 DC 2024 is being taken seriously. [ more › ]
DC 2024 is being taken seriously. [ more › ]Captain Easychord
Shared posts
Don't Blame Non-Voters for Not Voting
Fluxblog 2013 Survey Mix
This 10-disc, 184-song mix is a survey of some of the best and most notable music from 2013. For an even more broad overview of the year’s music across many genres, I encourage you to check out the many lists I made in collaboration with Aylin Zafar, Caitlin White, Maria Sherman, Alex Naidus, and several other writers over at BuzzFeed.
DOWNLOAD DISC 1
Ariana Grande “Honeymoon Avenue” / Miley Cyrus “We Can’t Stop” / Haim “The Wire” / Kanye West “Bound 2″ / Vampire Weekend “Don’t Lie” / King Krule “Neptune Estate” / Neko Case “Night Still Comes” / Sky Ferreira “I Blame Myself” / Laura Mvula “Make Me Lovely” / Beyoncé “Flawless” / Saint Pepsi “Better” / Disclosure featuring Ed Macfarlane “Defeated No More” / Maria Magdalena “CVMC (Cada Vez Mas Cerca)” / Phoenix “S.O.S. In Bel Air” / Laura Marling “Master Hunter” / David Bowie “The Next Day” / My Bloody Valentine “New You” / Nine Inch Nails “Find My Way”
DOWNLOAD DISC 2
Justin Timberlake “Pusher Love Girl” / Foxygen “Oh Yeah” / Cults “I Can Hardly Make You Mine” / Janelle Monaé “Dance Apocalyptic” / Brown Eyed Girls “날아갈래” / Coco O. “Where the Wind Blows” / Mariah Carey featuring Miguel “Beautiful” / Eleanor Friedberger “I’ll Never Be Happy Again” / Deerhunter “Dream Captain” / Fear of Men “Ritual Confession” / One Direction “Little Black Dress” / Superchunk “FOH” / Pink featuring Nate Ruess “Just Give Me A Reason” / Killer Mike and El-P featuring Big Boi “Banana Clipper” / Earl Sweatshirt featuring Vince Staples and Casey Veggies “Hive” / Kelela “Enemy” / Rhye “Open” / Goldfrapp “Alvar” / Glass Candy “The Possessed”
DOWNLOAD DISC 3
Chvrches “The Mother We Share” / GEMS “Medusa” / Lorde “Royals” / Vic Mensa “Orange Soda” / Pusha T featuring Kendrick Lamar “Nosetalgia” / Wet “Dreams” / Darkside “Metatron” / The Field “Cupid’s Head” / Major Lazer “Bubble Butt (Remix)” / Pitbull featuring Ke$ha “Timber” / Queens of the Stone Age “Smooth Sailing” / The Preatures “Is This How You Feel?” / Tricot “おちゃんせんすぅす” / Unknown Mortal Orchestra “So Good At Being In Trouble” / Action Bronson featuring Big Body Bes “72 Virgins” / Boards of Canada “Nothing Is Real” / Baths “Ironworks” / Tim Hecker “Virginal II” / Scout Niblett “Can’t Fool Me Now”
DOWNLOAD DISC 4
A$AP Rocky “Long Live A$AP” / Four Tet “Parallel Jalebi” / Blood Orange “You’re Not Good Enough” / James Blake “Retrograde” / Yo La Tengo “Cornelia and Jane” / Kacey Musgrave “Merry Go Round” / Iron & Wine “Grace for Saints and Ramblers” / Eminem featuring Kendrick Lamar “Love Game” / M.I.A. “YALA” / Icona Pop “All Night” / Lady Gaga “Applause” / Basement Jaxx “Back 2 the Wild” / Duke Dumont featuring A*M*E “Need U (100%)” / Betty Who “Somebody Loves You” / Alan Braxe “Time Machine” / Britney Spears “Til It’s Gone” / Jai Paul “Str8 Outta Mumbai” / FKA Twigs “Papi Pacify” / Beck “I Won’t Be Long”
DOWNLOAD DISC 5
Okkervil River “Stay Young” / Elvis Costello and the Roots “Sugar Don’t Work” / Big Sean featuring Kendrick Lamar and Jay Electronica “Control” / Sage the Gemini “Gas Pedal” / Le1f “Plush” / Jessy Lanza “5785021″ / Eric Copeland “Rokzi” / Kurt Vile “Walkin’ On A Pretty Day” / Florida Georgia Line “Get Your Shine On” / Brandy Clark “Stripes” / The National “Don’t Swallow the Cap” / Yvette “Cuts Me In Half” / Grouper “Cloud in Places” / Tove Lo “Habits” / Lone “Airglow Fires” / Dawn Richard “Frequency” / The Weeknd “Belong to the World”
DOWNLOAD DISC 6
Autre Ne Veut “Play By Play” / Atoms For Peace “Default” / La Big Vic “All That Heaven Allows” / Pretty Lights “Color of My Soul” / Majical Cloudz “This Is Magic” / Juveniles “Strangers” / Mount Kimbie featuring King Krule “You Took Your Time” / Schoolboy Q featuring Kendrick Lamar “Collard Greens” / Tyler, the Creator “Jamba” / Bibio “You” / Thee Oh Sees “Toe Cutter – Thumb Buster” / of Montreal “Belle Glade Missionaries” / Marnie Stern “You Don’t Turn Down” / Sophie “Bipp” / The Knife “Full of Fire” / Doldrums “She Is the Wave”
DOWNLOAD DISC 7
Sleigh Bells “Bitter Rivals” / Teen Girl Scientist Monthly “Summer Skin” / Danny Brown “Dip” / Cakes Da Killa “Break Em Off” / Drake “Hold On, We’re Going Home” / San E “이별식탁” / AlunaGeorge “Body Music” / Oneohtrix Point Never “Zebra” / Lana Del Rey vs Cedric Gervais “Summertime Sadness” / Seven Lions vs. Myon & Shane 54 featuring Tove Lo “Strangers” / Octo Octa “His Kiss” / Au Revoir Simone “Crazy” / Alpine “In the Wild” / Phosphorescent “Ride On/Right On” / Burial “Rival Dealer” / VÅR “Begin to Remember” / Yeah Yeah Yeahs “Despair”
DOWNLOAD DISC 8
Chance the Rapper “Good Ass Intro” / Knife Party “Power Glove” / Ciara featuring Nicki Minaj “I’m Out” / Migos featuring Drake “Versace” / The Juan Maclean “Feel Like Movin’” / The Julie Ruin “Cookie Road” / Grass House “The Colours in the Light May Obscure” / Charli XCX “You (Ha Ha Ha)” / Jay Z “Somewhere In America” / J. Cole “Forbidden Fruit” / The Blow “I Tell Myself Everything” / The Range “Loftmane” / Speedy Ortiz “No Below” / Kate Nash “Part Heart” / Electric Six “Show Me What Your Lights Mean” / Paul McCartney “Queenie Eye” / Unmade Beds “Go the Whole Way” / A$AP Ferg featuring A$AP Rocky “Shabba” / Robin Thicke featuring Kendrick Lamar “Give It 2 U” / Dënver “Revista de Gimnasia”
DOWNLOAD DISC 9
G-Dragon “미치GO (GO)” / Arcade Fire “We Exist” / Daft Punk “Get Lucky” / The Head and the Heart “Summertime” / Fleetwood Mac “Sad Angel” / Pearl Jam “Infallible” / Waxahatchee “Brother Bryan” / Future of the Left “The Male Gaze” / DJ Khaled featuring Drake and Rick Ross “No New Friends” / Rudimental featuring Foxes “Right Here” / Classixx featuring Nancy Whang “All You’re Waiting For” / Giant Drag “90210″ / The Dismemberment Plan “No One’s Saying Nothing” / Luke Bryan “Crash My Party” / The Last Hurrah “Lonely Whistle Call” / Sebadoh “Love You Here” / Savages “I Am Here” / Jason Derulo featuring 2 Chainz “Talk Dirty” / MellowHigh “Get’n Drunk” / Sandy Lam “无言歌”
DOWNLOAD DISC 10
Tegan and Sara “Closer” / Fol Chen “A Tourist Town” / Franz Ferdinand “Right Action” / Destroyer “El Rito” / The Flaming Lips “Sun Blows Up Today” / Lee Ranaldo and the Dust “Key-Hole” / Mazzy Star “In the Kingdom” / Julia Holter “Maxim’s II” / Lightning Dust “Diamond” / Rizzle Kicks “The Reason I Live” / Toro Y Moi “Say That” / Bflecha “B33″ / Cassie featuring Jeremih “Sound of Love” / Daughn Gibson “The Sound of Law” / Anna Calvi “Love of My Life” / Cass McCombs “Big Wheel” / Chelsea Light Moving “Heavenmetal” / Candy Claws “White Seal – Shell & Spine” / Factory Floor “Here Again”
Gmail blows up e-mail marketing by caching all images on Google servers
Ever wonder why most e-mail clients hide images by default? The reason for the "display images" button is because images in an e-mail must be loaded from a third-party server. For promotional e-mails and spam, usually this server is operated by the entity that sent the e-mail. So when you load these images, you aren't just receiving an image—you're also sending a ton of data about yourself to the e-mail marketer.
