluffyland, fontenayDL001, Four Points by Sheraton, Free wifi (5 MACs), free-hotspot.com, FreeSkydeckWifi1, FRITZ!Box Cubitt, Fuck-Off, FWMM2, FWMM2-guest, GAGAWAVE, Galactica, Galactica Guest, Gareth Edwards...s iPhone4, GoogleGuest (3 MACs), hahd.fr (Cette), Havana, Hertzpert, HH-GUEST, hhonors, Holiday Inn Public Wireless (2 MACs), HollerWF, home, home2ng8wlanv, HOTEL BRUNY FREE INTERNET, Hotelpuri.com, Hotspot-TXL, HTC Portable Hotspot (2 MACs), Hypnotoad, ibahn, Ibis, ii005745primary, iMac G5, Inspire9 (2 MACs), inteddies, Internode (2 MACs), Io, iROOM-Akama 2, ISIS, J and P, j74eX5drDdgf, James's iPhone, Jason, JOHNDEBLANK-PC_Network, JScamp2012, JSConf EU 2012, Kevin Yank...s iPhone, KINWOWLAN (2 MACs), KIT-GUEST (2 MACs), kylevermeulen, L n J, LAX OneWorld Lounge, LAX-WiFi, Link (2 MACs), linksys_reception, linuxconfau, Little Shed, LittleWireless, lovenest, LtBourkeSt, Luana 1207, Macquarie Public, MagicJohnston, Marty McWiFi, MAXSPOT, MAYA, McDonald's FREE WiFi, Melbourne Virgin Lounge, meteorology, metguest, Metro Wifi (2 MACs), met-wlan999, Miller Street Brewery Mobile 4G, Millhood, mka-27784, MOBILE, mojito, monstrouswifi, Mort, MOTOROLA-E5BE7, Movistar-Vex, Mozilla Guest, MPLUX AirPort, MRC-Guest, MTH Functions (6 MACs), museumcg, museumpublic, NDABBAYE, NetComm Wireless, NETGEAR (2 MACs), NETGEAR2, Nexus, no-one here but us chickens, Norah Han...s iPhone, Novotel-Canberra, NPS Wireless, ntegrity.com.au, Ogilvy_Melbourne, OgilvyWiFi, OptimusPrime, Optus E583C f0b5, OPTUS_B1, OPTUSA82B5A1, OptusCD3_365c80, OPTUSV6FF126, OPTUSV8D64B0, Other... (2 MACs), PalaceMeetingRooms, Panasonic Display1, pandy, password: ken sent me, Patient, Pegasus, pgh-wireless, Pluto, Porto, Porty Extreme, pp, PP-AP, Pretty Fly For A Wifi, Pretty Fly for a WiFi..., Prometheus-2-4, public, Qantas Free WiFi, Qantas-Lounge (2 MACs), QANTASWebConnect, RAMMMOODIEWLAN, RCSWIFI_1, redlea (2 MACs), Residence du Rougier 1, rhapsody (2 MACs), Ricky...s iPhone 5, RMIT, Robot, roomlinx, ROSENEATH_WIFI, rtw, Scarlett Extreme, Sceptre, ScottiePippen, Seaport Wireless, SFR_E8C8, Shanghai_Wireless, Sherwood Forest, SH-Wireless, SJS, sky-free-e872b5, SKYMESH, Skynet Global Defence Network, Skynet mobile defence unit, Skynet Mobile Unit, SOH_Guest, SpeedTouch913EE2, Squareweave - We build web apps, squiz.net, State Library of Victoria, StormsEnd, studiocea, Subaru_Customer_Lounge, Super_Dragon, SuperDragon, T1 Free wifi by SYD, t1fg, TASSWEB Wireless, Telecom wireless hotspot, TelerikAPAC, TEWM_0A7E0B, The Lounge Sydney, The Office of Marketing, THE PARLOR (2 MACs), thebrook, theinterweb, TheOffice, thisismyhouse, ThousandPoundBend, tobyandloz, Tomizone @ Movenpick, Tony le Pony, trust me, TULIP (4 MACs), Tygwyn1, UConnect, ULTIMATE-4F77, ULTIMATE-Rhapsody, UniWireless, vanessa's Network, Ventura_Free_WiFi, Verizon MIFI4510L 2412 Secure, vermeulen, Victoria Hotel, VirusProwler, W3710, WANADOO-6058, Wards, Wayport_Access, wdc-a, wdc-b (2 MACs), weatherzone, webteam (2 MACs), webteam2, WIFI@CintaAyu, WIFI@CintaTerrace, wilnet, winboard, wireless, Wireless@SG (3 MACs), wireless01 (2 MACs), WLANadmin, wlan-ap (2 MACs), WME, WME iinet, WME Wireless, www.koodoz.com.au, Xperia S_284e, YBF-b, Young Henrys, Zentrum_Der_Macht, ZyXEL
Tricks are one thing, but it can also act is a normal Wi-Fi access point which people connect to of their own free volition; see an SSID called “Free wifi” – sounds good, let’s go! Once you’re connected, you’re in a whole world of trouble, at least you are if you visit any websites that don’t implement sufficient transport layer protection. And that’s the real story here – unprotected Wi-Fi traffic.
What you saw in the screens above is the work of dnsspoof which in simple terms, was able to intercept the request for stackoverflow.com and rather than routing it to their server, routed it to the web server running in the Pineapple instead. The screens above were served from the Pineapple in response to the Stack Overflow request and in fact configured this way it will respond with that same page regardless of the site being requested, so long as it’s an HTTP request and not an HTTPS one.
What this demonstrates is that the Pineapple controls the traffic – anything sent over HTTP can be manipulated with clever software, including where requests are routed to. Now let’s imagine that there is no DNS spoofing and the Pineapple simply passes requests through to a network bridge and out over an internet connection. It might look like this:
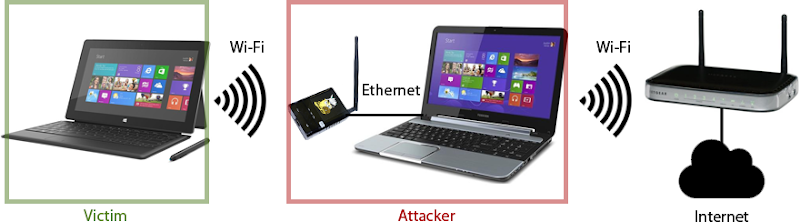
What this means is that the Pineapple and the attacker’s PC it’s connected to now control the unencrypted traffic. Anything sent over that connection – including Stack Overflow’s cookies – may be intercepted by the attacker. As you’ll see in the demo while I’m on stage, that is a very serious security risk.
