Read more of this story at Slashdot.
Shared posts
Confronting an Ancient Indian Hierarchy, Apple and IBM Ban Discrimation By Caste
Twitter Exposes Personal Information for 5.4 Million Accounts
Twitter accidentally exposed the personal information—including phone numbers and email addresses—for 5.4 million accounts. And someone was trying to sell this information.
In January 2022, we received a report through our bug bounty program of a vulnerability in Twitter’s systems. As a result of the vulnerability, if someone submitted an email address or phone number to Twitter’s systems, Twitter’s systems would tell the person what Twitter account the submitted email addresses or phone number was associated with, if any. This bug resulted from an update to our code in June 2021. When we learned about this, we immediately investigated and fixed it. At that time, we had no evidence to suggest someone had taken advantage of the vulnerability.
In July 2022, we learned through a press report that someone had potentially leveraged this and was offering to sell the information they had compiled. After reviewing a sample of the available data for sale, we confirmed that a bad actor had taken advantage of the issue before it was addressed.
This includes anonymous accounts.
This comment has it right:
So after forcing users to enter a phone number to continue using twitter, despite twitter having no need to know the users phone number, they then leak the phone numbers and associated accounts. Great.
But it gets worse… After being told of the leak in January, rather than disclosing the fact millions of users data had been open for anyone who looked, they quietly fixed it and hoped nobody else had found it.
It was only when the press started to notice they finally disclosed the leak.
That isn’t just one bug causing a security leak—it’s a chain of bad decisions and bad security culture, and if anything should attract government fines for lax data security, this is it.
Twitter’s blog post unhelpfully goes on to say:
If you operate a pseudonymous Twitter account, we understand the risks an incident like this can introduce and deeply regret that this happened. To keep your identity as veiled as possible, we recommend not adding a publicly known phone number or email address to your Twitter account.
Earth sets record for the shortest day
Having Rich Childhood Friends is Linked To a Higher Salary as an Adult
Read more of this story at Slashdot.
How to subscribe to YouTube RSS Feeds without third-party services
YouTube, at one time, supported RSS feeds. Anyone could subscribe to channel feeds to receive updates in any RSS reader.
Google made it harder over the years to subscribe to channels, likely to push YouTube's own subscriptions feature. Unlike feeds, subscriptions requires that users are signed in to an account to receive updates.
Third-party apps like NewPipe for Android or the Vivaldi web browser support subscriptions out of the box. Even Microsoft is experimenting with a "follow creator" feature in its Edge browser.
While those options are great, some users prefer to use a dedicated feed reader instead. Ideally, they'd subscribe to all their favorite channels to receive notifications whenever new videos are posted. One extra benefit of that is that there is no artificial limit in place.
How to subscribe to YouTube creator RSS feeds manually
It takes a bit of code digging to reveal the RSS feed of a channel or a playlist without third-party tools.
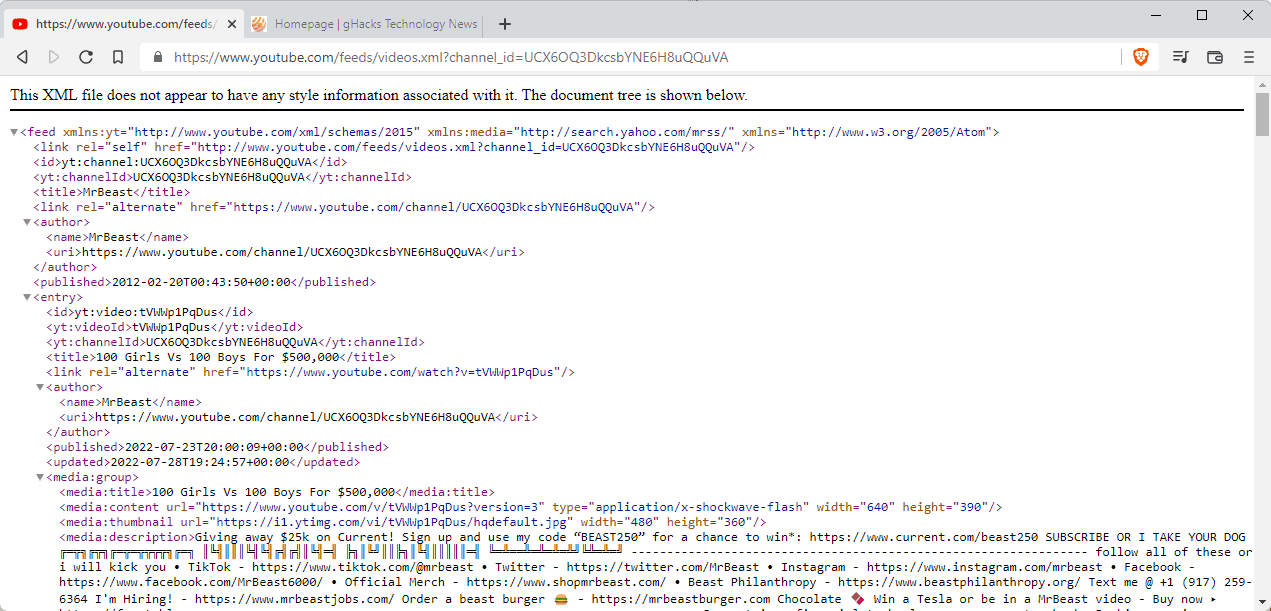
The core URL that you require is https://www.youtube.com/feeds/videos.xml?channel_id=CHANNELID.