Loading images from these promotional e-mails reveals a lot about you. Marketers get a rough idea of your location via your IP address. They can see the HTTP referrer, meaning the URL of the page that requested the image. With the referral data, marketers can see not only what client you are using (desktop app, Web, mobile, etc.) but also what folder you were viewing the e-mail in. For instance, if you had a Gmail folder named "Ars Technica" and loaded e-mail images, the referral URL would be "https://mail.google.com/mail/u/0/#label/Ars+Technica"—the folder is right there in the URL. The same goes for the inbox, spam, and any other location. It's even possible to uniquely identify each e-mail, so marketers can tell which e-mail address requested the images—they know that you've read the e-mail. And if it was spam, this will often earn you more spam since the spammers can tell you've read their last e-mail.
But Google has just announced a move that will shut most of these tactics down: it will cache all images for Gmail users. Embedded images will now be saved by Google, and the e-mail content will be modified to display those images from Google's cache, instead of from a third-party server. E-mail marketers will no longer be able to get any information from images—they will see a single request from Google, which will then be used to send the image out to all Gmail users. Unless you click on a link, marketers will have no idea the e-mail has been seen. While this means improved privacy from e-mail marketers, Google will now be digging deeper than ever into your e-mails and literally modifying the contents. If you were worried about e-mail scanning, this may take things a step further. However, if you don't like the idea of cached images, you can turn it off in the settings.
Read 2 remaining paragraphs | Comments
Weather wars: who should be allowed to engineer our climate?

“The big thing nuclear weapons did wasn't all the details,” says Harvard climate scientist David Keith. “The really big thing is, they changed what it means to be a nation-state.” It’s on his mind because as the next century unfolds, Keith expects it to happen again.
Scientists usually shy away from Oppenheimer comparisons, but in the case of geoengineering, they’re a given. Spend enough time at geoengineering conferences, and you’re guaranteed to hear a reference to The Bomb. Keith, who has grown into geoengineering’s leading advocate after his recent book on the topic, says the technology would be “as disruptive to the political order of the 21st century as nuclear weapons were for the 20th." It’s an exciting,...
New Spotify report debunks “per stream” payments for artists
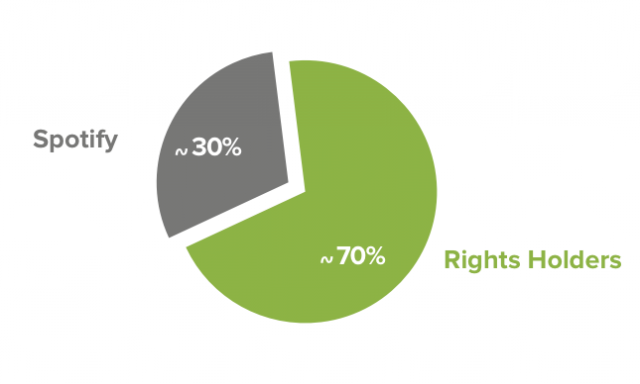
In a report published Tuesday, Spotify revealed the inner workings of its payout systems for artists with music available on the service. The company debunked the claim that the service pays per stream, revealing that things are slightly more complex.
Rather than a flat rate per play of a song, Spotify considers the success of an artist relative to the entire Spotify ecosystem to determine how much money they get. Royalties for, say, one song are paid out based on the proportion of plays it gets out of all of the plays Spotify doles out in a given time period.
There are other factors to the payout formula. How much revenue Spotify earns in a month determines the total amount of royalty money available on a country-by-country basis. After that, Spotify does the math on how much traffic a given artist constituted for the month. For instance, if Spotify has $100 in royalty money from one country and an artist represented 0.01 percent of that month’s streams, the payout for that country would be 0.01 cents.
Read 11 remaining paragraphs | Comments
Healthcare.gov is Hacker-Bait, Say Security Experts
 As it now exists,
Healthcare.gov, the federal exchange for approved health plans,
"creates massive opportunity for fraud, scams, deceptive trade
practices, identity theft and more," Morgan Wright, CEO, Crowd
Sourced Investigations, LLC told the House Science, Space, and
Technology committee in a
hearing held yesterday. He was only one of several
cybersecurity experts who testified as to the vulnerabilities of
the already infamous Website, launched October 1 as part of the
rollout of Obamacare. Perhaps the only saving grace is the
frequency with which Healthcare.gov
crashes, dissuading people from entering information, or even
making use impossible, and so sparing them the high risk of data
theft.
As it now exists,
Healthcare.gov, the federal exchange for approved health plans,
"creates massive opportunity for fraud, scams, deceptive trade
practices, identity theft and more," Morgan Wright, CEO, Crowd
Sourced Investigations, LLC told the House Science, Space, and
Technology committee in a
hearing held yesterday. He was only one of several
cybersecurity experts who testified as to the vulnerabilities of
the already infamous Website, launched October 1 as part of the
rollout of Obamacare. Perhaps the only saving grace is the
frequency with which Healthcare.gov
crashes, dissuading people from entering information, or even
making use impossible, and so sparing them the high risk of data
theft.
In his testimony (PDF), Wright said:
The first major issue is the lack of, and inability to conduct, an end to end security test on the production system. The number of contractors and absence of an apparent overall security lead indicates no one was in possession of a comprehensive, top down view of the full security posture. 3For a system dealing with what will be one of the largest collections of PII, and certain to be the target of malicious attacks and intrusions, the lack of a clearly defined and qualified security lead is inconsistent with accepted practices.
Wright pointed to a flaw involving the management of names and passwords, discovered by a private security researcher, that would have allowed hackers to take control of people's accounts. That hole has been patched, but others have been assigned a fix date of May 31, 2014—while the Website remains up and running.
This is completely unacceptable from an industry perspective, and is in extreme contravention of security best practices. Only in the government could such a gaping hole be allowed to exist without fear of consequence. This shows a lack of understanding for the consequences to consumers and the protection of also creates massive opportunity for fraud, scams, deceptive trade practices, identity theft and more. Much of this is playing out right now.
Avi Rubin, professor of Computer Science at Johns Hopkins University, pointed out (PDF), "One cannot build a system and add security later any more than you can construct a building and then add the plumbing and duct work afterwards." He then discussed the challenges faced in necessarily doing exactly that with the federal exchange.
Dr. Frederick R. Chang, Bobby B. Lyle Centennial Distinguished Chair in Cyber Security at Southern Methodist University, was similarly critical (PDF).
The fact that there is not one single place to sign up for health care coverage will lead to confusion by the public. There is the main federal site, individual state sites, as well as legitimate third party sites. As I understand it, there is no official designation or marking that a consumer can use to determine whether they are on the correct site or not. As people seek to register for health care coverage they may find that there are a dizzying array of websites to select from. When it comes to typing in information like a social security number into a web form, many people might be cautious about doing so, but given that it has do with health insurance coverage people might be more inclined to do so (particularly if they think the request is coming from a legitimate website). These two factors could combine to create a ripe circumstance for personal information to get into the wrong hands. It is difficult to estimate how much traffic these fake websites will siphon off, but it could be significant
David Kennedy, CEO and Founder of TrustedSec, cautioned (PDF) that existing reports of hacking attempts on Healthcare.gov are incomplete and that, because of poor security precautions, "in the event that the website is hacked (or already has been), the attacks would go largely unnoticed and the website would remain compromised for a long period of time." He went on to detail a series of vulnerabilities his company discovered on the site, and then alluded to others he said he was unwilling to publicly reveal.
Kennedy recommended building an entirely new Healthcare.gov website while the first one is up and running (including its flaws) and replacing the existing one when it's ready. If, instead, the already bought-and -paid-for site is taken down for a full fix, "the remediation process will span seven to twelve months at a minimum."
Fixing the exisiting site while it's being used would take even longer.
Password hack of vBulletin.com fuels fears of in-the-wild 0-day attacks
Update:On Monday afternoon, vBulletin Technical Support Lead Wayne Luke issued a statement that said:
"Given our analysis of the evidence provided by the Inject0r team, we do not believe that they have uncovered a 0-day vulnerability in vBulletin. These hackers were able to compromise an insecure system that was used for testing vBulletin mobile applications. The best defense against potential compromises is to keep your system running on the very latest patch release of the software."