What’s the risk?
I mean it’s just some cookies, why should you care? Let’s go back to the basics for a moment which means understanding what SSL is about and it boils down to three things:
- Assurance of identity – only the legitimate owner of the site should be able to serve up a certificate for it
- Integrity – the content moving backwards and forwards over the connection can’t be manipulated
- Confidentiality – the content also can’t be eavesdropped on
It’s that last point that most people associate with SSL and they expect passwords and banking info to be kept from prying eyes. But there’s other info that needs to be protected as well and it’s not as immediately obvious. Should the demo gods be kind to me, the audience will see one simple request to a Stack Overflow API appear on the attacker’s PC. It’s a request to the up-vote service and along with the request is the authentication cookie used to identify the user. Because it’s sent over an unencrypted connection it can be intercepted and once it’s intercepted then the session can be hijacked. The attacker will simply recreate the cookie in his browser (that’ll be me) and badaboom – they’re logged on as the victim!
One thing I do want to point out is that the guys at Stack Overflow understand this intimately. As I’ve written before, these are without doubt some of the smartest developers on the planet and they’ve made a conscious decision about the risk versus benefit of SSL. They know exactly what they’re doing. In fact Nick Craver wrote a very good blog post just last week on the road to SSL where he outlines the sort of challenges they need to overcome in order to secure the transport layer. As you can read in this question, clearly there is an intention to make Stack Overflow SSL only so that’s a very positive move in the right direction security wise.
Get Pineapple Surprise! on GitHub
I want to make the implementation of this freely available to the community in part so that others can take it and adapt it (contributions are welcome!) and in part so that it’s clear that despite the obvious opportunity to do evil, it’s not doing anything nasty. You can find it on GitHub here: https://github.com/troyhunt/PineappleSurprise
Told you it was rudimentary! The index page merely replaces the default one on the device that did nothing other than a client-side redirect by meta tag to redirect.php. Replacing the existing index page keeps the URL clean – whatever resource is requested is served over that URL.
There’s some logging that happens right up front in the file but it is very, very consciously only grabbing info that would be logged by a webserver anyway: time stamp, requested address, HTTP accept headers (to identify whether it’s an API call or a browser call), the IP address of the device (helps for looking at associated requests and the user agent (should give you an idea of the client being used).
What’s not logged is far more important and that’s cookies. They’re reflected back to the screen as you can see above, but they are absolutely, positively not logged anywhere and for those that did (do?) come along to my talk, the reason will be crystal clear.
tl;dr
Secure your web services! Anything you don’t want an attacker observing or manipulating needs to be sent over HTTPS and that includes auth cookies. Oh – and turn off your Wi-Fi in public!
Is This The Worst Craigslist Job Posting Ever?
A painful lesson in the art of copy/paste “Emoticons. Format.”

Sotheby's Inc. is looking for an administrative assistant. And judging by this unbelievable Craigslist post, it would seem they could really use one.
The post starts off normal enough — a concise and standard description of the administrative assistant role — but quickly veers off the rails as the post's author appears to accidentally include a rambling IM transcript that chronicles the poster's epic struggles with a simple copy/paste.
It's unclear if the post is real or simply a well executed fake — certainly the author's struggles with a standard "Ctrl-C, Ctrl-V" copy/paste are hard to comprehend, to say the least.
If it's real, it's perfect. If it's fake, it's still a pretty excellent script.
Here is the full text of the post below. Warning: it's pretty brutal.
Sotheby's Inc. requires a Skilled and dedicated Administrative Assistant, Office Executive and Receptionist for its New York office. Applicant would be coordinating, planning and supporting daily operational and administrative functions. Scheduling meetings, coordinating travel and managing all essentials tasks. We require someone who is highly focused and able to identify goals and priorities and resolve issues in initial stages. Highly skilled in greeting guests with a positive attitude and helping them with their needs. Should be proficient in Microsoft Office. Position opens to students. Send in your updated resume.Mr Debras. Delman (Apr 29 2:02 PM): Copy and paste the job description above in the space provided for it
Mrs. Debra Delman (Apr 29 2:02 PM): Did you get that?mejia.saima (Apr 29 2:03 PM): okay I will do it now
Mrs. Debra Delman (Apr 29 2:02 PM): Copy and paste the job description above in the space provided for it
Mrs. Debra Delman (Apr 29 2:02 PM): Did you get that?mejia.saima (Apr 29 2:03 PM): okay I will do it now
Mrs. Debra Delman (Apr 29 2:04 PM): Compensation: $15-$20/Hr + Attractive Wages
mejia.saima (Apr 29 2:07 PM): I am trying to copy and paste the informationMrs. Debra Delman (Apr 29 2:09 PM): Okay
Mrs. Debra Delman (Apr 29 2:09 PM): Let me know when you are done with thatmejia.saima (Apr 29 2:10 PM): I'm having problems copying and pasting the info. I try to highlighted adn then go to edit and click copy. can you help me please?
Mrs. Debra Delman (Apr 29 2:02 PM): Sotheby's Inc. requires a Skilled and dedicated Administrative Assistant, Office Executive and Receptionist for its New York office. Applicant would be coordinating, planning and supporting daily operational and administrative functions. Scheduling meetings, coordinating travel and managing all essentials tasks. We require someone who is highly focused and able to identify goals and priorities and resolve issues in initial stages. Highly skilled in greeting guests with a positive attitude and helping them with their needs. Should be proficient in Microsoft Office. Position opens to students. Send in your updated resume.
Mrs. Debra Delman (Apr 29 2:02 PM): Copy and paste the job description above in the space provided for it
Mrs. Debra Delman (Apr 29 2:02 PM): Did you get that?mejia.saima (Apr 29 2:03 PM): okay I will do it now
Mrs. Debra Delman (Apr 29 2:04 PM): Compensation: $15-$20/Hr + Attractive Wages
mejia.saima (Apr 29 2:07 PM): I am trying to copy and paste the informationMrs. Debra Delman (Apr 29 2:09 PM): Okay
Mrs. Debra Delman (Apr 29 2:09 PM): Let me know when you are done with thatmejia.saima (Apr 29 2:10 PM): I'm having problems copying and pasting the info. I try to highlighted adn then go to edit and click copy. can you help me please?