You need to replace CHANNELID with the ID of the channel, and that is where it may get tricky for some.
Most YouTube channels use personalized names in the URL and not the channel ID. While you may access a YouTube channel using the personalized name and the channel ID, you can't access the RSS feed using the personalized name.
One example:
- Mr. Beast Channel ID URL: https://www.youtube.com/channel/UCX6OQ3DkcsbYNE6H8uQQuVA
- Mr. Beast Personalized URL: https://www.youtube.com/user/MrBeast6000
Reveal the YouTube channel ID
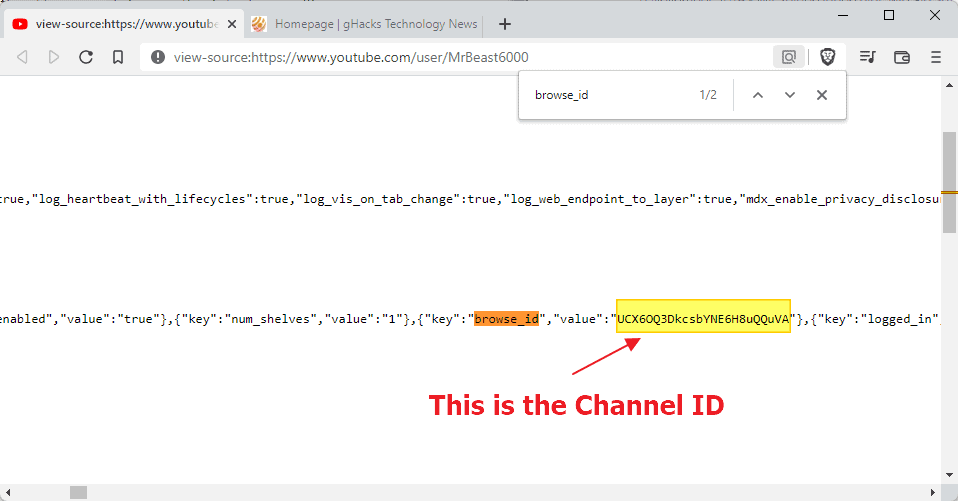
You need to display the source code of the channel on YouTube to reveal the ID. Here is how that is done:
- Open the creator channel on YouTube, e.g., https://www.youtube.com/user/PewDiePie
- Right-click on a blank part of the page and select "view page source". Depending on the browser that you use, it may have a slightly different name. Alternatively, prepend view-source: before the URL and hit the Enter-key.
- Search for browse_id. You may open the search option with Ctrl-F, or from the browser's main menu.
- The browser jumps to the first instance of browse_id in the source code. Copy the string of the value field that is right next to it; this is the channel's ID.
Create the YouTube channel RSS feed URL
Now that you have the channel ID and the default feed address, you can combine the two to create a working feed address:
- Default URL: https://www.youtube.com/feeds/videos.xml?channel_id=CHANNELID
- Channel ID: UCX6OQ3DkcsbYNE6H8uQQuVA
- Working Feed URL: https://www.youtube.com/feeds/videos.xml?channel_id=UCX6OQ3DkcsbYNE6H8uQQuVA
The easiest way to test the feed URL is to load it in the browser. The browser should display the content of the XML file. You may subscribe to the channel using that URL in any feed reader that supports it.
Create a YouTube playlist RSS feed URL
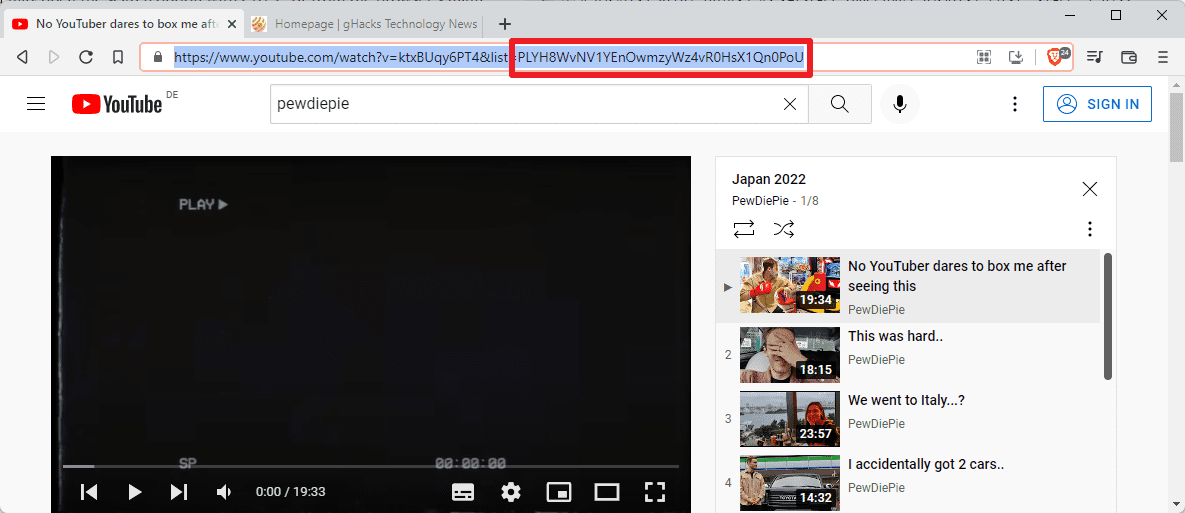
You may create RSS feed URLs of playlists on YouTube as well. Thankfully, this is easier as the IDs of playlists are already visible in playlist URLs.
