Shared posts
Simple Method Yields A Wrinkly, Durable, Water-Repellent Coating
Read more of this story at Slashdot.
Windows Telemetry Rolls Out
DantoseWell, so much for privacy...
Read more of this story at Slashdot.
Lifelock Once Again Failed at Its One Job: Protecting Data

"In truth, the protection they provided left such a large hole … that you could drive that truck through it."
The post Lifelock Once Again Failed at Its One Job: Protecting Data appeared first on WIRED.
Online Anonymity Project ProxyHam Mysteriously Vanishes

The highly anticipated anonymity project may be the subject of a law enforcement gag order.
The post Online Anonymity Project ProxyHam Mysteriously Vanishes appeared first on WIRED.
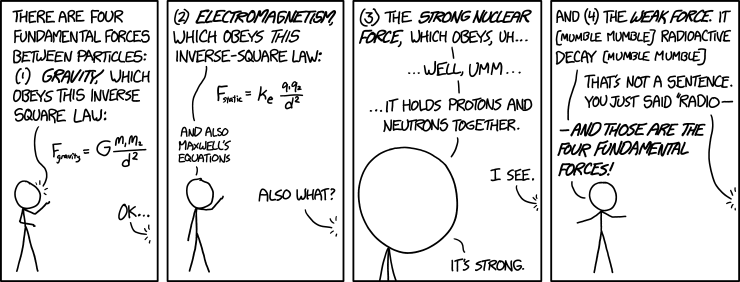
Fundamental Forces
DantoseThis is exactly how I feel every time i have to teach fundamental forces.
UPS: We've Been Hacked
Read more of this story at Slashdot.
A core-collapse, or Type II, supernova occurs in massive stars...
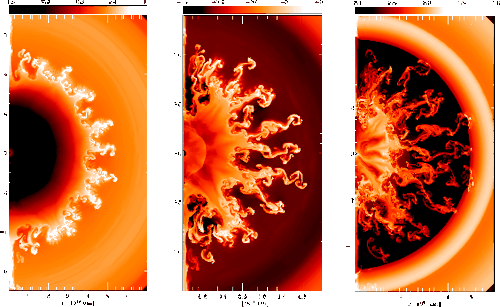
A core-collapse, or Type II, supernova occurs in massive stars when they can no longer sustain fusion. For most of their lives, stars produce energy by fusing hydrogen into helium. Eventually, the hydrogen runs out and the core contracts until it reaches temperatures hot enough to cause the helium to fuse into carbon. This process repeats through to heavier elements, producing a pre-collapse star with onion-like layers of elements with the heaviest elements near the center. When the core consists mostly of nickel and iron, fusion will come to an end, and the core’s next collapse will trigger the supernova. When astronomers observed Supernova 1987A, the closest supernova in more than 300 years, models predicted that the onion-like layers of the supernova would persist after the explosion. But observations showed core materials reaching the surface much faster than predicted, suggesting that turbulent mixing might be carrying heavier elements outward. The images above show several time steps of a 2D simulation of this type of supernova. In the wake of the expanding shock wave, the core materials form fingers that race outward, mixing the fusion remnants. Hydrodynamically speaking, this is an example of the Richtmyer-Meshkov instability, in which a shock wave generates mixing between fluid layers of differing densities. (Image credit: K. Kifonidis et al.; see also B. Remington)
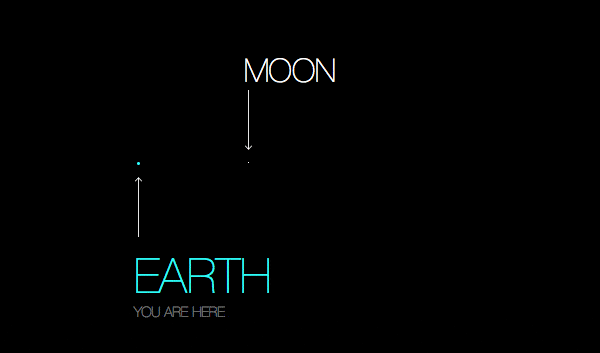
The solar system, were the moon a single pixel
Matt Bors on the dark and awful .GIF wars
Men named Dennis more likely to become dentists
Nominative determinism--one's name influencing oneself--is real. Alice Robb, for The New Republic, recaps research from the last decade or so.
Can we blame Ron Paul’s political ambitions on his last name? Research suggests that people choose—or are unconsciously drawn to—careers that resemble their own names. The effect is stronger for women’s first names and men’s last names; psychologists hypothesize that women are less attached to their last names because they anticipate taking their husbands’
Depending on how you pronounce it, "Beschizza" sounds like various German words and slang terms meaning things like messed up, crappy, shitty, shitfaced, etc. Workin' on it, guys.![]()
How many of your health supplements are actually snake oil?

Recent studies have shown that many vitamins and supplements do little for our health and are a waste of money. This chart will make it abundantly clear how true that is.
Was iOS 7 Made in Microsoft Word?
Ha! What a dumb title! There's no way that could be true.
But I want to watch just to see how dumb it is...
Hmm, okay, that's a decent point... but it's just one decent point!
Huh, well that's... wait, really?
Seriously? This is... What? You've got to be kidding me...
Submitted by: Unknown
Zzzzzzzzz-Thoomp! Phthtbbbhtthbt!!!
Kids Should Hack Their School-Provided iPads
This article originally appeared in Zócalo Public Square and the New America Foundation’s Weekly Wonk. Future Tense is a partnership of Slate, the New America Foundation, and Arizona State University; Zócalo Public Square is a partnership of NAF and Arizona State.
UK officials detain Glenn Greenwald's partner at Heathrow, question him about Snowden interviews, steal all his gadgets & data