Mrs. Debra Delman (Apr 29 2:11 PM): Just click and drag the content I sent to you from our conversation menu and as soon as the job description i sent to you has been highlighted press "control + c" or right click and click on copy
Mrs. Debra Delman (Apr 29 2:12 PM): Hope am clear?mejia.saima (Apr 29 2:12 PM): is there an easier way to do it
Mrs. Debra Delman (Apr 29 2:13 PM): Am afraid there isnt. Unless you have to type it out
Mrs. Debra Delman (Apr 29 2:02 PM): Sotheby's Inc. requires a Skilled and dedicated Administrative Assistant, Office Executive and Receptionist for its New York office. Applicant would be coordinating, planning and supporting daily operational and administrative functions. Scheduling meetings, coordinating travel and managing all essentials tasks. We require someone who is highly focused and able to identify goals and priorities and resolve issues in initial stages. Highly skilled in greeting guests with a positive attitude and helping them with their needs. Should be proficient in Microsoft Office. Position opens to students. Send in your updated resume.
Mrs. Debra Delman (Apr 29 2:02 PM): Copy and paste the job description above in the space provided for it
Mrs. Debra Delman (Apr 29 2:02 PM): Did you get that?
mejia.saima (Apr 29 2:03 PM): okay I will do it now
Mrs. Debra Delman (Apr 29 2:04 PM): Compensation: $15-$20/Hr + Attractive Wagesmejia.saima (Apr 29 2:07 PM): I am trying to copy and paste the information
Mrs. Debra Delman (Apr 29 2:09 PM): Okay
Mrs. Debra Delman (Apr 29 2:09 PM): Let me know when you are done with thatmejia.saima (Apr 29 2:10 PM): I'm having problems copying and pasting the info. I try to highlighted adn then go to edit and click copy. can you help me please?
Mrs. Debra Delman (Apr 29 2:11 PM): Just click and drag the content I sent to you from our conversation menu and as soon as the job description i sent to you has been highlighted press "control + c" or right click and click on copy
Mrs. Debra Delman (Apr 29 2:12 PM): Hope am clear?
mejia.saima (Apr 29 2:12 PM): is there an easier way to do itMrs. Debra Delman (Apr 29 2:13 PM): Am afraid there isnt. Unless you have to type it out
Sotheby's Inc. required a skilled and dedicated administrative assistant, office executive and receptionist for its New York office. Applicant would be coordinating, planning and supporting daily operational and administrative functions. Scheduling meetings, coordinating travel and managing all essentials tasks. We require someone who is highly focused and able to indentify goals and priorities and resolve issues in initial stages. Highly skilled in greeting guests with a positive attitude and help them with their needs. Should be proficient in Microsoft office. Position open to students. Send in your resume.
Emoticons
Format
Emoticons
FormatEmoticons
FormatEmoticons
Format
Oh my.
h/t (@maggieserota)
Mind-Bending Recursive Illusion Created Using Printed Photographs
Whoa. If you enjoy watching mind-bending concepts that confuse you and make your brain hurt, check out this experimental short by Willie Witte, titled “Screengrab.”
Nothing in the video is computer generated trickery: it simply uses clever camera tricks and a whole lotta printed photographs to create the seamless transitions. “All the trickery took place literally in front of the camera,” Witte says. See if you can understand what’s going on through the entire 1 minute and 30 seconds.![]()
The whole thing is an “experiment in transitions,” Witte says in the video’s description. You can try to recreate the effect yourself by printing out high-resolution screengrabs at the end of each segment and using those photo as the transition into the next clip.
BOOOOOOOM writes that Witte is a documentary filmmaker who’s currently working on a series of PBS. In his free time, Witte turns to experimental personal projects that deal with analog visual techniques. This short film was created during one of his evening brainstorming sessions.
(via Boing Boing)
P.S. In case you’re wondering, the background music is by artist Kevin McAlpine.
90-Year-Old Woman Does a Double Backflip
'The Matrix' Retold by Mom
Joe Nicolosi watched The Matrix with his 65-year-old mother, had her explain the plot and then animated the results.
[pixelspersecond]
Your Mac, iPhone or iPad may have left the Apple store with a serious security risk
Just over a year ago to the day, my wife and I walked into the Apple store in Sydney’s CBD and bought her a shiny new MacBook Air. Macs weren’t familiar territory for us so we happily accepted the offer for a staff member to walk us through some of the nuts and bolts of OSX. That was a handy little starter and we left the store none the wiser that the machine now had a serious security risk that wouldn’t become apparent for another year.
A couple of weeks ago I wrote about my new favourite device, the Wi-Fi Pineapple. Despite its friendly tropical name, the Pineapple is a piece of cigarette-pack-sized professional security equipment I picked up online for $100 to help me demonstrate secure coding practices. Specifically, it’s helping me educate web developers about the risk of not using encryption between browsers and the websites they’re communicating with, something that needs to be built into the design of the site itself.
Among various party tricks packed into this little piece of equipment is a feature called “Karma” and it works like this: When you connect a device to a wireless network – let’s imagine the network is named “WILSON” for the purposes of demonstration – the device then continues to look for that network for perpetuity. What that means is that the device (laptop, smart phone, tablet, etc.) is running around shouting “WILSON, WILSON, where are you WILSON?” What Karma says when it hears this is “I’m Wilson, let’s get connected” and if WILSON wasn’t originally secured with a wireless password, the device connects to the Pineapple automatically. It now looks just like a normal wireless connection and it has been made without any action whatsoever on the user’s behalf.