The default feed address for playlists: https://www.youtube.com/feeds/videos.xml?playlist_id=PLAYLISTID
Here is how that is done:
- Open the playlist on YouTube, e.g., https://www.youtube.com/watch?v=ktxBUqy6PT4&list=PLYH8WvNV1YEnOwmzyWz4vR0HsX1Qn0PoU
- The ID begins after list=; in the case above, it is PLYH8WvNV1YEnOwmzyWz4vR0HsX1Qn0PoU
- Replace PLAYLISTID of the default feed address with the real ID to create the RSS feed for the playlist. In the example above, you get https://www.youtube.com/feeds/videos.xml?playlist_id=PLYH8WvNV1YEnOwmzyWz4vR0HsX1Qn0PoU
Now You: are you subscribe to YouTube channels?
Thank you for being a Ghacks reader. The post How to subscribe to YouTube RSS Feeds without third-party services appeared first on gHacks Technology News.
RSS Support For MarkDown
Favorited dev Notes for Markdown in RSS by Dave Winer
As part of celebrating twenty years of RSS, Dave Winer adds the ability to incorporate markdown in RSS feeds. Essentially this was always possible, but there was no way to tell a RSS reader that something was to be interpreted not as HTML but as Markdown. Doing this makes it possible to provide both HTML and Markdown in the same feed, if Markdown is e.g. the way you’ve written a posting and want to be able to also edit it again in Markdown, and not in HTML.
After my hiatus I think this is worth an experiment to see if I can generate an RSS feed directly from my markdown notes on my local system. Just like I already can generate OPML feeds and blogposts or website pages from my notes. Chris Aldrich recently asked about using WordPress and Webmention as a way of publishing your own notes with the capability of linking them to other peoples notes. Could RSS play a role there too? Could I provide selected RSS feeds for specific topics directly from my notes? Or for specific people? For them to read along? Is there something here that can play a role in social sharing of annotations, such as Hypothes.is provides? I need to play with this thought. RSS is well understood an broadly used, providing not just HTML but also Markdown through it sounds like a step worth exploring.
Critical Vulnerabilities in GPS Trackers
This is a dangerous vulnerability:
An assessment from security firm BitSight found six vulnerabilities in the Micodus MV720, a GPS tracker that sells for about $20 and is widely available. The researchers who performed the assessment believe the same critical vulnerabilities are present in other Micodus tracker models. The China-based manufacturer says 1.5 million of its tracking devices are deployed across 420,000 customers. BitSight found the device in use in 169 countries, with customers including governments, militaries, law enforcement agencies, and aerospace, shipping, and manufacturing companies.
BitSight discovered what it said were six “severe” vulnerabilities in the device that allow for a host of possible attacks. One flaw is the use of unencrypted HTTP communications that makes it possible for remote hackers to conduct adversary-in-the-middle attacks that intercept or change requests sent between the mobile application and supporting servers. Other vulnerabilities include a flawed authentication mechanism in the mobile app that can allow attackers to access the hardcoded key for locking down the trackers and the ability to use a custom IP address that makes it possible for hackers to monitor and control all communications to and from the device.
The security firm said it first contacted Micodus in September to notify company officials of the vulnerabilities. BitSight and CISA finally went public with the findings on Tuesday after trying for months to privately engage with the manufacturer. As of the time of writing, all of the vulnerabilities remain unpatched and unmitigated.
These are computers and computer vulnerabilities, but because the computers are attached to cars, the vulnerabilities become potentially life-threatening. CISA writes:
These vulnerabilities could impact access to a vehicle fuel supply, vehicle control, or allow locational surveillance of vehicles in which the device is installed.
I wouldn’t have buried “vehicle control” in the middle of that sentence.
Why HDR gaming on PC is such a mess, according to a Ubisoft developer
HDR has been an embarrassment for PC gaming for years. The state of affairs isn’t much better in 2022 than it was five years ago, but to really understand what has gone wrong, I needed to speak to an authority on the game development side of the story.
Contents
- Not a ‘first-class citizen’
- Platform-agnostic
- HDR is a premium, even for developers
So, I spoke with a technical developer over at Ubisoft to get their take on the matter. It’s an issue that large developers like Ubisoft are well aware of, and have even developed tools to combat — but they also say we’re making progress, even if we have a long way to go.
Not a ‘first-class citizen’
Nicolas Lopez is a rendering technical lead working on Ubisoft Anvil — the engine behind Assassin’s Creed Valhalla, Rainbow Six Extraction, and the upcoming Prince of Persia: The Sands of Time Remake, among others. Lopez leads the charge on getting all of the art, mechanics, and code into a final image, and he didn’t mince words about HDR: “HDR is not treated as the first class-citizen it should be in the game industry.”
A big reason why is adoption, according to Lopez. HDR on PC monitors hasn’t been a focal point like it has on consumer TVs, and for a multiplatform studio like Ubisoft, that means focusing much of the effort on the SDR result. Lopez says that the teams at Ubisoft “are very confident about our SDR workflows and outputs, but we know that the mileage may vary when working with HDR on PC.”
The vast majority of HDR monitors available today only meet the lowest DisplayHDR 400 level.
The mileage on PC varies so much because PC monitors have unstable standards for what constitutes HDR (even among the best HDR monitors). The DisplayHDR standard from VESA attempts to standardize the appearance of HDR on gaming monitors, but it has some major loopholes. Take the Samsung Odyssey G7 and MSI MPG32-QD as two examples. Both have DisplayHDR 600 certification, but the MSI monitor has twice as many local dimming zones. That leads to a much more natural HDR image despite the fact that both monitors have the same certification.