Glenn Greenwald's partner David Miranda was detained at Heathrow Airport under an anti-terrorism law that allows the cops to hold terrorism suspects and question them for nine hours without a lawyer. He was held for exactly nine hours, and questioned -- but not about terrorism. Instead, they questioned him about Greenwald's interviews with NSA leaker Edward Snowden. In other words, they misused a terrorism law to attack a journalist through his loved ones in order to get information on sources in a story that embarrassed the government.
What's more, they stole his laptop, his phone, his memory sticks, his game devices -- basically, all his electronics and gadgets. I say "stole" because there's no indication that they'll ever be returned. And of course, all the data on those devices is forfeit to the UK spookocracy, without any charge, suspicion, or colourable claim of involvement with any crime.
According to a document published by the UK government about Schedule 7 of the Terrorism Act, "fewer than 3 people in every 10,000 are examined as they pass through UK borders" (David was not entering the UK but only transiting through to Rio). Moreover, "most examinations, over 97%, last under an hour." An appendix to that document states that only .06% of all people detained are kept for more than 6 hours.
The stated purpose of this law, as the name suggests, is to question people about terrorism. The detention power, claims the UK government, is used "to determine whether that person is or has been involved in the commission, preparation or instigation of acts of terrorism."
But they obviously had zero suspicion that David was associated with a terrorist organization or involved in any terrorist plot. Instead, they spent their time interrogating him about the NSA reporting which Laura Poitras, the Guardian and I are doing, as well the content of the electronic products he was carrying. They completely abused their own terrorism law for reasons having nothing whatsoever to do with terrorism: a potent reminder of how often governments lie when they claim that they need powers to stop "the terrorists", and how dangerous it is to vest unchecked power with political officials in its name.
Worse, they kept David detained right up until the last minute: for the full 9 hours, something they very rarely do. Only at the last minute did they finally release him. We spent all day - as every hour passed - worried that he would be arrested and charged under a terrorism statute. This was obviously designed to send a message of intimidation to those of us working journalistically on reporting on the NSA and its British counterpart, the GCHQ.
Detaining my partner: a failed attempt at intimidation [Glenn Greenwald/The Guardian]
(Image: Heathrow Terminal 5, a Creative Commons Attribution (2.0) image from eguidetravel's photostream)![]()
Senator requests NASA investigation of Space Vikings
Dantosepretty funny
This photo, taken by astronautics grad student and hobby photographer Ved Chirayath, was meant to be a bit of free promotion for NASA and space exploration. With the help of a Viking re-enactment troupe and scientists from the Ames Research Center, he put together a shot that was meant to connect current NASA projects to the exploration-oriented Viking culture. What if two of Earth's greatest explorers met face-to-face?
But the photo, which was done on Chirayath's own time, for fun, has become the center of an extensive investigation initiated by Senator Chuck Grassley, aimed at discovering whether dastardly NASA scientists were using taxpayer money to make whimsical photos. They weren't. Ironically, though, the investigation did use taxpayer money. More, Chirayath estimates, than it would have cost him to get such a photo done by a professional.
How Much Is About Florida Law?
TPM Reader DD writes in from Wisconsin. Going on the below, I'd be curious to hear from lawyers in other jurisdictions how distinct Florida law seems from how a case with a similar set of facts would have been adjudicated in their jurisdictions ...
I'm a criminal defense lawyer in Wisconsin, but I'll tell you my reaction to the Zimmerman verdict today. I've had friends in Florida asking for my take. I haven't watched the trial very closely (it seems like an ordinary criminal case to me in many respects). But I was astounded that the defense would put on a "self-defense" argument without the defendant testifying. In most civilized jurisdictions, the burden is on the defense to prove, at least more likely than not, that the law breaking was done for reasons of self-defense. I couldn't figure out how they could do this without the defendant's testimony.
I got curious and read the jury instructions Friday night and, I was wrong. In Florida, if self-defense is even suggested, it's the states obligation to prove it's absence beyond a reasonable doubt(!). That's crazy. But 'not guilty' was certainly a reasonable result in this case. As I told in friend in Tampa today though, if you're ever in a heated argument with anyone, and you're pretty sure there aren't any witnesses, it's always best to kill the other person. They can't testify, you don't have to testify, no one else has any idea what happened; how can the state ever prove beyond a doubt is wasn't self-defense? Holy crap! What kind of system is that?
Following up on the conversation, Eugene Volokh suggests that the law of self-defense is actually the same in Florida as it is throughout the country, with the single exception of Ohio.
US Entertainment Industry To Congress: Make It Legal For Us To Deploy Rootkits
Read more of this story at Slashdot.
Hardwood Escher tesselated interlocking lizard tiles
DantosePretty awesome

 The Spanish firm Arbore offered these custom Escher-inspired floor tiles back in 2011; from the looks of things, they're still available. It's a very well-executed conceit, done in hardwood.
The Spanish firm Arbore offered these custom Escher-inspired floor tiles back in 2011; from the looks of things, they're still available. It's a very well-executed conceit, done in hardwood.
Diseño geometrico inspiración Escher (via Geekologie) ![]()

![Googling inevitably reveals that my problem is caused by a known bug triggered by doing [the exact combination of things I want to do]. I can fix it, or wait a few years until I don't want that combination of things anymore, using the kitchen timer until then. Googling inevitably reveals that my problem is caused by a known bug triggered by doing [the exact combination of things I want to do]. I can fix it, or wait a few years until I don't want that combination of things anymore, using the kitchen timer until then.](http://imgs.xkcd.com/comics/hard_reboot.png)


 Click the icons at the top, or
Click the icons at the top, or 