You didn’t know this could happen? It’s written right there on the wireless network screen of every iOS device, albeit without explaining that “Known” means nothing more than an access point claiming to be exactly what the device has just publicly broadcast it’s looking for:
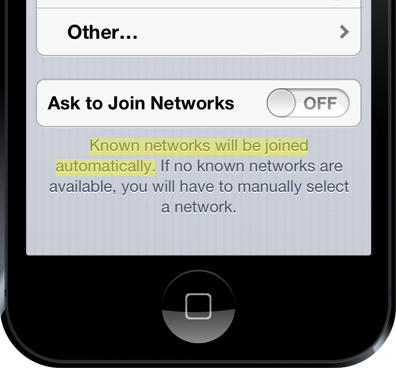
So what’s the risk of a device connecting to the Pineapple (or any similar equipment – it’s not the only one) without knowing it? It means that every single byte of data that passes through that connection and is not encrypted can be read or changed by an attacker. Passwords, personal information, photos, videos and anything else not properly protected by the website can be intercepted. Links to secure login pages, documents, emails and even banking websites can be manipulated when that protection doesn’t exist.
What’s now evident is that a large number of devices are leaving Apple stores after having been connected to an insecure network leaving them at risk for years to come. Let me explain.
The “Apple Demo” conundrum
When I wrote the blog post I mentioned above I commented that whilst testing the Pineapple I noticed some unexpected traffic flowing through it, traffic that looked like this:
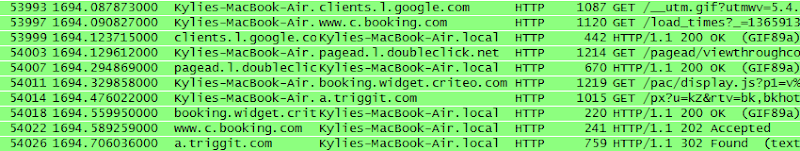
This is my wife’s MacBook Air and I was able to intercept her internet traffic simply because she had wandered into range. This struck me as odd at the time because she had already been connected to our (secure) home wireless that also had a much stronger signal than the Pineapple’s. Sure enough though, she was now connected to the Pineapple’s rogue access point under the name “Apple Demo”:

I made a note of this in the post then moved on.
Then this weekend just gone I was at a Microsoft event in a small room with dozens of fellow techie people, all with their laptops out for hours on end. Some of them were Macs. In amongst participating in the activities of the day, I was also preparing for a conference talk I’m doing down in Melbourne later this week which will involve using the Pineapple to demonstrate the risk of websites that don’t implement sufficient security measures. Without giving away the details of a yet-to-occur event, I had configured the device to simply see if anything would connect to it – and it did. Here’s what happened:
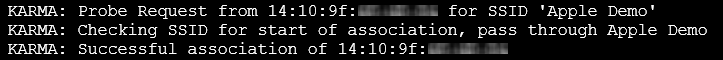
This is a “Probe Request” from a Wi-Fi device which as I explained earlier, is essentially the device calling out “WILSON” except that in this case, it’s calling out “Apple Demo”. The Pineapple then responds with “I’m Apple Demo” and a successful association is made. Had the Pineapple been connected to the internet, all the unencrypted communication between the device and any websites it visited or services any apps connected to could have been logged or manipulated.
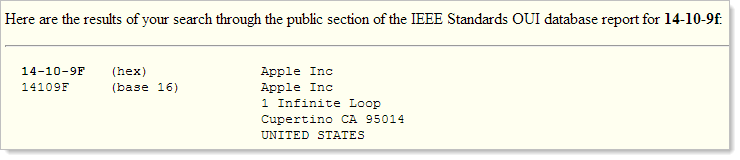
In the image above, the first and last lines contain the partially blurred MAC address – the uniquely identifying fingerprint that all network devices have – of the device that connected. The first three sets of two digits are the organisationally unique identifier which tells us who manufactured the device. You can check it up online and you’ll get a result that’s not too surprising:
In the very small amount of testing I’d done with the Pineapple, this was the second Mac that had connected to the same insecure network it had previously been associated to. This was more than just coincidence and far too prevalent for such a small sample size. It was time a visit to the Apple store.
The Sydney Apple store
As is usually the case with Apple, the Sydney store is an impressive piece of architecture with an amazing glass facade:

I’d made an appointment with a Genius to take a look at my iPad and had a bit of time to kill first so thought I’d take a look at what all the display models were connecting to. First up was an iPad mini:
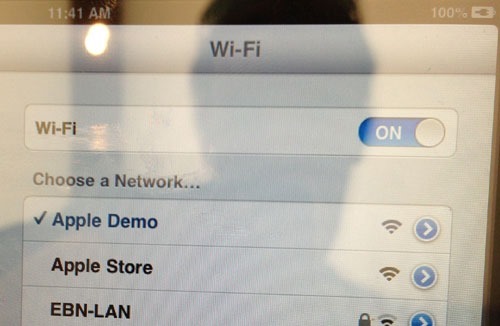
And then a MacBook Pro:
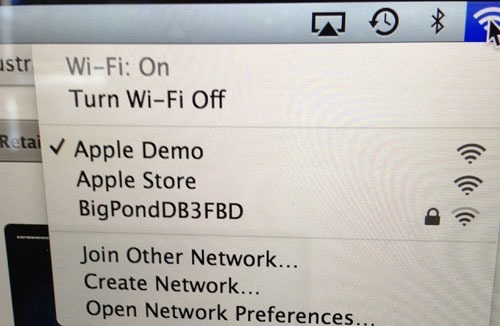
Although not surprising, it’s reasonable validation of the assumption regarding the origin of the other “Apple Demo” machines I’d been seeing. Of course the main thing is that the network is still insecure – there’s no padlock icon hence no Wi-Fi authentication is required. Now none of that matters in this case anyway – you’re not exactly about to do anything of a nature where you’d want to protect your data using floor stock.
I go upstairs for my appointment with the Genius and explain two issues I’m genuinely having with the iPad that irk me. Both issues will require internet to demonstrate. The Genius – let’s call him “John” – is exceptionally helpful and he promptly directs me over to the Wi-Fi settings on the iPad and has me select this:
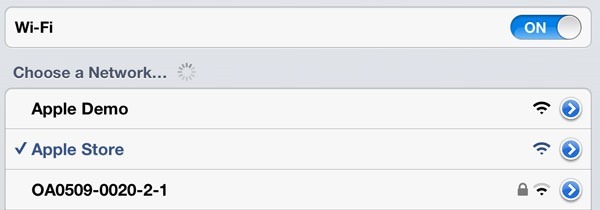
It’s “Apple Store” rather than “Apple Demo” but the risk is identical – there’s no wireless password and the device will now happily remember this name and attempt to reconnect to it at any time. We finish our session and I leave the store.