To make matters worse, the vast majority of HDR monitors available today only meet the lowest DisplayHDR 400 level — a certification that doesn’t even come close to the requirements of HDR. TVs, on the other hand, have much better HDR at a much lower price. The Hisense U8G, for example, gets much brighter than a gaming monitor and comes with full array local dimming (a feature you can only find on gaming monitors north of $1,200).
Riley Young/Digital Trends
Lopez says developers are acutely aware of the difference between gaming monitors and TVs, and the teams at Ubisoft prioritize accordingly: “We assume the vast majority of players who are going to play our games on a HDR display will do so on a console plugged to a HDR TV, so it’s our main target. However we make sure all platforms look good in the end.”
Platform-agnostic
With the vast differences between HDR gaming monitors in mind, Lopez says the teams as Ubisoft “try to make the process as transparent and platform-agnostic as possible” to avoid duplicating work and speed up production pipelines. For that, Ubisoft uses the Academy Color Encoding System (ACES), which is a device-independent color space developed by the Academy of Motion Picture Arts and Sciences (yes, the Oscars people).
The main benefit of ACES is that it takes in all of the data and processes it down to the color space of the display you’re using. “Thanks to ACES, you can technically grade your game on an SDR display, and it will still be valid in HDR,” Lopez says. However, he also clarified that “it’s still better to master on an HDR display.”
Although a generalist approach is good for a multiplatform studio like Ubisoft, it can’t solve the issues that HDR gaming monitors have today. “HDR support on PC monitors has been lagging behind for quite a while compared to consumer TVs,” Lopez says.
Outside of the panels themselves, a key feature missing from all but a few gaming expensive gaming monitors is dynamic metadata. HDR 10+ and Dolby Vision are widely supported on TVs like the LG C2 OLED and consoles, which both offer dynamic metadata to adjust the color and brightness on a scene-by-scene or even frame-by-frame basis.
With static metadata, Lopez says that games set the minimum and maximum brightness values once at the start, essentially covering the entire spectrum of color possible for every possible lighting situation. “With dynamic metadata, we can determine the optimal range of min/max brightness per frame … and produce more accurate colors.”
Ubisoft, and likely most AAA studios, color games to look great on as many display as possible. But all of the effort still can’t reproduce the exact same image on every display, an issue that’s compounded by the fact that HDR gaming monitors are behind TVs in terms of panel technology and dynamic metadata. The result: Wildly different HDR experiences despite the developer’s intentions and effort.
HDR is a premium, even for developers
Dan Baker/Digital Trends
It’s easy to assume that a multibillion-dollar company like Ubisoft has a fleet of high-quality HDR displays to calibrate games with, but I still posed the question to Lopez. He says the vast majority of work still happens on SDR displays, while HDR is “usually assigned to a few key people equipped with consumer HDR TVs, or very specific calibrated HDR monitors.”
Lopez even shared a story about running game builds across the street to a different company to test HDR performance. “At some point, we had a deal with a high-end electronic product review company on the other side of the street. Some teams would take their game builds over there and have the opportunity to test on a wide range of consumer displays.”
“I’m confident we’re getting there.”
Although a large developer like Ubisoft has access to high-quality HDR displays, it’s safe to assume that smaller developers don’t have the same luxuries (especially given some of the hoops a developer like Ubisoft has needed to jump through). Lopez said this gap became all the more apparent during the pandemic, when the team had to lean on ACES as developers remotely connected to their SDR work desktops.
At the end of my Q&A, Lopez reiterated that HDR is not treated like the first-class citizen it should be. Much more development time and effort goes toward making a high-quality SDR version that, hopefully, offers a solid HDR experience on consumer TVs. Lopez seemed confident that HDR is improving, though: “It’s been a slow transition and adoption, but with the new generation of HDR consoles and vendors ramping up their production lines, I’m confident we’re getting there.”
The post Why HDR gaming on PC is such a mess, according to a Ubisoft developer appeared first on AIVAnet.
New Browser De-anonymization Technique
Researchers have a new way to de-anonymize browser users, by correlating their behavior on one account with their behavior on another:
The findings, which NJIT researchers will present at the Usenix Security Symposium in Boston next month, show how an attacker who tricks someone into loading a malicious website can determine whether that visitor controls a particular public identifier, like an email address or social media account, thus linking the visitor to a piece of potentially personal data.
When you visit a website, the page can capture your IP address, but this doesn’t necessarily give the site owner enough information to individually identify you. Instead, the hack analyzes subtle features of a potential target’s browser activity to determine whether they are logged into an account for an array of services, from YouTube and Dropbox to Twitter, Facebook, TikTok, and more. Plus the attacks work against every major browser, including the anonymity-focused Tor Browser.
[…]
“Let’s say you have a forum for underground extremists or activists, and a law enforcement agency has covertly taken control of it,” Curtmola says. “They want to identify the users of this forum but can’t do this directly because the users use pseudonyms. But let’s say that the agency was able to also gather a list of Facebook accounts who are suspected to be users of this forum. They would now be able to correlate whoever visits the forum with a specific Facebook identity.”
What Makes Workers 'Thrive'? Microsoft Study Suggests Shorter Workweeks and Less Collaboration
Read more of this story at Slashdot.