The Defcon forums remained unavailable as of Monday afternoon.
Read 12 remaining paragraphs | Comments
American Health Care Killed My Father: David Goldhill on How Consumer-Driven Medicine Saves Lives
In 2007, David Goldhill's father was admitted to a New York City hospital with pneumonia, and five weeks later he died there from multiple hospital-acquired infections. "I probably would have been like any other family member dealing with the grief and disbelief," says Goldhill, a self-described liberal Democrat who is currently the CEO of the Game Show Network. "But," as Goldhill recounts,
A month later there was a profile in The New Yorker of physician Peter Provonost, who was running around the country with fairly simple steps for cleanliness and hygiene that could significantly reduce the hospital-acquired infection rate, but he was having a hard time getting hospitals to sign up for this. I had helped run a movie chain, and we had a rule that if a soda spilled, it had to be cleaned up in five minutes or someone got in trouble. And I thought to myself, if we can do that to get you not to go to the theater across the street, why are hospitals having such a hard time doing simple cost-free things to save lives?
That's how Goldhill first got interested in the economics of the American health care system. In 2009, he published a much-discussed article in The Atlantic, which he has now expanded into a book, titled Catastrophic Care: How American Health Care Killed My Father--and How We Can Fix It.
Goldhill argues that the major problem in health care is a system of incentives that puts most of the purchasing power in the hands of insurance companies and the government, while cutting patients out of the equation. This system isn't just costing us a lot of money, it's killing us. As Goldhill explains, there's a direct link between the way we pay for health care and the estimated 100,000 patients in the U.S. who die every year from infections they picked up in hospital.
Reason TV Contributor Kmele Foster sat down with Goldhill to discuss the problems in our health care system and why turning patients back into customers will go a long way towards solving them.
Produced, shot, and edited by Jim Epstein. Additional camera by Anthony Fisher.
About 30 minutes.
Scroll down for downloadable versions and subscribe to Reason TV's YouTube Channel to receive automatic updates when new material goes live.
It’s official: Computer scientists pick stronger passwords
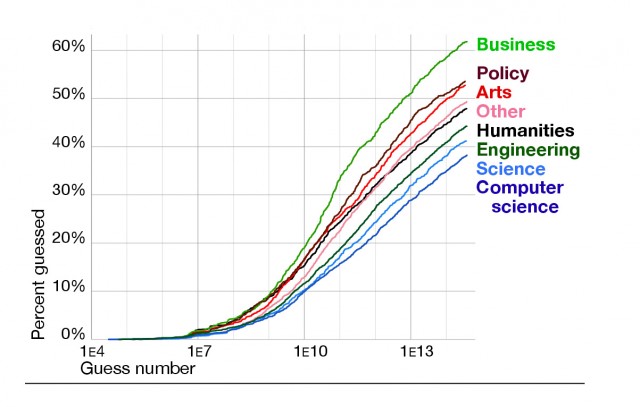
If you're a student or teacher in a computer science school of a big college, chances are good that you pick stronger passwords than your peers in the arts school. In turn, the arts students usually pick better passwords than those in the business school, according to research presented this week.
The landmark study is among the first to analyze the plaintext passwords that a sizable population of users choose to safeguard high-value accounts. The researchers examined the passwords of 25,000 faculty, staff, and students at Carnegie Mellon University used to access grades, e-mail, financial transcripts, and other sensitive data. The researchers then analyzed how guessable the passwords would be during an offline attack, such as those done after hackers break into a website and steal its database of cryptographically hashed login credentials. By subjecting the CMU passwords to a cracking algorithm with a complex password policy, the researchers found striking differences in the quality of the passwords chosen by various subgroups within the university population.
For instance, people associated with CMU's computer science and technology schools chose passwords that were more than 1.8 times stronger than those used by people in the business school. In between these two groups were people associated with the art school. Statistically speaking, passwords picked by computer science and technology users were only 68 percent as likely to be guessed as arts users and only 55 percent as likely to be cracked as people in the business school. Stated differently, the number of attempts required to successfully guess 100 arts school passwords in the typical offline crack would yield passwords for 124 people in the business school and 68 people in the computer science school.
Read 6 remaining paragraphs | Comments
Ross Douthat on the burden and incidence of ACA
As Angus has pointed out, Ross has been on a real roll lately, here is yet another good bit:
Now an effective levy of several thousand dollars on the small fraction of middle class Americans who buy on the individual market is not history’s great injustice. But neither does it seem like the soundest or most politically stable public policy arrangement. And to dig back into the position where I do strong disagree with Cohn’s perspective, what makes this setup potentially more perverse is that it raises rates most sharply on precisely those Americans who up until now were doing roughly what we should want more health insurance purchasers to do: Economizing, comparison shopping, avoiding paying for coverage they don’t need, and buying a level of insurance that covers them in the event of a true disaster while giving them a reason not to overspend on everyday health expenses.
If we want health inflation to stay low and health care costs to be less of an anchor on advancement, we should want more Americans making $50,000 or $60,000 or $70,000 to spend less upfront on health insurance, rather than using regulatory pressure to induce them to spend more. And seen in that light, the potential problem with Obamacare’s regulation-driven “rate shock” isn’t that it doesn’t let everyone keep their pre-existing plans. It’s that it cancels plans, and raises rates, for people who were doing their part to keep all of our costs low.
The full post is here.
Stayaway from Layaway
Layaway plans are immensely popular, a fact I find deeply puzzling much like the popularity of Justin Bieber, Snooki, and homeopathy makes me question the rationality of my fellow human beings.
The typical layaway plan requires a deposit of 10-15% of the price of the good, say a new TV. If the consumer pays the balance over the following 10-12 weeks (i.e. by Christmas) they can pickup the good. If the consumer doesn’t pay the balance they get a refund of payments made less a service fee.
 Walmart and Kmart advertise their layaway plans heavily. I am shocked, however, that so-called consumer advocates also have good things to say about poor people lending big corporations money:
Walmart and Kmart advertise their layaway plans heavily. I am shocked, however, that so-called consumer advocates also have good things to say about poor people lending big corporations money:
Consumer advocates say layaway is a great way to manage a major purchase and stick to a budget, allowing consumers to spread the cost of an item over a number of payments without running up a lot of costly debt.
…”The fees, if any, are generally nominal and probably much lower than the interest you’d pay if you purchased those things with a credit card and didn’t pay off the bill for several months,” said Tod Marks, senior editor and shopping expert at Consumer Reports.
Stop the insanity! The relevant comparison is not to buying on credit but to saving. Instead of lending Walmart money, get yourself an old-fashioned piggy bank and avoid the cancellation fee and the hassle of going to the store to make the periodic payments.
Tod Marks, from Consumer Reports (!), also makes this astounding argument:
With layaway, you don’t have to worry that the store will run out of an item you want,” he said.
Are we living in the Soviet Union? Who worries about Walmart and Kmart running out of goods? Occasionally an item will be discontinued but then the replacement is usually better and/or cheaper. Similarly, layaway plans advertise that you can “lock-in” the current price. Right, and if the price goes down or you find a lower price elsewhere you are similarly locked in.
Still not convinced? In the spirit of Tabarrok’s Wager I offer Tabarrok’s Layaway Plan.
Send me $10 right away along with a message telling me what you want, when you want it and the current price. Save your money. If you save enough to buy the good at the requisite time send me a note and I will heartily congratulate you with a $10 reward. If you don’t save enough, thanks for the $10 and better luck next time. Unlike Walmart I will not guarantee the current price but Tabarrok’s Layaway Plan offers significant advantages that Walmart’s plan does not. On the day that you have saved up enough, Tabarrok’s Layaway Plan lets you buy at any store and at the lowest price that you can find! And that’s not all! Tabarrok’s Layaway Plan offers another great advantage, The Tabarrok Switch™. If you find a good that you like more than the good that you had originally planned to buy the Tabarrok Layaway Plan lets you switch to the new good!
Congratulations on choosing the Tabarrok Layaway Plan, the plan with the most options and flexibility of all layaway plans.
Can Walmart Shake Up The Renewable Energy Sector?
Given that it is the most massive retail store on the planet, Walmart is an unlikely champion for sustainable causes. But it has engaged in the past on issues ranging from local food and responsible sourcing to phasing out toxic chemicals.
Every time Walmart makes a green commitment, it has reverberations throughout entire industry sectors. That's just what happens when you're the world's largest corporation. And that's why Walmart's work in renewable energy could have a major impact.