I come home, turn on the Pineapple and immediately see this:

My once-secure iPad has now become vulnerable. As soon as I walked out of the store the device started looking to reconnect to anything that would acknowledge it. Consider the consequences of this: as soon as someone walks out of the Apple store after receiving support it’s highly likely that an attacker can begin immediately monitoring their internet traffic. It’s that easy.
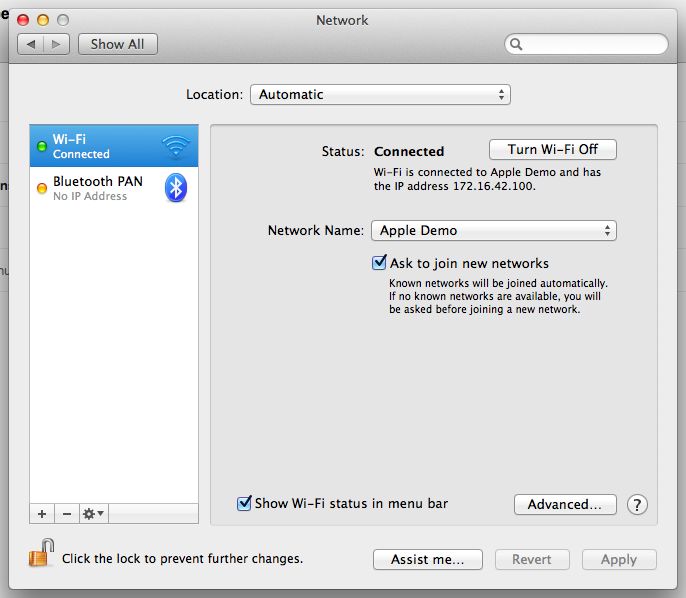
What can you do if you own a Mac?
When I looked at the network properties of my wife’s Mac, obviously there was a stored connection to Apple Demo:
What really made the risk hit home though was when I looked at the “Advanced…” settings of the network:
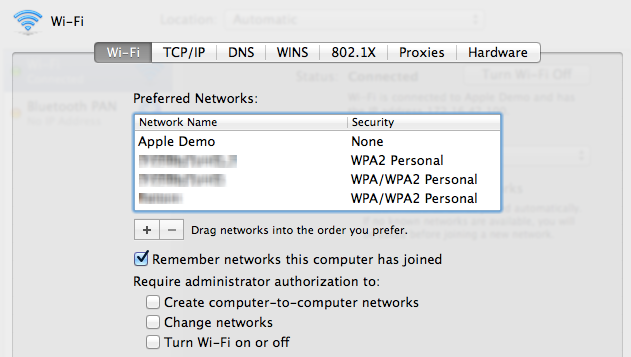
The Apple Demo network is the first on the list and will take priority over all networks that came after it. My wife’s machine first connected to Apple’s network then we came straight home and set it up on our own. Even now, one year later, the machine is still prioritising the first network it connected to and dropping off the newer one. This meant that the Pineapple was able to hijack the connection even when the machine already had a perfectly legitimate association to a wireless access point.
The solution is simply to delete any networks where the Security is “None”. That’s easy on the Mac, not so much on iOS.
What can you do if you own an iOS device?
It’s a little trickier in iOS as there’s no way of viewing the networks the device has previously connected to and consequently no way of removing the insecure ones. In fact the only way you can forget an individual network and not automatically reconnect to it is by selecting it when the network is in range:
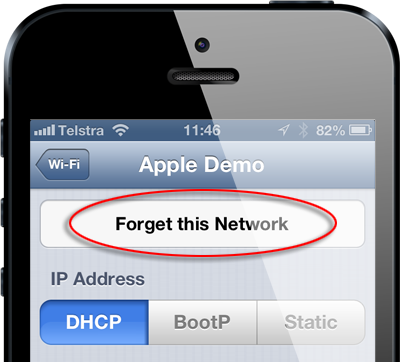
This isn't going to do most people much good as they’re not exactly going to travel back to the store just to have their device forget the network. If you think it might have gone through the demo or support process in store or for that matter connected to any unprotected wireless network you’ll need to erase all your trusted ones and start from scratch.
Jump over to “Settings” –> “General” –> “Reset” and then “Reset Network Settings”:

It’s going to make it unpleasant if you regularly connect to secure networks you now need to go and retrieve passwords for again, but it will ensure your iOS device hasn’t left Apple with a serious security risk.
Can’t this happen after connecting to any insecure wireless network?
It sure can. If you go down to McDonalds and jump on their free Wi-Fi and it doesn’t require a password, you’ve got exactly the same problem. The difference, of course, is that McDonalds makes fast food whilst Apple makes devices with networking capabilities. McDonalds (and similar) need to lift their game and secure their network (and of course deal with the usability issues that creates) but to some degree they can be forgiven for the oversight.
When you buy a brand new phone or tablet or laptop you expect to walk out of the store with a secure piece of equipment, certainly one that would take some amount of effort to exploit. That’s not what’s happening after Apple connects it in-store and that’s the real story – it’s insecure by default and vulnerable to a simple attack from day one.
This may well be the case with other stores as well. I don’t know how Microsoft or Samsung or other retail outlets selling similar devices and offering a similar setup service handle wireless connections, but clearly if they’re not using a protected network then they’re leaving consumers with exactly the same risks.
Keeping customers safe is as easy as pie
Paradoxically, there’s a little meat pie shop just around the corner from Apple’s gleaming architectural masterpiece. The pie shop is nothing more than a hole in the wall with a counter one staff member can barely fit behind. Somehow they still manage to offer free Wi-Fi and use an ingenious means of properly securing it for their customers. It works like this:

That’s all it takes – kindly provide customers with a Wi-Fi password when they ask and this entire problem just disappears. Good work by the pie shop!
For the more technically minded
For those who want some more detail, here are a few key points:
Traffic sent via HTTPS can’t be intercepted and either read or manipulated by a man in the middle, at least not without resorting to attacks against the protocol such as BEAST. Apps that make calls to APIs over SSL and validate the certificate are in good shape as are browsing sessions which occur entirely over HTTPS.