On the Subversion of NIST by the NSA
Nadiya Kostyuk and Susan Landau wrote an interesting paper: “Dueling Over DUAL_EC_DRBG: The Consequences of Corrupting a Cryptographic Standardization Process“:
Abstract: In recent decades, the U.S. National Institute of Standards and Technology (NIST), which develops cryptographic standards for non-national security agencies of the U.S. government, has emerged as the de facto international source for cryptographic standards. But in 2013, Edward Snowden disclosed that the National Security Agency had subverted the integrity of a NIST cryptographic standardthe Dual_EC_DRBGenabling easy decryption of supposedly secured communications. This discovery reinforced the desire of some public and private entities to develop their own cryptographic standards instead of relying on a U.S. government process. Yet, a decade later, no credible alternative to NIST has emerged. NIST remains the only viable candidate for effectively developing internationally trusted cryptography standards.
Cryptographic algorithms are essential to security yet are hard to understand and evaluate. These technologies provide crucial security for communications protocols. Yet the protocols transit international borders; they are used by countries that do not necessarily trust each other. In particular, these nations do not necessarily trust the developer of the cryptographic standard.
Seeking to understand how NIST, a U.S. government agency, was able to remain a purveyor of cryptographic algorithms despite the Dual_EC_DRBG problem, we examine the Dual_EC_DRBG situation, NIST’s response, and why a non-regulatory, non-national security U.S. agency remains a successful international supplier of strong cryptographic solutions.
Ambrose Bierce
Tracking People via Bluetooth on Their Phones
We’ve always known that phones—and the people carrying them—can be uniquely identified from their Bluetooth signatures, and that we need security techniques to prevent that. This new research shows that that’s not enough.
Computer scientists at the University of California San Diego proved in a study published May 24 that minute imperfections in phones caused during manufacturing create a unique Bluetooth beacon, one that establishes a digital signature or fingerprint distinct from any other device. Though phones’ Bluetooth uses cryptographic technology that limits trackability, using a radio receiver, these distortions in the Bluetooth signal can be discerned to track individual devices.
[…]
The study’s scientists conducted tests to show whether multiple phones being in one place could disrupt their ability to track individual signals. Results in an initial experiment showed they managed to discern individual signals for 40% of 162 devices in public. Another, scaled-up experiment showed they could discern 47% of 647 devices in a public hallway across two days.
The tracking range depends on device and the environment, and it could be several hundred feet, but in a crowded location it might only be 10 or so feet. Scientists were able to follow a volunteer’s signal as they went to and from their house. Certain environmental factors can disrupt a Bluetooth signal, including changes in environment temperature, and some devices send signals with more power and range than others.
One might say “well, I’ll just keep Bluetooth turned off when not in use,” but the researchers said they found that some devices, especially iPhones, don’t actually turn off Bluetooth unless a user goes directly into settings to turn off the signal. Most people might not even realize their Bluetooth is being constantly emitted by many smart devices.
Vytal: browser extension to spoof your location and user agent
Vytal is an open source browser extension for Google Chrome and other Chromium-based browsers, that will spoof the location, locale, timezone and user agent manually or automatically.
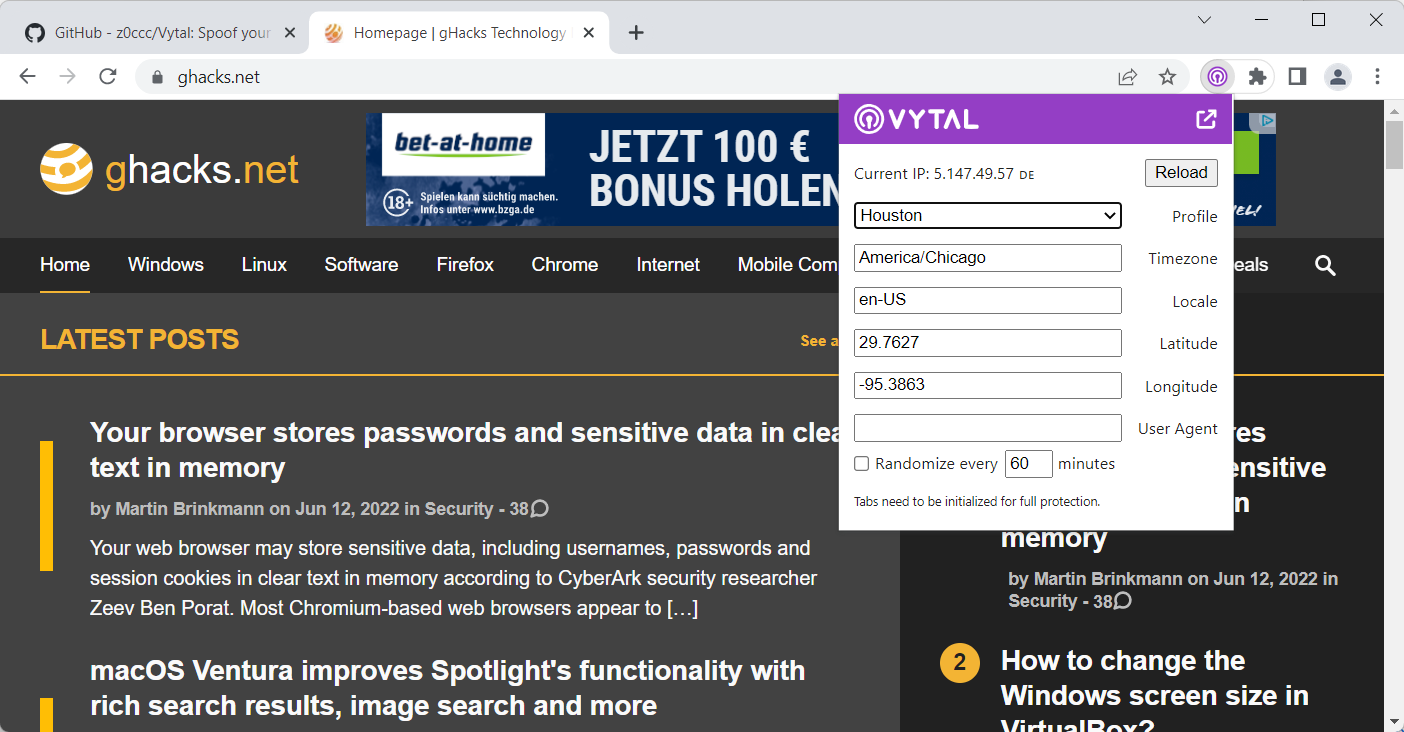
Vytal uses the chrome.debugger API, which the developer believes makes the use of the extension undetectable by websites and will spoof the data during the initial loading of webpages as well as in iframes and web workers.