By 2020, Walmart wants to procure 7 billion kWh of renewable energy (the equivalent of powering 620,000 average American homes for a year).
In 2005, Walmart announced three broad sustainability goals: creating zero waste, selling products that sustain people and the environment, and powering itself by 100% renewable energy. At the time, the company didn't have any set time frame or any real metrics for reaching its goals. Since then, it has reached a number of milestones, including a 20% reduction in greenhouse gases in 2012. By 2020, Walmart wants to procure 7 billion kWh of renewable energy globally (the equivalent of powering over 620,000 average American homes for a year), and reduce its energy demand on a per square foot basis by another 20%.
Today, Walmart has 150 solar installations in seven countries, as well as 26 fuel cell installations in the U.S. and a smattering of experimental micro–wind and large scale wind projects (hundreds of stores in Mexico also purchase wind power from Eléctrica del Valle de Mexico).
"One of the big paradigm shifts was that we had to start opening up our doors. In the past, we thought we could keep our heads down. We had to learn from experts, and we started meeting with NGOs and academia," says Kim Saylors, VP of Energy at Walmart.
Jenny Ahlen, a project manager at Environmental Defense Fund, has worked since 2011 at EDF's small office in Bentonville, Arkansas––a branch of the nonprofit dedicated to working with Walmart. EDF isn't the only NGO that Walmart works with, but the two organizations have a close relationship. On the day that Ahlen and I spoke, she had just wrapped up a coffee meeting with Greg Poole, who makes deals for Walmart's renewable energy arm. "We have learned a lot about how Walmart functions," she says.
We had to learn from experts, and we started meeting with NGOs and academia.
In the renewable energy arena, she says, Walmart is taking a piecemeal approach, where lots of individual projects add up to an impressive whole. Still, Walmart has its share of challenges to deal with: technologies are still evolving, and regulatory and financial hurdles abound.
"Like any big company, there's always going to be fire drills moving people's resources and time away from daily activities, which can slow progress," Ahlen says.
SolarCity, one of a handful of solar leasing companies operating in the U.S., has worked with Walmart on the majority of its solar installations (and will presumably continue to work with the company as it ramps up to solar photovoltaic systems in 6,000 stores in the next six years). Lyndon Rive, the CEO and founder of SolarCity, believes that Walmart chose to work with his company because of simple economics. "There is no capital investment, installation is free, and you lock in electricity pricing for 20 years [with SolarCity's solar leasing plan]," he says. "It's a mistake not to do it."
Just in terms of our ability to get a product approved ... in China it is very difficult.
Plus, Saylors says, "We didn't know enough about the technology to own and operate the systems." The easiest and most efficient option was to enter into power–purchase agreements, where solar providers either own or operate the systems and sell the power to Walmart.
Walmart's emphasis on cost–effectiveness––the company wants ditch fossil fuels, but nothing passes muster if it doesn't make excellent financial sense––means that solar still is limited to certain locations. In states where the retail cost of energy is low (including many states in the Midwest), Saylors says that Walmart is "continuing to make progress," but that it doesn't yet have the full answer as to how it will deal with these more challenging markets.
SolarCity itself doesn't yet operate in all 50 states because of poor economics. But, says Rive, "In most states where the cost is really low, it's because they're burning the most coal. As our costs come down, we will be able to expand into newer states." (The cost of solar is rapidly dropping in many states).
For Walmart, U.S. markets aren't nearly as challenging as foreign markets. "Just in terms of our ability to get a product approved ... in China it is very difficult. We just got the first solar installation on a rooftop that was a non–government building. That was a big deal," says Saylors.
Walmart is not going to do something that's not cost–effective.
Ultimately, Walmart believes that it won't be able to reach its renewable energy goals without new technologies coming on the market––the company can't just rely on rooftop solar (and the micro–turbine tests haven't been as successful as Walmart hoped, though Saylors says that the company still thinks the technology has a future). "We do believe that new, innovative technology will have to continue to help us," she says.
Even though the company still has a long way to go to reach its goals, it has already impacted the larger solar market in the U.S. Once Walmart announced that it was beginning to rely on solar, Saylors says that the retail chain received tons of calls from other companies wanting to learn more. At the same time, she believes that Walmart's commitments have helped solar companies drive down the costs of solar since "they could go out and buy larger amounts and know they had someone there ready to consume it."
Rive thinks that the mere fact of Walmart's budget–consciousness may have increased the size of the corporate solar market. "Some companies that want to do the right thing but don't mind spending more money––that carries less weight. Walmart is not going to do something that's not cost–effective," he says. So far, it is: in 2012 alone, Walmart saved $2 million by relying on solar installations instead of traditional energy sources.
When those new and innovative energy technologies come along, they should be so lucky as to get a boost from the world's largest company. It's the best advertisement that anyone could ask for.
No––You Don't Need To Learn To Code
Imagine being harangued by a deluge of articles with headlines like "Why everyone should learn to knit." With all due respect to knitters, it would seem ridiculous. Yet the rallying cry to learn to code has become so pervasive that we're barely surprised when a software developer in New York engages in a highly publicized attempt to teach a homeless man how to code. New York Mayor Michael Bloomberg famously told the press last year that even he planned to take a course on Codecademy, but of course, you can also get programming tutorials from Bill Gates or Mark Zuckerberg on Code.org. Oddly, even non–technical people like VCs are urging you to learn to code.
I'm a programmer. Do I think everyone should learn how to code? No. Here's why.
The Joys Of The Craft
The software project management classic The Mythical Man–Month opens with a description of the joys and woes of the craft of coding.
Why is programming fun? What delights may its practitioner expect as his reward?
First is the sheer joy of making things. As the child delights in his mud pie, so the adult enjoys building things, especially things of his own design. I think this delight must be an image of God's delight in making things, a delight shown in the distinctness and newness of each leaf and each snowflake.
I have no recollection of the content of the first programs I wrote; I just remember that it was fun. One Christmas in the 1980s, my sisters and I got a Sharp personal computer for Christmas. Mostly we used it to play Pac–Man (which was stored on a cassette tape), but the machine also came with a BASIC compiler and that's how I first learned how to program. Coding came easily to me and was something that I could do for hours on end. Like games, code gives you constant feedback, and for that reason can quickly become addictive, but it's also a massively time–consuming and often maddening activity. In describing the woes of the craft, Brooks refers to the "dreary hours of tedious, painstaking labor" and the perfect precision required to communicate with the machine. "If one character, one pause, of the incantation is not strictly in proper form, the magic doesn't work."
Like any skill, you can only become good at it by ploughing through hours and hours of boring practice, and there are many other things you could do with your time. Coding trains you to think in a certain fashion, and while it can teach you useful cognitive skills like breaking down problems, that thinking can be rather narrow. Sitting still and staring at a screen for days, and sometimes nights, on end is detrimental to your health and general well–being. Finally, competence is the currency of the development world. Good coders don't want to work with beginners and do not like to see their craft devalued by hoards of "instant" developers cranked out of short courses, although they may be prepared to mentor you if they see potential. Still think you want to learn how to code? Read on.
Why Do You Want To Code?
Coding is not a goal. It's a tool for solving problems. Even professional developers can forget that when they get caught up in the minutiae of a new language or a religious argument over the best IDE (Integrated Development Environment). The best "learn to code" candidates are often scientists or professionals in other fields who can use code to solve the problems they see in front of them. Think of what a social scientist can learn from Facebook or Twitter data. The Nobel prize for chemistry was just awarded for computer modeling of chemical reactions. Much of the coding done by researchers wouldn't pass muster in a professional software team, and often falls more into the category of scripting, but that doesn't mean that some coding knowledge can't improve results in other fields.
However, much of the "learn to code" frenzy seems to spring from the idea that you can achieve fame and riches by starting a tech company and you need to actually code something first. Programming is not a get–rich–quick scheme. Even if you do hit the jackpot, the CEOs of successful tech companies do not spend a lot of time coding, even if they started out behind a keyboard. There are simply too many other tasks involved in running a company. So if coding is what you really love to do, you probably wouldn't want to be a CEO in the first place.
Some people learn the piano simply in order to play a particular piece of music they love. In the same way, if you have a problem which can be solved with code, and which nobody will develop for you, go ahead and learn to code to create it, but be aware that if it becomes successful you will probably need to hire a professional to rewrite the whole thing. Think of your effort as a prototype which you can use to get feedback on your idea.