Browsing sessions that begin over HTTP are not safe even if they redirect to HTTPS, for example if you simply type americanexpress.com into the address bar and the browser defaults to an unencrypted scheme (read about sslstrip if you want to know more). Webpages which load login forms over HTTP or embed them in an iframe within an HTTP page (even if the login page is HTTPS) are also at risk as the original HTTP request can be manipulated to load any other content an attacker desires (such as a rogue login page). Authentication cookies not flagged as “secure” and sent over an unencrypted network also pose a serious risk.
The Pineapple can detect probe requests for WPA protected networks but devices looking for them won’t automatically or even manually make the association if you try it that way. You’ll see the names of secure networks listed in the device’s Wi-Fi settings but that’s it – the initial authentication handshake won’t occur and the device won’t connect.
In this case, Wi-Fi security isn’t about protecting the network from unauthorised access nor is it about protecting any given client’s data from monitoring by other clients. This is entirely about not leaving the device in an insecure state long after the association with the network in question has ended.
Summary
What all this means is simply this: if Apple helped you set your device up or provided you with support in the store it’s now exceptionally easy for an attacker to monitor and manipulate the majority of internet traffic that passes through it. So long as an attacker can get in range of the wireless (and I’ve already done it accidentally and with good intent on multiple occasions), they own your device.
Obviously this was all tested on devices that had been through the Sydney store (this was the most likely source of the one I observed at the conference on the weekend). I don’t know how other Apple stores in other locations handle the situation described above, but given the carbon copy design, staff and experience in stores across the globe, I’d be surprised if the practice differed.
I’m still a happy iPhone and iPad user. My wife is a happy Mac user. There is nothing about the products per se that is insecure with regards to the information above, it’s simply an in-store process which leaves them vulnerable. It’s also easily rectified by simply putting a password on their wireless – any password and the devices won’t be fooled into connecting to rogue access points in the future. I know that doesn’t make for as slick an experience as it currently is for customers, but it’s the only way to solve the issue short of the staff manually removing the connection again at the end of the session. Unfortunately, all this is also only any good for new devices and I’ll wager that as of right now there are thousands of devices in Australia alone that have been left vulnerable.
Disclosure
Yesterday I contacted Apple and shared the risk regarding their in-store practices:
Recently I've learnt that customers are receiving support for their Apple products in store with the help of Geniuses who connect their devices to unprotected wireless networks, from my experience named either "Apple Demo" or "Apple Store" (certainly this is the case in the George St store in Sydney). The association to a network with no security then leaves the devices vulnerable to inadvertently connecting to rogue access points which respond to probe requests the devices send out specifically looking for the presence of an insecure network it has once known.
In short, when a device leaves an Apple store after having been connected to an insecure network it is now at risk of an attacker hijacking internet traffic. This is a trivial process and easily exploited by those with malicious intent. I've observed this first hand with my wife's MacBook Air and my own iPad as well as observing other Apple devices exhibiting the same behaviour.
Your review and comments would be most appreciated.
I’ll update the post with any responses.
Are Google Hangouts The Perfect Office Environment?
This is the perfect office environment:
Source: sfgirlbybay.com via Assaf on Pinterest
But since we can't have that one, let's try to approximate.
Working from home can be awesome. It's certainly not for everyone. Lots of people need that shared office environment to be productive. Some actually prefer to work in an open-space.
You know, one of these:
 |
| your typical open space |
Those that prefer to work in an open space can stop reading now.
We, reasonable people, we appreciate what a quiet, private work environment means. When you have your own office, with a door and all, you can actually concentrate. You're less easily distracted, and less stressed. You can have a conversation with a colleague without breaking everybody else's concentration. And yea, you can also give your brain the occasional rest by checking up on Facebook for a few minutes, or playing a couple of Angry Birds levels.
Yes, games at work - big whoop. As long as you're not overdoing it, they can actually increase your productivity.
"Okay, we get it", you say, "what does this have to do with Google Hangouts?"
In the perfect programmer office:
 |
| Who touched the thermostat?! |
- You are by yourself. Just you. When you have two programmers sharing a room, at least one of them will have a seasonal allergy at any point in time, and will be blowing his nose every five minutes.
- People can see when you're in, and can knock on your door if they need to pop in and ask a question. But you also have a do not disturb sign for those hours that you're really in the zone.
- Your team members are nearby, so you can ask them a quick question if you need to.
- You got your fancy Aeron chair, your private AC thermostat, and an en-suite bathroom that nobody else uses.
Everybody joins the hangout each morning, and stays on for the duration of the work day but with their microphone muted. This is crucial. Without it you're just listening to other people's typing noises and we're back to the horribleness that is an open space environment. When you want to say something, un-mute your mic and everybody else hears you.
Tweak #3
Need to blow your nose for a second and don't want it broadcast around the globe? Turn off the camera for a moment. Same if you want to take a short break. Others will still be able to speak up and ask whether you're really there if they have something urgent to discuss.
It's really as close as you can get to that ideal working environment. No real office environment is this flexible. It's like your teammates having adjacent offices with sound-proof glass walls that turn one-way opaque at the press of a button. You can see everyone, or hide them. You can be seen, and you can have your privacy. You can play music and not have to wear headphones for 9 hours. You don't even have to get up to walk over to your colleague's office when you need to talk.
And Google Hangout has all kinds of other cool features. Being free is one of them. Another one is being able to share a screen and collaborate on documents and chat. I guess other video conferencing solutions have similar features, but not many of them are as well made and still free.
Pro tip: if you can dedicate some old laptop just for hangouts, then do. It can sit beside your main screen and you can easily mute the whole thing with one click, turn it away if you want to... very flexible. It feels more like you're sitting alongside a coworker than actually video conferencing. Give it a shot.
The Downsides
 Hangouts aren't perfect. They have a few quirks and missing features, but maybe Google will read this and fix them. Somebody please +1 this.
Hangouts aren't perfect. They have a few quirks and missing features, but maybe Google will read this and fix them. Somebody please +1 this.No PTT - Push To Talk. You know, like a Walkie-Talkie. Muting and un-muting can get tedious. Occasionally someone will forget to mute his mic and has to be asked to. Occasionally you'll forget you're muted and find yourself talking to the air for a few seconds. It's not a huge deal, but it would be great to have.
Google Hangouts time out after a while. I guess they weren't really designed to be used for hours and hours. After an hour or so a popup asks you whether you're really still hanging out or not, and if you don't answer it it'll close the hangout. Annoying.