One of the main ideas behind Vytal was to give VPN users a tool at hand to match location-based identifiers to the VPN's location. Sites may use scripts to find discrepancies between the VPN's location, based on the IP address, and other location data, which the browser may provide.
The Vytal extension is available in the Chrome Web Store. Just visit its profile page there and install it, just like any other Chrome extension. You may check the source code of the extension on GitHub.
Installation adds an icon to Chrome's main toolbar that you may interact with. A click displays the available options and information about the current IP address and region. The profile menu lists dozens of regional profiles that you may apply manually, e.g., to spoof your location, timezone and locale to Houston, Jersusalem, or Bangkok.
You also find an option to match the regional settings to the active IP address; this is what VPN users may want to activate, as it automates the process of matching the VPN server location to the spoofed data of the browser. A custom option is available next to that, to enter data manually into the fields.
There is an option to randomize the data every 60 minutes, or any other period that you set the randomizer to.
Last but not least, you may also set a different user agent, but none appears to be provided, which means that you need to set it manually.
Vytal has two shortcomings that users need to be aware of. Chromium-based browsers display a "started debugging this browser" message at the top when extensions are active that use the debugging API. The notification is displayed at the top in the browser when Vytal is being used.
Chrome and other Chromium-based browsers support the command line switch --silent-debugger-extension-api, which supresses the message in the browser.
The second issue weights more heavily. There is a slight delay between opening a new tab and the start of the debugger. Sites may use this delay to retrieve information before the actual spoofing takes place. Since this is tab-based, users might get around this by loading safe sites in tabs first before loading sites that might detect spoofing this way.
The browser extension is not available for Firefox, as the browser does not support the debugging API according to the developer.
Closing Words
The browser extension Vytal may be useful to Internet users who run into location-based issues when using sites; this may affect users who are abroad on vacation or because of their job, and users who use VPN's to access content in different locations in the world.
Sites have other means to block access to content, for example, by detecting that IP addresses that are linked to a VPN service are being used.
Still, it may be worth a shot for users who can't use certain services because of their location.
Now you: do you use VPNs to spoof your location?
Thank you for being a Ghacks reader. The post Vytal: browser extension to spoof your location and user agent appeared first on gHacks Technology News.
Ralph Waldo Emerson
Ronald Reagan
Google 'Private Browsing' Mode Not Really Private, Texas Lawsuit Says
Read more of this story at Slashdot.
Google Blocks File Manager Total Commander From Allowing Users To Sideload Apps
Maxim BangeWhat is an Operating System these days?
Read more of this story at Slashdot.
Unconvincing Criticism of Data Altruism
Bookmarked Data altruism: how the EU is screwing up a good idea (by Winfried Veil)
I find this an unconvincing critique of the data altruism concept in the new EU Data Governance Act (caveat: the final consolidated text of the new law has not been published yet).
“If the EU had truly wanted to facilitate processing of personal data for altruistic purposes, it could have lifted the requirements of the GDPR”
GDPR slackened for common good purposes? Let’s loosen citizen rights requirements? It asumes common good purposes can be well enough defined to not endanger citizen rights, turtles all the way down. The GDPR is a foundational block, one in which the author, some googling shows, is disappointed with having had some first hand experience in its writing process. The GDPR is a quality assurance instrument, meaning, like with ISO style QA systems, it doesn’t make anything impossible or unallowed per se but does require you organise it responsibly upfront. That most organisations have implemented it as a compliance checklist to be applied post hoc is the primary reason for it being perceived as “straight jacket” and for the occurring GDPR related breaches to me.
It is also worth noting that data altruism also covers data that is not covered by the GDPR. It’s not just about person identifiable data, but also about otherwise non-public or confidential organisational data.
The article suggests it makes it harder for data altruistic entities to do something that already now can be done under the GDPR by anyone, by adding even more rules.