Code Cannot Solve Every Problem
All that time spent in front of a screen battling, often self–created problems can lead coders to the conclusion that every problem can be solved with more or better code. It can't. The biggest problems always involve people as well as systems, and people are annoyingly messy and unpredictable. One of the joys of coding is that when you do hit on the perfect incantation, the machine will do exactly what you asked over and over again in a reliable manner. People rarely do that, and systems which rely on people don't either. The story of developer Patrick McConlogue trying to teach a homeless man called Leo how to code illustrates this delusion perfectly. It's not that Leo couldn't learn, but that there are so many other resources needed to get to the stage where you can make your living as a coder. A few days ago Leo was arrested for trespassing in a city park and his laptop was confiscated. Homelessness is a complex problem and code alone isn't going to solve it.
Learn To Program... In 10 Years
Peter Norvig, director of research at Google, wrote that the prevailing trend implies that "Bad programming is easy. Idiots can learn it in 21 days, even if they are dummies." The fact that you can make a sound on a flute doesn't mean that you can compose a flute concerto. In the same way, throwing together a bit of JavaScript does not qualify you to build complex, scalable systems.
If you do want to become a professional developer, or you find that you just really enjoy programming, then by all means continue to build your knowledge. Going from self–taught hobbyist to competent software developer is not usually a short road, but it is a well–trodden one in the software world. As long as you are competent, other coders don't really care where or how you acquired your skills.
Norvig gives excellent advice on how to become a good developer, as opposed to someone who can string a few lines of code together. Learn at least half a dozen languages, work on projects with other coders who will either openly mock your mistakes or pass silent and withering judgement on your ignorance, maintain somebody else's code, and learn the basics of how the hardware on which your software runs actually works. Sounds exhausting? Here are a few alternatives.
Instead, Learn To Understand Coders!
If you still want to work in the tech world but are reconsidering coding, designer Nick Marsh suggests doing something coders find useful. Brilliant as great developers are, there are plenty of things that they hate doing or are just no good at. Coding requires a level of focus bordering on tunnel vision, and if there's one thing developers hate, it's distractions. For a coder "distractions" mean dealing with business people, management, customers or, in fact, anyone outside the engineering team. If you want to get popular with developers, spare them from some of these interactions, which they often see as a shocking waste of their time. A great product manager, for example, is as crucial to success as a competent coder. It doesn't matter how clear the code is, if nobody wants the product. Translate the language of the developers into that of the users and vice versa. Promote the product. All makers of creative work want their work to be used. Marsh concludes that it's much more important to understand coders than to understand code.
Learn How Everyday Software Works
Unless your goal is to become a professional programmer, it may be more useful to learn the basics of how the networks and software you use every day work, and their biases and blind spots, rather than go about adding to the world's stock of bad code. You can drive a car without knowing how an engine works, but it would be handy to know what makes the engine stall or that the steering skews to the right. Knowing how to evaluate the privacy bargain we make with tech companies, escape the filter bubble, analyze the values behind a piece of software, verify information you get on Twitter, understand how the Internet is structured or how search and recommendation algorithms work, is probably more valuable in everyday life than writing Python code.
Learn Something Else Entirely
The Greek physician Hippocrates said "Ars longa, vita brevis," meaning "The craft is long, Life is short." So choose your craft wisely. In the time that you saved by not learning to code, learn to do something you enjoy more. Playing a musical instrument has been proven to improve other mental functions including creativity, as well as bringing joy to the player. Yoga expands your world view as well as stretching your body. To give pleasure every day, don't learn how to code; learn how to cook. Finally, engineering manager Rands In Repose suggests learning to write in your own language.
Your readers are far more critical than the Python interpreter. Not only do they care about syntax, but they also want to learn something, and, perhaps, be entertained while all this learning is going down. Success means they keep coming back––failure is a lonely silence. Python is looking pretty sweet now, right?
Maybe coding would be easier after all.
Miley Cyrus' 'Wrecking Ball' Is No. 1, But Is It A Real Hit?
Based on the data, Katy Perry's "Roar" feels like a culture-dominating No. 1 hit, while "Wrecking Ball" feels a bit like a trollgaze meme. But on a chart with a history of one-off, faddish but surprisingly enduring No. 1 hits, Cyrus' song is part of a long tradition.
Be Paranoid
“What are you afraid of Matt?”
That was the subject line of an email I received in April 2003, shortly after I wrote a column for the progressive website AlterNet warning about the federal government’s post–PATRIOT Act plans to increase warrantless surveillance on unsuspecting U.S. citizens.
“I wonder about you lefties who fear these upgraded measures of security,” a person identifying herself as Lynn McLaughlin wrote to me. “You must have something to hide, and since my husband works for the DIA, I’ll make sure he looks into what it may be.”
The DIA stands for the Defense Intelligence Agency, the central collector and interpreter of foreign military intelligence for the United States Armed Forces. According to the agency’s website FAQ at the time (though not now), the DIA was “prohibited by law and in no circumstance does it collect information on U.S. citizens or on information not related to military intelligence.”
Though exact figures for budget and payroll are classified “due to security considerations,” the DIA has an estimated 16,500 employees—just a bit more than the number of agents working for the FBI. One of those employees at the time, I was told by someone in the public relations department, was a computer systems analyst named Wayne McLaughlin.
They say the past is a different planet, but spring 2003 was a different universe. The Iraq War had begun. The congressional 9/11 Commission, after being slowed every step of the way by a defiant Bush administration, was only beginning to hold hearings 19 months after the attacks. And my main concern in alerting the feds about my correspondent was to make sure America’s defense wasn’t being needlessly jeopardized by a loose-cannon spouse. Surely my own government wouldn’t snoop petulantly—and illegally—into its citizens’ affairs?
Boy, was I stupid.
We now know that 2003 was the year the National Security Agency (NSA) opened up Room 641A at an AT&T building in San Francisco to tap into and analyze data flowing through the Internet backbone, even as then–Attorney General John Ashcroft was dismissing privacy objections to the PATRIOT Act as “baseless hysteria.”
And thanks to an avalanche of revelations this spring and summer triggered by leaks from former NSA contractor Edward Snowden, we know that the federal government has collected email and telephone data on “hundreds of millions of Americans” (according to McClatchy News Service), is “systematically searching—without warrants—through the contents of Americans’ communications” (New York Times), and is sharing that data with a “secretive U.S. Drug Enforcement Administration unit” that targets Americans then covers its investigatory tracks with prosecutors and judges (Reuters).
As the fog of post-9/11 executive-branch activity slowly begins to lift, one thing has already become clear: We are losing the bedrock American notion that citizens should be able to go about their daily affairs without being monitored by their government. The Fourth Amendment stipulations that people “be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures,” and that “no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized,” have been shredded beyond recognition.
Walk around in lower Manhattan? The New York Police Department is watching you, on camera. Soon those cameras will be supplemented by a fleet of unmanned surveillance aircraft (see “Drones Away,” page 32). Turn on your cellphone? Government-run “Stingray” towers collect and transmit your geolocation data within an accuracy of six feet. Where those don’t yet exist the feds can always compel phone carriers to cough up all your relevant information.
Bank accounts. Medical information. Any sensitive data you willingly divulge to a third party. What Washington isn’t demanding overtly, it is rifling through covertly, without notification of those being targeted. Probable cause in 2013 America is a folk tradition, not a binding constitutional limitation on power.
Nobody wants to go through life paranoid, muttering about elaborate conspiracies while shaking a fist at the sun. (For a history of this tendency in U.S. politics, including the ways dissenters have been marginalized as being unhinged, see Jesse Walker’s “America the Paranoid,” page 52.) But the rude fact is that the executive branch is conducting all this contra-constitutional surveillance while constantly lying about it.
“There is no spying on Americans,” President Barack Obama lied to Jay Leno in August. “We don’t have a domestic spying program.” (For an examination of the president’s mendacity, see “Obama’s Flip-Flop on Spying,” page 10.) In March, when asked by Sen. Ron Wyden (D-Ore.) whether the NSA collects “any type of data at all on millions or hundreds of millions of Americans,” Director of National Intelligence James Clapper also lied: “No, sir.”
These bald-faced deceptions suggest a national security culture accustomed to doing and saying anything without fear of adverse consequences. A president who gained office by mobilizing the anti-war, anti-torture, pro–civil liberties vote is now operating secret prisons in Somalia, authorizing lethal drone strikes against Americans, and intervening personally to keep a Yemeni journalist in jail for doing his job—all without losing much support from his political base. Obama has locked in the George W. Bush/Dick Cheney policies he so skillfully campaigned against. (For more on these and other outrages, see our interview with Dirty Wars author Jeremy Scahill on page 42.)