Setting up and shutting down the hangout is cumbersome. It's just too many clicks. You can't "save" a hangout and get back to it with one click. You have to invite people manually each time. What Google Hangout really needs is the concept of rooms, like chat systems have. Rooms could have well known links so anybody can join them without being invited. You could also be in more than one room, talking to a different group of people each time. You could have one-on-one rooms. Hangouts should copy IRC. IRC is awesome.
In Summary
If you're a distributed team, staying in touch can be challenging. Chat isn't enough. Calling people up on Skype isn't quite it, either. You can have a lot of the good things a real office environment gives you, without many of the annoyances. That's how we work at Gigantt, which, by the way, is perfect for distributed teams that collaborate on the same projects.
Hey, what do you know, I managed to plug our product in our blog...
 |
| HubSpot, give me my marketing grade points now please! |
Gigantt is Not Psychic
When tasks are left without estimates, Gigantt tries to nudge you to properly estimate them by showing a little icon beside them (and beside each task that contains them):
Until today, tasks left without estimates were treated by Gigantt's scheduler as one hour long. One hour seemed like roughly the most common task size, so that's what we went with.
Starting today, you can control the default estimate yourself by going to Options -> This Plan and changing the setting:
Also starting today, all new plans will have a one-minute default estimate. Your existing plans will still have the one-hour default, unless you change it yourself.
Why did we change the default estimate to be one-minute?
Well, we noticed a lot of users wanted to be able to plan ahead very quickly, and only give estimates to their tasks when they're done. The freedom to use Gigantt this way is important, because if you're brainstorming and furiously writing down task after task, we don't want to slow you down by demanding that you stop and estimate each task that you create. The problem with the previous default of one hour was that if you quickly created, say, 20 tasks without estimates, you basically added a 20-hour delay into your plan. This can be very disruptive, especially when you have lots of people collaborating on the same plan. One guy adds a bunch of tasks and suddenly the entire plan is delayed unintentionally.
With the 1-minute default, you can do more than just separate planning from estimating. You can also use Gigantt to manage check-lists. When you create a check-list of tiny one-minute tasks, then you're hardly affecting the overall schedule.
We hope this change won't be disruptive to our existing users. If you would like to give us feedback, please visit our feedback site and let us know what you think.
Above all, remember to estimate those tasks. Gigantt isn't psychic, yet. You need to tell it how long tasks are going to take. It takes just a few seconds to do so, and in return you get fully automatic scheduling and resource leveling. That's a good deal.
Time-Lapse Documents a Backyard Tree Growing Up Over Five Years
Want to see a tree grow up before your very eyes? Sonoma County, California resident YouTube user Lapeere created this neat video that squeezes five years in the life of his backyard tree into a one-minute-long time-lapse video.
Lapeere took about one photograph a week over the course of the five years. To keep the framing the same through the shots, he pressed his 3.3-megapixel Olympus 3030 point-and-shoot in a specific spot on his air conditioner, between a screw and an edge of the AC unit. This allowed the shots to be from an identical viewpoint throughout the whole video.
![]()
The main dog in the photographs was named Sara. She unfortunately died in 2012, a few years after this video was released in 2009. “She new when it was time to take my pictures and always ran outside to pose. I’m glad I kept her in the pictures and didn’t shoo her away,” Lapeere says.
Lapeere also says that the video documents not just the life of that tree in his yard, but his personal life as well:
I do not consider myself an arborist as much as I consider myself a historian. I try to capture the steady flow of events that effected my life. When my in-laws lived in the house pictured, they had a passion for the yard. In later pictures after my divorce, not in the video, the yard doesn’t look so good. The tree still grows, but so does the grass.
This video captures the struggle my in-laws had keeping the lawn healthy when we had a dog that loved to lay in the same place all the time.
Here’s a second time-lapse video Lapeere created, showing a different view of his backyard over six years.
Lapeere has been faithfully snapping these time-lapse photos for over a decade now, and says he has gone through three digital cameras in the process. Now that’s dedication.
Hard yakka: Why Atlassian’s founders are the pride of Australia’s startup world

A few years ago, Mike Cannon-Brookes was invited to speak to a student entrepreneurial society at a Sydney university. The co-founder of Atlassian, one of Australia’s most successful software companies, showed up to the venue in cut-off jeans and a T-shirt. One of the workers who was setting up the venue mistook him for IT support. When Cannon-Brookes walked in the room, the worker asked the scruffy entrepreneur if he could get the projector, which was acting up, to work. Not one to disappoint, Cannon-Brookes said “Sure,” and fixed it.
It would be difficult to more perfectly encapsulate the disposition of the self-made Aussie Entrepreneur. Atlassian’s other co-founder, Scott Farquhar, tells similar stories of new employees bumping into the founders and not knowing who they were.
“How long have you been here?” one asked Farquhar on his first day at the company.
“Oh, about 11 years,” the surreptitious boss replied.
“And what do you do?”
“Well, I’m kind of in management.”
In the US, there’s a lot of talk about Zuckerberg’s hoodie and founders who work from laptops at the same desks as the rest of their teams. But Cannon-Brookes and Farquhar (pictured above left and right respectively), who are both 33, take tech-casual to another level. When I visit their offices, housed in a converted Victorian-era bank building in downtown Sydney, we chat over beers raided from a fridge in a community space on the sixth floor. Farquhar, who used to sport a mohawk and a goatee, is wearing jeans and sneakers with a long-sleeve T-shirt, while Cannon-Brookes rocks a fisherman’s sweater, a tatty baseball cap emblazoned with the Atlassian logo, shoulder-length hair, and an unkempt beard that wraps around his neck like moss on the trunk of a tree.
These guys are the heroes of Australia’s nascent startup ecosystem. Atlassian has not only been hailed as perhaps the country’s coolest company, but it is a name routinely invoked as a role model by anyone with a stake in Aussie startups. In 2011, it recorded a $100 million year of revenue without a single salesperson. When Sarah Lacy wrote about the company last year, she noted that it had achieved 40 straight quarters of profitability and had a compound annual growth rate of 43 percent for the last five years. In 2010, Accel Partners sunk $60 million into the company, the largest enterprise deal the VC firm had ever done. [Disclosure: Accel Partners is an investor in PandoDaily.] It now has 400 staff in Sydney, and another 200 in San Francisco.