The GDPR pertains to the grounds for data collection in the context of usage specified at the time of collection. Whereas data altruism is also aimed at non-specified and at not yet known future use of data collected here and now. As such it covers an unaddressed element in the GDPR and offers a path out of the purpose binding the GDPR stipulates. It’s not a surprise that a data altruism entity needs to comply with both the GDPR and a new set of rules, because those additional rules do not add to the GDPR responsibilities but cover other activities. The type of entities envisioned for it already exist in the Netherlands, common good oriented entities called public benefit organisations: ANBI‘s. These too do not absolve you from other legal obligations, or loosen the rules for you. On the contrary these too have additional (public) accountability requirements, similar to those described in the DGA (centrally registered, must publish year reports). The DGA creates ANBI’s for data, Data-ANBI’s. I’ve been involved in data projects that could have benefited from that possibility but never happened in the end because it couldn’t be made to work without this legal instrument.
To me the biggest blind spot in the criticism is that each of the examples cited as probably more hindered than helped by the new rules are single projects that set up their own data collection processes. That’s what I think data altruism is least useful for. You won’t be setting up a data altruism entity for your project, because by then you already know what you want the data for and start collecting that data after designing the project. It’s useful as a general purpose data holding entity, without pre-existing project designs, where later, with the data already collected, such projects as cited as example will be applicants to use the data held. A data altruistic entity will not cater to or be created for a single project but will serve data as a utility service to many projects. I envision that universities, or better yet networks of universities, will set up their own data altruistic entities, to cater to e.g. medical or social research in general. This is useful because there currently are many examples where handling the data requirements being left to the research team is the source of not just GDPR breaches but also other ethical problems with data use. It will save individual projects such as the examples mentioned a lot of time and hassle if there’s one or more fitting data altruistic entities for them to go to as a data source. This as there will then be no need for data collection, no need to obtain your own consent or other grounds for data collection for each single respondent, or create enough trust in your project. All that will be reduced to guaranteeing your responsible data use and convince an ethical board of having set up your project in a responsible way so that you get access to pre-existing data sources with pre-existing trust structures.
It seems to me sentences cited below require a lot more thorough argumentation than the article and accompanying PDF try to provide. Ever since I’ve been involved in open data I’ve seen plenty of data innovations, especially if you switch your ‘only unicorns count’ filter off. Barriers that unintentionally do exist typically stem more from a lack of a unified market for data in Europe, something the DGA (and the GDPR) is actually aimed at.
“So long as the anti-processing straitjacket of the GDPR is not loosened even a little for altruistic purposes, there will be little hope for data innovations from Europe.” “In any case, the EU’s bureaucratic ideas threaten to stifle any altruism.”
Winfried Veil
How America Reached One Million Covid Deaths | Jeremy White, Amy...

How America Reached One Million Covid Deaths | Jeremy White, Amy Harmon, Danielle Ivory, Lauren Leatherby, Albert Sun and Sarah Almukhtar
The virus did not claim lives evenly, or randomly. The New York Times analyzed 25 months of data on deaths during the pandemic and found that some demographic groups, occupations and communities were far more vulnerable than others. A significant proportion of the nation’s oldest residents died, making up about three-quarters of the total deaths. And among younger adults across the nation, Black and Hispanic people died at much higher rates than white people.
Understanding the toll — who makes up the one million and how the country failed them — is essential as the pandemic continues. More than 300 people are still dying of Covid every day.
“We are a country with the best doctors in the world, we got a vaccine in an astoundingly short period of time, and yet we’ve had so many deaths,” said Mary T. Bassett, the health commissioner for New York State.
“It really should be a moment for us all to reflect on what sort of society we want to have,” she added.
Adding Unoffice Hours
Matt Webb has been keeping UnOffice hours for a few years, a few timeslots in his week during which anyone can come by and talk to him. Several people in my network similarly have opened parts of their weekly schedule for others to be able to plan a conversation with them. Using a tool like Calendly, it saves the back and forth of finding a time. More importantly it is a clear signal you don’t have to ask if it’s ok to have a conversation. You can just go ahead and plan it if you want to talk to them.
I like that idea. A few times in the past I’ve mailed a selection of my own contacts to ask them for a conversation, just to catch up and hear what they are doing. It always leads to some new insights or connections, and sometimes it generates a next step. It’s a serendipity aid.
As an experiment I’ve created a schedule in which anyone can book a conversation on Wednesday afternoons (Central European Time). You can find the link to my Calendly schedule in the right hand side bar.
Cleaner Air Leads To More Atlantic Hurricanes, Study Finds
Read more of this story at Slashdot.
I kind of miss how pretty Nokia Lumia Windows phones looked

Allan Goldfein
Joint Statement on the Invasion of Ukraine and the Importance of Freedom of Expression and Information
In the light of the invasion of Ukraine by the Russian Federation and the continuation of the Russian war of aggression against Ukraine, the monitors for freedom of expression and freedom of the media for the United Nations (UN), the African Commission of Human Rights (ACHR), the Inter-American Commission for Human Rights (ItACHR), and the Organization for Security and Co-operation in Europe (OSCE) issued the following joint statement:
We collectively condemn the invasion of and continuous aggression against Ukraine, its sovereignty and territorial integrity by the Russian Federation. The actions of the Russian Federation violate international law and the common UN, OSCE, ItACHR and ACHR commitments and the very principles on which our organizations are based.
We are outraged about the continuous atrocities and the resulting grave human rights and humanitarian crises, which have a massive detrimental impact on civilians’ lives, safety and well-being. We stand in solidarity with the people of Ukraine in these difficult times.
We recall that it is precisely during times of war and armed conflict that the right to freedom of expression and free access to information must be vigorously defended, as it is instrumental for the promotion of lasting peace, understanding the nature of the conflict and ensuring accountability.