The key behind all these programs is secrecy, invoked in the name of national security. We’re only beginning to understand the scope of NSA skullduggery because of a leaker who fled the country and is wanted back home under the Espionage Act, an odious Woodrow Wilson–era law that the Obama administration has used to unprecedented effect on journalists and leakers. The White House says with a straight face that the president “welcomes a debate about how best to simultaneously safeguard both our national security and the privacy of our citizens” even while he’s attempting to imprison those who started the conversation in the first place.
The secrecy has gotten so out of control that the very legal reasoning the government relies on in its snooping has been persistently and successfully shielded from public view, despite the best efforts of civil libertarians such as Sen. Wyden and Rep. Justin Amash (R-Mich.). To sum up: The executive branch is furiously trying to prevent citizens from knowing that they can be spied on, from knowing whether they are being spied on, and from knowing what legal theory the feds are using in the conduct of their spying. There can be no co-equal branches of government in this scenario. The legislature cannot be responsive to informed public opinion when the public is prevented from having one.
When the constitutional balance goes so far out of whack, democratic legitimacy is not far behind. As the press critic Jay Rosen put it in August, “Can there even be an informed public and consent-of-the-governed for decisions about electronic surveillance, or have we put those principles aside so that the state can have its freedom to maneuver?” The answer for more than a decade now has been grim.
That is finally beginning to change. In July Amash came within an eyelash of having the House of Representatives vote to defund the NSA program that Snowden exposed. That same month, the Pew Research Center found that, for the first time in its nine years of polling the question, more Americans feared intrusion on their civil liberties than feared a terrorist attack. The more Americans find out about their lawless executive branch, the more they rebel.
When government is lying to you about the constitutional rights it routinely violates, it’s time to change your habits of mind. No more blank checks. No more “trust, but verify.” No more hoping for the best. Be paranoid. (PublicAffairs).
Forward Spam Text Messages to 7726 to Report Them
NIN enters the 'loudness war' with multiple versions of new album

Nine Inch Nails is offering its new album, Hesitation Marks, in two different ways: a standard mix for the CD, iTunes, and other digital stores, and a different mix catered to audiophiles available through the band's website. This second "audiophile master" mix is the latest salvo against the overbearing loudness of pop music today, and, according to the band, it's the first time that anyone has mastered the same album twice for different audiences.
Most songs produced today are louder than ever before, and have less variance between the loud and soft sounds within their tracks. This "brickwall" method of mixing music (which refers a very compressed and loud audio track) is generally derided by audiophiles because it eliminates the...
'Japan World Cup 3': Everything's Made Up and the Points Don't Matter

Over the years, Japan has earned a reputation for producing some of the most bizarre and highly entertaining content on the planet. Thanks to games like Japan World Cup 3, it's easy to see why.
Originally released in 2011, Japan World Cup is a computer-generated Web browser game in which players bet on the outcomes of races that feature jockeys riding anything from a Trojan horse to a Yeti. In 2012, these predetermined scenes were compiled into three DVDs (a copy of Japan World Cup 3 can be purchased for $34.49 on Amazon).
To say that the racing sequences are absurd would be an understatement. In May, Hightower and AxialMatt of the Achievement Hunter Community Video channel uploaded a five-minute clip with footage from the third DVD to YouTube. The insanity of the game — which features a horse on its hind legs doing the Charleston as well as a limousine equine with multiple naked jockeys on its back — coupled with the hilarious reaction heard on the voice-overs, is a great recipe for laughs. Read more...
More about Reddit, Gaming, Videogames, Japan, and Online GamingAre we the last generation that will know a free Internet?
Governments all around the world are changing their relationship to the Internet. It's a war of Internet norms.
Atlas of Prejudice
Alphadesigner continues to take satirical mapping to a new level, with several dozen maps of stereotypes, from many different perspectives, updated regularly.

MIT Delays Release of Aaron Swartz's Secret Service Files

The Massachusetts Institute of Technology filed a motion on Thursday to delay the release of the Secret Service files on Aaron Swartz, the late hacker and Internet freedom activist.
In an unusual and last-minute move, lawyers representing MIT successfully blocked the release of the files, under claims that the documents might identify MIT employees who may have helped the prosecution press criminal charges against Swartz. The first batch of files were scheduled for a Friday release after Wired's investigations editor Kevin Poulsen won a FOIA lawsuit
See also: Is Strongbox the New Wikileaks?
"I have never, in fifteen years of reporting, seen a non-governmental party argue for the right to interfere in a Freedom of Information Act release of government documents," Poulsen wrote in a post explaining the circumstances. "My lawyer has been litigating FOIA for decades, and he’s never encountered it eitherIt’s saddening to see an academic institution set this precedent." Read more...
More about Mit, Secret Service, Aaron Swartz, Us World, and UsDisgruntled Google users try to live a low-Google lifestyle
Google’s services are undergoing some shape-shifting lately, with new features in places like Hangouts and the Latitude redundancy. Other services, like Reader, are simply disappearing.
Given the breadth and depth of Google's services, many people use at least one of them. But a pair of writers have become uncomfortable with how the company has not only permeated their lives, but how it keeps rearranging itself. Over the last few days, these two have laid out their plans for moving on.
Physicist and engineer Sam Whited wrote about his preferred Google service replacements: OpenStreetMap and MapBox for Maps, DuckDuckGo for search, App.net or Diaspora for Google+, and GNU IceCat or Firefox for Chrome. Whited added that he’s sticking with Gmail as he hasn’t been able to find a suitable free alternative.
Read 2 remaining paragraphs | Comments
We Were The (1000+). Goodbye, Google Reader

“We launched Google Reader in 2005 in an effort to make it easy for people to discover and keep tabs on their favorite websites. While the product has a loyal following, over the years usage has declined. So, on July 1, 2013, we will retire Google Reader.” – Google, March 2013.
Today, Google Reader’s remaining users will “Mark All As Read” one last time. There are two schools of thought on Google’s decision to move on from its aging RSS aggregator, never adopted by the mainstream: one, that’s it’s pretty much the worst thing to ever happen to the Internet. Ever! And two: who cares?
Even though I count myself as someone who falls into that earlier group, it’s hard to argue against Google’s thinking in the matter. Following websites using RSS feeds is just not something the “normals” do. So an RSS reader like Google’s remained in the hands of the tech elite, the domain of the I.T. crowd, the programmers, the researchers, the journalists.
The rest of the world merely surfs the web, and now they just tweet.
But Google Reader was special because it was one of the last remaining places on the Internet you could really call your own. In every other way, the nature of news reading on the web these days and the social services that now dominate your attention are crafted by others who dictate what you will read and when. Whether browsing through an editorially run news site, parsing your Twitter stream or reading your Facebook News Feed, the links before you are those that others have deemed important.
There’s value in this signal, of course – a sense of what’s trending in the larger world allows for serendipitous discovery. But it’s also a relinquishing of control. Oh sure, you can choose who to follow, but it’s not the same as choosing which news news sources’ feeds you will subscribe, why, and how often you will read them.
In Google Reader, I’ve gleefully stuffed websites into collections like “B-List” and “C-List” and “Can’t Miss” and “Panic Button,” instead of more proper names like “top tech sites” or “Apple bloggers.” It’s my decision which headline collections get scanned with a glance, and which writers will see me devouring their every word.
Meanwhile on Twitter, every missive is as important as the one that preceded it. A photo of your cat. News from the war. A beautiful sunset on Instagram. A government overthrown. It’s a real-time firehouse of information that you dip into as you can. There’s no unread count. You just refresh and refresh and refresh for more.
Days Until Cancellation: 0
Having never caught on as a social network in its own right outside of a niche group of users, Google Reader couldn’t rival something like Twitter. The writing was on the wall for its demise when Google ripped out the social features in the product back in October 2011 in order to make room for deeper integration with Google’s newer social network Google+.
The move, essentially a big @#$% you to Reader’s small but highly engaged audience of users, may have come as a surprise to some, but with the internal thinking at Google, perhaps it was a miracle that Reader was being given any sort of development attention at all.
In the definitive recounting of Google Reader’s history here on BuzzFeed, Brian Shih, who became Reader Product Manager in fall 2008, spoke of how the team had to fight internally for what, in terms of Google’s scale, was a really, really, really small project. “Someone hung a sign in the Reader offices that said “DAYS SINCE LAST THREAT OF CANCELLATION.” The number was almost always zero,” he said.
At Google, senior execs only cared about absolute user numbers, not on growth or market share.
But even though Google Reader could never compete in numbers with Gmail or other Google products, it wiped out the market of RSS competitors, while letting its 800-pound gorilla sit and rot.
Today, Google is too busy trying to change the world with self-driving cars and face computers, search engines that think for you and a balloon-powered Internet to care about Google Reader. It’s thinking of how to dominate mobile and connect the next 5 billion users to the web – lofty goals that leave no time for a silly little product from Web 2.0′s early days.