The founders in particular are held up as humble titans in Australia. Both are known for giving back generously to the startup community, and for investing in homegrown companies. Both are investors in the new Blackbird VC fund that was founded in part to address a lack of Series A funding options in the country, and both are involved with local accelerators and incubators. They have a shared fortune of $480 million, according to Australia’s BRW magazine. Incidentally, they each have one child and another on the way.
“They’re no bullshit,” says Ahmed Haider, the founder and CEO of Zookal, who also happens to be the guy who organized the event at which Cannon-Brookes was enlisted to fix the projector. Haider says that talk in particular helped convince him to drop out of university to pursue his entrepreneurial ambitions. “They’re two very real guys and they went out to make a dent in the universe.”
For Haider, the Atlassian founders showed what’s possible to achieve in Australia by following their dreams and sticking to their ideals. “I never heard anything like that before,” he says. “It was like, ‘Wow, it’s possible to do that and still make a living.” He doesn’t know any young entrepreneurs in Sydney who don’t look up to Farquhar and Cannon-Brookes.
Those comments were echoed by everyone I spoke to in Sydney’s startup ecosystem this week. When asked to name an Aussie success story, the word “Atlassian” was the first to come out of people’s mouths. One of the reasons they’re so proud of the company is that it proved it is possible to reach Silicon Valley scale and riches without having any of the benefits of actually being in Silicon Valley. By the time Accel invested, Atlassian already had close to 20,000 customers and many tens of millions of dollars in annual revenue.
When Farquhar and Cannon-Brookes started Atlassian straight out of university with a $10,000 credit card in 2002, they couldn’t rely on venture money to sustain the company. There were few local investors interested in the tech sector, and Australia wasn’t on the radar for Valley VCs. The word “startup,” in fact, wasn’t even part of the Australian business lexicon. Like most other Australian tech companies, Atlassian had to prove its worth by earning revenue from day one. It did that with the release of its issue-management software Jira. The next year, it launched content collaboration tool Confluence. The company was an early mover in the software-as-a-service sector, distributing its products solely through the Internet and relying on Google AdWords to get the word out. By 2004, it had 2,000 paying customers.
Another big part of why the Atlassian founder are so popular in their homeland, however, is they embody Australian ideals, including a delicate mix of straight talk, modesty, and the ballsiness to take on a global market. That much is reflected in the company’s values, which include the clarion calls “Open Company, No Bullshit,” and “Don’t Fuck the Customer.” Young entrepreneurs look at them and see themselves. Cannon-Brookes and Farquhar built the company on their terms without having to play by anyone else’s rules in a market that was stacked against them. Rather than scrape and bow at the foot of high-powered American investors, the VCs came to them. It’s not just a case of an underdog Aussie company taking on the world, it’s a case of the world coming to an Aussie company.
The next major step in that reverse-colonization process is likely to happen this year in the form of a much-anticipated IPO. Cannon-Brookes says the company will be cautious and patient in its approach to going public and that the event is not in the company’s “immediate plans.” One has to assume, however, that it will come sooner or later. It has been more than two years since that enormous round from Accel, and Cannon-Brookes concedes that there’s no point in “delaying it unnecessarily.”
However, he is also quick to downplay a potential IPO’s significance. “It’s not a victory line,” he says. “It’s a financing event.”
Spoken like a true Aussie.
Hamish McKenzie
 Hamish McKenzie is a Baltimore-based reporter for PandoDaily who covers media, politics, and international startups. His first name is pronounced "hey-mish" and you can follow him on Twitter.
Hamish McKenzie is a Baltimore-based reporter for PandoDaily who covers media, politics, and international startups. His first name is pronounced "hey-mish" and you can follow him on Twitter.
    
|
What Happens If You Text Your Parents Pretending To Be A Drug Dealer?
Nathan Fielder, star and creator of one of the funniest shows on television, Nathan for You , asked his Twitter followers to tweet their parents saying they had weed for sale. And the results are as good and painful as you'd imagine.
It all started with one tweet...

Via: @nathanfielder

Via: @levicarstensen

Via: @ronniemorganjr

Via: @TaylorrrDeee
Hacked AP Twitter Account Starts White House Attack Rumor; Markets Tank

That is a real tweet sent out by the real Associated Press account, but the AP didn't write it or send it. It seems the account was hacked by a group calling themselves the Syrian Electronic Army.
It took about 30 seconds for savvy Twitter users to figure out the hack, comparing style and syntax to normal AP tweets, but the markets had already reacted.
enlarge Credit: http://www.businessinsider.com/stocks-plunge-after-ap-tweet-2013-4
Credit: http://www.businessinsider.com/stocks-plunge-after-ap-tweet-2013-4
The AP says their accounts had been the targets of repeated phishing attempts over the past few days.
The false tweet said there had been two explosions at the White House and that President Barack Obama was injured. The attack on AP's Twitter account and the AP Mobile Twitter account was preceded by phishing attempts on AP's corporate network.
Market loss in that short 100-point dip was estimated to be $100 billion or so. They bounced right back as soon as the tweet was confirmed to be the result of a hack, but it certainly highlights how real time information flows can be used to game the markets. I'll be interested to discover whether anyone profited from that brief dip in stock values.
Bike headlight displays speed
My friend Matt Richardson made a system for his bike that projects a spotlight with data onto the street. It's currently set up to display speed, but it can also be used to project other kinds of information (like turn-by-turn directions). He's going to write about it for MAKE so you can build one, too.
The gel that stops bleeding instantly
This video is a bit gruesome, but it is demonstrating a remarkable substance that can stop bleeding almost instantaneously. Jack Millner of Humans Invent interviewed NYU student Joe Landolina, the creator of Veti-Gel.
"In all of our tests we found we were able to immediately stop bleeding,” says Landolina. “Your skin has this thing called the extracellular matrix,” he explains. “It’s kind of a mesh of molecules and sugars and protein that holds your cells in place.” Landolina synthesises his own extracellular matrix (ECM) using plant polymers, which can form a liquid when broken up into pieces. He says, “So it goes into the wound and the pieces of the synthetic ECM in the gel will recognise the pieces of the real ECM in the wound and they’ll link together. It will re-assemble into something that looks like, feels like and acts like skin."
The gel that stops bleeding instantly