In this connection, we highlight the following:
First, we are profoundly concerned about the safety of journalists, media workers and associated personnel in Ukraine, who are carrying out their work under unprecedented conditions, and are now at a very high risk. There are numerous reports that journalists and they are being targeted, tortured, kidnapped, attacked and killed, or refused safe passage from the cities and regions under siege. Such actions are abhorrent and must be stopped immediately. We recall that under international humanitarian law, during armed conflict journalists are considered to be civilians and must be afforded protection as such. An attack to kill, wound or abduct a journalist constitutes a war crime. Those responsible for direct or indiscriminate attacks on civilians, including journalists, should be held accountable and brought to justice under national and international law. Measures must also be taken to trace missing journalists, ascertain their fate, provide appropriate assistance and facilitate their return to their families. States have the duty and obligation to protect and guarantee human rights, to conduct effective investigations and to guarantee effective remedies and reparations.
Second, we are alarmed by reports that Ukraine’s media and internet infrastructure may be intentionally targeted by the Russian forces in an effort to disrupt access to information, including by means of cyberattacks. We appreciate that access to Ukraine's internet infrastructure has remained largely resilient. It is crucial to ensure that people in Ukraine have continued access to the internet, broadcasting and other means of communication. We call for the adoption of all feasible measures to protect the media, media organisations, and internet infrastructure from attacks and hostile take overs. We also call for increased support in various forms by the international community to ensure media sustainability in Ukraine at a time when a number of national and local media outlets have lost their premises and equipment or have been damaged or destroyed. Initiatives that enable Ukrainian journalists and media in exile to continue their professional work should also be supported in a manner that is sustainable and adapted to the exceptional conditions they are facing.
Third, we underline that propaganda for war and national hatred which constitutes incitement to discrimination, hostility or violence are profoundly harmful and prohibited under article 20 of the International Covenant on Civil and Political Rights. We call on the Russian Federation to immediately refrain from these unlawful practices.
Fourth, we are concerned at the spread of disinformation concerning the conflict in Ukraine in Russian state-owned media. However, we believe that disinformation cannot be addressed by blocking or banning media outlets. Any restriction of freedom of expression should respect scrupulously the three-part test of legality, legitimate aim, and necessity and proportionality. We are concerned that the EU’s decision to ban two Russian state-owned media outlets may have been a disproportionate response to disinformation. It has been used as a pretext for additional closure of independent media outlets in the Russian Federation. Promoting access to diverse and verifiable information, including ensuring access to free, independent and pluralistic media, is a more effective response to disinformation.
Fifth, we believe that the erosion of the right to freedom of expression and other human rights over a prolonged period of time and the silencing of critical voices in the Russian Federation have contributed to creating an environment that facilitates Russia’s war against Ukraine. We are alarmed at the further tightening of censorship and repression of dissent and pluralist sources of information and opinion in the Russian Federation, including the blocking of social media platforms and news websites, disruption of services from foreign content and service providers, massive labeling of independent journalists and media as “foreign agents”, introduction of criminal liability and imprisonment of up to fifteen years for spreading so-called “fake” information about the war in Ukraine or questioning Russian military action in Ukraine or simply standing for peace or even mentioning the word “war”. We deplore the systematic crackdown on political opponents, independent journalists and the media, human rights activists, protesters and many others opposing the Russian government’s actions. All these measures amount to the creation of a state monopoly on information in blatant violation of Russia’s international obligations. They must stop. We call on the Russian government to fully implement its international human rights obligations, including by respecting, promoting and protecting the freedom to seek, receive and impart information regardless of frontiers, and by ensuring a safe working environment for independent media, journalists and civil society actors.
Six, we note that the war in Ukraine has further highlighted the risks of the proliferation of disinformation, misinformation and incitement to violence and hatred and restrictions of lawful speech on digital and social media platforms as a result of their business models, policies and practices. While we appreciate that dominant companies recently made some efforts to address these problems, we urge them to strengthen their human rights due diligence and impact assessment, accountability, transparency and equal and consistent application of policies to uphold the rights of all users.
* The freedom of expression mandates are: Mrs. Irene Khan, Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression; Mrs. Teresa Ribeiro, OSCE Representative on Freedom of the Media, Mr. Pedro Pedro Vaca Villarreal, Inter-American Commission on Human Rights Special Rapporteur for Freedom of Expression, and Hon. Ourveena Geereesha Topsy-Sonoo, African Commission Special Rapporteur on Freedom of Expression and Access to Information.
Razer co-founder and gaming mouse pioneer Robert Krakoff has passed away
Maxim BangeR.I.P.

Robert “Razerguy” Krakoff, the co-founder and former president of gaming hardware company Razer, passed away last week at the age of 81. Maybe you’ve never heard Krakoff’s name, but it’s possible you’ve been impacted by his far-reaching legacy.
In 1999, Krakoff was behind the first-ever gaming mouse: the Razer Boomslang. Not only was it the foundation of Razer’s now-massive lineup of gaming mice, it arguably jumpstarted the entire gaming peripheral industry. Below, you can see Krakoff himself in an ad promoting the Razer Boomslang mouse in 2002 — alongside professional gamer Johnathan “Fatal1ty” Wendel, who signed a historic sponsorship deal with Razer long before the word “esports” entered the lexicon.
Origin stories can be...
All of the Bases In DNA, RNA Have Now Been Found In Meteorites
Read more of this story at Slashdot.
A Visit to the Nuclear Missile Next Door
Read more of this story at Slashdot.