At least by shutting down Reader, Google is admitting that its stewardship in this area has failed.
Google can’t – and no longer wants to – do it all.
We’ve seen evidence of that already in the systematic shutdowns of other dated, stagnant services through Google’s “Spring Cleanings.” Google Reader was not the first, nor will it be the last that fails to survive these cuts. Google Alerts and Feedburner are other prime candidates at this point.
We’re retiring Reader on July 1. We know many of you will be sad to see it go. Thanks for 8 great years! http://t.co/0jtSqBnORp
— Google Reader (@googlereader) March 13, 2013
Ever since Google’s announcement this spring, many new services have stepped up to help fill the void Google Reader leaves behind, but none will ever fill its shoes. None of those that now vie to become the new incumbent even have search built in, for example. A few promise “yeah, it’s coming” but too many startups begging for a second look think that merely supporting RSS feeds makes them a Google Reader clone.
Google Reader wasn’t a list of things to read. It wasn’t a collection of RSS feeds.
It was your own, personal Google. A search engine built on top of the sites you cared about. A Google News with the stories you wanted to see. A taxonomy where you chose the labels, and drove the SEO. Google Reader was your web, your slice of the Internet.
Social media, now, is theirs.
Reader’s death isn’t the end of a product, it’s the end of an era. We have protested, bargained, begged, and cried. Now we have to accept and adapt.
Google Reader, thank you for eight great years.
Goodbye.
shift-a
OK kids, it's time. Throw this on in one tab http://t.co/Mj3njMeWZn open "All Items" in @GoogleReader & "Mark all as read" One. Last. Time.
— Jason Shellen (@shellen) July 1, 2013
Commit Any Felonies Lately?
Elizabeth Daly went to jail over a case of bottled water.
According to the Charlottesville Daily Progress, shortly after 10 p.m. on April 11, the 20-year-old U.Va. student bought ice cream, cookie dough and a carton of LaCroix sparkling water from the Harris Teeter grocery store at the popular Barracks Road Shopping Center. In the parking lot, a half-dozen men and a woman approached her car, flashing some kind of badges. One jumped on the hood. Another drew a gun. Others started trying to break the windows.
Daly understandably panicked. With her roommate in the passenger seat yelling “Go, go, go!” Daly drove off, hoping to reach the nearest police station. The women dialed 911. Then a vehicle with lights and sirens pulled them over, and the situation clarified: The persons who had swarmed Daly’s vehicle were plainclothes agents of the Virginia Department of Alcoholic Beverage Control. The agents had thought the sparkling water was a 12-pack of beer.
Did the ABC’s enforcers apologize? Not in the slightest. They charged Daly with three felonies: two for assaulting an officer (her vehicle had grazed two agents; neither was hurt) and one for eluding the police. Last week, the commonwealth’s attorney dropped the charges.
The agents’ excessive display of force is outrageously disproportionate to the offense they mistakenly thought they witnessed: an underage purchase of alcohol. But in a sense, Daly got off easy. A couple weeks after her ordeal, a 61-year-old man in Tennessee was killed when the police executed a drug raid on the wrong house. A few weeks later, in another wrong-house raid, police officers killed a dog belonging to an Army veteran. These are not isolated incidents; for more information, visit the interactive map at www.cato.org/raidmap.
They are, however, part and parcel of two broader phenomena. One is the militarization of domestic law enforcement. In recent years police departments have widely adopted military tactics, military equipment (armored personnel carriers, flashbang grenades) – and, sometimes, the mindset of military conquerors rather than domestic peace-keepers.
The other phenomenon is the increasing degree to which civilians are subject to criminal prosecution for non-criminal acts – including exercising the constitutionally protected right to free speech.
Last week A. J. Martin was arrested in Harrisburg, Penn., for writing in chalk on the sidewalk. Martin was participating in a health-care demonstration outside Gov. Tom Corbett’s residence when he wrote, “Governor Corbett has health insurance, we should too.” Authorities charged Martin with writing “a derogatory remark about the governor on the sidewalk.” The horror.
This follows the case of Jeff Olson, who chalked messages such as “Stop big banks” outside branches of Bank of America last year. Law professor Jonathan Turley reports that prosecutors brought 13 vandalism charges against him. Moreover, the judge in the case recently prohibited Olson’s attorney from “mentioning the First Amendment, free speech,” or anything like them during the trial.
In Texas last month, a woman was arrested for asking to see a warrant for the arrest of her 11-year-old son. “She spent the night in jail while her son was left at home,” reports Fox34 News. The son never was arrested. Also in Texas, Justin Carter has spent months in jail – and faces eight years more –for making an admittedly atrocious joke about shooting up a school in an online chat. Though he was plainly kidding, authorities charged him with making a terrorist threat.
Federal prosecutors also recently used an anti-terrorism measure to seize almost $70,000 from the owners of a Maryland dairy. Randy and Karen Sowers had made several bank deposits of just under $10,000 to avoid the headache of filing federal reports required for sums over that amount. The feds charged them with unlawful “structuring.” Last week they settled the case. Authorities kept half their money to teach them a lesson.
“I broke the law yesterday,” writes George Mason economics professor Alex Tabarrok, “and I probably will break the law tomorrow. Don’t mistake me, I have done nothing wrong. I don’t even know what laws I have broken. . . . It’s hard for anyone to live today without breaking the law. Doubt me? Have you ever thrown out some junk mail that . . . was addressed to someone else? That’s a violation of federal law punishable by up to five years in prison.” Tabarrok notes that lawyer Harvey Silvergate believes the typical American commits Three Felonies a Day – the title of Silvergate’s book on the subject.
As The Wall Street Journal has reported, lawmakers in Washington have greatly eroded the notion of mens rea – the principle that you need criminal intent in order to commit a crime. Thanks to a proliferating number of obscure offenses, Americans now resemble the condemned souls in Jonathan Edwards’ “Sinners in the Hands of an Angry God” – spared from perdition only by the temporary forbearance of those who sit in judgment.
“What once might have been considered simply a mistake,” the Journal explains, is now “punishable by jail time.” And as 20-year-old Elizabeth Daly has now learned, you can go to jail even when the person making the mistake wasn’t you.
This article originally appeared in the Richmond Times-Dispatch.
A New Ingeniously Designed Shelter For Refugees—Made By Ikea
Today, the best shelter we can usually offer the world’s tens of millions of refugees is a tent. So the folks who make your bookcase (and bed, and table) have designed a cheap, solar-powered hut that only takes four hours to assemble but offers refugees more protection and privacy.
What do you do when a flash mob of a million homeless refugees shows up to your third world country from the neighboring third world country? Make them sleep on the hot (or cold) ground and wait for the United Nations to show up with crappy tents, of course.
Until next month, that is, when you’ll be able to put them up in solar-powered huts on the cheap. In July, Ikea Foundation and the United Nations High Commissioner for Refugees (UNCHR) will roll out one of the major innovations for war-torn homeless since the canvas tent: cheap, flat-packed, build-it-yourself homes with electricity-generating roofs.

More than 43 million people--globally--live as refugees or "internally displaced" (refugees within their own countries), having fled home due to "a well-founded fear of persecution" of race, religion, nationality, or socio-political membership. Right now, 3.5 million of them live in UN-provided tents, says Per Heggenes, CEO of the Ikea Foundation. "They offer little comfort, dignity, or security," he continues. "Further, the existing tents are cold in the winter and hot in the summer. They have no electricity or lighting, limiting refugee families’ ability to lead a normal life."
Eighty percent of refugees are women and children, and 80% of these end up in undeveloped countries. Many remain in limbo for more than a decade at a time, waiting for tension to cool down in their home countries and struggling to find work in new territory. (Imagine Tom Hanks in that one movie where he’s stuck in the airport, only with dirt floor, no air conditioning, and multiplied by 3,500,000 people.)
Up to this point, the best elemental protection relief workers could often provide refugees have been cheap, canvas UN tents that start to disintegrate after about six months.

The new Ikea-designed shelters are built to last 10 times that long. They’re twice as large as an old-school refugee tent, at 17.5 square meters (fitting five people comfortably) and take about four hours to assemble, which is about how long it took my lawyer friend, Frank, and me to bolt together my giant Ikea bookshelf the other day.
Unlike my bookshelf and other standard, wood-based Ikea fare, the shelters are made from lightweight, Porta-Potty-style plastic mounted on a supersteel skeleton. To make them cost-effective to build, assemble, and ship, the Refugee Housing Unit, which is manufacturing the actual shelter components per the Ikea Foundation’s design, developed a new type of polymer siding called Rhulite that lets light in during the day but keeps light from casting embarrassing shadows outside during the night--a privacy concern with the current UN tents that leads to many refugees extinguishing what little candle- or kerosene-lighting they can afford.
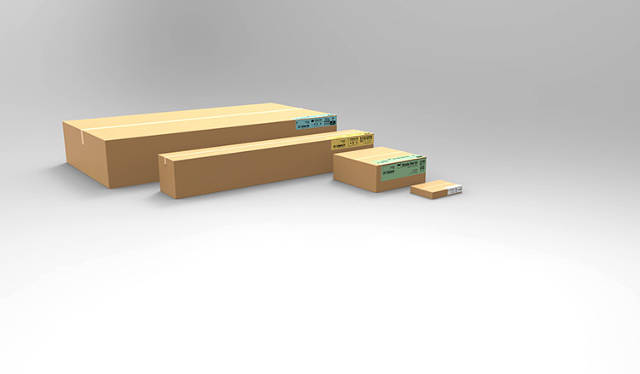
"It is important that the shelter is lightweight enough so that it can be easily and cost efficiently transported, but strong enough to withstand the harsh conditions of refugee camps," says Johan Karlsson, Project Manager at Refugee Housing Unit. "The design is to balance the mechanical properties such as UV, structural strength, insulation, cost and a very specific requirement for this application: privacy."
During the day, an external screen on the shelter’s roof provides 70% solar reflection and cooling, and at night it keeps heat in. "The net is knitted from technical textile made interlaced with aluminum and polyolefin strips," Karlsson sys. "On top of the shade net is solar panel laminated on a thin plastic film, taking away the bulky panels used traditionally."

Ikea and UNHCR will beta test the shelters in Ethiopia next month, then iterate to a final design for mass production. The RHU is keeping an eye on the development of Organic Photo Voltaic cells (OPV) that could one day be printed directly onto the shade net and scale up enough solar power to run water purification and cooking devices. But until then, each flat-packed kit will come with a single solar panel that powers a built-in light and a USB outlet.
At first blush, the USB seems odd, but it actually speaks to at least one aspect in which high tech has brought the world together. We 7 billion Earthlings may look, speak, and worship in a thousand different ways, but we all plug our mobile phones into the same four-pin port. And soon, hopefully, we’ll all be able to take care of our unfortunate neighbors a little better, too.
Easy Credit Is Inflating a Massive Student-Loan Bubble
Americans are still talking about the recently deflated housing bubble, but there’s a new bubble in town. It’s the student loan bubble and when this one pops, it might dwarf the wreckage we’ve witnessed in the real-estate markets.
In the latest news, the Federal Reserve’s Board of Governors warned that soaring student-loan debt has “parallels to the housing crisis,” according to a May report in Bloomberg. As with housing, free-flowing cash will lead to widespread default. Of course, it’s easier to repossess a tract house than to take back a potentially worthless degree.
Federal Reserve Chairman Ben Bernanke dismissed these concerns by saying that most of the money in the student-loan sector is federal money, which just means taxpayers – rather than lending institutions – will take the initial hit. But the board of governors makes a salient point as student loan debt soars to $1 trillion and exceeds the nation’s level of credit-card debt.
“The bankers said student lending shares features of the housing crisis including ‘significant growth of subsidized lending in pursuit of a social good,’ in this case higher education instead of expanded home ownership,” according to that Bloomberg report. “The lending has put upward pressure on tuition, just as the mortgage lending boom led to rising home prices, they said, calling both examples of a ‘lack of underwriting discipline.’”
For my entire life, I’ve heard policy makers insist that there is insufficient funding for education and that getting a college degree is the pathway to a better life. But as the bankers noted, the sea of student-loan money artificially boosts the cost of tuition, which creates a new cycle of indebtedness by students. Higher tuition makes “pay-as-you-go” a less-likely option.
Lax student loans make it easier for colleges to spend money poorly. If the federal government provides a loan to virtually anyone who applies for one, then university administrations can spend foolishly. There’s so much money, why not hike salaries and pensions for professors? Why not offer programs and majors that are of questionable intellectual or economic merit?
I know people with six-figure loan debt, multiple degrees and few job prospects. There were few lending standards – hey, it’s only government money – so they racked up loan after loan. Others use loans to gain useful degrees with lucrative job potential, but these graduates come out of school with a crushing load of debt that will take decades to repay.
In 2012, Congress debated a controversy surrounding for-profit colleges, which receive about a quarter of the total federal Title IV student aid programs. The impetus was the latest iteration of the GI bill for active military and veterans, who often choose for-profit education programs.
“These colleges use high-pressure sales tactics to ensnare veterans, promising them a high-quality education and a ‘guaranteed job,’ and urging them to sign up on the spot,” according to Jerome Kohlberg, in an opinion piece in the Pittsburgh Post-Gazette. “They lock themselves into long-term commitments, turn over their GI education benefits and sign up for student loans to cover the difference.”
The alleged abuses at some for-profit colleges have reminded some critics of abuses by the subprime mortgage industry. But these problems are almost solely the result of easy access to government dollars. Indeed, public universities do the same thing – lure students into long-term debt commitments based on a free flow of federal dollars, even if they don’t use the high-pressure tactics used by some recruiters in the private educational business. For-profit and non-profit universities rely heavily on government tuition subsidies.
Many government employees, by the way, receive automatic pay boosts when they receive additional education, so this government-funded system ratchets up government spending throughout the entire taxpayer-funded system.
When I attended college, only the rarest student stayed on campus beyond four years. Many received degrees in less than four years. Now, it’s typical for students to take six years to get through a California State University program. The education establishment claims the problem is the result of too little money, but it’s the opposite. There is so much money available to anyone with a pulse that there are too many students on campus and not enough classes for them.
Look at the large portion of students taking remedial courses, which reminds us that more college doesn’t always equal a better education.
Given that students who get themselves in financial trouble can’t unload their debt through bankruptcy, easy college tuition money can mean a lifetime of personal debt problems. These problems are the result of government officials pushing a social good – i.e., broader college attendance, or, in the real estate market, broader home ownership.
The housing bubble was inflated by government-dictated lending policies designed to expand home ownership by requiring banks to make loans to people who couldn’t meet traditional down-payment and credit standards. And government policies designed to expand educational opportunities have inflated the cost of tuition, cheapened the value of education and burdened new generations with crushing debt loads.
Yet those of us who call for less government meddling and more private-sector discipline are the ones considered heartless.
Why you should care about surveillance
I got tired of people savvying me about the revelations of NSA surveillance and asking why anyone would care about secret, intrusive spying, so I wrote a new Guardian column about it, "The NSA's Prism: why we should care."
We're bad at privacy because the consequences of privacy disclosures are separated by a lot of time and space from the disclosures themselves. It's like trying to get good at cricket by swinging the bat, closing your eyes before you see where the ball is headed, and then being told, months later, somewhere else, where the ball went. So of course we're bad at privacy: almost all our privacy disclosures do no harm, and some of them cause grotesque harm, but when this happens, it happens so far away from the disclosure that we can't learn from it.
You should care about privacy because privacy isn't secrecy. I know what you do in the toilet, but that doesn't mean you don't want to close the door when you go in the stall.
You should care about privacy because if the data says you've done something wrong, then the person reading the data will interpret everything else you do through that light. Naked Citizens, a short, free documentary, documents several horrifying cases of police being told by computers that someone might be up to something suspicious, and thereafter interpreting everything they learn about that suspect as evidence of wrongdoing. For example, when a computer programmer named David Mery entered a tube station wearing a jacket in warm weather, an algorithm monitoring the CCTV brought him to the attention of a human operator as someone suspicious. When Mery let a train go by without boarding, the operator decided it was alarming behaviour. The police arrested him, searched him, asked him to explain every scrap of paper in his flat. A doodle consisting of random scribbles was characterised as a map of the tube station. Though he was never convicted of a crime, Mery is still on file as a potential terrorist eight years later, and can't get a visa to travel abroad. Once a computer ascribes suspiciousness to someone, everything else in that person's life becomes sinister and inexplicable.
The NSA's Prism: why we should care ![]()
Browsers, Huzzah!
Submitted by: Unknown







![1916: 'PHYSICIST DAD' TURNS HIS ATTENTION TO GRAVITY, AND YOU WON'T BELIEVE WHAT HE FINDS. [PICS] [NSFW] 1916: 'PHYSICIST DAD' TURNS HIS ATTENTION TO GRAVITY, AND YOU WON'T BELIEVE WHAT HE FINDS. [PICS] [NSFW]](http://imgs.xkcd.com/comics/headlines.png)



